Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article explains how to create and use automation rules in Microsoft Sentinel to manage and orchestrate threat response, in order to maximize your SOC's efficiency and effectiveness.
In this article you'll learn how to define the triggers and conditions that determine when your automation rule runs, the various actions that you can have the rule perform, and the remaining features and functionalities.
Important
Microsoft Sentinel is generally available in the Microsoft Defender portal, including for customers without Microsoft Defender XDR or an E5 license.
Starting in July 2026, all customers using Microsoft Sentinel in the Azure portal will be redirected to the Defender portal and will use Microsoft Sentinel in the Defender portal only. Starting in July 2025, many new customers are automatically onboarded and redirected to the Defender portal.
If you're still using Microsoft Sentinel in the Azure portal, we recommend that you start planning your transition to the Defender portal to ensure a smooth transition and take full advantage of the unified security operations experience offered by Microsoft Defender. For more information, see It’s Time to Move: Retiring Microsoft Sentinel’s Azure portal for greater security.
Design your automation rule
Before you create your automation rule, we recommend that you determine its scope and design, including the trigger, conditions, and actions that make up your rule.
Determine the scope
The first step in designing and defining your automation rule is figuring out which incidents or alerts you want it to apply to. This determination directly impacts how you create the rule.
You also want to determine your use case. What are you trying to accomplish with this automation? Consider the following options:
- Create tasks for your analysts to follow in triaging, investigating, and remediating incidents.
- Suppress noisy incidents. (Alternatively, use other methods to handle false positives in Microsoft Sentinel.)
- Triage new incidents by changing their status from New to Active and assigning an owner.
- Tag incidents to classify them.
- Escalate an incident by assigning a new owner.
- Close resolved incidents, specifying a reason and adding comments.
- Analyze the incident's contents (alerts, entities, and other properties) and take further action by calling a playbook.
- Handle or respond to an alert without an associated incident.
Determine the trigger
Do you want this automation to be activated when new incidents or alerts are created? Or anytime an incident gets updated?
Automation rules are triggered when an incident is created or updated or when an alert is created. Recall that incidents include alerts, and that both alerts and incidents can be created by analytics rules, of which there are several types, as explained in Threat detection in Microsoft Sentinel.
The following table shows the different possible scenarios that cause an automation rule to run.
| Trigger type | Events that cause the rule to run |
|---|---|
| When incident is created | Microsoft Defender portal: Microsoft Sentinel not onboarded to the Defender portal: |
| When incident is updated | |
| When alert is created |
Create your automation rule
Most of the following instructions apply to any and all use cases for which you'll create automation rules.
If you're looking to suppress noisy incidents and are working in the Azure portal, try handling false positives.
If you want to create an automation rule to apply to a specific analytics rule, see Set automated responses and create the rule.
To create your automation rule:
For Microsoft Sentinel in the Azure portal, select the Configuration > Automation page. For Microsoft Sentinel in the Defender portal, select Microsoft Sentinel > Configuration > Automation.
From the Automation page in the Microsoft Sentinel navigation menu, select Create from the top menu and choose Automation rule.
The Create new automation rule panel opens. In the Automation rule name field, enter a name for your rule.
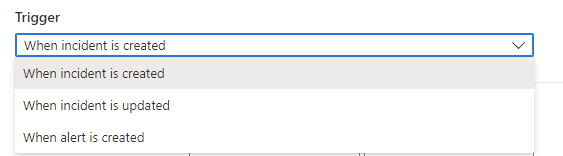
Choose your trigger
From the Trigger drop-down, select the appropriate trigger according to the circumstance for which you're creating the automation rule—When incident is created, When incident is updated, or When alert is created.
