Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
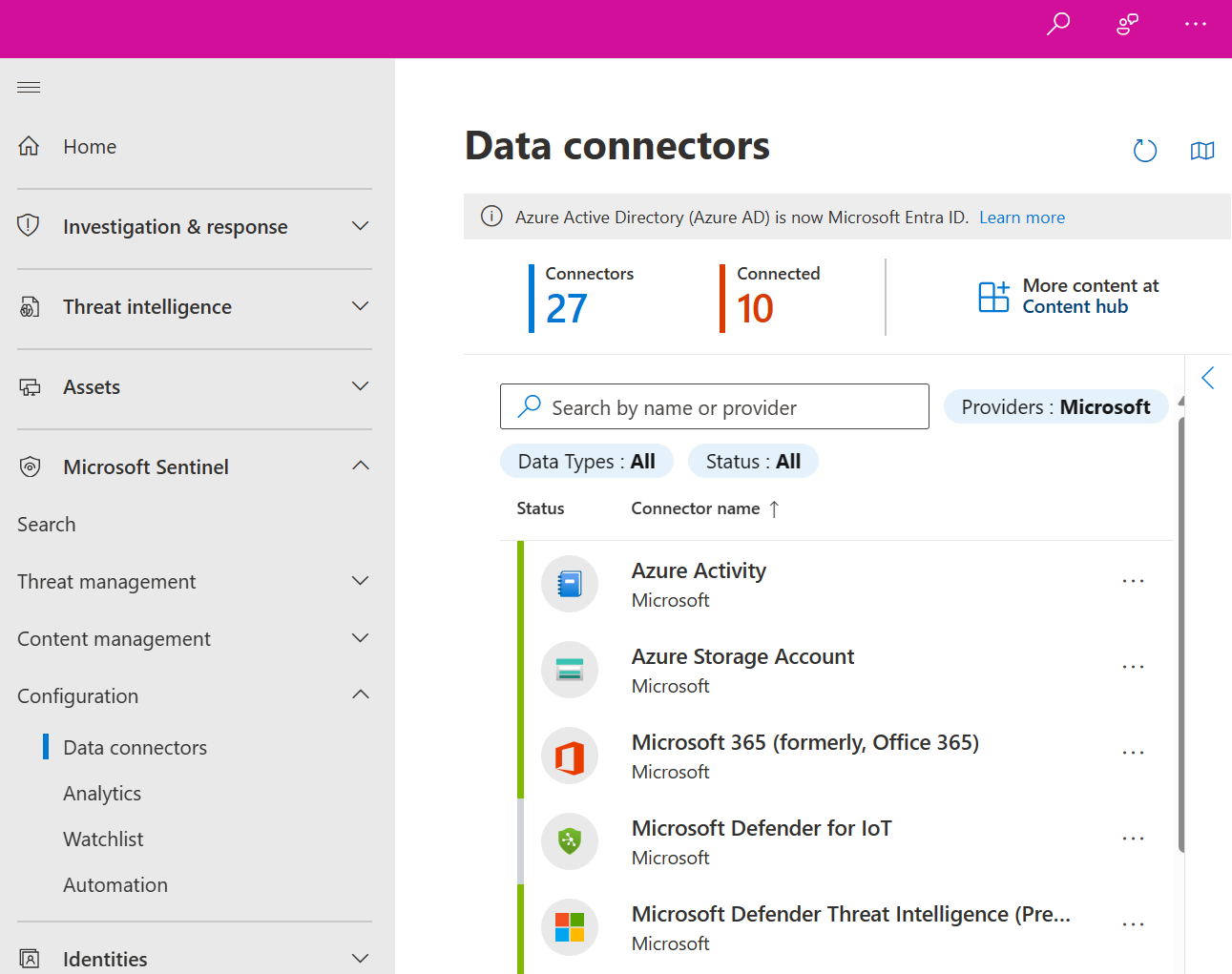
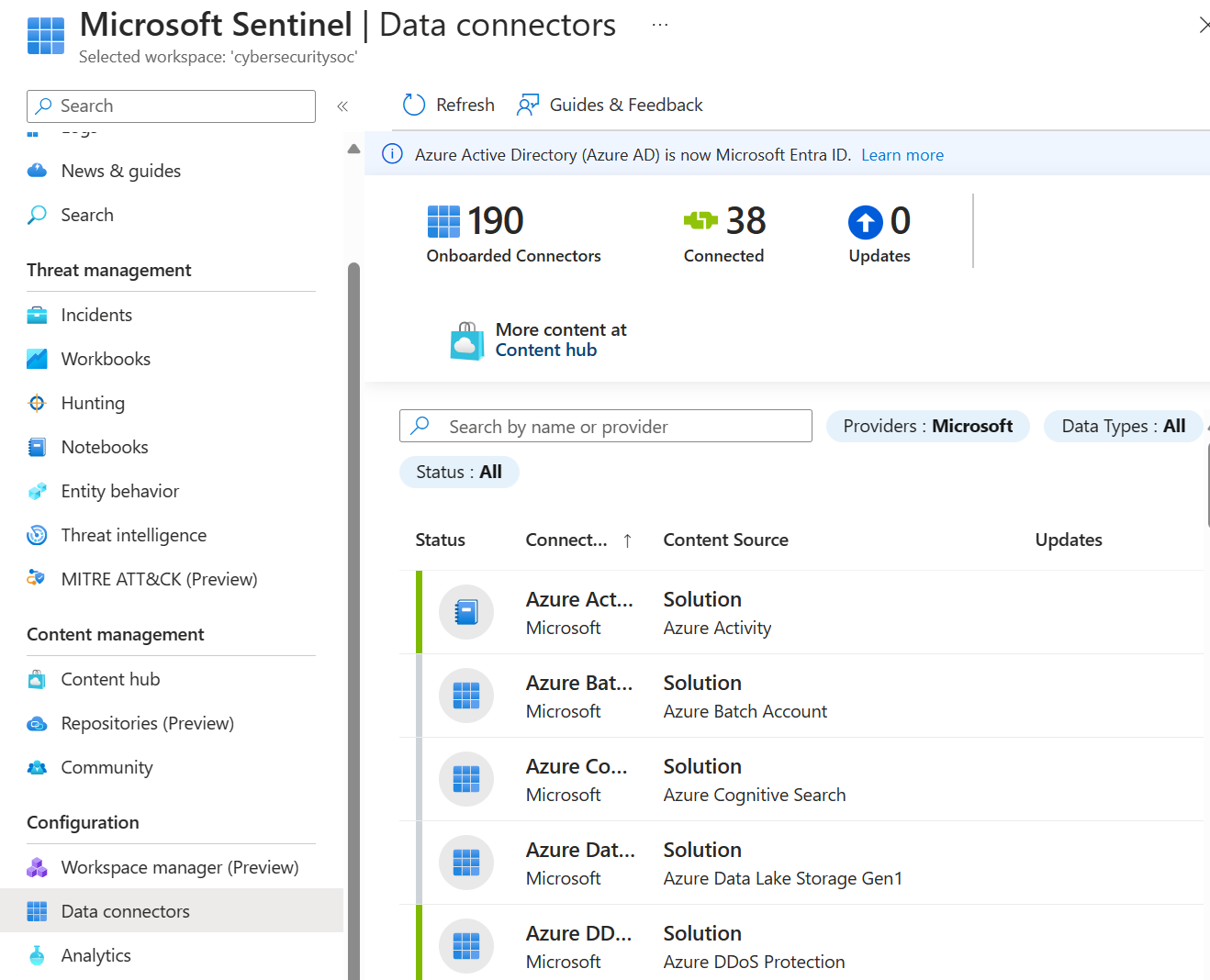
After you onboard Microsoft Sentinel into your workspace, use data connectors to start ingesting your data into Microsoft Sentinel. Microsoft Sentinel comes with many out of the box connectors for Microsoft services, which integrate in real time. For example, the Microsoft Defender XDR connector is a service-to-service connector that integrates data from Office 365, Microsoft Entra ID, Microsoft Defender for Identity, and Microsoft Defender for Cloud Apps.
Built-in connectors enable connection to the broader security ecosystem for non-Microsoft products. For example, use Syslog, Common Event Format (CEF), or REST APIs to connect your data sources with Microsoft Sentinel.
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
Important
Microsoft Sentinel is generally available in the Microsoft Defender portal, including for customers without Microsoft Defender XDR or an E5 license.
Starting in July 2026, Microsoft Sentinel will be supported in the Defender portal only, and any remaining customers using the Azure portal will be automatically redirected.
We recommend that any customers using Microsoft Sentinel in Azure start planning the transition to the Defender portal for the full unified security operations experience offered by Microsoft Defender. For more information, see Planning your move to Microsoft Defender portal for all Microsoft Sentinel customers.
Data connectors provided with solutions
Microsoft Sentinel solutions provide packaged security content, including data connectors, workbooks, analytics rules, playbooks, and more. When you deploy a solution with a data connector, you get the data connector together with related content in the same deployment.
The Microsoft Sentinel Data connectors page lists the installed or in-use data connectors.
