Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article provides Microsoft Defender for Cloud Apps admins with guidance on how to investigate and resolve common access and session control issues as experienced by admins.
Note
Any troubleshooting related to proxy functionality is only relevant for sessions that are not configured for in-browser protection with Microsoft Edge.
Check minimum requirements
Before you start troubleshooting, make sure your environment meets the following minimum general requirements for access and session controls.
| Requirement | Description |
|---|---|
| Licensing | Make sure you have a valid license for Microsoft Defender for Cloud Apps. |
| Single Sign-On (SSO) | Apps must be configured with one of the supported SSO solutions: - Microsoft Entra ID using SAML 2.0 or OpenID Connect 2.0 - Non-Microsoft IdP using SAML 2.0 |
| Browser support | Session controls are available for browser-based sessions on the latest versions of the following browsers: - Microsoft Edge - Google Chrome - Mozilla Firefox - Apple Safari In-browser protection for Microsoft Edge also has specific requirements, including the user signed in with their work profile. For more information, see In-browser protection requirements. |
| Downtime | Defender for Cloud Apps allows you to define the default behavior to apply if there's a service disruption, such as a component not functioning correctly. For example, when the normal policy controls can't be enforced, you might choose to harden (block) or bypass (allow) users from taking actions on potentially sensitive content. To configure the default behavior during system downtime, in Microsoft Defender XDR, go to Settings > Conditional Access App Control > Default behavior > Allow or Block access. |
In-browser protection requirements
If you're using in-browser protection with Microsoft Edge and are still being served by a reverse proxy, make sure you meet the following additional requirements:
The feature is turned on in your Defender XDR settings. For more information, see Configure in-browser protection settings.
All policies that the user is covered by are supported for Microsoft Edge for Business. If a user is served by another policy that's not supported by Microsoft Edge for Business, they're always served by the reverse proxy. For more information, see In-browser protection requirements.
You're using a supported platform, including a supported operating system, identity platform, and Edge version. For more information, see In-browser protection requirements.
Reference of troubleshooting issues for admins
Use the following table to find the issue you're trying to troubleshoot:
Network condition issues
Common network condition issues you might encounter include:
Network errors when navigating to a browser page
When you're first setting up Defender for Cloud Apps access and session controls for an app, common network errors that might arise include: This site isn't secure and There's no internet connection. These messages can indicate a general network configuration error.
Recommended steps
Configure your firewall to work with Defender for Cloud Apps using the Azure IP addresses and DNS names relevant to your environment.
- Add outbound port 443 for the following IP addresses and DNS names for your Defender for Cloud Apps data center.
- Restart your device and your browser session
- Verify that the sign-in is working as expected
Enable TLS 1.2 in your browser's internet options. For example:
Browser Steps Microsoft Internet Explorer 1. Open Internet Explorer
2. Select Tools > Internet Options > Advance tab
3. Under Security, select TLS 1.2
4. Select Apply, and then select OK
5. Restart your browser and verify that you can access the appMicrosoft Edge / Edge Chromium 1. Open search from the taskbar and search for "Internet Options"
2. Select Internet Options
3. Under Security, select TLS 1.2
4. Select Apply, and then select OK
5. Restart your browser and verify that you can access the appGoogle Chrome 1. Open Google Chrome
2. At the top-right, select More (3 vertical dots) > Settings
3. At the bottom, select Advanced
4. Under System, select Open proxy settings
5. On the Advanced tab, under Security, select TLS 1.2
6. Select OK
7. Restart your browser and verify that you're able to access the appMozilla Firefox 1. Open Mozilla Firefox
2. In the address bar and search for "about:config"
3. In the Search box, search for "TLS"
4. Double-click the entry for security.tls.version.min
5. Set the integer value to 3 to force TLS 1.2 as the minimum required version
6. Select Save (check mark to the right of the value box)
7. Restart your browser and verify that you're able to access the appSafari If you're using Safari version 7 or greater, TLS 1.2 is automatically enabled
Defender for Cloud Apps uses Transport Layer Security (TLS) protocols 1.2+ to provide best-in-class encryption:
- Native client apps and browsers that don't support TLS 1.2+ aren't accessible when configured with session control.
- SaaS apps that use TLS 1.1 or lower appear in the browser as using TLS 1.2+ when configured with Defender for Cloud Apps.
Tip
While session controls are built to work with any browser on any major platform on any operating system, we support the latest versions of Microsoft Edge, Google Chrome, Mozilla Firefox, or Apple Safari. You might want to block or allow access specifically to mobile or desktop apps.
Slow sign-ins
Proxy chaining and nonce-handling are some of the common issues that could result in slow sign-in performance.
Recommended steps
Configure your environment to remove any factors that might be causing slowness during sign-in. For example, you might have firewalls or forward proxy chaining configured, which connects two or more proxy servers to navigate to the intended page. You might also have other external factors affecting the slowness.
- Identify whether proxy chaining is occurring in your environment.
- Remove any forward proxies where possible.
Some apps use a nonce hash during authentication to prevent replay attacks. By default, Defender for Cloud Apps assumes that an app uses a nonce. If the app you're working with doesn't use nonce, disable nonce-handling for this app in Defender for Cloud Apps:
- In Microsoft Defender XDR, select Settings > Cloud Apps.
- Under Connected apps, select Conditional Access App Control apps.
- In the list of apps, on the row in which the app you're configuring appears, select the three dots at the end of the row, and then select Edit for your app.
- Select Nonce-handling to expand the section and then clear Enable nonce handling.
- Sign out of the app and close out all browser sessions.
- Restart your browser and sign-in to the app again. Verify that the sign-in is working as expected.
More considerations for network conditions
While troubleshooting network conditions, also consider the following notes about the Defender for Cloud Apps proxy:
Verify whether your session is being routed to another data center: Defender for Cloud Apps uses Azure Data Centers around the world to optimize performance through geolocation.
This means that a user's session might be hosted outside of a region, depending on traffic patterns and their location. However, to protect your privacy, no session data is stored in these data centers.
Proxy performance: Deriving a performance baseline depends on many factors outside of the Defender for Cloud Apps proxy, such as:
- What other proxies or gateways sit in series with this proxy
- Where the user is coming from
- Where the targeted resource resides
- Specific requests on the page
In general, any proxy adds latency. The advantages of the Defender for Cloud Apps proxy are:
Using the global availability of Azure domain controllers to geolocate users to the nearest node and reduce their round-trip distance. Azure domain controllers can geolocate on a scale that few services around the world have.
Using the integration with Microsoft Entra Conditional Access to only route the sessions you want to proxy to our service, instead of all users in all situations.
Device identification issues
Defender for Cloud Apps provides the following options for identifying a device's management state.
- Microsoft Intune compliance
- Hybrid Microsoft Entra Domain joined
- Client certificates
For more information, see Identity-managed devices with Conditional Access app control.
Common device identification issues you might encounter include:
- Misidentified Intune Compliant or Microsoft Entra hybrid joined devices
- Client certificates aren't prompting when expected
- Client certificates are prompting at every sign-in
- Extra considerations
Misidentified Intune Compliant or Microsoft Entra hybrid joined devices
Microsoft Entra Conditional Access enables Intune-compliant and Microsoft Entra hybrid joined device information to be passed directly to Defender for Cloud Apps. In Defender for Cloud Apps, use the device state as a filter for access or session policies.
For more information, see Introduction to device management in Microsoft Entra ID.
Recommended steps
In Microsoft Defender XDR, select Settings > Cloud Apps.
Under Conditional Access App Control, select Device identification. This page shows the device identification options available in Defender for Cloud Apps.
For Intune compliant device identification and Microsoft Entra hybrid joined identification respectively, select View configuration and verify that the services are set up. Services are automatically synced from Microsoft Entra ID and Intune respectively.
Create an access or session policy with the Device Tag filter equal to Hybrid Azure AD joined, Intune compliant, or both.
In a browser, sign in to a device that is Microsoft Entra hybrid joined or Intune compliant based on your policy filter.
Verify that activities from these devices are populating the log. In Defender for Cloud Apps, on the Activity log page, filter on Device Tag equal to Hybrid Azure AD joined, Intune compliant, or both based on your policy filters.
If activities aren't populating in the Defender for Cloud Apps activity log, go to Microsoft Entra ID and do the following steps:
Under Monitoring > Sign-ins, verify that there are sign-in activities in logs.
Select the relevant log entry for the device you logged into.
In the Details pane, on the Device info tab, verify that the device is Managed (Hybrid Azure AD joined) or Compliant (Intune compliant).
If you can't verify either state, try another log entry or ensure that your device data is configured correctly in Microsoft Entra ID.
For Conditional Access, some browsers may require extra configuration such as installing an extension. For more information, see Conditional Access browser support.
