Enable vulnerability assessment on your Azure SQL databases
In this article, you learn how to enable vulnerability assessment so you can find and remediate database vulnerabilities. We recommend that you enable vulnerability assessment using the express configuration so you aren't dependent on a storage account. You can also enable vulnerability assessment using the classic configuration.
Prerequisites
- Make sure that Microsoft Defender for Azure SQL is enabled so that you can run scans on your Azure SQL databases.
- Make sure you read and understand the differences between the express and classic configuration.
Enable vulnerability assessment
When you enable the Defender for Azure SQL plan in Defender for Cloud, Defender for Cloud automatically enables Advanced Threat Protection and vulnerability assessment with the express configuration for all Azure SQL databases in the selected subscription.
If you have Azure SQL databases with vulnerability assessment enabled in the classic configuration, you can enable the express configuration so that assessments don't require a storage account.
If you have Azure SQL databases with vulnerability assessment disabled, you can enable vulnerability assessment in the express or classic configuration.
You enable vulnerability assessment in one of two ways:
Express configuration
To enable vulnerability assessment without a storage account, using the express configuration:
Sign in to the Azure portal.
Open the specific Azure SQL Database resource.
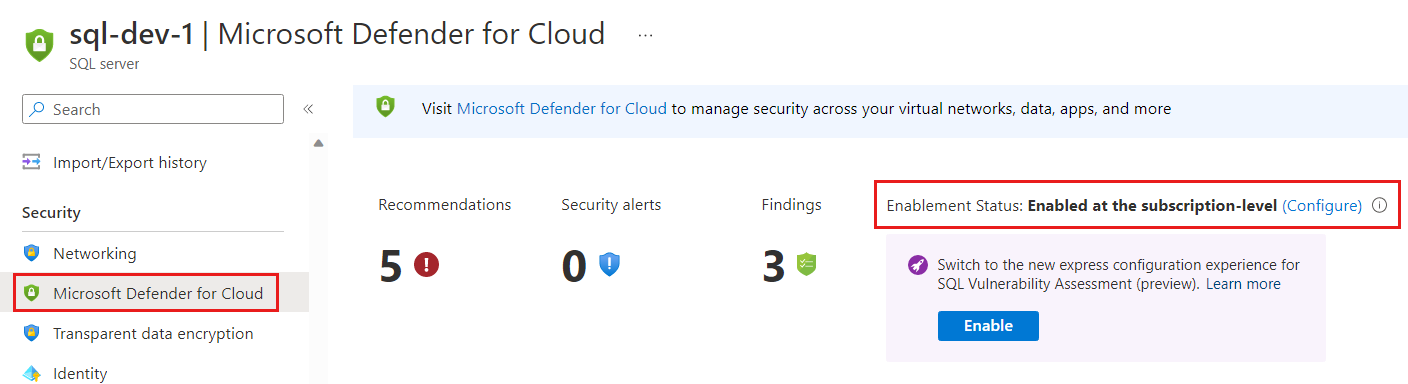
Under the Security heading, select Defender for Cloud.
Enable the express configuration of vulnerability assessment:
If vulnerability assessment is not configured, select Enable in the notice that prompts you to enable the vulnerability assessment express configuration, and confirm the change.
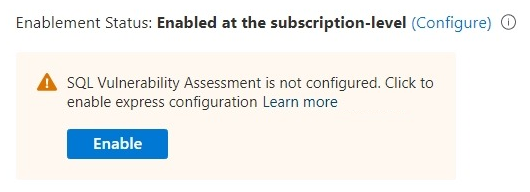
You can also select Configure and then select Enable in the Microsoft Defender for SQL settings:
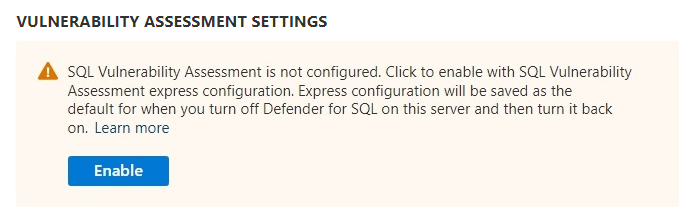
Select Enable to use the vulnerability assessment express configuration.
