Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Defender for Cloud can scan machines and cloud deployments for supported secrets, to reduce lateral movement risk.
This article helps you to identify and remediate machine secrets scan findings.
- You can review and remediate findings using machine secrets recommendations.
- View secrets discovered on a specific machine in the Defender for Cloud inventory
- Drill down into machine secrets findings using cloud security explorer queries and machine secrets attack paths
- Not every method is supported for every secret. Review the supported methods for different types of secrets.
It’s important to be able to prioritize secrets and identify which ones need immediate attention. To help you do this, Defender for Cloud provides:
- Providing rich metadata for every secret, such as last access time for a file, a token expiration date, an indication whether the target resource that the secrets provide access to exists, and more.
- Combining secrets metadata with cloud assets context. This helps you to start with assets that are exposed to the internet, or contain secrets that might compromise other sensitive assets. Secrets scanning findings are incorporated into risk-based recommendation prioritization.
- Providing multiple views to help you pinpoint the mostly commonly found secrets, or assets containing secrets.
Prerequisites
- An Azure account. If you don't already have an Azure account, you can create your Azure free account today.
- Defender for Cloud must be available in your Azure subscription.
- At least one of these plans must be enabled:
- Agentless machine scanning must be enabled.
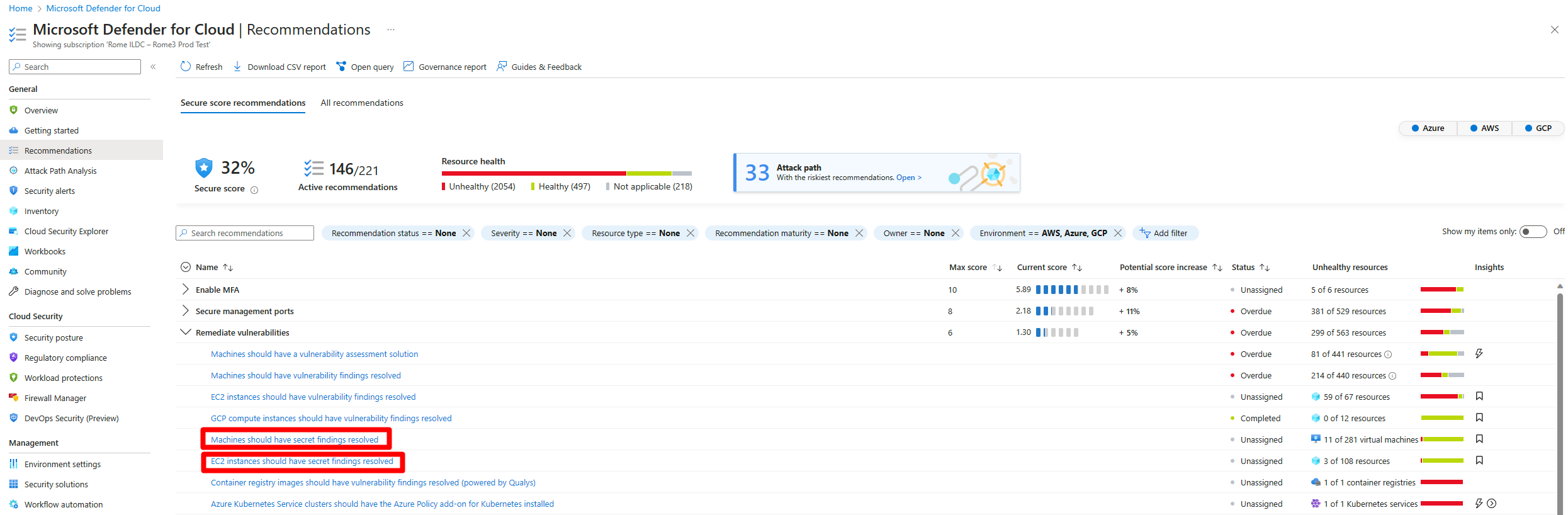
Remediate secrets with recommendations
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Recommendations.
Expand the Remediate vulnerabilities security control.
