Containers support matrix in Defender for Cloud
Caution
This article references CentOS, a Linux distribution that is nearing End Of Life (EOL) status. Please consider your use and planning accordingly. For more information, see the CentOS End Of Life guidance.
This article summarizes support information for Container capabilities in Microsoft Defender for Cloud.
Note
- Specific features are in preview. The Azure Preview Supplemental Terms include other legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
- Only the versions of AKS, EKS and GKE supported by the cloud vendor are officially supported by Defender for Cloud.
Important
The Defender for Cloud Containers Vulnerability Assessment powered by Qualys is being retired. The retirement will be completed by March 6, and until that time partial results may still appear both in the Qualys recommendations, and Qualys results in the security graph. Any customers who were previously using this assessment should upgrade to to Vulnerability assessments for Azure with Microsoft Defender Vulnerability Management. For information about transitioning to the container vulnerability assessment offering powered by Microsoft Defender Vulnerability Management, see Transition from Qualys to Microsoft Defender Vulnerability Management.
Azure
Following are the features for each of the domains in Defender for Containers:
Security posture management
| Feature | Description | Supported resources | Linux release state | Windows release state | Enablement method | Sensor | Plans | Azure clouds availability |
|---|---|---|---|---|---|---|---|---|
| Agentless discovery for Kubernetes | Provides zero footprint, API-based discovery of Kubernetes clusters, their configurations and deployments. | AKS | GA | GA | Enable Agentless discovery on Kubernetes toggle | Agentless | Defender for Containers OR Defender CSPM | Azure commercial clouds |
| Comprehensive inventory capabilities | Enables you to explore resources, pods, services, repositories, images, and configurations through security explorer to easily monitor and manage your assets. | ACR, AKS | GA | GA | Enable Agentless discovery on Kubernetes toggle | Agentless | Defender for Containers OR Defender CSPM | Azure commercial clouds |
| Attack path analysis | A graph-based algorithm that scans the cloud security graph. The scans expose exploitable paths that attackers might use to breach your environment. | ACR, AKS | GA | GA | Activated with plan | Agentless | Defender CSPM (requires Agentless discovery for Kubernetes to be enabled) | Azure commercial clouds |
| Enhanced risk-hunting | Enables security admins to actively hunt for posture issues in their containerized assets through queries (built-in and custom) and security insights in the security explorer. | ACR, AKS | GA | GA | Enable Agentless discovery on Kubernetes toggle | Agentless | Defender for Containers OR Defender CSPM | Azure commercial clouds |
| Control plane hardening | Continuously assesses the configurations of your clusters and compares them with the initiatives applied to your subscriptions. When it finds misconfigurations, Defender for Cloud generates security recommendations that are available on Defender for Cloud's Recommendations page. The recommendations let you investigate and remediate issues. | ACR, AKS | GA | Preview | Activated with plan | Agentless | Free | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Kubernetes data plane hardening | Protect workloads of your Kubernetes containers with best practice recommendations. | AKS | GA | - | Enable Azure Policy for Kubernetes toggle | Azure Policy | Free | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Docker CIS | Docker CIS benchmark | VM, Virtual Machine Scale Set | GA | - | Enabled with plan | Log Analytics agent | Defender for Servers Plan 2 | Commercial clouds National clouds: Azure Government, Microsoft Azure operated by 21Vianet |
Vulnerability assessment
| Feature | Description | Supported resources | Linux release state | Windows release state | Enablement method | Sensor | Plans | Azure clouds availability |
|---|---|---|---|---|---|---|---|---|