Define conditions
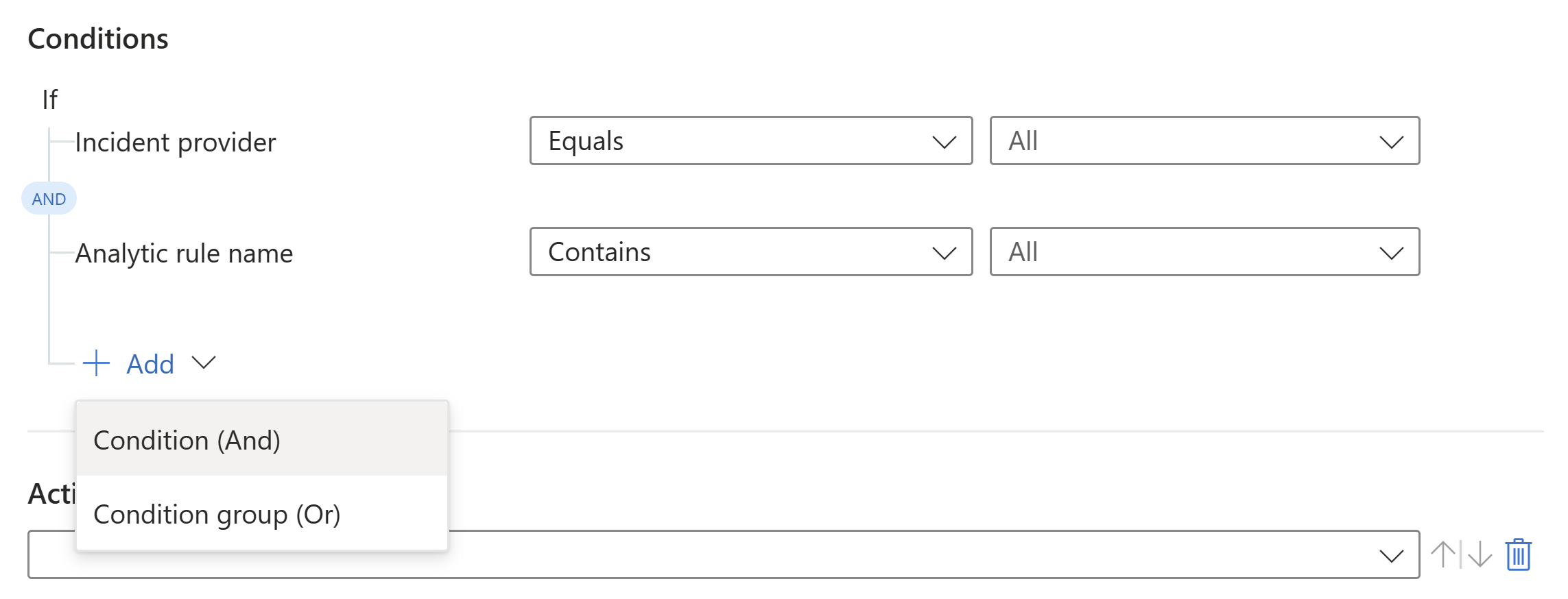
Use the options in the Conditions area to define conditions for your automation rule. All conditions are case insensitive.
Rules you create for when an alert is created support only the If Analytic rule name property in your condition. Select whether you want the rule to be inclusive (Contains) or exclusive (Does not contain), and then select the analytic rule name from the drop-down list.
Analytic rule name values include only analytics rules, and don't include other types of rules, such as threat intelligence or anomaly rules.
Rules you create for when an incident is created or updated support a large variety of conditions, depending on your environment. These options start with you've onboarded Microsoft Sentinel to the Defender portal:
If your workspace is onboarded to the Defender portal, start by selecting one of the following operators, in either the Azure or the Defender portal:
AND: individual conditions that are evaluated as a group. The rule executes if all the conditions of this type are met.
To work with the AND operator, select the + Add expander and choose Condition (And) from the drop-down list. The list of conditions is populated by incident property and entity property fields.
OR (also known as condition groups): groups of conditions, each of which are evaluated independently. The rule executes if one or more groups of conditions are true. To learn how to work with these complex types of conditions, see Add advanced conditions to automation rules.
For example:

If you selected When an incident is updated as the trigger, start by defining your conditions, and then adding extra operators and values as needed.
