Relocate Azure Monitor - Log Analytics workspace to another region
There are various reasons why you may want to move your existing Azure resources from one region to another. You may want to:
- Take advantage of a new Azure region.
- Deploy features or services available in specific regions only.
- Meet internal policy and governance requirements.
- Align with company mergers and acquisitions
- Meet capacity planning requirements.
A relocation plan for Log Analytics workspace must include the relocation of any resources that log data with Log Analytics Workspace.
Log Analytics workspace doesn't natively support migrating workspace data from one region to another and associated devices. Instead, you must create a new Log Analytics workspace in the target region and reconfigure the devices and settings in the new workspace.
The diagram below illustrates the relocation pattern for a Log Analytics workspace. The red flow lines represent the redeployment of the target instance along with data movement and updating domains and endpoints.
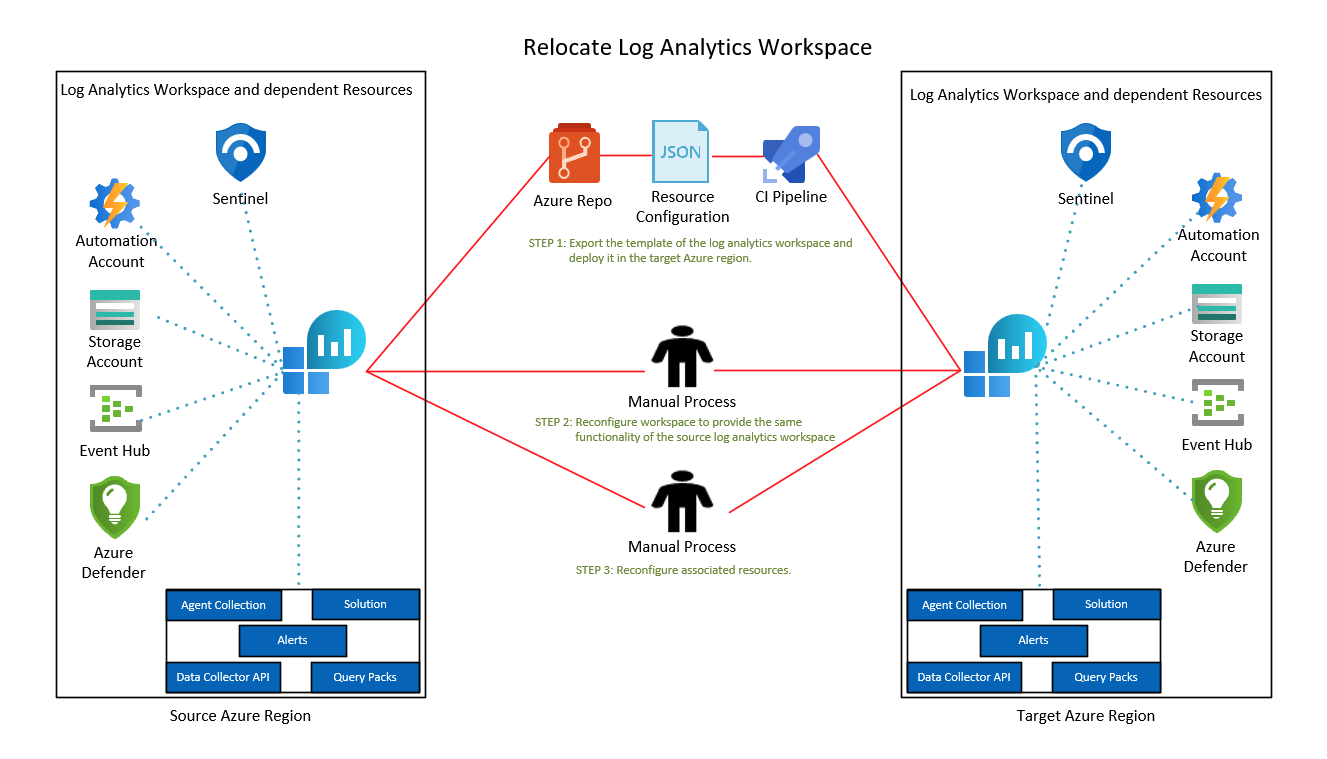
Relocation to availability zone support
Azure availability zones are at least three physically separate groups of datacenters within each Azure region. Datacenters within each zone are equipped with independent power, cooling, and networking infrastructure. In the case of a local zone failure, availability zones are designed so that if the one zone is affected, regional services, capacity, and high availability are supported by the remaining two zones.