If you still don't see the device information in the Sign-ins page, open a support ticket for Microsoft Entra ID.
Client certificates aren't prompting when expected
The device identification mechanism can request authentication from relevant devices using client certificates. You can upload an X.509 root or intermediate certificate authority (CA) certificate, formatted in the PEM certificate format.
Certificates must contain the CA's public key, which is then used to sign the client certificates presented during a session. For more information, see Check for device management without Microsoft Entra.
Recommended steps
In Microsoft Defender XDR, select Settings > Cloud Apps.
Under Conditional Access App Control, select Device identification. This page shows the device identification options available with Defender for Cloud Apps.
Verify that you uploaded an X.509 root or intermediate CA certificate. You must upload the CA certificate that's used to sign for your certificate authority.
Create an access or session policy with the Device Tag filter equal to Valid client certificate.
Make sure that your client certificate is:
- Deployed using the PKCS #12 file format, typically a .p12 or .pfx file extension
- Installed in the user store, not the device store, of the device you're using for testing
Restart your browser session.
When logging in to the protected app:
- Verify that you're redirected to the following URL syntax:
<https://*.managed.access-control.cas.ms/aad_login> - If you're using iOS, make sure you're using the Safari browser.
- If you're using Firefox, you must also add the certificate to Firefox's own certificate store. All other browsers use the same default certificate store.
- Verify that you're redirected to the following URL syntax:
Validate that the client certificate is prompted in your browser.
If it doesn't appear, try a different browser. Most major browsers support performing a client certificate check. However, mobile and desktop apps often use built-in browsers that might not support this check and therefore affect authentication for these apps.
Verify that activities from these devices are populating the log. In Defender for Cloud Apps, on the Activity log page, add a filter on Device Tag equal to Valid client certificate.
If you still don't see the prompt, open a support ticket and include the following information:
- The details of the browser or native app where you experienced the problem
- The operating system version, such as iOS/Android/Windows 10
- Mention if the prompt is working on Microsoft Edge Chromium
Client certificates are prompting at every sign-in
If you're experiencing the client certificate popping up after opening a new tab, this might be due to settings hidden within Internet Options. Verify your settings in your browser. For example:
In Microsoft Internet Explorer:
- Open Internet Explorer and select Tools > Internet Options > Advanced tab.
- Under Security, select Don't prompt for Client Certificate selection when only one certificate exists > Select Apply > OK.
- Restart your browser and verify that you can access the app without the extra prompts.
In Microsoft Edge / Edge Chromium:
- Open search from the taskbar and search for Internet Options.
- Select Internet Options > Security > Local intranet > Custom level.
- Under Miscellaneous > Don't prompt for Client Certificate selection when only one certificate exists, select Disable.
- Select OK > Apply > OK.
- Restart your browser and verify that you can access the app without the extra prompts.
More considerations for device identification
While troubleshooting device identification, you can require certificate revocation for Client Certificates.
Certificates that are revoked by the CA are no longer trusted. Selecting this option requires all certificates to pass the CRL protocol. If your client certificate doesn't contain a CRL endpoint, you can't connect from the managed device.
Issues when onboarding an app
Microsoft Entra ID apps are automatically onboarded to Defender for Cloud Apps for Conditional Access and session controls. You must manually onboard non-Microsoft IdP apps, including both catalog and custom apps.
For more information, see:
- Deploy Conditional Access app control for catalog apps with non-Microsoft IdPs
- Deploy Conditional Access app control for custom apps with non-Microsoft IdPs
Common scenarios you might encounter while onboarding an app include:
- App doesn't appear on the Conditional Access App Control apps page
- App status: Continue Setup
- Can't configure controls for built-in apps
- Request session control option appears
App doesn't appear on the conditional access app control apps page
When onboarding an non-Microsoft IdP app to conditional access app control, the final deployment step is to have the end user navigate to the app. Do the steps in this section if the app isn't appearing on the Settings > Cloud apps > Connected apps > Conditional Access App Control apps page expected.
Recommended steps
Make sure your app meets the following Conditional Access app control prerequisites:
- Make sure you have a valid Defender for Cloud Apps license.
- Create a duplicate app.
- Make sure that the app uses the SAML protocol.
- Validate that you have fully onboarded the app and the status of the app is Connected.
Make sure to navigate to the app in a new browser session by using a new incognito mode or by signing in again.
