Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this quickstart, you learn how you can use Azure Log Analytics to create alerts on Azure Resource Graph queries. You can create alerts with Azure Resource Graph query, Log Analytics workspace, and managed identities. The alert's conditions send notifications at a specified interval.
You can use queries to set up alerts for your deployed Azure resources. You can create queries using Azure Resource Graph tables, or you can combine Azure Resource Graph tables and Log Analytics data from Azure Monitor Logs.
In this article's examples, create resources in the same resource group and use the same region, like West US 3. The examples in this article run queries and create alerts for Azure resources in a single Azure tenant. Azure Data Explorer clusters are out of this article's scope.
This article includes two examples of alerts:
- Azure Resource Graph: Uses the Azure Resource Graph
Resourcestable to create a query that gets data for your deployed Azure resources and create an alert. - Azure Resource Graph and Log Analytics: Uses the Azure Resource Graph
Resourcestable and Log Analytics data from the from Azure Monitor LogsHeartbeattable. This example uses a virtual machine to show how to set up the query and alert.
Note
Azure Resource Graph alerts integration with Log Analytics is in public preview.
Prerequisites
- If you don't have an Azure account, create a free account before you begin.
- Resources deployed in Azure like virtual machines or storage accounts.
- To use the example for the Azure Resource Graph and Log Analytics query, you need at least one Azure virtual machine with the Azure Monitor Agent.
Create workspace
Create a Log Analytics Workspace in the subscription that's being monitored.
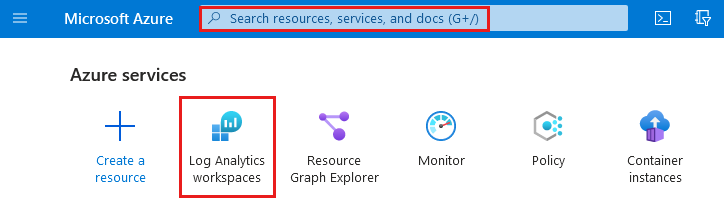
Sign in to the Azure portal.
In the search field, type log analytics workspaces and select Log Analytics workspaces.
If you used Log Analytics workspaces, you can select it from Azure services.
Select Create:
- Subscription: Select your Azure subscription
- Resource group: demo-arg-alert-rg
- Name: demo-arg-alert-workspace
- Region: West US 3
- You can select a different region, but use the same region for other resources.
Select Review + create and wait for Validation passed to be displayed.
Select Create to begin the deployment.
Select Go to resource when the deployment is completed.
Create virtual machine
You don't need to create a virtual machine for the example that uses the Azure Resource Graph table.
Create query
From the Log Analytics workspace, create an Azure Resource Graph query to get a count of your Azure resources. This example uses the Azure Resource Graph Resources table.
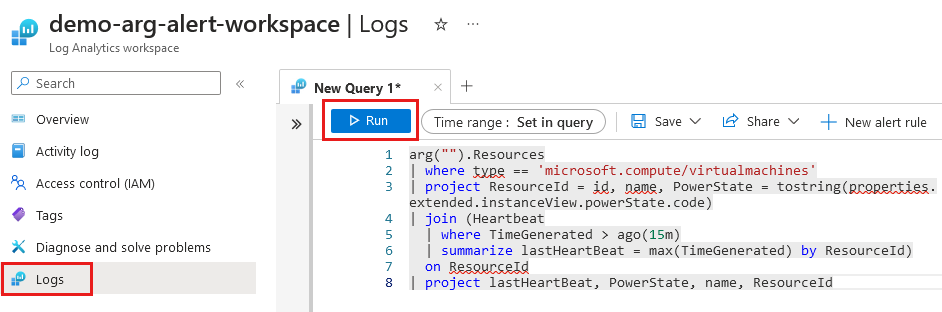
Select Logs from the left side of the Log Analytics workspace page. Close the Queries window if displayed.
Use the following code in the New Query:
arg("").Resources | countTable names in Log Analytics need to be camel case with the first letter of each word capitalized, like
ResourcesorResourceContainers. You can also use lowercase likeresourcesorresourcecontainers.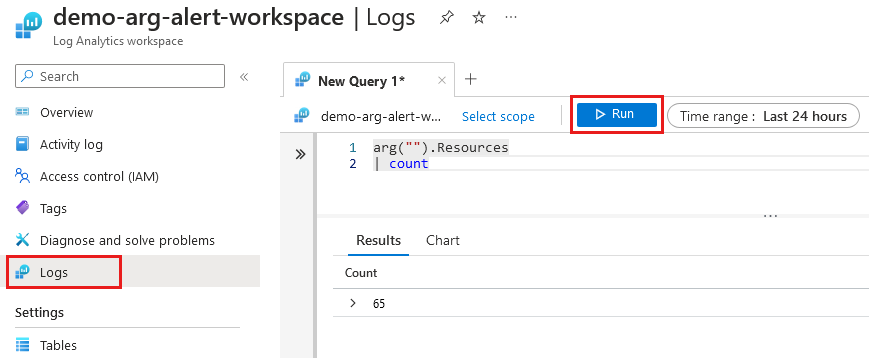
Select Run.