Failures can range from software and hardware failures to events such as earthquakes, floods, and fires. Tolerance to failures is achieved with redundancy and logical isolation of Azure services. For more detailed information on availability zones in Azure, see Regions and availability zones.
Azure availability zones-enabled services are designed to provide the right level of reliability and flexibility. They can be configured in two ways. They can be either zone redundant, with automatic replication across zones, or zonal, with instances pinned to a specific zone. You can also combine these approaches. For more information on zonal vs. zone-redundant architecture, see Recommendations for using availability zones and regions.
If you want to relocate your Log Analytics workspace to a region that supports availability zones:
- Read Azure availability zone migration baseline to assess the availability-zone readiness of your workload or application.
- Follow the guidance in Migrate Log Analytics to availability zone support.
Prerequisites
To export the workspace configuration to a template that can be deployed to another region, you need the Log Analytics Contributor or Monitoring Contributor role, or higher.
Identify all the resources that are currently associated with your workspace, including:
Connected agents: Enter Logs in your workspace and query a heartbeat table to list connected agents.
Heartbeat | summarize by Computer, Category, OSType, _ResourceIdDiagnostic settings: Resources can send logs to Azure Diagnostics or dedicated tables in your workspace. Enter Logs in your workspace, and run this query for resources that send data to the
AzureDiagnosticstable:AzureDiagnostics | where TimeGenerated > ago(12h) | summarize by ResourceProvider , ResourceType, Resource | sort by ResourceProvider, ResourceTypeRun this query for resources that send data to dedicated tables:
search * | where TimeGenerated > ago(12h) | where isnotnull(_ResourceId) | extend ResourceProvider = split(_ResourceId, '/')[6] | where ResourceProvider !in ('microsoft.compute', 'microsoft.security') | extend ResourceType = split(_ResourceId, '/')[7] | extend Resource = split(_ResourceId, '/')[8] | summarize by tostring(ResourceProvider) , tostring(ResourceType), tostring(Resource) | sort by ResourceProvider, ResourceTypeInstalled solutions: Select Legacy solutions on the workspace navigation pane for a list of installed solutions.
Data collector API: Data arriving through a Data Collector API is stored in custom log tables. For a list of custom log tables, select Logs on the workspace navigation pane, and then select Custom log on the schema pane.
Linked services: Workspaces might have linked services to dependent resources such as an Azure Automation account, a storage account, or a dedicated cluster. Remove linked services from your workspace. Reconfigure them manually in the target workspace.
Alerts: To list alerts, select Alerts on your workspace navigation pane, and then select Manage alert rules on the toolbar. Alerts in workspaces created after June 1, 2019, or in workspaces that were upgraded from the Log Analytics Alert API to the scheduledQueryRules API can be included in the template.
You can check if the scheduledQueryRules API is used for alerts in your workspace. Alternatively, you can configure alerts manually in the target workspace.
Query packs: A workspace can be associated with multiple query packs. To identify query packs in your workspace, select Logs on the workspace navigation pane, select queries on the left pane, and then select the ellipsis to the right of the search box. A dialog with the selected query packs opens on the right. If your query packs are in the same resource group as the workspace that you're moving, you can include it with this migration.
Verify that your Azure subscription allows you to create Log Analytics workspaces in the target region.
Downtime
To understand the possible downtimes involved, see Cloud Adoption Framework for Azure: Select a relocation method.
Prepare
The following procedures show how to prepare the workspace and resources for the move by using a Resource Manager template.
Note
Not all resources can be exported through a template. You'll need to configure these separately after the workspace is created in the target region.
Sign in to the Azure portal, and then select Resource Groups.
Find the resource group that contains your workspace and select it.
To view an alert resource, select the Show hidden types checkbox.
Select the Type filter. Select Log Analytics workspace, Solution, SavedSearches, microsoft.insights/scheduledqueryrules, defaultQueryPack, and other workspace-related resources that you have (such as an Automation account). Then select Apply.