| Agentless registry scan (powered by Microsoft Defender Vulnerability Management) supported packages | Vulnerability assessment for images in ACR | ACR, Private ACR | GA | GA | Enable Agentless container vulnerability assessment toggle | Agentless | Defender for Containers or Defender CSPM | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Agentless/agent-based runtime (powered by Microsoft Defender Vulnerability Management) supported packages | Vulnerability assessment for running images in AKS | AKS | GA | GA | Enable Agentless container vulnerability assessment toggle | Agentless (Requires Agentless discovery for Kubernetes) OR/AND Defender sensor | Defender for Containers or Defender CSPM | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
Runtime threat protection
| Feature | Description | Supported resources | Linux release state | Windows release state | Enablement method | Sensor | Plans | Azure clouds availability |
|---|---|---|---|---|---|---|---|---|
| Control plane | Detection of suspicious activity for Kubernetes based on Kubernetes audit trail | AKS | GA | GA | Enabled with plan | Agentless | Defender for Containers | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Workload | Detection of suspicious activity for Kubernetes for cluster level, node level, and workload level | AKS | GA | - | Enable Defender Sensor in Azure toggle OR deploy Defender sensors on individual clusters | Defender sensor | Defender for Containers | Commercial clouds National clouds: Azure Government, Azure China 21Vianet |
Deployment & monitoring
| Feature | Description | Supported resources | Linux release state | Windows release state | Enablement method | Sensor | Plans | Azure clouds availability |
|---|---|---|---|---|---|---|---|---|
| Discovery of unprotected clusters | Discovering Kubernetes clusters missing Defender sensors | AKS | GA | GA | Enabled with plan | Agentless | Free | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Defender sensor auto provisioning | Automatic deployment of Defender sensor | AKS | GA | - | Enable Defender Sensor in Azure toggle | Agentless | Defender for Containers | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
| Azure Policy for Kubernetes auto provisioning | Automatic deployment of Azure policy sensor for Kubernetes | AKS | GA | - | Enable Azure policy for Kubernetes toggle | Agentless | Free | Commercial clouds National clouds: Azure Government, Azure operated by 21Vianet |
Registries and images support for Azure - Vulnerability assessment powered by Microsoft Defender Vulnerability Management
| Aspect | Details |
|---|---|
| Registries and images | Supported • ACR registries • ACR registries protected with Azure Private Link (Private registries requires access to Trusted Services) • Container images in Docker V2 format • Images with Open Container Initiative (OCI) image format specification Unsupported • Super-minimalist images such as Docker scratch images is currently unsupported |
| Operating systems | Supported • Alpine Linux 3.12-3.19 • Red Hat Enterprise Linux 6-9 • CentOS 6-9 • Oracle Linux 6-9 • Amazon Linux 1, 2 • openSUSE Leap, openSUSE Tumbleweed • SUSE Enterprise Linux 11-15 • Debian GNU/Linux 7-12 • Google Distroless (based on Debian GNU/Linux 7-12) • Ubuntu 12.04-22.04 • Fedora 31-37 • Mariner 1-2 • Windows Server 2016, 2019, 2022 |
| Language specific packages |
Supported • Python • Node.js • .NET • JAVA • Go |
Kubernetes distributions and configurations for Azure - Runtime threat protection
| Aspect | Details |
|---|---|
| Kubernetes distributions and configurations | Supported • Azure Kubernetes Service (AKS) with Kubernetes RBAC Supported via Arc enabled Kubernetes 1 2 • Azure Kubernetes Service hybrid • Kubernetes • AKS Engine • Azure Red Hat OpenShift |
1 Any Cloud Native Computing Foundation (CNCF) certified Kubernetes clusters should be supported, but only the specified clusters have been tested on Azure.
2 To get Microsoft Defender for Containers protection for your environments, you need to onboard Azure Arc-enabled Kubernetes and enable Defender for Containers as an Arc extension.
Note
For additional requirements for Kubernetes workload protection, see existing limitations.
Private link restrictions
Defender for Containers relies on the Defender sensor for several features. The Defender sensor doesn't support the ability to ingest data through Private Link. You can disable public access for ingestion, so that only machines that are configured to send traffic through Azure Monitor Private Link can send data to that workstation. You can configure a private link by navigating to your workspace > Network Isolation and setting the Virtual networks access configurations to No.
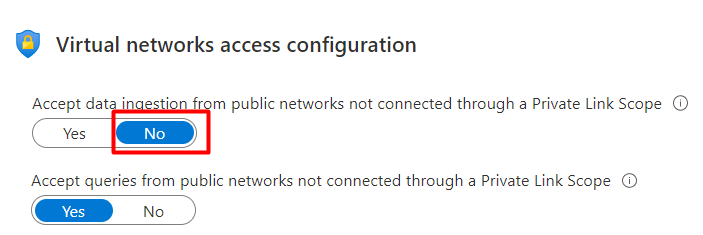
Allowing data ingestion to occur only through Private Link Scope on your workspace Network Isolation settings, can result in communication failures and partial converge of the Defender for Containers feature set.
Learn how to use Azure Private Link to connect networks to Azure Monitor.
AWS
| Domain | Feature | Supported Resources | Linux release state | Windows release state | Agentless/Sensor-based | Pricing tier |
|---|---|---|---|---|---|---|
| Security posture management | Agentless discovery for Kubernetes | EKS | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Comprehensive inventory capabilities | ECR, EKS | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Attack path analysis | ECR, EKS | GA | GA | Agentless | Defender CSPM |
| Security posture management | Enhanced risk-hunting | ECR, EKS | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Docker CIS | EC2 | GA | - | Log Analytics agent | Defender for Servers Plan 2 |
| Security posture management | Control plane hardening | - | - | - | - | - |
| Security posture management | Kubernetes data plane hardening | EKS | GA | - | Azure Policy for Kubernetes | Defender for Containers |
| Vulnerability assessment | Agentless registry scan (powered by Microsoft Defender Vulnerability Management) supported packages | ECR | GA | GA | Agentless | Defender for Containers or Defender CSPM |
| Vulnerability assessment | Agentless/sensor-based runtime (powered by Microsoft Defender Vulnerability Management) supported packages | EKS | GA | GA | Agentless OR/AND Defender sensor | Defender for Containers or Defender CSPM |
| Runtime protection | Control plane | EKS | GA | GA | Agentless | Defender for Containers |
| Runtime protection | Workload | EKS | GA | - | Defender sensor | Defender for Containers |
| Deployment & monitoring | Discovery of unprotected clusters | EKS | GA | GA | Agentless | Defender for Containers |
| Deployment & monitoring | Auto provisioning of Defender sensor | EKS | GA | - | - | - |
| Deployment & monitoring | Auto provisioning of Azure Policy for Kubernetes | EKS | GA | - | - | - |
Registries and images support for AWS - Vulnerability assessment powered by Microsoft Defender Vulnerability Management
| Aspect | Details |
|---|---|
| Registries and images | Supported • ECR registries • Container images in Docker V2 format • Images with Open Container Initiative (OCI) image format specification Unsupported • Super-minimalist images such as Docker scratch images is currently unsupported • Public repositories • Manifest lists |
| Operating systems | Supported • Alpine Linux 3.12-3.19 • Red Hat Enterprise Linux 6-9 • CentOS 6-9 • Oracle Linux 6-9 • Amazon Linux 1, 2 • openSUSE Leap, openSUSE Tumbleweed • SUSE Enterprise Linux 11-15 • Debian GNU/Linux 7-12 • Google Distroless (based on Debian GNU/Linux 7-12) • Ubuntu 12.04-22.04 • Fedora 31-37 • Mariner 1-2 • Windows server 2016, 2019, 2022 |
| Language specific packages |
Supported • Python • Node.js • .NET • JAVA • Go |
Kubernetes distributions/configurations support for AWS - Runtime threat protection
| Aspect | Details |
|---|---|
| Kubernetes distributions and configurations | Supported • Amazon Elastic Kubernetes Service (EKS) Supported via Arc enabled Kubernetes 1 2 • Kubernetes Unsupported • EKS private clusters |
1 Any Cloud Native Computing Foundation (CNCF) certified Kubernetes clusters should be supported, but only the specified clusters have been tested.
2 To get Microsoft Defender for Containers protection for your environments, you need to onboard Azure Arc-enabled Kubernetes and enable Defender for Containers as an Arc extension.
Note
For additional requirements for Kubernetes workload protection, see existing limitations.
Outbound proxy support - AWS
Outbound proxy without authentication and outbound proxy with basic authentication are supported. Outbound proxy that expects trusted certificates is currently not supported.
GCP
| Domain | Feature | Supported Resources | Linux release state | Windows release state | Agentless/Sensor-based | Pricing tier |
|---|---|---|---|---|---|---|
| Security posture management | Agentless discovery for Kubernetes | GKE | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Comprehensive inventory capabilities | GAR, GCR, GKE | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Attack path analysis | GAR, GCR, GKE | GA | GA | Agentless | Defender CSPM |
| Security posture management | Enhanced risk-hunting | GAR, GCR, GKE | GA | GA | Agentless | Defender for Containers OR Defender CSPM |
| Security posture management | Docker CIS | GCP VMs | GA | - | Log Analytics agent | Defender for Servers Plan 2 |
| Security posture management | Control plane hardening | GKE | GA | GA | Agentless | Free |
| Security posture management | Kubernetes data plane hardening | GKE | GA | - | Azure Policy for Kubernetes | Defender for Containers |
| Vulnerability assessment | Agentless registry scan (powered by Microsoft Defender Vulnerability Management) supported packages | GAR, GCR | GA | GA | Agentless | Defender for Containers or Defender CSPM |
| Vulnerability assessment | Agentless/sensor-based runtime (powered by Microsoft Defender Vulnerability Management) supported packages | GKE | GA | GA | Agentless OR/AND Defender sensor | Defender for Containers or Defender CSPM |
| Runtime protection | Control plane | GKE | GA | GA | Agentless | Defender for Containers |
| Runtime protection | Workload | GKE | GA | - | Defender sensor | Defender for Containers |
| Deployment & monitoring | Discovery of unprotected clusters | GKE | GA | GA | Agentless | Defender for Containers |
| Deployment & monitoring | Auto provisioning of Defender sensor | GKE | GA | - | Agentless | Defender for Containers |
| Deployment & monitoring | Auto provisioning of Azure Policy for Kubernetes | GKE | GA | - | Agentless | Defender for Containers |
Registries and images support for GCP - Vulnerability assessment powered by Microsoft Defender Vulnerability Management
| Aspect | Details |
|---|---|
| Registries and images | Supported • Google Registries (GAR, GCR) • Container images in Docker V2 format • Images with Open Container Initiative (OCI) image format specification Unsupported • Super-minimalist images such as Docker scratch images is currently unsupported • Public repositories • Manifest lists |
| Operating systems | Supported • Alpine Linux 3.12-3.19 • Red Hat Enterprise Linux 6-9 • CentOS 6-9 • Oracle Linux 6-9 • Amazon Linux 1, 2 • openSUSE Leap, openSUSE Tumbleweed • SUSE Enterprise Linux 11-15 • Debian GNU/Linux 7-12 • Google Distroless (based on Debian GNU/Linux 7-12) • Ubuntu 12.04-22.04 • Fedora 31-37 • Mariner 1-2 • Windows server 2016, 2019, 2022 |
| Language specific packages |
Supported • Python • Node.js • .NET • JAVA • Go |
Kubernetes distributions/configurations support for GCP - Runtime threat protection
| Aspect | Details |
|---|---|
| Kubernetes distributions and configurations | Supported • Google Kubernetes Engine (GKE) Standard Supported via Arc enabled Kubernetes 1 2 • Kubernetes Unsupported • Private network clusters • GKE autopilot • GKE AuthorizedNetworksConfig |
1 Any Cloud Native Computing Foundation (CNCF) certified Kubernetes clusters should be supported, but only the specified clusters have been tested.
