General availability of Team automation rules and improved AB# validation
We're excited to announce that improved AB# validation by the Azure Boards App in GitHub and Team Automation rules are generally available! We improved AB# validation so that you can get notified when a link to a work item is not valid. In Team Automation Rules, you can now configure each backlog level to automate the opening and closing/resolving of work items based on the state(s) of the child item.
With this update, we also introduce support for custom CodeQL queries in Code scanning! This will let you craft your own queries tailored to identify issues specific to your codebase.
Check out the release notes for details.
GitHub Advanced Security for Azure DevOps
Azure Boards
- GitHub Integration - Improved AB# validation is generally available
- Team Automation rules is generally available
Azure Pipelines
- Update deprecated tasks before January 31
- Microsoft hosted agents use PowerShell 7.4
- New Azure service connection secrets expire in three months
GitHub Advanced Security for Azure DevOps
Custom CodeQL queries now supported in GitHub Advanced Security for Azure DevOps
We're thrilled to announce the introduction of support for custom CodeQL queries in Code scanning! This enables you to craft your own queries tailored to identify issues specific to your codebase. Now, you can create and publish packs containing custom queries, execute these queries in your pipelines, and customize the detection of vulnerabilities that are pertinent to your organization.
For more information on utilizing custom queries for code scanning in GitHub Advanced Security for Azure DevOps, see to Code scanning alerts for GitHub Advanced Security for Azure DevOps.