Select the workspace, solutions, saved searches, alerts, query packs, and other workspace-related resources that you have (such as an Automation account). Then select Export template on the toolbar.
Note
Microsoft Sentinel can't be exported with a template. You need to onboard Sentinel to a target workspace.
Select Deploy on the toolbar to edit and prepare the template for deployment.
Select Edit parameters on the toolbar to open the parameters.json file in the online editor.
To edit the parameters, change the
valueproperty underparameters. Here's an example:{ "$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentParameters.json#", "contentVersion": "1.0.0.0", "parameters": { "workspaces_name": { "value": "my-workspace-name" }, "workspaceResourceId": { "value": "/subscriptions/resource-id/resourceGroups/resource-group-name/providers/Microsoft.OperationalInsights/workspaces/workspace-name" }, "alertName": { "value": "my-alert-name" }, "querypacks_name": { "value": "my-default-query-pack-name" } } }Select Save in the editor.
Edit the template
Select Edit template on the toolbar to open the template.json file in the online editor.
To edit the target region where the Log Analytics workspace will be deployed, change the
locationproperty underresourcesin the online editor.To get region location codes, see Data residency in Azure. The code for a region is the region name with no spaces. For example, Central US should be
centralus.Remove linked-services resources (
microsoft.operationalinsights/workspaces/linkedservices) if they're present in the template. You should reconfigure these resources manually in the target workspace.The following example template includes the workspace, saved search, solutions, alerts, and query pack:
{ "$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#", "contentVersion": "1.0.0.0", "parameters": { "workspaces_name": { "type": "String" }, "workspaceResourceId": { "type": "String" }, "alertName": { "type": "String" }, "querypacks_name": { "type": "String" } }, "variables": {}, "resources": [ { "type": "microsoft.operationalinsights/workspaces", "apiVersion": "2020-08-01", "name": "[parameters('workspaces_name')]", "location": "france central", "properties": { "sku": { "name": "pergb2018" }, "retentionInDays": 30, "features": { "enableLogAccessUsingOnlyResourcePermissions": true }, "workspaceCapping": { "dailyQuotaGb": -1 }, "publicNetworkAccessForIngestion": "Enabled", "publicNetworkAccessForQuery": "Enabled" } }, { "type": "Microsoft.OperationalInsights/workspaces/savedSearches", "apiVersion": "2020-08-01", "name": "[concat(parameters('workspaces_name'), '/2b5112ec-5ad0-5eda-80e9-ad98b51d4aba')]", "dependsOn": [ "[resourceId('Microsoft.OperationalInsights/workspaces', parameters('workspaces_name'))]" ], "properties": { "category": "VM Monitoring", "displayName": "List all versions of curl in use", "query": "VMProcess\n| where ExecutableName == \"curl\"\n| distinct ProductVersion", "tags": [], "version": 2 } }, { "type": "Microsoft.OperationsManagement/solutions", "apiVersion": "2015-11-01-preview", "name": "[concat('Updates(', parameters('workspaces_name'))]", "location": "france central", "dependsOn": [ "[resourceId('microsoft.operationalinsights/workspaces', parameters('workspaces_name'))]" ], "plan": { "name": "[concat('Updates(', parameters('workspaces_name'))]", "promotionCode": "", "product": "OMSGallery/Updates", "publisher": "Microsoft" }, "properties": { "workspaceResourceId": "[resourceId('microsoft.operationalinsights/workspaces', parameters('workspaces_name'))]", "containedResources": [ "[concat(resourceId('microsoft.operationalinsights/workspaces', parameters('workspaces_name')), '/views/Updates(', parameters('workspaces_name'), ')')]" ] } } { "type": "Microsoft.OperationsManagement/solutions", "apiVersion": "2015-11-01-preview", "name": "[concat('VMInsights(', parameters('workspaces_name'))]", "location": "france central", "plan": { "name": "[concat('VMInsights(', parameters('workspaces_name'))]", "promotionCode": "", "product": "OMSGallery/VMInsights", "publisher": "Microsoft" }, "properties": { "workspaceResourceId": "[resourceId('microsoft.operationalinsights/workspaces', parameters('workspaces_name'))]", "containedResources": [ "[concat(resourceId('microsoft.operationalinsights/workspaces', parameters('workspaces_name')), '/views/VMInsights(', parameters('workspaces_name'), ')')]" ] } }, { "type": "microsoft.insights/scheduledqueryrules", "apiVersion": "2021-08-01", "name": "[parameters('alertName')]", "location": "france central", "properties": { "displayName": "[parameters('alertName')]", "severity": 3, "enabled": true, "evaluationFrequency": "PT5M", "scopes": [ "[parameters('workspaceResourceId')]" ], "windowSize": "PT15M", "criteria": { "allOf": [ { "query": "Heartbeat | where computer == 'my computer name'", "timeAggregation": "Count", "operator": "LessThan", "threshold": 14, "failingPeriods": { "numberOfEvaluationPeriods": 1, "minFailingPeriodsToAlert": 1 } } ] }, "autoMitigate": true, "actions": {} } }, { "type": "Microsoft.OperationalInsights/querypacks", "apiVersion": "2019-09-01-preview", "name": "[parameters('querypacks_name')]", "location": "francecentral", "properties": {} }, { "type": "Microsoft.OperationalInsights/querypacks/queries", "apiVersion": "2019-09-01-preview", "name": "[concat(parameters('querypacks_name'), '/00000000-0000-0000-0000-000000000000')]", "dependsOn": [ "[resourceId('Microsoft.OperationalInsights/querypacks', parameters('querypacks_name'))]" ], "properties": { "displayName": "my-query-name", "body": "my-query-text", "related": { "categories": [], "resourceTypes": [ "microsoft.operationalinsights/workspaces" ] }, "tags": { "labels": [] } } } ] }Select Save in the online editor.
Redeploy
Select Subscription to choose the subscription where the target workspace will be deployed.
Select Resource group to choose the resource group where the target workspace will be deployed. You can select Create new to create a new resource group for the target workspace.
Verify that Region is set to the target location where you want the network security group to be deployed.
Select the Review + create button to verify your template.
Select Create to deploy the workspace and the selected resource to the target region.
Your workspace, including selected resources, is now deployed in the target region. You can complete the remaining configuration in the workspace for paring functionality to the original workspace.
- Connect agents: Use any of the available options, including Data Collection Rules, to configure the required agents on virtual machines and virtual machine scale sets and to specify the new target workspace as the destination.
- Diagnostic settings: Update diagnostic settings in identified resources, with the target workspace as the destination.
- Install solutions: Some solutions, such as Microsoft Sentinel, require certain onboarding procedures and weren't included in the template. You should onboard them separately to the new workspace.
- Configure the Data Collector API: Configure Data Collector API instances to send data to the target workspace.
- Configure alert rules: When alerts aren't exported in the template, you need to configure them manually in the target workspace.
Verify that new data isn't ingested to the original workspace. Run the following query in your original workspace, and observe that there's no ingestion after the migration:
search * | where TimeGenerated > ago(12h) | summarize max(TimeGenerated) by Type
After data sources are connected to the target workspace, ingested data is stored in the target workspace. Older data stays in the original workspace and is subject to the retention policy. You can perform a cross-workspace query. If both workspaces were assigned the same name, use a qualified name (subscriptionName/resourceGroup/componentName) in the workspace reference.
Here's an example for a query across two workspaces that have the same name:
union
workspace('subscription-name1/<resource-group-name1/<original-workspace-name>')Update,
workspace('subscription-name2/<resource-group-name2/<target-workspace-name>').Update,
| where TimeGenerated >= ago(1h)
| where UpdateState == "Needed"
| summarize dcount(Computer) by Classification
Discard
If you want to discard the source workspace, delete the exported resources or the resource group that contains these resources:
Select the target resource group in the Azure portal.
On the Overview page:
- If you created a new resource group for this deployment, select Delete resource group on the toolbar to delete the resource group.
- If the template was deployed to an existing resource group, select the resources that were deployed with the template, and then select Delete on the toolbar to delete selected resources.
Clean up
While new data is being ingested to your new workspace, older data in the original workspace remains available for query and is subject to the retention policy defined in the workspace. We recommend that you keep the original workspace for as long as you need older data to query across workspaces.
If you no longer need access to older data in the original workspace:
- Select the original resource group in the Azure portal.
- Select any resources that you want to remove, and then select Delete on the toolbar.
Related content
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for