Introduction to Microsoft Defender for Kubernetes (deprecated)
Defender for Cloud provides real-time threat protection for your Azure Kubernetes Service (AKS) containerized environments and generates alerts for suspicious activities. You can use this information to quickly remediate security issues and improve the security of your containers.
Threat protection at the cluster level is provided by the analysis of the Kubernetes audit logs. Host-level threat detection for your Linux AKS nodes is available if you enable Microsoft Defender for Servers and its Log Analytics agent. However, if your cluster is deployed on an Azure Kubernetes Service virtual machine scale set, the Log Analytics agent isn't currently supported.
Availability
Important
Microsoft Defender for Kubernetes has been replaced with Microsoft Defender for Containers. If you've already enabled Defender for Kubernetes on a subscription, you can continue to use it. However, you won't get Defender for Containers' improvements and new features.
This plan is no longer available for subscriptions where it isn't already enabled.
To upgrade to Microsoft Defender for Containers, open the Defender plans page in the portal and enable the new plan:
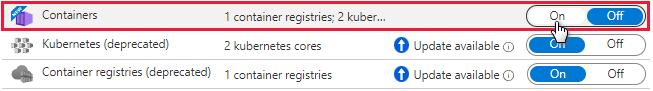
Learn more about this change in the release note.
| Aspect | Details |
|---|---|
| Release state: | Deprecated (Use Microsoft Defender for Containers) |
| Required roles and permissions: | Security admin can dismiss alerts. Security reader can view findings. |
| Clouds: |
What are the benefits of Microsoft Defender for Kubernetes?
Our global team of security researchers constantly monitor the threat landscape. As container-specific alerts and vulnerabilities are discovered, these researchers add them to our threat intelligence feeds and Defender for Cloud alerts you to any that are relevant for your environment.
In addition, Microsoft Defender for Kubernetes provides cluster-level threat protection by monitoring your clusters' logs. This means that security alerts are only triggered for actions and deployments that occur after you've enabled Defender for Kubernetes on your subscription.
Examples of security events that Microsoft Defenders for Kubernetes monitors include:
- Exposed Kubernetes dashboards
- Creation of high privileged roles
- Creation of sensitive mounts.
For a full list of the cluster level alerts, see alerts with "K8S_" prefix in the alert type in the reference table of alerts.
FAQ - Microsoft Defender for Kubernetes
- What happens to subscriptions with Microsoft Defender for Kubernetes or Microsoft Defender for Containers enabled?
- Is Defender for Containers a mandatory upgrade?
- How can I calculate my potential price change?
What happens to subscriptions with Microsoft Defender for Kubernetes or Microsoft Defender for Containers enabled?
Subscriptions that already have one of these plans enabled can continue to benefit from it.
If you haven't enabled them yet, or create a new subscription, these plans can no longer be enabled.
Is Defender for Containers a mandatory upgrade?
No. Subscriptions that have either Microsoft Defender for Kubernetes or Microsoft Defender for Containers Registries enabled doesn't need to be upgraded to the new Microsoft Defender for Containers plan. However, they won't benefit from the new and improved capabilities and they’ll have an upgrade icon shown alongside them in the Azure portal.
How can I calculate my potential price change?
In order to help you understand your costs, Defender for Cloud offers the Price Estimation workbook as part of its published Workbooks. The Price Estimation workbook allows you to estimate the expected price for Defender for Cloud plans before enabling them.
Your price is dependent on your container architecture and coverage. Learn how to enable and use the Price Estimation workbook.
Next steps
In this article, you learned about Kubernetes protection in Defender for Cloud, including Microsoft Defender for Kubernetes.
For related material, see the following articles: