Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes feature availability in the Microsoft Azure and Azure Government clouds. Features are listed as GA (Generally Available), Public Preview, or Not Available for the following security services:
- Azure Information Protection
- Microsoft Defender for Cloud
- Microsoft Sentinel
- Microsoft Defender for IoT
- Azure Attestation
Note
Additional security services will be added to this article soon.
Azure Government
Azure Government uses the same underlying technologies as Azure (sometimes referred to as Azure Commercial or Azure Public), which includes the core components of Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS). Both Azure and Azure Government have comprehensive security controls in place, and the Microsoft commitment on the safeguarding of customer data.
Azure Government is a physically isolated cloud environment dedicated to US federal, state, local, and tribal governments, and their partners. Whereas both cloud environments are assessed and authorized at the FedRAMP High impact level, Azure Government provides an extra layer of protection to customers through contractual commitments regarding storage of customer data in the United States and limiting potential access to systems processing customer data to screened US persons. These commitments may be of interest to customers using the cloud to store or process data subject to US export control regulations such as the EAR, ITAR, and DoE 10 CFR Part 810.
For more information about Azure Government, see What is Azure Government?
Note
These lists and tables do not include feature or bundle availability in the Azure Government Secret or Azure Government Top Secret clouds. For more information about specific availability for air-gapped clouds, please contact your account team.
Microsoft 365 integration
Integrations between products rely on interoperability between Azure and Office platforms. Offerings hosted in the Azure environment are accessible from the Microsoft 365 Enterprise and Microsoft 365 Government platforms. Office 365 and Office 365 GCC are paired with Microsoft Entra ID in Azure. Office 365 GCC High and Office 365 DoD are paired with Microsoft Entra ID in Azure Government.
The following diagram displays the hierarchy of Microsoft clouds and how they relate to each other.
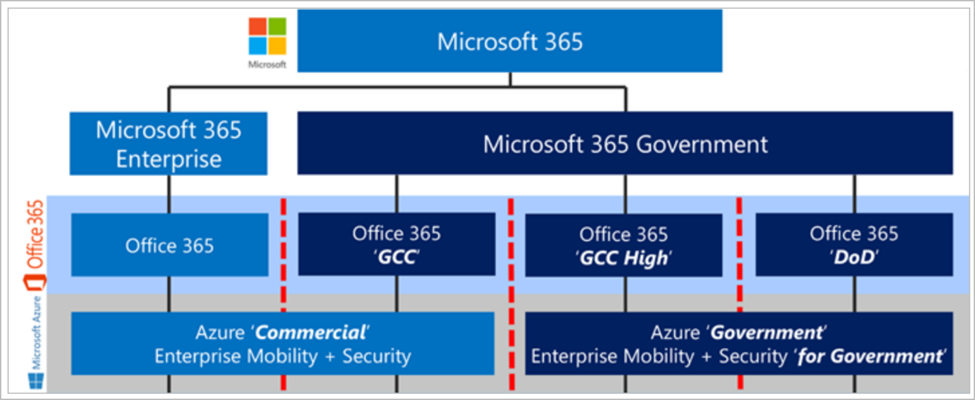
The Office 365 GCC environment helps customers comply with US government requirements, including FedRAMP High, CJIS, and IRS 1075. The Office 365 GCC High and DoD environments support customers who need compliance with DoD IL4/5, DFARS 7012, NIST 800-171, and ITAR.
For more information about Office 365 US Government environments, see:
The following sections identify when a service has an integration with Microsoft 365 and the feature availability for Office 365 GCC, Office 365 High, and Office 365 DoD.
Azure Information Protection
Azure Information Protection (AIP) is a cloud-based solution that enables organizations to discover, classify, and protect documents and emails by applying labels to content.
AIP is part of the Microsoft Purview Information Protection (MIP) solution, and extends the labeling and classification functionality provided by Microsoft 365.
For more information, see the Azure Information Protection product documentation.
Office 365 GCC is paired with Microsoft Entra ID in Azure. Office 365 GCC High and Office 365 DoD are paired with Microsoft Entra ID in Azure Government. Make sure to pay attention to the Azure environment to understand where interoperability is possible. In the following table, interoperability that is not possible is marked with a dash (-) to indicate that support is not relevant.
Extra configurations are required for GCC-High and DoD customers. For more information, see Azure Information Protection Premium Government Service Description.
Note
More details about support for government customers are listed in footnotes below the table.
Extra steps are required for configuring Azure Information Protection for GCC High and DoD customers. For more information, see the Azure Information Protection Premium Government Service Description.
| Feature/Service | Azure | Azure Government |
|---|---|---|
| Azure Information Protection scanner 1 | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| Administration | ||
| Azure Information Protection portal for scanner administration | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| Classification and labeling 2 | ||
| AIP scanner to apply a default label to all files in an on-premises file server / repository | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| AIP scanner for automated classification, labeling, and protection of supported on-premises files | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
1 The scanner can function without Office 365 to scan files only. The scanner cannot apply labels to files without Office 365.
2 The classification and labeling add-in is only supported for government customers with Microsoft 365 Apps (version 9126.1001 or higher), including Professional Plus (ProPlus) and Click-to-Run (C2R) versions. Office 2010, Office 2013, and other Office 2016 versions are not supported.
Office 365 features
3 The Mobile Device Extension for AD RMS is currently not available for government customers.
4 Information Rights Management with SharePoint Online (IRM-protected sites and libraries) is currently not available.
5 Information Rights Management (IRM) is supported only for Microsoft 365 Apps (version 9126.1001 or higher), including Professional Plus (ProPlus) and Click-to-Run (C2R) versions. Office 2010, Office 2013, and other Office 2016 versions are not supported.
6 Only on-premises Exchange is supported. Outlook Protection Rules are not supported. File Classification Infrastructure is not supported. On-premises SharePoint is not supported.
7 Sharing of protected documents and emails from government clouds to users in the commercial cloud is not currently available. Includes Microsoft 365 Apps users in the commercial cloud, non-Microsoft 365 Apps users in the commercial cloud, and users with an RMS for Individuals license.
8 The number of Sensitive Information Types in your Microsoft Purview compliance portal may vary based on region.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud - whether they're in Azure or not - as well as on premises.
For more information, see the Microsoft Defender for Cloud product documentation.
The following table displays the current Defender for Cloud feature availability in Azure and Azure Government.
1 Partially GA: The ability to disable specific findings from vulnerability scans is in public preview.
2 Vulnerability scans of container registries on Azure Gov can only be performed with the scan on push feature.
3 Requires Microsoft Defender for container registries.
4 Partially GA: Support for Azure Arc-enabled clusters is in public preview and not available on Azure Government.
5 Requires Microsoft Defender for Kubernetes.
6 Partially GA: Some of the threat protection alerts from Microsoft Defender for Storage are in public preview.
7 These features all require Microsoft Defender for servers.
8 There may be differences in the standards offered per cloud type.
9 Partially GA: Support for Arc-enabled Kubernetes clusters (and therefore AWS EKS too) is in public preview and not available on Azure Government. Run-time visibility of vulnerabilities in container images is also a preview feature.
Microsoft Sentinel
Microsoft Sentinel is a scalable, cloud-native, security information event management (SIEM), and security orchestration automated response (SOAR) solution. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
For more information, see the Microsoft Sentinel product documentation.
For Microsoft Sentinel feature availability in Azure, Azure Government, and Azure China 21 Vianet, see Microsoft Sentinel feature support for Azure clouds.
Microsoft Purview Data Connectors
Office 365 GCC is paired with Microsoft Entra ID in Azure. Office 365 GCC High and Office 365 DoD are paired with Microsoft Entra ID in Azure Government.
Tip
Make sure to pay attention to the Azure environment to understand where interoperability is possible. In the following table, interoperability that is not possible is marked with a dash (-) to indicate that support is not relevant.