We value your input. If you have any questions or feedback, we encourage you to engage with our community at Developer Community.
Azure Boards
GitHub Integration - Improved AB# validation is generally available
A few sprints ago we announced the preview for improved AB# validation by the Azure Boards App in GitHub. We've enhanced the app to better notify users about the validity of work item links, helping them spot and fix any issues before merging a Pull Request.
After several weeks of testing and feedback, this feature is now available to all users using the GitHub + Azure Boards integration.
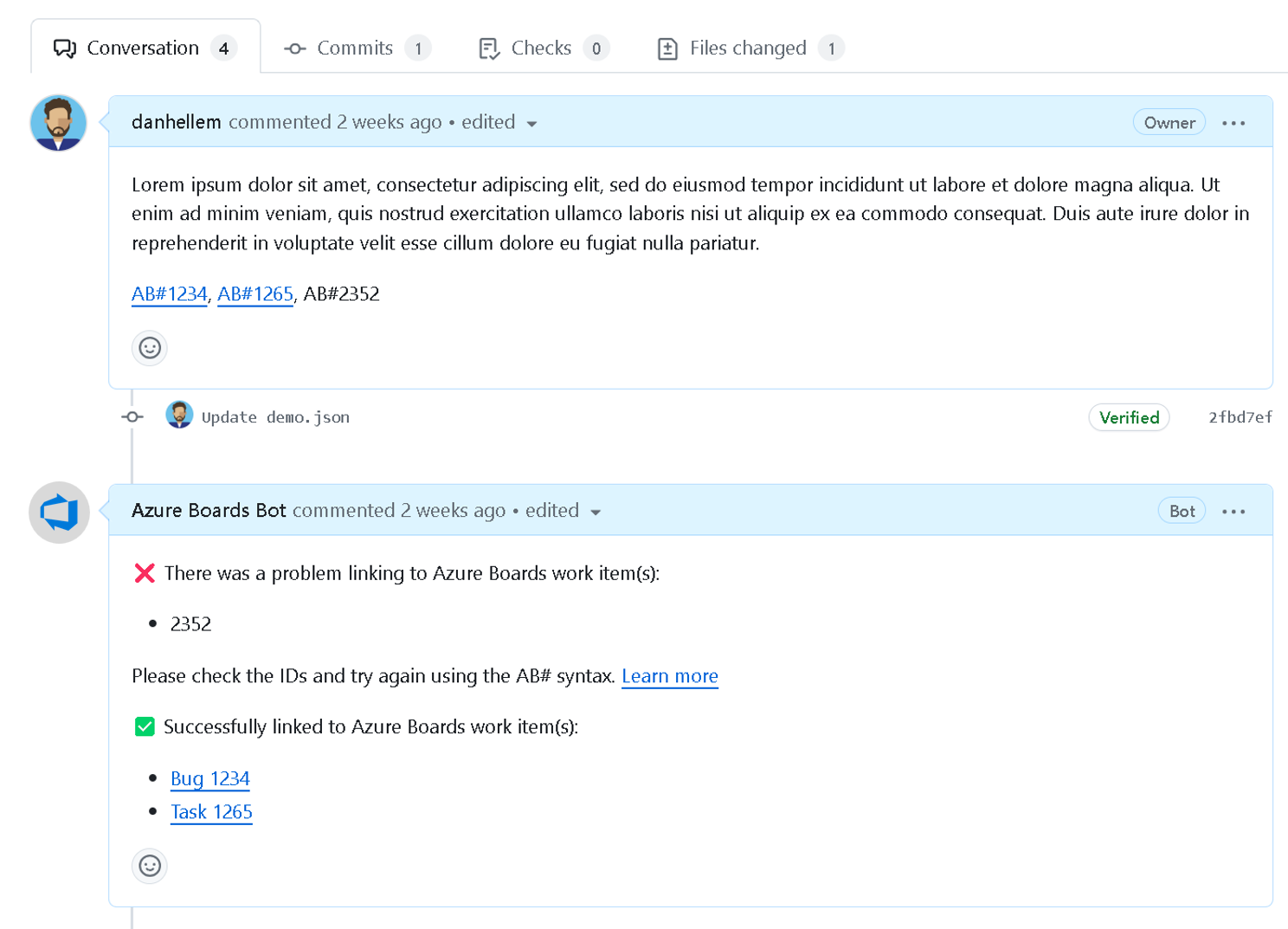
This is the first of several features we're making to improve the current integration. Be sure to check out the other Azure Boards + GitHub integration features we have planned on the public roadmap.
Team Automation Rules is generally available
We're happy to announce the release of this feature to all customers of Azure DevOps Service.
Note
This feature will roll out over the next two to three weeks. It may not be available to your organization until early February 2024.
You can now configure each backlog level to automate the opening and closing (or resolving) of work items based on the state of the child items. There are two main scenarios we're attempting to solve.
- When a single child item is activated, then activate the parent.
- When all child items are closed, then close the parent (or resolve it).
To enable these settings, click on the backlog level configuration for your team. Then go to the Automation > Rules tab to see the two different rules you can apply to your backlog. Each backlog level (requirements, features, epics) can be configured differently depending on how your team wants to work.