The Results displays the Count of resources in your Azure subscription. Make a note of that number because you need it for the alert rule's condition. When you manually run the query the count is based on user identity, and a fired alert uses a managed identity. It's possible that the count might vary between a manual run or fired alert.
Remove the count from your query.
arg("").Resources
Create alert rule
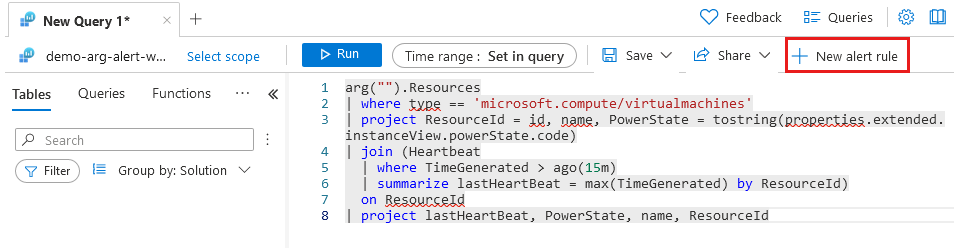
From the Log Analytics workspace, select New alert rule. The query from your Log Analytics workspace is copied to the alert rule. Create an alert rule has several tabs that need to be updated to create the alert.
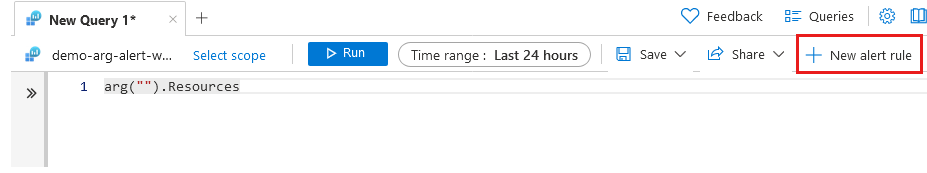
Scope
Verify that the scope defaults to your Log Analytics workspace named demo-arg-alert-workspace.
Only if your scope isn't set to the default, do the following steps:
- Go to the Scope tab and select Select scope.
- At the bottom of the Selected resources screen, remove the current scope.
- Select the option to Select scope.
- Expand the demo-arg-alert-rg from the list of resources and select demo-arg-alert-workspace.
- Select Apply.
- Select Next: Condition.
Condition
The form has several fields to complete:
- Signal name: Custom log search
- Search query: Displays the query code
- If you changed the scope, you need to add the query from the Create query section.
Measurement
- Measure: Table rows
- Aggregation type: Count
- Aggregation granularity: 5 minutes
Alert logic
- Operator: Greater than
- Threshold value: Use a number that's less that the number returned from the resources count.
- For example, if your resource count was 50 then use 45. This value triggers the alert to fire when it evaluates your resources because your number of resources is greater than the threshold value.
- Frequency of evaluation: 5 minutes
Select Next: Actions.
Actions
Select Create action group:
- Subscription: Select your Azure subscription.
- Resource group: demo-arg-alert-rg
- Region: Global allows the action groups service to select location.
- Action group name: demo-arg-alert-action-group
- Display name: demo-action (limit is 12 characters)
Select Next: Notifications:
- Notification type: Select Email/SMS message/Push/Voice.
- Name: email-alert
- Select the Email checkbox and type your email address.
- Select Ok.
Select Review + create, verify the summary is correct, and select Create. You're returned to the Actions tab of the Create an alert rule page. The Action group name shows the action group you created. You receive an email notification to confirm you were added to the action group.
Select Next: Details.
Details
Use the following information on the Details tab:
- Subscription: Select your Azure subscription.
- Resource group: demo-arg-alert-rg
- Severity: Accept the default value 3 - Informational.
- Alert rule name: demo-arg-alert-rule
- Alert rule description: Email alert for count of Azure resources
- Region: West US 3
- Identity: Select System assigned managed identity.
Select Review + create, verify the summary is correct, and select Create. You're returned to the Logs page of your Log Analytics workspace.
Assign role
Assign the Log Analytics Reader to the system-assigned managed identity so that it has permissions fire alerts that send email notifications.
- Select Monitoring > Alerts in the Log Analytics workspace. Select OK if you're prompted that Your unsaved edits will be discarded.
- Select Alert rules.
- Select demo-arg-alert-rule.