If vulnerability assessment is already configured, select Enable in the notice that prompts you to switch to express configuration, and confirm the change.
Important
Baselines and scan history are not migrated.
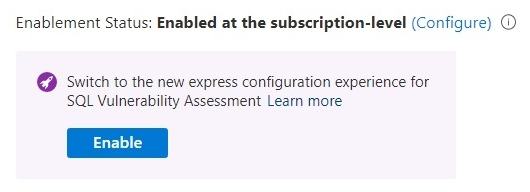
You can also select Configure and then select Enable in the Microsoft Defender for SQL settings:
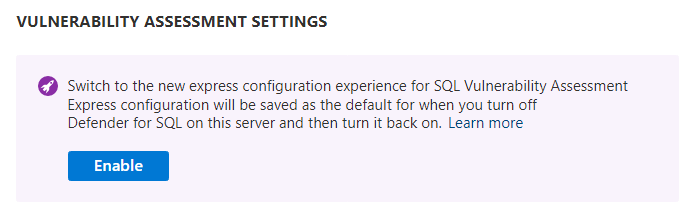
Now you can go to the SQL databases should have vulnerability findings resolved recommendation to see the vulnerabilities found in your databases. You can also run on-demand vulnerability assessment scans to see the current findings.
Note
Each database is randomly assigned a scan time on a set day of the week.
Enable express vulnerability assessment at scale
If you have SQL resources that don't have Advanced Threat Protection and vulnerability assessment enabled, you can use the SQL vulnerability assessment APIs to enable SQL vulnerability assessment with the express configuration at scale.
Classic configuration
To enable vulnerability assessment with a storage account, use the classic configuration:
In the Azure portal, open the specific resource in Azure SQL Database, SQL Managed Instance Database, or Azure Synapse.
Under the Security heading, select Defender for Cloud.
Select Configure on the link to open the Microsoft Defender for SQL settings pane for either the entire server or managed instance.
In the Server settings page, enter the Microsoft Defender for SQL settings:
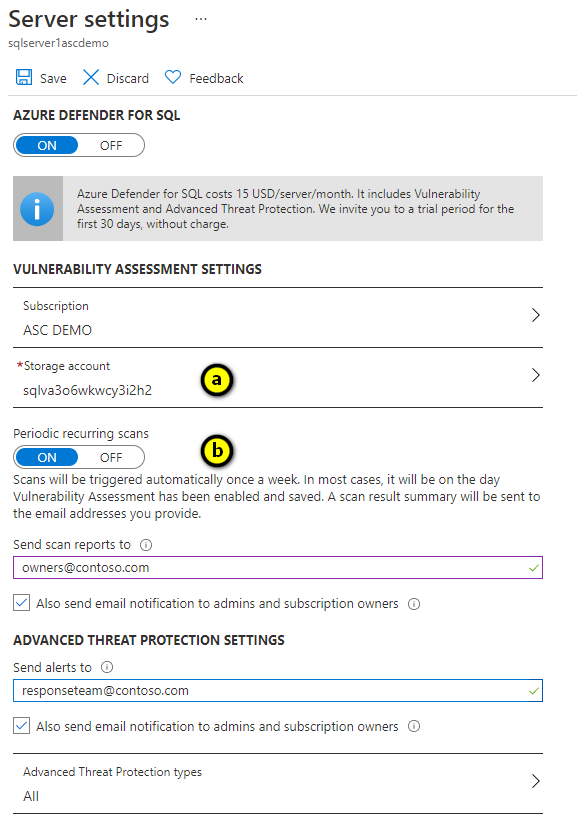
Configure a storage account where your scan results for all databases on the server or managed instance will be stored. For information about storage accounts, see About Azure storage accounts.
To configure vulnerability assessments to automatically run weekly scans to detect security misconfigurations, set Periodic recurring scans to On. The results are sent to the email addresses you provide in Send scan reports to. You can also send email notification to admins and subscription owners by enabling Also send email notification to admins and subscription owners.
Note
Each database is randomly assigned a scan time on a set day of the week. Email notifications are scheduled randomly per server on a set day of the week. The email notification report includes data from all recurring database scans that were executed during the preceding week (does not include on-demand scans).
Related content
Learn more about: