How to share access to Azure Managed Grafana
A DevOps team may build dashboards to monitor and diagnose an application or infrastructure that it manages. Likewise, a support team may use a Grafana monitoring solution for troubleshooting customer issues. In these scenarios, multiple users are accessing one Grafana instance.
Azure Managed Grafana enables such collaboration by allowing you to set custom permissions on an instance that you own. This article explains what permissions are supported and how to grant permissions to share an Azure Managed Grafana instance with your stakeholders.
Prerequisites
- An Azure account with an active subscription. Create an account for free.
- An Azure Managed Grafana instance. If you don't have one yet, create a Managed Grafana instance.
- You must have Grafana Admin permissions on the instance.
Supported Grafana roles
Azure Managed Grafana supports the following Grafana roles:
- Grafana Admin: provides full control of the instance including managing role assignments, viewing, editing, and configuring data sources.
- Grafana Editor: provides read-write access to the dashboards in the instance.
- Grafana Limited Viewer: provides read-only access to the Grafana home page. This role contains no permissions assigned by default and it is not available for Grafana v9 workspaces.
- Grafana Viewer: provides read-only access to dashboards in the instance.
Go to Azure role-based access control within Azure Managed Grafana for more information about these roles in Azure, and to Organization roles to learn about Grafana roles from the Grafana website. The Grafana Limited Viewer role in Azure maps to the "No Basic Role" in the Grafana documentation.
Add a Grafana role assignment
Grafana user roles and assignments are fully integrated within Microsoft Entra ID. You can assign a Grafana role to any Microsoft Entra user, group, service principal or managed identity, and grant them access permissions associated with that role. You can manage these permissions from the Azure portal or the command line. This section explains how to assign Grafana roles to users in the Azure portal.
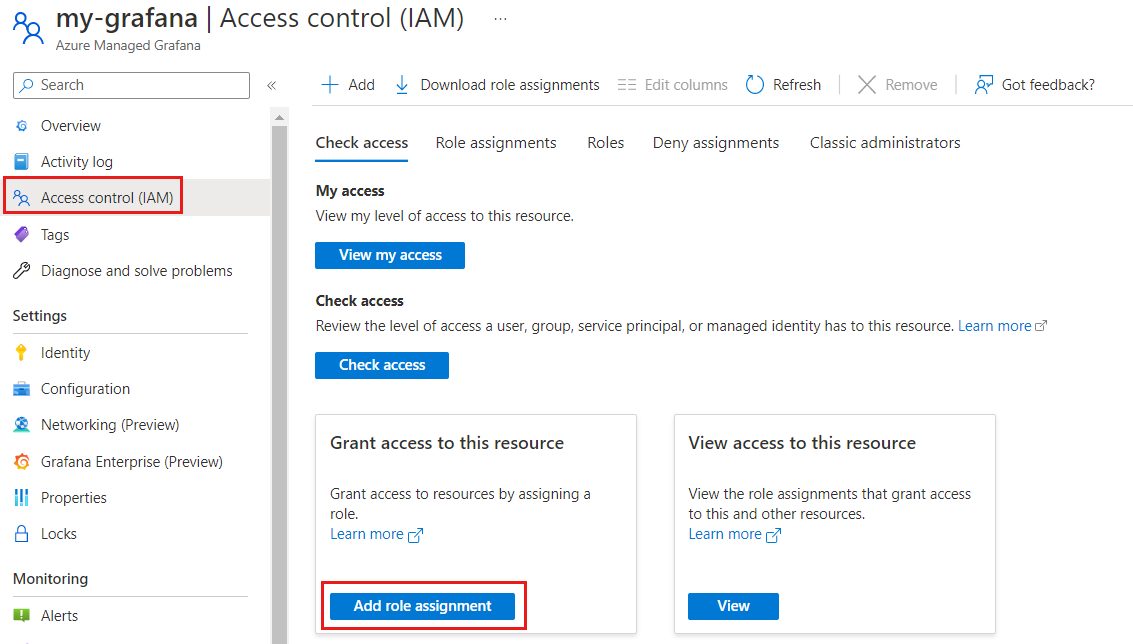
Open your Azure Managed Grafana instance.
Select Access control (IAM) in the left menu.
Select Add role assignment.
Select a Grafana role to assign among Grafana Admin, Grafana Editor, Grafana Limited Viewer or Grafana Viewer, then select Next.
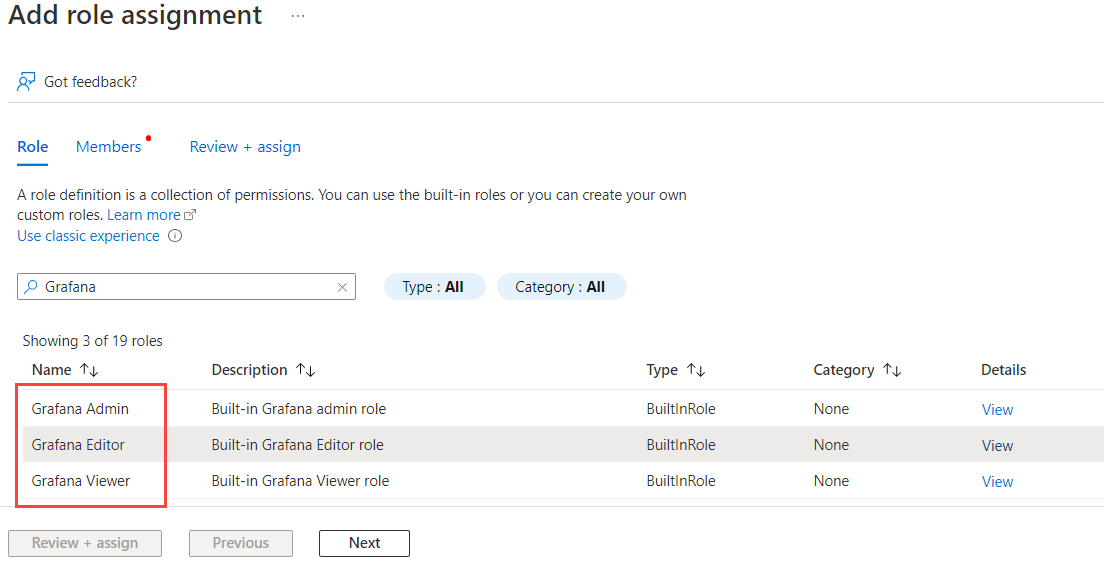
Choose if you want to assign access to a User, group, or service principal, or to a Managed identity.
Click on Select members, pick the members you want to assign to the Grafana role and then confirm with Select.
Select Next, then Review + assign to complete the role assignment.
Note
Dashboard and data source level sharing are done from within the Grafana application. For more information, refer to Share a Grafana dashboard or panel and Data source permissions.