Note
Entra ID apps only appear on the Conditional Access App Control apps page after they're configured in at least one policy, or if you have a policy without any app specification and a user has signed into the app.
App status: Continue Setup
An app's status can vary, and can include Continue Setup, Connected, or No Activities.
For apps connected via non-Microsoft identity providers (IdP), if the setup isn't complete, when accessing the app you see a page with the status of Continue Setup. Use the following steps to complete the setup.
Recommended steps
Select Continue Setup.
Review the following articles and verify that you've completed all the steps required:
- Deploy Conditional Access app control for catalog apps with non-Microsoft IdPs
- Deploy Conditional Access app control for custom apps with non-Microsoft IdPs
Pay special attention to the following steps:
- Make sure you create a new custom SAML app. You need this app to change the URLs and SAML attributes that might not be available in gallery apps.
- If your identity provider doesn't allow the reuse of the same identifier, also known as Entity ID or Audience, change the identifier of the original app.
Can't configure controls for built-in apps
Built-in apps can be detected heuristically and you can use access policies to monitor or block them. Use the following steps to configure controls for native apps.
Recommended steps
In an access policy, add a Client app filter, and set it equal to Mobile and desktop.
Under Actions, select Block.
Optionally, customize the blocking message that your users get when they're unable to download files. For example, customize this message to You must use a web browser to access this app.
Test and validate that the control is working as expected.
App isn't recognized page appears
Defender for Cloud Apps can recognize over 31,000 apps through the cloud app catalog.
If you're using a custom app that is configured through Microsoft Entra SSO, and isn't one of the supported apps, you come across an App is not recognized page. To resolve the issue, you must configure the app with Conditional Access app control.
Recommended steps
In Microsoft Defender XDR, select Settings > Cloud Apps. Under Connected apps, select Conditional Access App Control apps.
In the banner, select View new apps.
In the list of new apps, locate the app that you're onboarding, select the + sign, and then select Add.
- Select whether the app is a custom or standard app.
- Continue through the wizard, make sure that specified User-defined domains are correct for the app you're configuring.
Verify that the app appears in the Conditional Access App Control apps page.
Request session control option appears
After onboarding a non-Microsoft IdP app, you may see the Request session control option. This occurs because only catalog apps have out-of-the-box session controls. For any other app, you must go through a self-onboarding process.
Follow the instructions at Deploy Conditional Access app control for custom apps with non-Microsoft IdPs.
Recommended steps
In Microsoft Defender XDR, select Settings > Cloud Apps.
Under Conditional Access App Control, select App onboarding/maintenance.
Enter the principal name or email for the user who will be onboarding the app, and then select Save.
Go to the app that you're deploying. The page you see depends on whether the app is recognized. Do one of the following, depending on the page you see:
Not recognized. You see an App not recognized page that prompts you to configure your app. Do the following steps:
- Onboard the app for Conditional Access app control.
- Add the domains for the app.
- Install the app's certificates.
Recognized. If your app is recognized, you see an onboarding page prompting you to continue the app configuration process.
Make sure the app is configured with all domains required for the app to function correctly, and then return to the app page.
More considerations for onboarding apps
While troubleshooting for onboarding apps, there are some extra things to consider.
Understand the difference between the Microsoft Entra Conditional Access policy settings: "Monitor only", "Block downloads", and "Use custom policy"
In Microsoft Entra Conditional Access policies, you can configure the following built-in Defender for Cloud Apps controls: Monitor only and Block downloads. These settings apply and enforce the Defender for Cloud Apps proxy feature for cloud apps and conditions configured in Microsoft Entra ID.
For more complex policies, select Use custom policy, which allows you to configure access and session policies in Defender for Cloud Apps.
Understand the "Mobile and desktop" client app filter option in access policies
In Defender for Cloud Apps access policies, unless the Client app filter is set to Mobile and desktop, the resulting access policy applies to browser sessions.
The reason for this is to prevent inadvertently proxying user sessions, which might be a byproduct of using this filter.
Issues when creating access and session policies
Defender for Cloud Apps provides the following configurable policies:
- Access policies: Used to monitor or block access to browser, mobile, and/or desktop apps.
- Session policies. Used to monitor, block, and perform specific actions to prevent data infiltration and exfiltration scenarios in the browser.
To use these policies in Defender for Cloud Apps, you must first configure a policy in Microsoft Entra Conditional Access to extend session controls:
In the Microsoft Entra policy, under Access controls, select Session > Use Conditional Access App Control.