- Select Settings > Identity > System assigned:
- Status: On
- Object ID: Shows the GUID for your Enterprise Application (service principal) in Microsoft Entra ID.
- Permission: Select Azure role assignments:
- Verify your subscription is selected.
- Select Add role assignment:
- Scope: Subscription
- Subscription: Select your Azure subscription name.
- Role: Log Analytics Reader
- Select Save.
It takes a few minutes for the Log Analytics Reader to display on the Azure role assignments page. Select Refresh to update the page.
Use your browser's back button to return to the Identity and then select Overview to return to the alert rule. Select the link to your resource group named demo-arg-alert-rg.
Although out of scope for this article, if you're querying an Azure Data Explorer cluster, you must add the Reader role to the system-assigned managed identity. For more information, at the end of this article select the link Role assignments for Azure Data Explorer clusters.
Verify alerts
After the role is assigned to your alert rule, you begin to receive email for alert messages. The rule was created to send alerts every five minutes and it takes a few minutes to get the first alert.
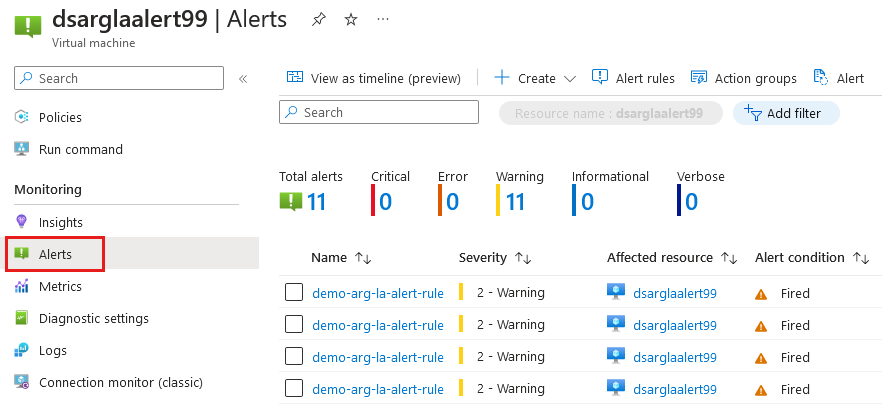
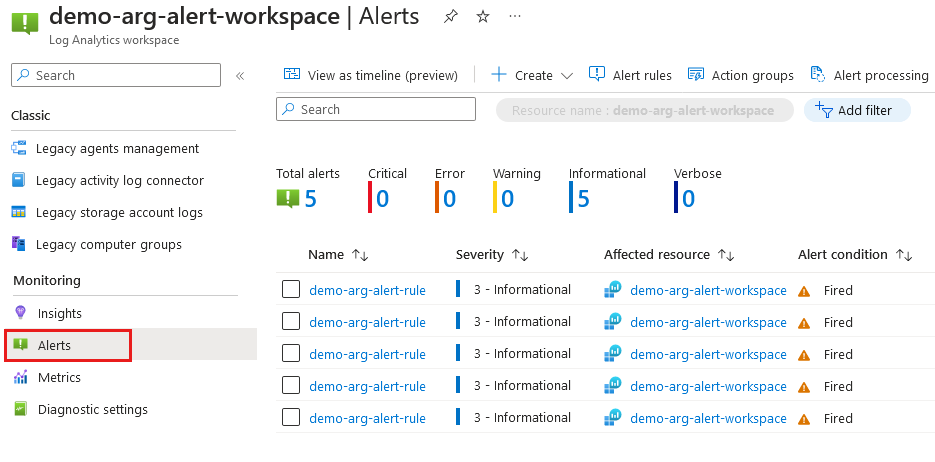
You can also view the alerts in the Azure portal:
Go to the resource group demo-arg-alert-rg.
Select demo-arg-alert-workspace in your list of resources.
Select Monitoring > Alerts.
A list of alerts is displayed.
Clean up resources
If you want to keep the alert configuration but stop the alert from firing and sending email notifications, you can disable it. Go to your alert rule demo-arg-alert-rule or demo-arg-la-alert-rule and select Disable.
If you don't need this alert or the resources you created in this example, delete the resource group with the following steps:
- Go to your resource group demo-arg-alert-rg.
- Select Delete resource group.
- Type the resource group name to confirm.
- Select Delete.
If you created a virtual machine, delete the private key you downloaded to your computer during the deployment. The filename has a .pem extension.
Related content
For more information about the query language or how to explore resources, go to the following articles.
- Troubleshoot Azure Resource Graph alerts
- Understanding the Azure Resource Graph query language
- Explore your Azure resources with Resource Graph
- Overview of Log Analytics in Azure Monitor
- Collect events and performance counters from virtual machines with Azure Monitor Agent
- Role assignments for Azure Data Explorer clusters