Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
One of the pillars of Microsoft Defender for Cloud Apps is SaaS security posture management (SSPM). SSPM offers detailed visibility into the security state of your software as a service (SaaS) applications. It also provides actionable guidance to help you strengthen your security posture efficiently.
Defender for Cloud Apps provides security configuration assessments to help you identify and mitigate potential risks in your SaaS application environments. These recommendations appear in Microsoft Security Exposure Management after you have a connector to an application.
Additionally, Defender for Cloud Apps includes OAuth applications in both the Attack Path and Attack Surface Map experiences. To learn more, see How to investigate OAuth application attack paths in Defender for Cloud Apps (Preview)
Note
Microsoft Security Exposure Management data and capabilities are currently unavailable in US government clouds: GCC, GCC High, and DoD. For these environments, we recommend consuming SaaS security posture recommendations via Microsoft Secure Score.
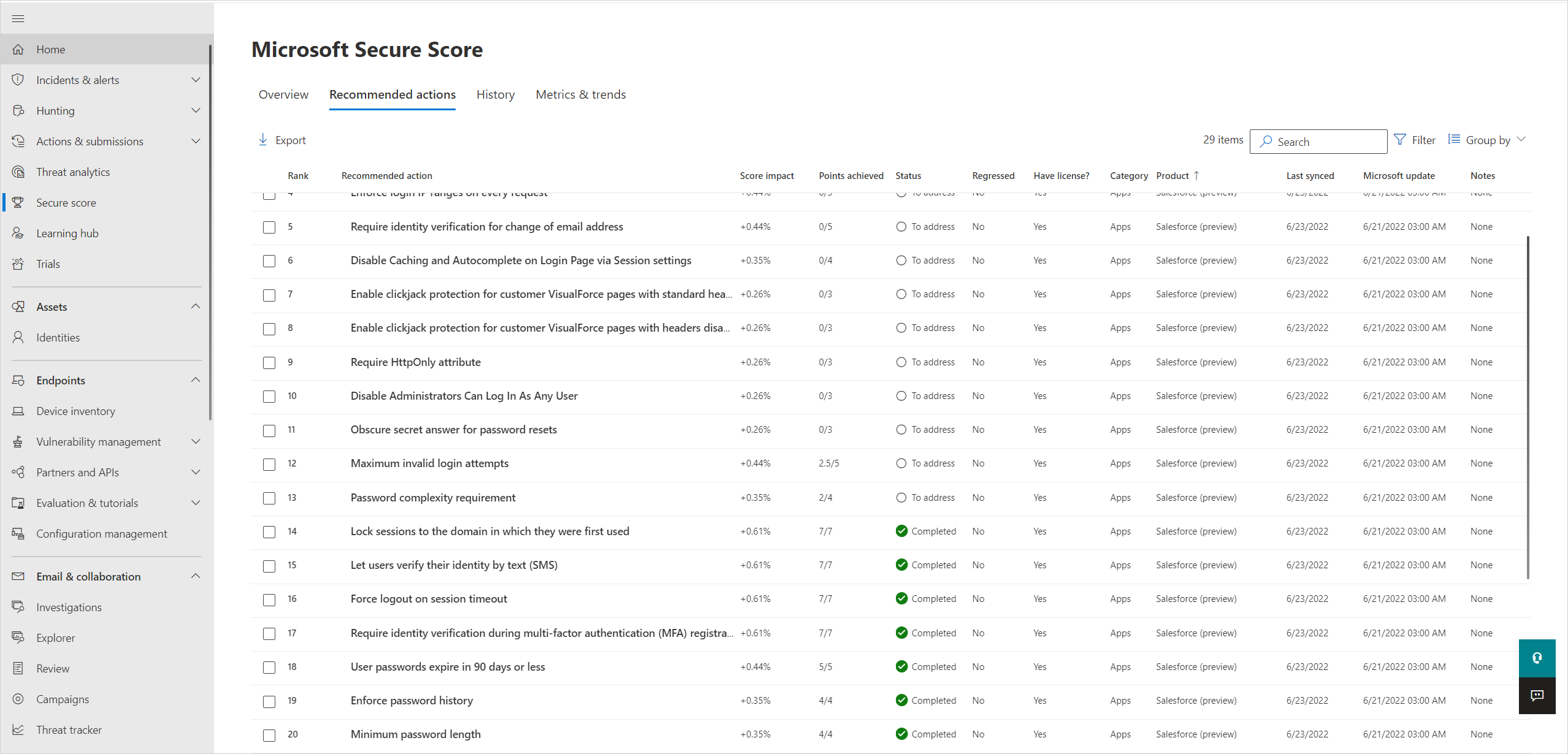
The following example shows Secure Score recommendations for a Salesforce app.
Prerequisites
- Your organization must have Microsoft Defender for Cloud Apps licenses.
- Your app must be connected to Defender for Cloud Apps. For information about connecting and about which of the app connectors provide security recommendations, see Connect apps to get visibility and control with Microsoft Defender for Cloud Apps.