To define your conditions:
Select a property from the first drop-down box on the left. You can begin typing any part of a property name in the search box to dynamically filter the list, so you can find what you're looking for quickly.
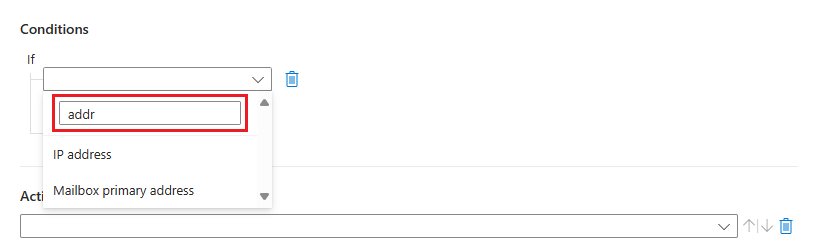
Select an operator from the next drop-down box to the right.
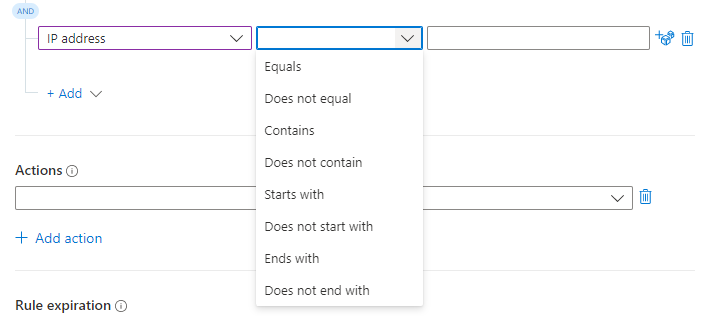
The list of operators you can choose from varies according to the selected trigger and property. When working in the Defender portal, we recommend that you use the Analytic rule name condition instead of an incident title.
Conditions available with the create trigger
Property Operator set - Title
- Description
- All listed entity properties
(see supported entity properties)- Equals/Does not equal
- Contains/Does not contain
- Starts with/Does not start with
- Ends with/Does not end with- Tag (See individual vs. collection) Any individual tag:
- Equals/Does not equal
- Contains/Does not contain
- Starts with/Does not start with
- Ends with/Does not end with
Collection of all tags:
- Contains/Does not contain- Severity
- Status
- Custom details key- Equals/Does not equal - Tactics
- Alert product names
- Custom details value
- Analytic rule name- Contains/Does not contain Conditions available with the update trigger
Property Operator set - Title
- Description
- All listed entity properties
(see supported entity properties)- Equals/Does not equal
- Contains/Does not contain
- Starts with/Does not start with
- Ends with/Does not end with- Tag (See individual vs. collection) Any individual tag:
- Equals/Does not equal
- Contains/Does not contain
- Starts with/Does not start with
- Ends with/Does not end with
Collection of all tags:
- Contains/Does not contain- Tag (in addition to above)
- Alerts
- Comments- Added - Severity
- Status- Equals/Does not equal
- Changed
- Changed from
- Changed to- Owner - Changed. If an incident's owner is updated via API, you must include the userPrincipalName or ObjectID for the change to be detected by automation rules. - Updated by
- Custom details key- Equals/Does not equal - Tactics - Contains/Does not contain
- Added- Alert product names
- Custom details value
- Analytic rule name- Contains/Does not contain Conditions available with the alert trigger
The only condition that can be evaluated by rules based on the alert creation trigger is which Microsoft Sentinel analytics rule created the alert.
Automation rules that are based on the alert trigger only run on alerts created by Microsoft Sentinel.
Enter a value in the field on the right. Depending on the property you chose, this might be either a text box or a drop-down in which you select from a closed list of values. You might also be able to add several values by selecting the dice icon to the right of the text box.