Select a built-in policy (Monitor only or Block downloads) or Use custom policy to set an advanced policy in Defender for Cloud Apps.
Select Select to continue.
Common scenarios you might encounter while configuring these policies include:
- In Conditional Access policies, you can't see the conditional access app control option
- Error message when creating a policy: You don't have any apps deployed with conditional access app control
- Can't create session policies for an app
- Can't choose Inspection Method: Data Classification Service
- Can't choose Action: Protect
In Conditional Access policies, you can't see the conditional access app control option
To route sessions to Defender for Cloud Apps, Microsoft Entra Conditional Access policies must be configured to include conditional access app control session controls.
Recommended steps
If you don't see the Conditional Access App Control option in your Conditional Access policy, make sure that you have a valid license for Microsoft Entra ID P1 and a valid Defender for Cloud Apps license.
Error message when creating a policy: You don't have any apps deployed with conditional access app control
When creating an access or session policy, you might see the following error message: You don't have any apps deployed with conditional access app control. This error indicates that the app is a non-Microsoft IdP app that hasn't been onboarded for Conditional Access app control.
Recommended steps
In Microsoft Defender XDR, select Settings > Cloud Apps. Under Connected apps, select Conditional Access App Control apps.
If you see the message No apps connected, use the following guides to deploy apps:
If you run into any issues while deploying the app, see Issues when onboarding an app.
Can't create session policies for an app
After onboarding a non-Microsoft IdP app for Conditional Access app control, in the Conditional Access App Control apps page, you may see the option: Request session control.
Note
Catalog apps have out-of-the-box session controls. For any other non-Microsoft IdP apps, you must go through a self-onboarding process. Recommended steps
Deploy your app to session control. For more information, see Onboard non-Microsoft IdP custom apps for Conditional Access app control.
Create a session policy and select the App filter.
Make sure that your app is now listed in the dropdown list.
Can't choose Inspection Method: Data Classification Service
In session policies, when using the Control file download (with inspection) session control type, you can use the Data Classification Service inspection method to scan your files in real time and detect sensitive content that matches any of the criteria you have configured.
If the Data Classification Service inspection method isn't available, use the following steps to investigate the issue.
Recommended steps
Verify that the Session control type is set to Control file download (with inspection).
Note
The Data Classification Service inspection method is only available for the Control file download (with inspection) option.
Determine whether the Data Classification Service feature is available in your region:
- If the feature isn't available in your region, use the Built-in DLP inspection method.
- If the feature is available in your region but you still can't see the Data Classification Service inspection method, open a support ticket.
Can't choose Action: Protect
In session policies, when using the Control file download (with inspection) session control type, in addition to the Monitor and Block actions, you can specify the Protect action. This action enables you to permit file downloads with the option to encrypt or apply permissions to the file based on conditions, content inspection, or both.
If the Protect action isn't available, use the following steps to investigate the issue.
Recommended steps
If the Protect action isn't available or is greyed out, verify that you have a Microsoft Purview license. For more information, see Microsoft Purview Information Protection integration.
If the Protect action is available, but aren't seeing the appropriate labels.
In Defender for Cloud Apps, in the menu bar, select the settings icon > Microsoft Information Protection, and verify that the integration is enabled.
For Office labels, in the Microsoft Purview portal, make sure Unified Labeling is selected.
Diagnose and troubleshoot with the Admin View toolbar
The Admin View toolbar sits at the bottom of your screen and provides tools for admin users to diagnose and troubleshoot issues with conditional access app control.