| Connector | Azure | Azure Government |
|---|---|---|
| Office IRM | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| Dynamics 365 | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| Microsoft Defender XDR | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Public Preview |
| - Office 365 DoD | - | Public Preview |
| Microsoft Defender for Cloud Apps | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| Microsoft Defender for Cloud Apps Shadow IT logs |
||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Public Preview |
| - Office 365 DoD | - | Public Preview |
| Microsoft Defender for Cloud Apps Alerts |
||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Public Preview |
| - Office 365 DoD | - | Public Preview |
| Microsoft Defender for Endpoint | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| Microsoft Defender for Identity | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| Microsoft Defender for Office 365 | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| - Microsoft Power BI | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| - Microsoft Project | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
| Office 365 | ||
| - Office 365 GCC | GA | - |
| - Office 365 GCC High | - | GA |
| - Office 365 DoD | - | GA |
| Teams | ||
| - Office 365 GCC | Public Preview | - |
| - Office 365 GCC High | - | Not Available |
| - Office 365 DoD | - | Not Available |
Microsoft Defender for IoT
Microsoft Defender for IoT lets you accelerate IoT/OT innovation with comprehensive security across all your IoT/OT devices. For end-user organizations, Microsoft Defender for IoT offers agentless, network-layer security that is rapidly deployed, works with diverse industrial equipment, and interoperates with Microsoft Sentinel and other SOC tools. Deploy on-premises or in Azure-connected environments. For IoT device builders, the Microsoft Defender for IoT security agents allow you to build security directly into your new IoT devices and Azure IoT projects. The micro agent has flexible deployment options, including the ability to deploy as a binary package or modify source code. And the micro agent is available for standard IoT operating systems like Linux and Azure RTOS. For more information, see the Microsoft Defender for IoT product documentation.
The following table displays the current Microsoft Defender for IoT feature availability in Azure, and Azure Government.
For organizations
| Feature | Azure | Azure Government |
|---|---|---|
| On-premises device discovery and inventory | GA | GA |
| Vulnerability management | GA | GA |
| Threat detection with IoT, and OT behavioral analytics | GA | GA |
| Manual and automatic threat intelligence updates | GA | GA |
| Unify IT, and OT security with SIEM, SOAR and XDR | ||
| Active Directory | GA | GA |
| ArcSight | GA | GA |
| ClearPass (Alerts & Inventory) | GA | GA |
| CyberArk PSM | GA | GA |
| GA | GA | |
| FortiGate | GA | GA |
| FortiSIEM | GA | GA |
| Microsoft Sentinel | GA | GA |
| NetWitness | GA | GA |
| Palo Alto NGFW | GA | GA |
| Palo Alto Panorama | GA | GA |
| ServiceNow (Alerts & Inventory) | GA | GA |
| SNMP MIB Monitoring | GA | GA |
| Splunk | GA | GA |
| SYSLOG Server (CEF format) | GA | GA |
| SYSLOG Server (LEEF format) | GA | GA |
| SYSLOG Server (Object) | GA | GA |
| SYSLOG Server (Text Message) | GA | GA |
For device builders
| Feature | Azure | Azure Government |
|---|---|---|
| Micro agent for Azure RTOS | GA | GA |
| Configure Sentinel with Microsoft Defender for IoT | GA | GA |
| Standalone micro agent for Linux | ||
| Standalone agent binary installation | Public Preview | Public Preview |
Azure Attestation
Microsoft Azure Attestation is a unified solution for remotely verifying the trustworthiness of a platform and integrity of the binaries running inside it. The service receives evidence from the platform, validates it with security standards, evaluates it against configurable policies, and produces an attestation token for claims-based applications (e.g., relying parties, auditing authorities).
Azure Attestation is currently available in multiple regions across Azure public and Government clouds. In Azure Government, the service is available in preview status across US Gov Virginia and US Gov Arizona.
For more information, see Azure Attestation public documentation.
| Feature | Azure | Azure Government |
|---|---|---|
| Portal experience to perform control-plane and data-plane operations | GA | - |
| PowerShell experience to perform control-plane and data-plane operations | GA | GA |
| TLS 1.2 enforcement | GA | GA |
| BCDR support | GA | - |
| Service tag integration | GA | GA |
| Immutable log storage | GA | GA |
| Network isolation using private link | Public Preview | - |
| FedRAMP High certification | GA | - |
| Customer lockbox | GA | - |
Next steps
- Understand the shared responsibility model and which security tasks are handled by the cloud provider and which tasks are handled by you.
- Understand the Azure Government Cloud capabilities and the trustworthy design and security used to support compliance applicable to federal, state, and local government organizations and their partners.
- Understand the Office 365 Government plan.
- Understand compliance in Azure for legal and regulatory standards.