To add more data connectors, install the solution associated with the data connector from the Content Hub. For more information, see the following articles:
- Find your Microsoft Sentinel data connector
- About Microsoft Sentinel content and solutions
- Discover and manage Microsoft Sentinel out-of-the-box content
- Microsoft Sentinel content hub catalog
- Advanced Security Information Model (ASIM) based domain solutions for Microsoft Sentinel
Create custom connectors
If you're unable to connect your data source to Microsoft Sentinel using any of the existing solutions available, consider creating your own data source connector. For example, many security solutions provide a set of APIs for retrieving log files and other security data from their product or service. Those APIs connect to Microsoft Sentinel with one of the following methods:
- The data source APIs are configured with the Codeless Connector Framework.
- The data connector uses the Log Ingestion API for Azure Monitor as part of an Azure Function or Logic App.
You can also use Azure Monitor Agent directly or Logstash to create your custom connector. For more information, see Resources for creating Microsoft Sentinel custom connectors.
Agent-based integration for data connectors
Microsoft Sentinel can use agents provided by the Azure Monitor service (on which Microsoft Sentinel is based) to collect data from any data source that can perform real-time log streaming. For example, most on-premises data sources connect by using agent-based integration.
The following sections describe the different types of Microsoft Sentinel agent-based data connectors. To configure connections using agent-based mechanisms, follow the steps in each Microsoft Sentinel data connector page.
Syslog and Common Event Format (CEF)
You can stream events from Linux-based, Syslog-supporting devices into Microsoft Sentinel by using the Azure Monitor Agent (AMA). Log formats vary, but many sources support CEF-based formatting. Depending on the device type, the agent is installed either directly on the device, or on a dedicated Linux-based log forwarder. The AMA receives plain Syslog or CEF event messages from the Syslog daemon over UDP. The Syslog daemon forwards events to the agent internally, communicating over TCP or UDS (Unix Domain Sockets), depending on the version. The AMA then transmits these events to the Microsoft Sentinel workspace.
Here's a simple flow that shows how Microsoft Sentinel streams Syslog data.
- The device's built-in Syslog daemon collects local events of the specified types, and forwards the events locally to the agent.
- The agent streams the events to your Log Analytics workspace.
- After successful configuration, Syslog messages appear in the Log Analytics Syslog table, and CEF messages in the CommonSecurityLog table.
For more information, see Syslog and Common Event Format (CEF) via AMA connectors for Microsoft Sentinel.
Custom logs
For some data sources, you can collect logs as files on Windows or Linux computers using the Log Analytics custom log collection agent.
To connect using the Log Analytics custom log collection agent, follow the steps in each Microsoft Sentinel data connector page. After successful configuration, the data appears in custom tables.
For more information, see Custom Logs via AMA data connector - Configure data ingestion to Microsoft Sentinel from specific applications.
Service-to-service integration for data connectors
Microsoft Sentinel uses the Azure foundation to provide out-of-the-box service-to-service support for Microsoft services and Amazon Web Services.
For more information, see the following articles:
- Connect Microsoft Sentinel to Azure, Windows, Microsoft, and Amazon services
- Find your Microsoft Sentinel data connector
Data connector support
Both Microsoft and other organizations author Microsoft Sentinel data connectors. Each data connector has one of the following support types listed on the data connector page in Microsoft Sentinel.
| Support type | Description |
|---|---|
| Microsoft-supported | Applies to:
Partners or the Community support data connectors authored by any party other than Microsoft. |
| Partner-supported | Applies to data connectors authored by parties other than Microsoft. The partner company provides support or maintenance for these data connectors. The partner company can be an Independent Software Vendor, a Managed Service Provider (MSP/MSSP), a Systems Integrator (SI), or any organization whose contact information is provided on the Microsoft Sentinel page for that data connector. For any issues with a partner-supported data connector, contact the specified data connector support contact. |
| Community-supported | Applies to data connectors authored by Microsoft or partner developers that don't have listed contacts for data connector support and maintenance on the data connector page in Microsoft Sentinel. For questions or issues with these data connectors, you can file an issue in the Microsoft Sentinel GitHub community. |
For more information, see Find support for a data connector.
Next steps
For more information about data connectors, see the following articles.
- Connect your data sources to Microsoft Sentinel by using data connectors
- Find your Microsoft Sentinel data connector
- Resources for creating Microsoft Sentinel custom connectors
For a basic Infrastructure as Code (IaC) reference of Bicep, Azure Resource Manager, and Terraform to deploy data connectors in Microsoft Sentinel, see Microsoft Sentinel data connector IaC reference.