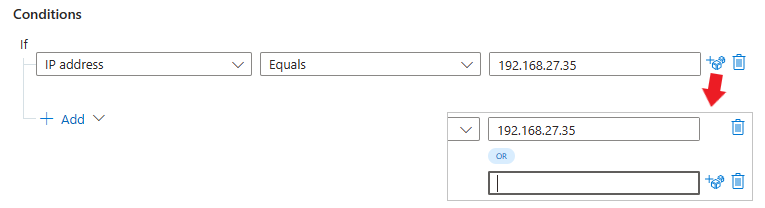
Again, for setting complex Or conditions with different fields, see Add advanced conditions to automation rules.
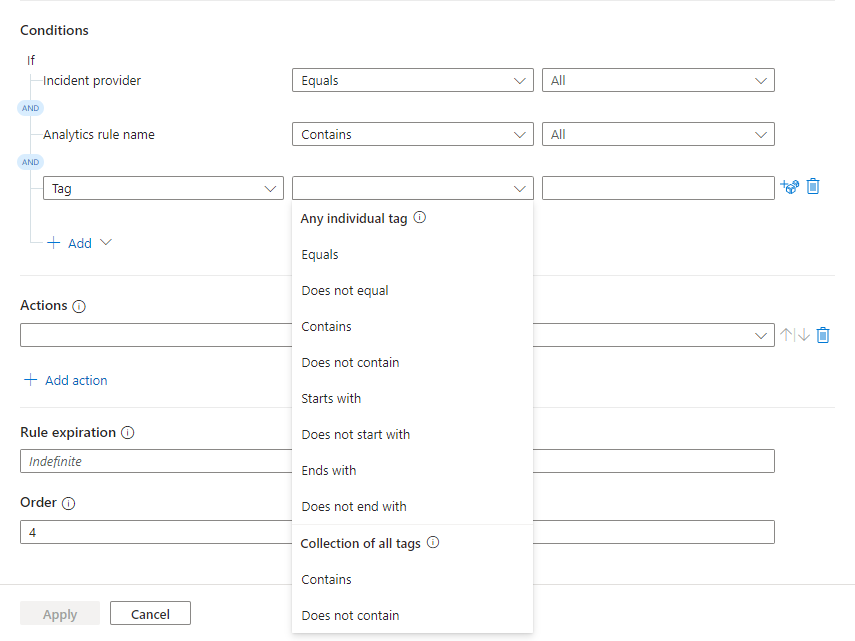
Conditions based on tags
You can create two kinds of conditions based on tags:
- Conditions with Any individual tag operators evaluate the specified value against every tag in the collection. The evaluation is true when at least one tag satisfies the condition.
- Conditions with Collection of all tags operators evaluate the specified value against the collection of tags as a single unit. The evaluation is true only if the collection as a whole satisfies the condition.
To add one of these conditions based on an incident's tags, take the following steps:
Create a new automation rule as described above.
Add a condition or a condition group.
Select Tag from the properties drop-down list.
Select the operators drop-down list to reveal the available operators to choose from.
See how the operators are divided in two categories as described before. Choose your operator carefully based on how you want the tags to be evaluated.
For more information, see Tag property: individual vs. collection.
Conditions based on custom details
You can set the value of a custom detail surfaced in an incident as a condition of an automation rule. Recall that custom details are data points in raw event log records that can be surfaced and displayed in alerts and the incidents generated from them. Use custom details to get to the actual relevant content in your alerts without having to dig through query results.
To add a condition based on a custom detail:
Create a new automation rule as described earlier.
Add a condition or a condition group.
Select Custom details key from the properties drop-down list. Select Equals or Does not equal from the operators drop-down list.
For the custom details condition, the values in the last drop-down list come from the custom details that were surfaced in all the analytics rules listed in the first condition. Select the custom detail you want to use as a condition.