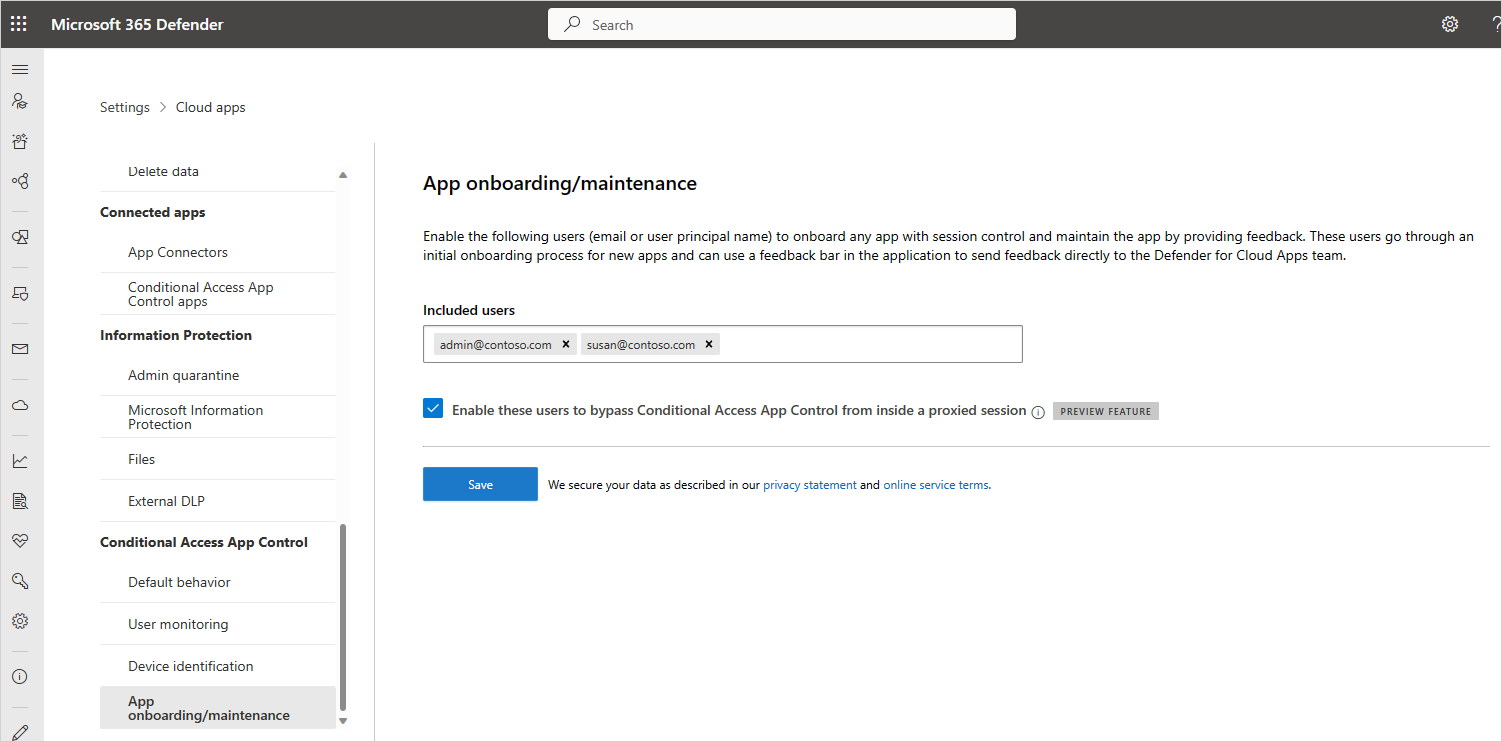
To view the Admin View toolbar, you must make sure to add specific admin user accounts to the App onboarding / maintenance list in the Microsoft Defender XDR settings.
To add a user to the App onboarding / maintenance list:
In Microsoft Defender XDR, select Settings > Cloud Apps.
Scroll down, and under Conditional Access App Control, select App onboarding/maintenance.
Enter the principal name or email address for the admin user you want to add.
Select the Enable these users to bypass Conditional Access App Control from inside a proxied session option, and then select Save.