Select one of the relevant recommendations:
Expand Affected resources to review the list of all resources that contain secrets.
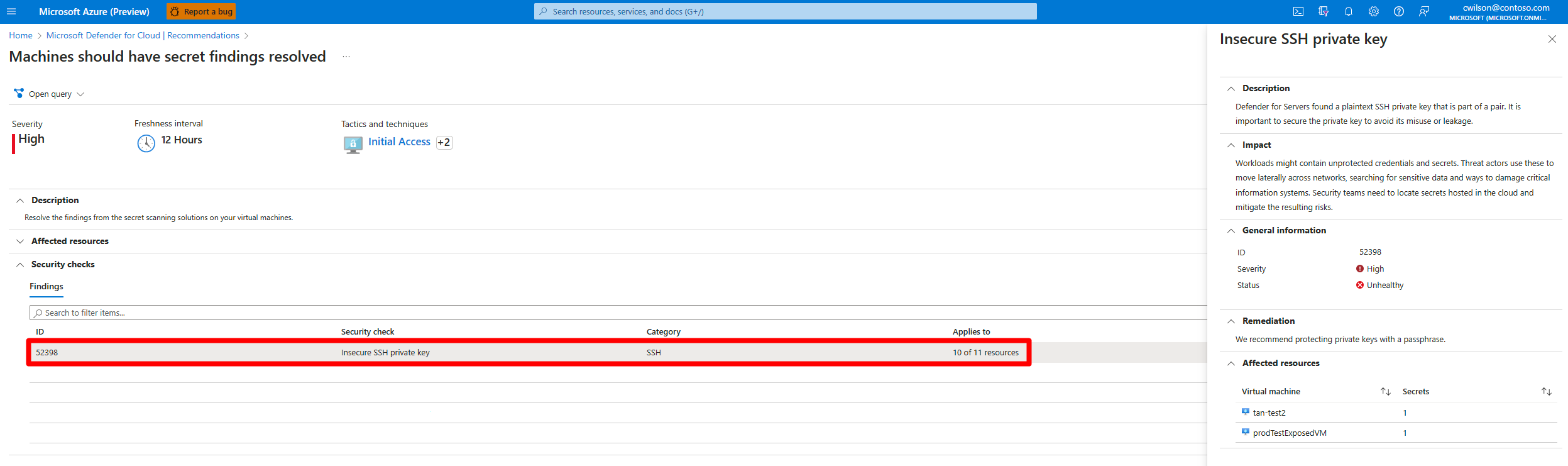
In the Findings section, select a secret to view detailed information about the secret.
Expand Remediation steps and follow the listed steps.
Expand Affected resources to review the resources affected by this secret.
(Optional) You can select an affected resource to see the resource's information.
Secrets that don't have a known attack path are referred to as secrets without an identified target resource.
Remediate secrets for a machine in the inventory
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Inventory.
Select the relevant VM.
Go to the Secrets tab.
Review each plaintext secret that appears with the relevant metadata.
Select a secret to view extra details of that secret.
Different types of secrets have different sets of additional information. For example, for plaintext SSH private keys, the information includes related public keys (mapping between the private key to the authorized keys’ file we discovered or mapping to a different virtual machine that contains the same SSH private key identifier).
Remediate secrets with attack paths
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Recommendations > Attack path.
Select the relevant attack path.
Follow the remediation steps to remediate the attack path.
Remediate secrets with cloud security explorer
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Cloud Security Explorer.
Select one of the following templates:
- VM with plaintext secret that can authenticate to another VM - Returns all Azure VMs, AWS EC2 instances, or GCP VM instances with plaintext secret that can access other VMs or EC2s.
- VM with plaintext secret that can authenticate to a storage account - Returns all Azure VMs, AWS EC2 instances, or GCP VM instances with plaintext secret that can access storage accounts.
- VM with plaintext secret that can authenticate to an SQL database - Returns all Azure VMs, AWS EC2 instances, or GCP VM instances with plaintext secret that can access SQL databases.
If you don't want to use any of the available templates, you can also build your own query in the cloud security explorer.