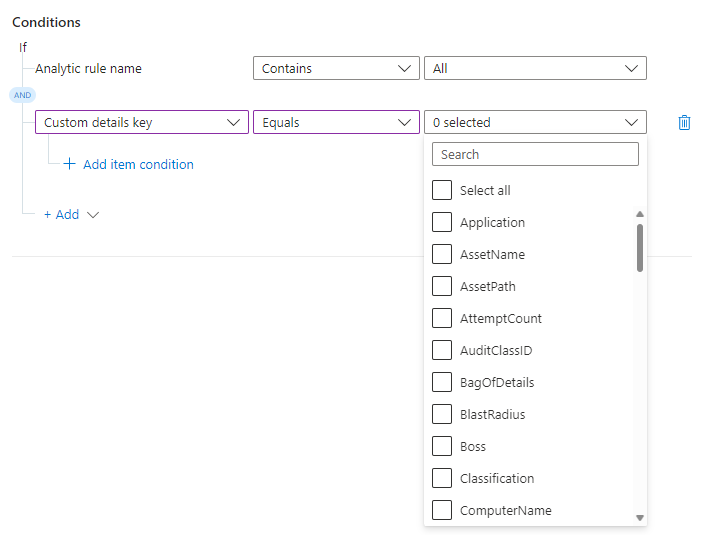
You chose the field you want to evaluate for this condition. Now specify the value appearing in that field that makes this condition evaluate to true.
Select + Add item condition.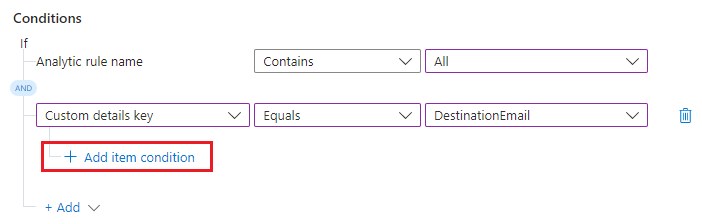
The value condition line appears below.

Select Contains or Does not contain from the operators drop-down list. In the text box to the right, enter the value for which you want the condition to evaluate to true.

In this example, if the incident has the custom detail DestinationEmail, and if the value of that detail is pwned@bad-botnet.com, the actions defined in the automation rule will run.
Add actions
Choose the actions you want this automation rule to take. Available actions include Assign owner, Change status, Change severity, Add tags, and Run playbook. You can add as many actions as you like.
Note
Only the Run playbook action is available in automation rules using the alert trigger.
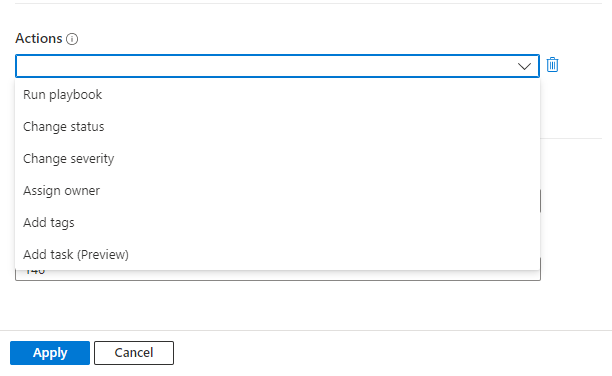
For whichever action you choose, fill out the fields that appear for that action according to what you want done.
If you add a Run playbook action, you're prompted to choose from the drop-down list of available playbooks.
Only playbooks that start with the incident trigger can be run from automation rules using one of the incident triggers, so only they appear in the list. Likewise, only playbooks that start with the alert trigger are available in automation rules using the alert trigger.
Microsoft Sentinel must be granted explicit permissions in order to run playbooks. If a playbook appears unavailable in the drop-down list, it means that Sentinel doesn't have permissions to access that playbook's resource group. To assign permissions, select the Manage playbook permissions link.
In the Manage permissions panel that opens up, mark the check boxes of the resource groups containing the playbooks you want to run, and select Apply.
