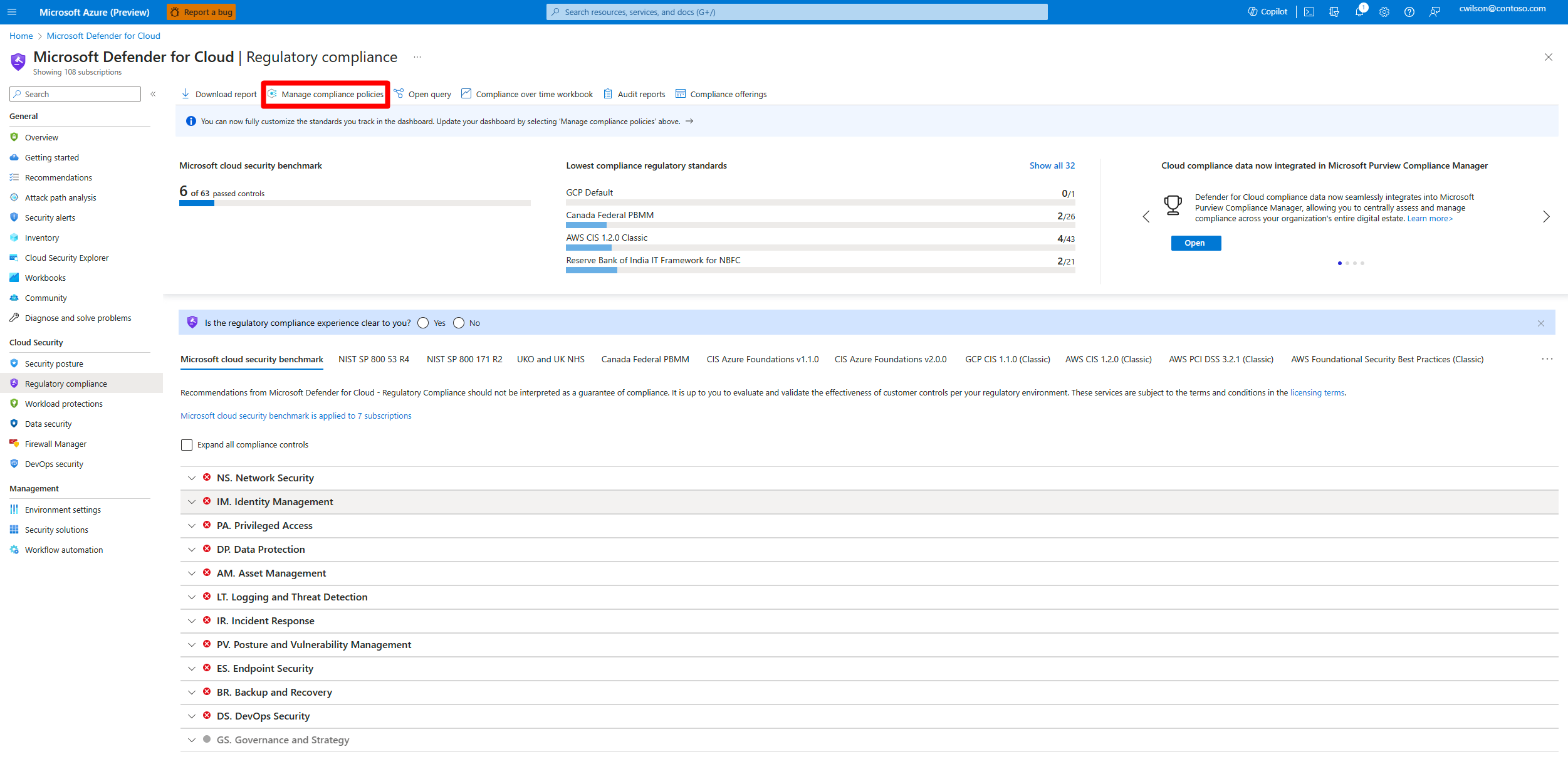
Defender for Cloud's regulatory standards and benchmarks are represented as security standards. Each standard is defined as an initiative in Azure Policy.
In Defender for Cloud, assign security standards to specific scopes such as Azure subscriptions, Amazon Web Services (AWS) accounts, and Google Cloud Platform (GCP) projects with Defender for Cloud enabled.
Defender for Cloud continually assesses the scoped environment against the standards. Based on assessments, it shows whether in-scope resources are compliant or noncompliant with the standard and provides remediation recommendations.
This article explains how to add regulatory compliance standards as security standards in an Azure subscription, AWS account, or GCP project.