Turn on SaaS security recommendations
To ensure that your application connector is set to show data in Microsoft Security Exposure Management, follow these steps:
In Microsoft Defender XDR, select Settings > Cloud Apps > Connected apps > App Connectors.
Use the filter to locate the application where you want to turn on security recommendations.
Open the instance drawer and note whether Security recommendations is turned on or off. The following example shows that Security recommendations is turned on.
If the instance is currently set to Off, select the ellipsis that denotes the options menu (...), and then select Turn on Security recommendations.
Note
If you have multiple instances of the same app, you can send security recommendations for each instance separately. Security recommendations for the selected instance are added to Microsoft Security Exposure Management in addition to the current recommendations.
Security recommendations appear automatically in Microsoft Security Exposure Management. Recommendations are based on Microsoft benchmarks, and they might take time to update.
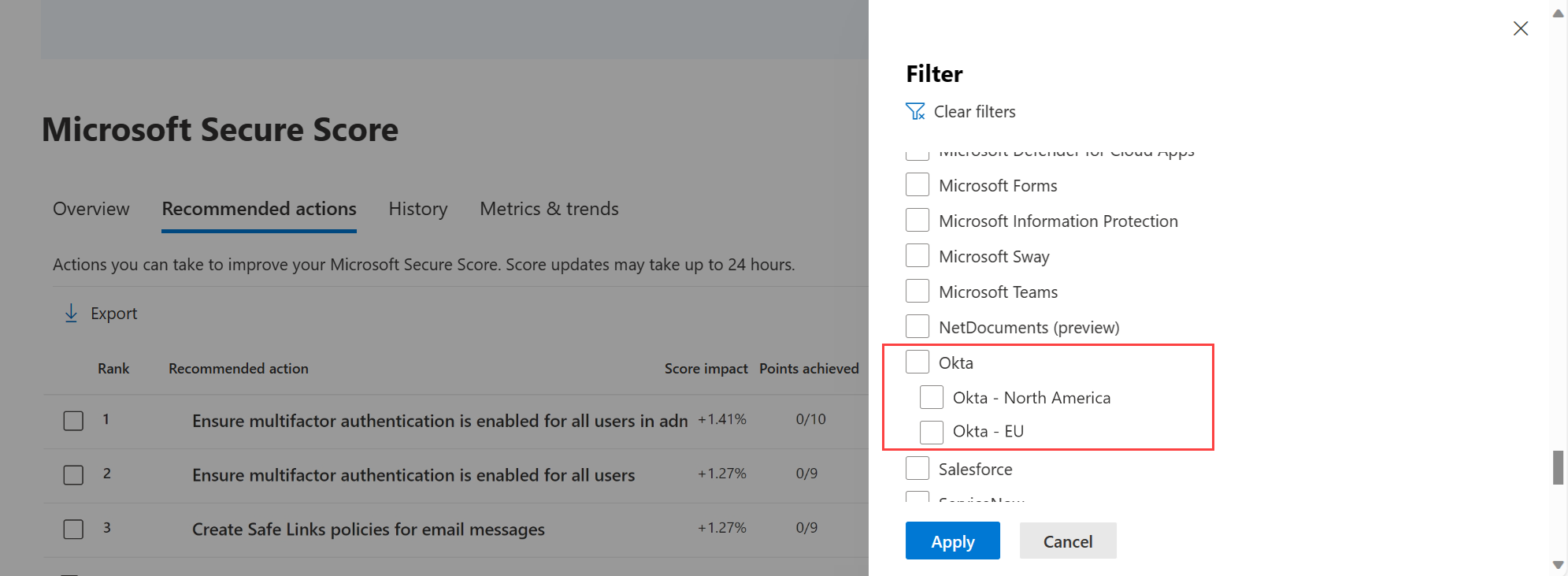
In Microsoft Secure Score, filter the Recommended actions tab by product to view any recommended actions. If you have multiple instances of an app, you can choose to filter recommendations from specific instances only. The following example shows options for filtering specific instances.
Select a recommendation, and then select the Implementation tab on the details pane for a step-by-step remediation guide.
For more information, see Assess your security posture with Microsoft Secure Score.
Manage your organization's SaaS security posture
To effectively manage your organization's SaaS security posture, we recommend beginning with the SaaS Security Initiative. This initiative consolidates best practices and measurable metrics specifically for securing SaaS applications, so that you can prioritize and address the most impactful recommendations for SaaS environments. The following example shows security metrics from the SaaS Security Initiative.
You can also find various SSPM recommendations under other initiatives:
- CIS Microsoft 365 Foundations Benchmark
- Ransomware Protection
- Identity Security
- Business Email Compromise (financial fraud)
- Zero Trust (foundational)
[Preview] After you configure your SaaS posture recommendations, use the attack paths capability to expand your investigation. Attack paths show how an attacker might move laterally from a vulnerable entry point, through an OAuth application, to gain high privileges in your Microsoft 365 SaaS environment. This visibility helps you investigate potential threats and take steps to remediate them. To learn more, see How to investigate OAuth application attack paths in Defender for Cloud Apps (Preview)
Next step
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.