Source IP restoration
With a cloud based network proxy between users and their resources, the IP address that the resources see doesn't match the actual source IP address. In place of the end-users’ source IP, the resource endpoints see the cloud proxy as the source IP address. Customers with these cloud proxy solutions can't use this source IP information.
Source IP restoration in Global Secure Access (preview) allows backward compatibility for Microsoft Entra customers to continue using original user Source IP. Administrators can benefit from the following capabilities:
- Continue to enforce Source IP-based location policies across both Conditional Access and continuous access evaluation.
- Identity Protection risk detections get a consistent view of original user Source IP address for assessing various risk scores.
- Original user Source IP is also made available in Microsoft Entra sign-in logs.
Prerequisites
- Administrators who interact with Global Secure Access preview features must have both of the following role assignments depending on the tasks they're performing.
- The Global Secure Access Administrator role to manage the Global Secure Access preview features.
- Conditional Access Administrator or Security Administrator to create and interact with Conditional Access policies and named locations.
- The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses.
Known limitations
When source IP restoration is enabled, you can only see the source IP. The IP address of the Global Secure Access service isn't visible. If you want to see the Global Secure Access service IP address, disable source IP restoration.
Source IP restoration is currently supported for only Microsoft 365 traffic, like SharePoint Online, Exchange Online, Teams, and Microsoft Graph. If you have any IP location-based Conditional Access policies for non-Microsoft 365 resources protected by continuous access evaluation (CAE), these policies aren’t evaluated at the resource as the source IP address isn’t known to the resource.
If you're using CAE’s strict location enforcement, users are blocked despite being in a trusted IP range. To resolve this condition, do one of the following recommendations:
- If you have IP location-based Conditional Access policies targeting non-Microsoft 365 resources, don't enable strict location enforcement.
- Ensure that the traffic is supported by Source IP Restoration, or don't send the relevant traffic through Global Secure Access.
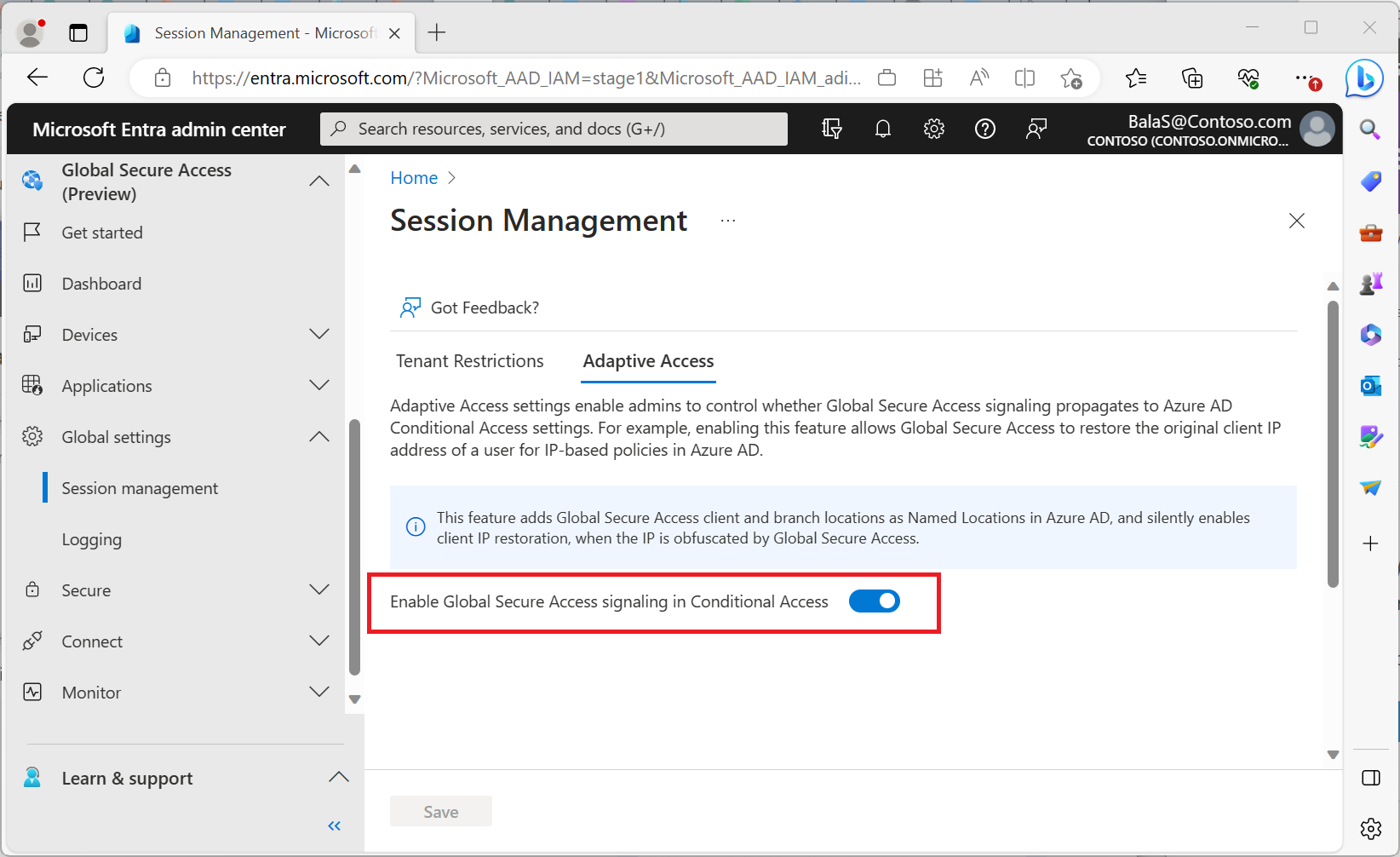
Enable Global Secure Access signaling for Conditional Access
To enable the required setting to allow source IP restoration, an administrator must take the following steps.
- Sign in to the Microsoft Entra admin center as a Global Secure Access Administrator.
- Browse to Global Secure Access > Global settings > Session management > Adaptive Access.
- Select the toggle to Enable Global Secure Access signaling in Conditional Access.
This functionality allows services like Microsoft Graph, Microsoft Entra ID, SharePoint Online, and Exchange Online to see the actual source IP address.
Caution
If your organization has active Conditional Access policies based on IP location checks, and you disable Global Secure Access signaling in Conditional Access, you may unintentionally block targeted end-users from being able to access the resources. If you must disable this feature, first delete any corresponding Conditional Access policies.
Sign-in log behavior
To see source IP restoration in action, administrators can take the following steps.
- Sign in to the Microsoft Entra admin center as at least a Security Reader.
- Browse to Identity > Users > All users > select one of your test users > Sign-in logs.
- With source IP restoration enabled, you see IP addresses that include their actual IP address.
- If source IP restoration is disabled, you can't see their actual IP address.
Sign-in log data might take some time to appear this delay is normal as there's some processing that must take place.
Terms of Use
Your use of the Microsoft Entra Private Access and Microsoft Entra Internet Access preview experiences and features is governed by the preview online service terms and conditions of the agreement(s) under which you obtained the services. Previews may be subject to reduced or different security, compliance, and privacy commitments, as further explained in the Universal License Terms for Online Services and the Microsoft Products and Services Data Protection Addendum (“DPA”), and any other notices provided with the Preview.
Related content
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for