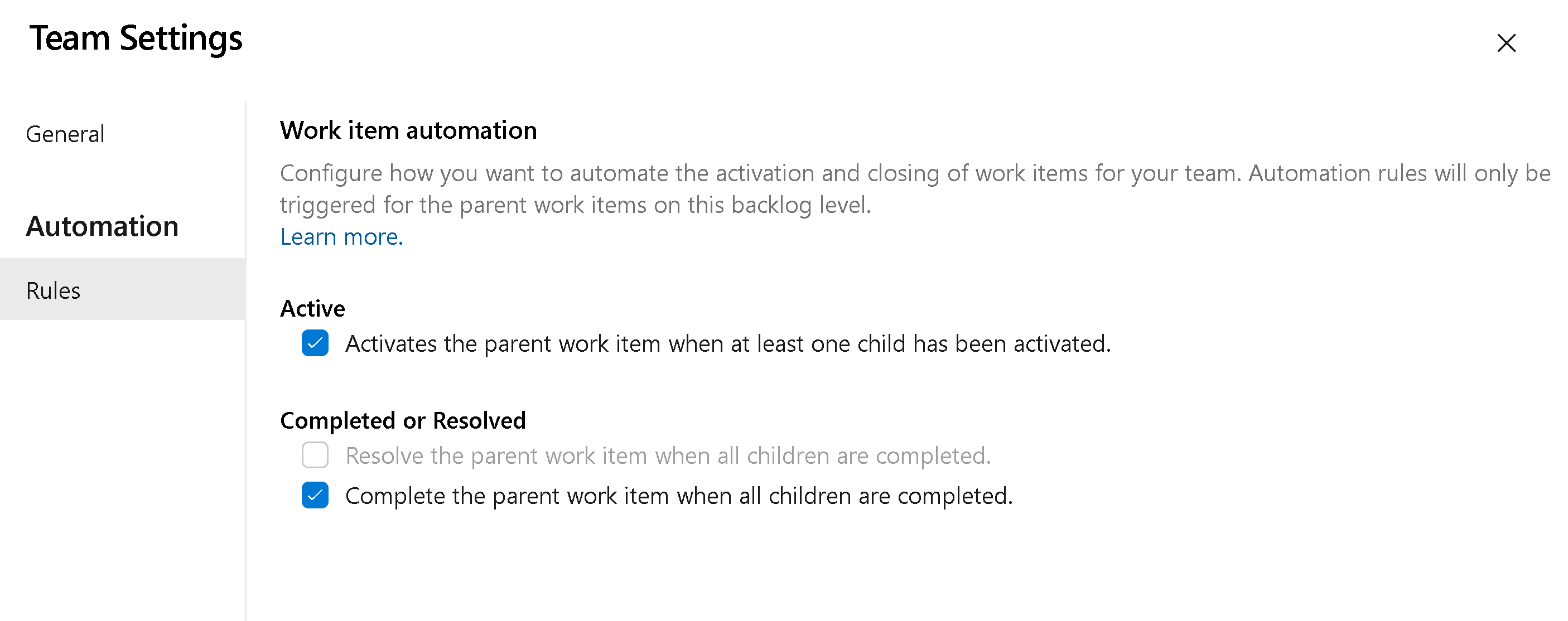
For example, when any child Task is set to Active, make the parent User Story active. Then, when all Tasks are completed, set the User Story to Closed.
You can learn more about this feature by reviewing the documentation and this blog post.
This feature was prioritized based on this Developer Community suggestion ticket.
Azure Pipelines
Update deprecated tasks before January 31
We are retiring deprecated tasks on January 31, 2024. To help you identify the pipelines that are using these tasks, we have included a warning message with a suggested alternative. We encourage you to update your pipelines to use a newer task version or an alternative before January 31, 2024.
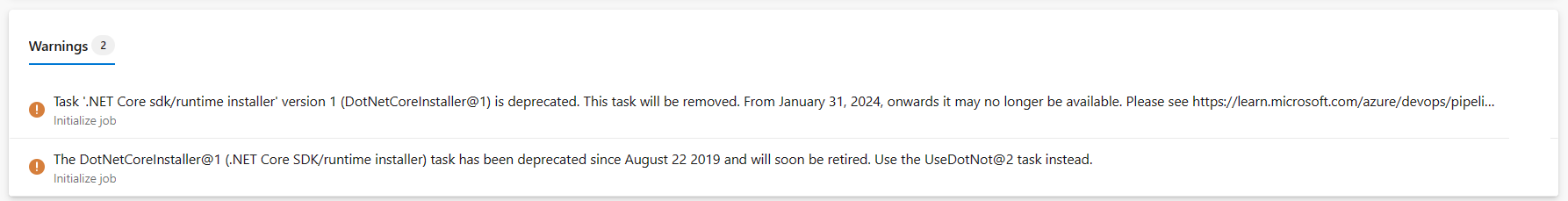
See earlier announcements related to deprecated tasks:
- Announcing retirement of deprecated tasks
- Announcement for NuGet Restore v1 and NuGet Installer v0 pipeline tasks
Microsoft hosted agents use PowerShell 7.4
All Microsoft hosted agents will start using PowerShell 7.2 LTS to PowerShell 7.4 LTS from January 28. See What's New in PowerShell 7.4 and PowerShell 7.4 General Availability.
Take note of breaking changes and update your scripts accordingly:
- Breaking changes between PowerShell 7.3 & 7.4 LTS
- Breaking changes between PowerShell 7.2 LTS & 7.3
- Updated argument parsing behavior controlled via
$PSNativeCommandArgumentPassing. The sample script below enforces the same behavior across Linux, macOS & Windows by setting$PSNativeCommandArgumentPassingexplicitly.
New Azure service connection secrets expire in three months
Azure Service Connections where Azure DevOps creates the secret, will have a secret expiration of three months instead of two years.
