SQL information protection policy in Microsoft Defender for Cloud
SQL information protection's data discovery and classification mechanism provides advanced capabilities for discovering, classifying, labeling, and reporting the sensitive data in your databases. It's built into Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics.
The classification mechanism is based on the following two elements:
- Labels – The main classification attributes, used to define the sensitivity level of the data stored in the column.
- Information Types – Provides additional granularity into the type of data stored in the column.
The information protection policy options within Defender for Cloud provide a predefined set of labels and information types that serve as the defaults for the classification engine. You can customize the policy, according to your organization's needs, as described below.
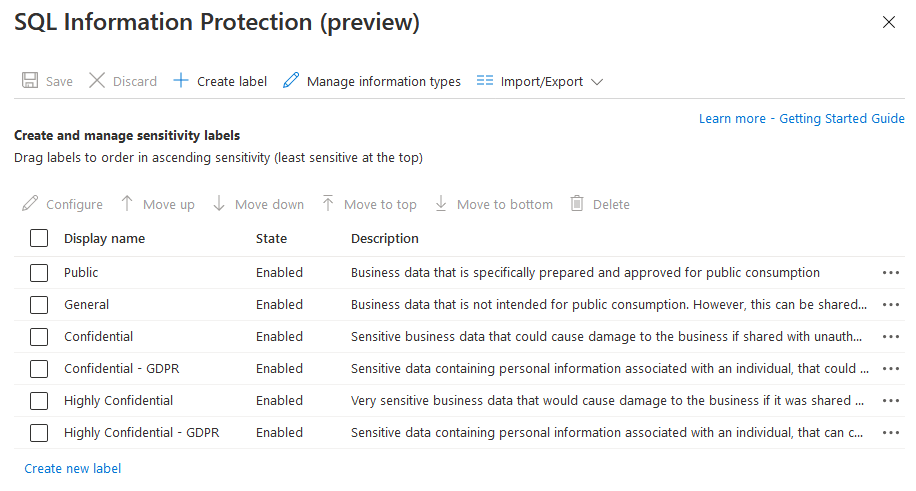
How do I access the SQL information protection policy?
There are three ways to access the information protection policy:
- (Recommended) From the Environment settings page of Defender for Cloud
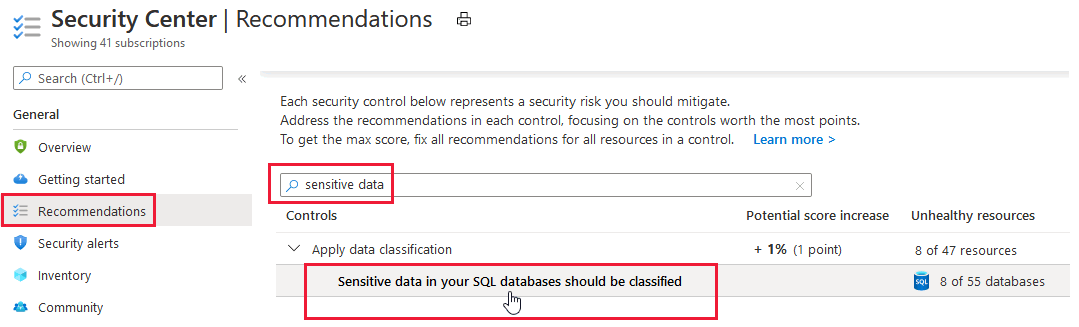
- From the security recommendation Sensitive data in your SQL databases should be classified
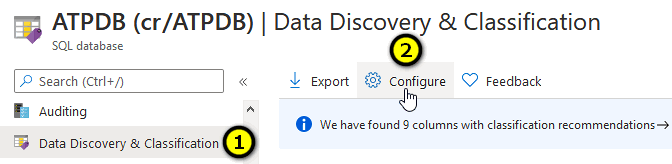
- From the Azure SQL DB data discovery page
Each of these is shown in the relevant tab below.
Access the policy from Defender for Cloud's environment settings page
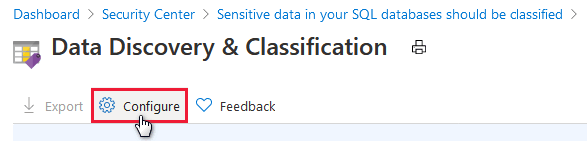
From Defender for Cloud's Environment settings page, select SQL information protection.
Note
This option only appears for users with tenant-level permissions. Grant tenant-wide permissions to yourself.

Customize your information types
To manage and customize information types:
Select Manage information types.
To add a new type, select Create information type. You can configure a name, description, and search pattern strings for the information type. Search pattern strings can optionally use keywords with wildcard characters (using the character '%'), which the automated discovery engine uses to identify sensitive data in your databases, based on the columns' metadata.
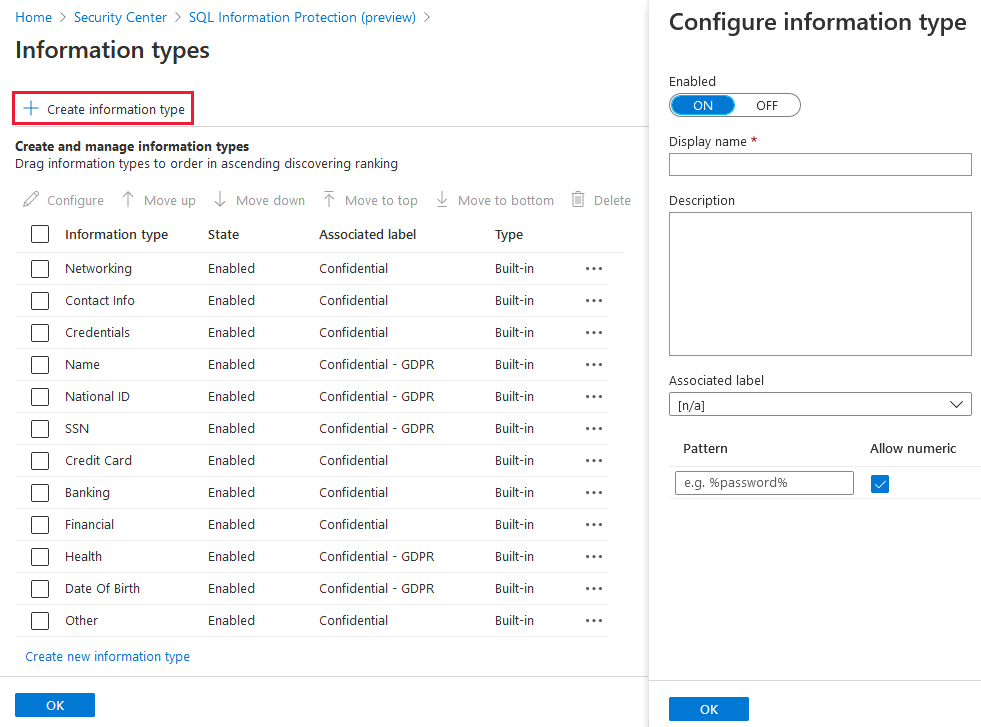
You can also modify the built-in types by adding additional search pattern strings, disabling some of the existing strings, or by changing the description.
Tip
You can't delete built-in types or change their names.
Information types are listed in order of ascending discovery ranking, meaning that the types higher in the list attempt to match first. To change the ranking between information types, drag the types to the right spot in the table, or use the Move up and Move down buttons to change the order.
Select OK when you're done.
After you completed managing your information types, be sure to associate the relevant types with the relevant labels, by selecting Configure for a particular label, and adding or deleting information types as appropriate.
To apply your changes, select Save in the main Labels page.
Exporting and importing a policy
You can download a JSON file with your defined labels and information types, edit the file in the editor of your choice, and then import the updated file.
Note
You'll need tenant level permissions to import a policy file.
Permissions
To customize the information protection policy for your Azure tenant, you need the following actions on the tenant's root management group:
- Microsoft.Security/informationProtectionPolicies/read
- Microsoft.Security/informationProtectionPolicies/write
Learn more in Grant and request tenant-wide visibility.
Manage SQL information protection using Azure PowerShell
- Get-AzSqlInformationProtectionPolicy: Retrieves the effective tenant SQL information protection policy.
- Set-AzSqlInformationProtectionPolicy: Sets the effective tenant SQL information protection policy.