2 To get Microsoft Defender for Containers protection for your environments, you need to onboard Azure Arc-enabled Kubernetes and enable Defender for Containers as an Arc extension.
Note
For additional requirements for Kubernetes workload protection, see existing limitations.
Outbound proxy support - GCP
Outbound proxy without authentication and outbound proxy with basic authentication are supported. Outbound proxy that expects trusted certificates is currently not supported.
On-premises, Arc-enabled Kubernetes clusters
| Domain | Feature | Supported Resources | Linux release state | Windows release state | Agentless/Sensor-based | Pricing tier |
|---|---|---|---|---|---|---|
| Security posture management | Docker CIS | Arc enabled VMs | Preview | - | Log Analytics agent | Defender for Servers Plan 2 |
| Security posture management | Control plane hardening | - | - | - | - | - |
| Security posture management | Kubernetes data plane hardening | Arc enabled K8s clusters | GA | - | Azure Policy for Kubernetes | Defender for Containers |
| Runtime protection | Threat protection (control plane) | Arc enabled K8s clusters | Preview | Preview | Defender sensor | Defender for Containers |
| Runtime protection | Threat protection (workload) | Arc enabled K8s clusters | Preview | - | Defender sensor | Defender for Containers |
| Deployment & monitoring | Discovery of unprotected clusters | Arc enabled K8s clusters | Preview | - | Agentless | Free |
| Deployment & monitoring | Auto provisioning of Defender sensor | Arc enabled K8s clusters | Preview | Preview | Agentless | Defender for Containers |
| Deployment & monitoring | Auto provisioning of Azure Policy for Kubernetes | Arc enabled K8s clusters | Preview | - | Agentless | Defender for Containers |
Kubernetes distributions and configurations
| Aspect | Details |
|---|---|
| Kubernetes distributions and configurations | Supported via Arc enabled Kubernetes 1 2 • Azure Kubernetes Service hybrid • Kubernetes • AKS Engine • Azure Red Hat OpenShift • Red Hat OpenShift (version 4.6 or newer) • VMware Tanzu Kubernetes Grid • Rancher Kubernetes Engine |
1 Any Cloud Native Computing Foundation (CNCF) certified Kubernetes clusters should be supported, but only the specified clusters have been tested.
2 To get Microsoft Defender for Containers protection for your environments, you need to onboard Azure Arc-enabled Kubernetes and enable Defender for Containers as an Arc extension.
Note
For additional requirements for Kubernetes workload protection, see existing limitations.
Supported host operating systems
Defender for Containers relies on the Defender sensor for several features. The Defender sensor is supported on the following host operating systems:
- Amazon Linux 2
- CentOS 8
- Debian 10
- Debian 11
- Google Container-Optimized OS
- Mariner 1.0
- Mariner 2.0
- Red Hat Enterprise Linux 8
- Ubuntu 16.04
- Ubuntu 18.04
- Ubuntu 20.04
- Ubuntu 22.04
Ensure your Kubernetes node is running on one of the verified supported operating systems. Clusters with different host operating systems, only get partial coverage.
Defender sensor limitations
The Defender sensor in AKS V1.28 and below is not supported on ARM64 nodes.
Network restrictions
Private link
Defender for Containers relies on the Defender sensor for several features. The Defender sensor doesn't support the ability to ingest data through Private Link. You can disable public access for ingestion, so that only machines that are configured to send traffic through Azure Monitor Private Link can send data to that workstation. You can configure a private link by navigating to your workspace > Network Isolation and setting the Virtual networks access configurations to No.

Allowing data ingestion to occur only through Private Link Scope on your workspace Network Isolation settings, can result in communication failures and partial converge of the Defender for Containers feature set.
Learn how to use Azure Private Link to connect networks to Azure Monitor.
Outbound proxy support
Outbound proxy without authentication and outbound proxy with basic authentication are supported. Outbound proxy that expects trusted certificates is currently not supported.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for