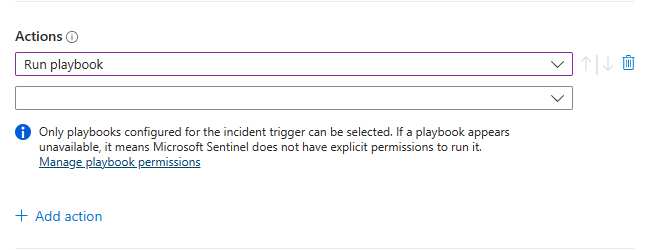
You yourself must have owner permissions on any resource group to which you want to grant Microsoft Sentinel permissions, and you must have the Microsoft Sentinel Automation Contributor role on any resource group containing playbooks you want to run.
If you don't yet have a playbook that takes the action that you want, create a new playbook. You have to exit the automation rule creation process and restart it after you create your playbook.
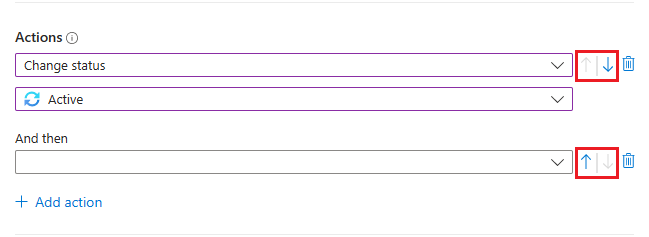
Move actions around
You can change the order of actions in your rule even after you've added them. Select the blue up or down arrows next to each action to move it up or down one step.
Finish creating your rule
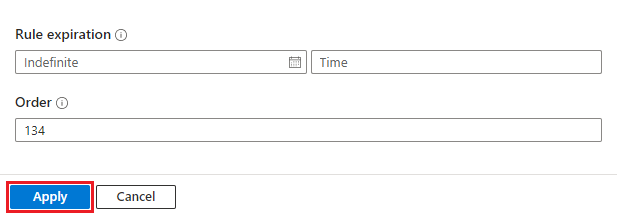
Under Rule expiration, if you want your automation rule to expire, set an expiration date, and optionally, a time. Otherwise, leave it as Indefinite.
The Order field is prepopulated with the next available number for your rule's trigger type. This number determines where in the sequence of automation rules (of the same trigger type) that this rule runs. You can change the number if you want this rule to run before an existing rule.
For more information, see Notes on execution order and priority.
Select Apply. You're done!
Audit automation rule activity
Find out what automation rules might have done to a given incident. You have a full record of incident chronicles available to you in the SecurityIncident table in the Logs page in the Azure portal, or the Advanced hunting page in the Defender portal. Use the following query to see all your automation rule activity:
SecurityIncident
| where ModifiedBy contains "Automation"
Automation rules execution
Automation rules run sequentially, according to the order that you determine. Each automation rule executes after the previous one finishes its run. Within an automation rule, all actions run sequentially in the order that they're defined. See Notes on execution order and priority for more information.
Playbook actions within an automation rule might be treated differently under some circumstances, according to the following criteria:
| Playbook run time | Automation rule advances to the next action... |
|---|---|
| Less than a second | Immediately after playbook is completed |
| Less than two minutes | Up to two minutes after playbook began running, but no more than 10 seconds after the playbook is completed |
| More than two minutes | Two minutes after playbook began running, regardless of whether or not it was completed |
Next steps
In this document, you learned how to use automation rules to centrally manage response automation for Microsoft Sentinel incidents and alerts.
- To learn how to add advanced conditions with
ORoperators to automation rules, see Add advanced conditions to Microsoft Sentinel automation rules. - To learn more about automation rules, see Automate incident handling in Microsoft Sentinel with automation rules
- To learn more about advanced automation options, see Automate threat response with playbooks in Microsoft Sentinel.
- To learn how to use automation rules to add tasks to incidents, see Create incident tasks in Microsoft Sentinel using automation rules.
- To migrate alert-trigger playbooks to be invoked by automation rules, see Migrate your Microsoft Sentinel alert-trigger playbooks to automation rules
- For help with implementing automation rules and playbooks, see Tutorial: Use playbooks to automate threat responses in Microsoft Sentinel.