To eliminate the need to rotate secrets, convert your service connection to use Workload identity federation instead. You can use the below sample script to quickly convert multiple Azure service connections to Workload identity federation:
#!/usr/bin/env pwsh
<#
.SYNOPSIS
Convert multiple Azure Resource Manager service connection(s) to use Workload identity federation
.LINK
https://aka.ms/azdo-rm-workload-identity-conversion
.EXAMPLE
./convert_azurerm_service_connection_to_oidc_simple.ps1 -Project <project> -OrganizationUrl https://dev.azure.com/<organization>
#>
#Requires -Version 7.3
param (
[parameter(Mandatory=$true,HelpMessage="Name of the Azure DevOps Project")]
[string]
[ValidateNotNullOrEmpty()]
$Project,
[parameter(Mandatory=$true,HelpMessage="Url of the Azure DevOps Organization")]
[uri]
[ValidateNotNullOrEmpty()]
$OrganizationUrl
)
$apiVersion = "7.1"
$PSNativeCommandArgumentPassing = "Standard"
#-----------------------------------------------------------
# Log in to Azure
$azdoResource = "499b84ac-1321-427f-aa17-267ca6975798"
az login --allow-no-subscriptions --scope ${azdoResource}/.default
$OrganizationUrl = $OrganizationUrl.ToString().Trim('/')
#-----------------------------------------------------------
# Retrieve the service connection
$getApiUrl = "${OrganizationUrl}/${Project}/_apis/serviceendpoint/endpoints?authSchemes=ServicePrincipal&type=azurerm&includeFailed=false&includeDetails=true&api-version=${apiVersion}"
az rest --resource $azdoResource -u "${getApiUrl} " -m GET --query "sort_by(value[?authorization.scheme=='ServicePrincipal' && data.creationMode=='Automatic' && !(isShared && serviceEndpointProjectReferences[0].projectReference.name!='${Project}')],&name)" -o json `
| Tee-Object -Variable rawResponse | ConvertFrom-Json | Tee-Object -Variable serviceEndpoints | Format-List | Out-String | Write-Debug
if (!$serviceEndpoints -or ($serviceEndpoints.count-eq 0)) {
Write-Warning "No convertible service connections found"
exit 1
}
foreach ($serviceEndpoint in $serviceEndpoints) {
# Prompt user to confirm conversion
$choices = @(
[System.Management.Automation.Host.ChoiceDescription]::new("&Convert", "Converting service connection '$($serviceEndpoint.name)'...")
[System.Management.Automation.Host.ChoiceDescription]::new("&Skip", "Skipping service connection '$($serviceEndpoint.name)'...")
[System.Management.Automation.Host.ChoiceDescription]::new("&Exit", "Exit script")
)
$prompt = $serviceEndpoint.isShared ? "Convert shared service connection '$($serviceEndpoint.name)'?" : "Convert service connection '$($serviceEndpoint.name)'?"
$decision = $Host.UI.PromptForChoice([string]::Empty, $prompt, $choices, $serviceEndpoint.isShared ? 1 : 0)
if ($decision -eq 0) {
Write-Host "$($choices[$decision].HelpMessage)"
} elseif ($decision -eq 1) {
Write-Host "$($PSStyle.Formatting.Warning)$($choices[$decision].HelpMessage)$($PSStyle.Reset)"
continue
} elseif ($decision -ge 2) {
Write-Host "$($PSStyle.Formatting.Warning)$($choices[$decision].HelpMessage)$($PSStyle.Reset)"
exit
}
# Prepare request body
$serviceEndpoint.authorization.scheme = "WorkloadIdentityFederation"
$serviceEndpoint.data.PSObject.Properties.Remove('revertSchemeDeadline')
$serviceEndpoint | ConvertTo-Json -Depth 4 | Write-Debug
$serviceEndpoint | ConvertTo-Json -Depth 4 -Compress | Set-Variable serviceEndpointRequest
$putApiUrl = "${OrganizationUrl}/${Project}/_apis/serviceendpoint/endpoints/$($serviceEndpoint.id)?operation=ConvertAuthenticationScheme&api-version=${apiVersion}"
# Convert service connection
az rest -u "${putApiUrl} " -m PUT -b $serviceEndpointRequest --headers content-type=application/json --resource $azdoResource -o json `
| ConvertFrom-Json | Set-Variable updatedServiceEndpoint
$updatedServiceEndpoint | ConvertTo-Json -Depth 4 | Write-Debug
if (!$updatedServiceEndpoint) {
Write-Debug "Empty response"
Write-Error "Failed to convert service connection '$($serviceEndpoint.name)'"
exit 1
}
Write-Host "Successfully converted service connection '$($serviceEndpoint.name)'"
}
Next steps
Note
These features will roll out over the next two to three weeks.
Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.
Thanks,
Dan Hellem
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for