For example:
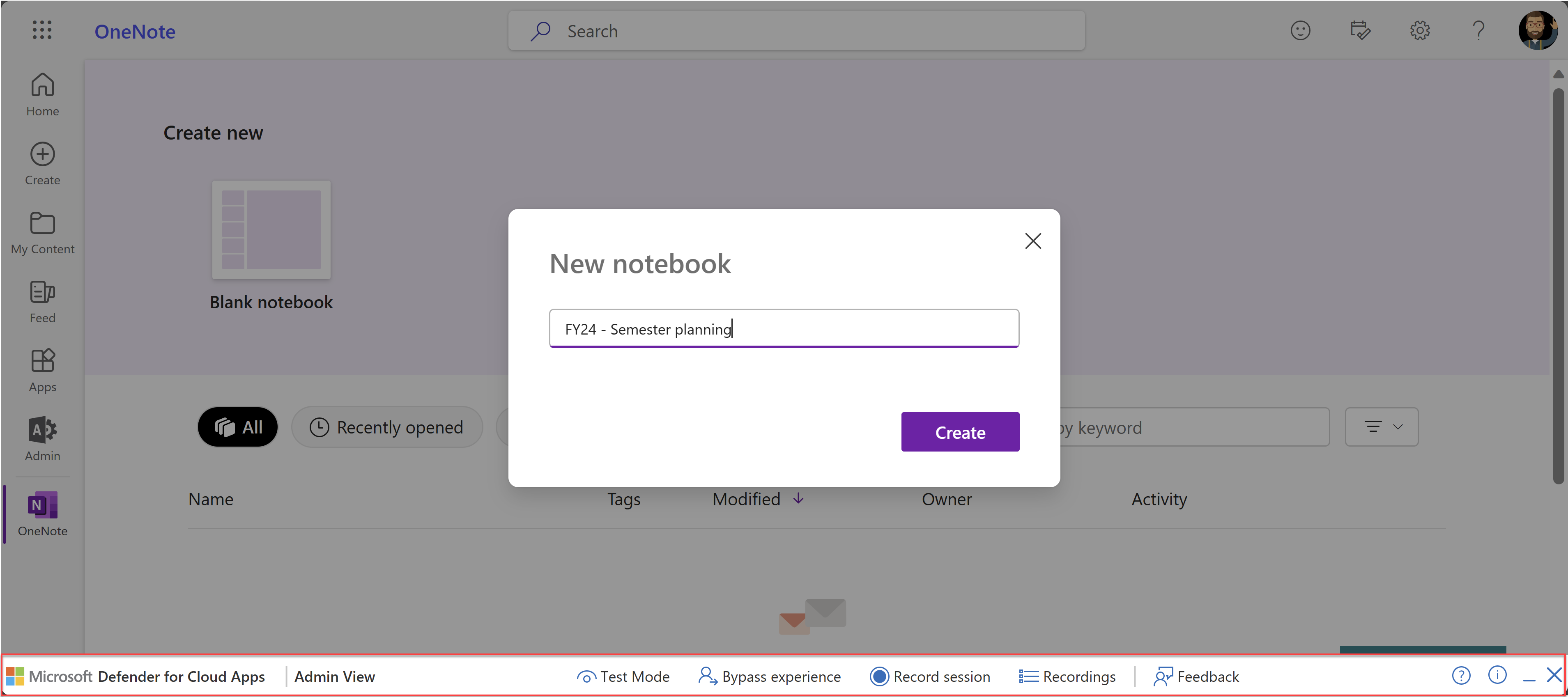
The next time that one of the listed users starts a new session in a supported app where they're an admin, the Admin View toolbar is shown at the bottom of the browser.
For example, the following image shows the Admin View toolbar showing at the bottom of a browser window, when using OneNote in the browser:
The following sections describe how to use the Admin View toolbar to test and troubleshoot.
Test mode
As an admin user, you might want to test upcoming proxy bug fixes before the latest release is fully rolled out to all tenants. Provide your feedback about the bug fix to the Microsoft support team to help speed up release cycles.
When in test mode, only the admin users are exposed to any changes provided in the bug fixes. There is no effect on other users.
- To turn on test mode, in the Admin View toolbar, select Test Mode.
- When you've finished your testing, select End Test Mode to return to the regular functionality.
Bypass proxy session
If you're using a non-Edge browser and have difficulty accessing or loading your application, you may want to verify whether the issue is with the Conditional Access proxy by running the application without the proxy.
To bypass the proxy, in the Admin View toolbar, select Bypass experience. Confirm that the session is bypassed by noting that the URL isn't suffixed.
The Conditional Access proxy is used again in your next session.
For more information, see Microsoft Defender for Cloud Apps Conditional Access app control and In-browser protection with Microsoft Edge for Business (Preview).
Second sign-in (also known as 'second login')
Some applications have more than one deep link to sign in. Unless you define the sign-in links in the app settings, users might be redirected to an unrecognized page when they sign in, blocking their access.
The integration between IdPs such as Microsoft Entra ID is based on intercepting an app sign-in and redirecting it. This means that browser sign-ins can't be controlled directly without triggering a second sign-in. To trigger a second sign-in, we need to employ a second sign-in URL specifically for that purpose.
If the app uses a nonce, the second sign-in might be transparent to users, or they are prompted to sign-in again.
If it isn't transparent to the end user, add the second sign-in URL to the app settings:
Go to Settings > Cloud apps > Connected apps > Conditional Access App Control Apps
Select the relevant app and then select the three dots.
Select Edit app\Advanced login configuration.
Add the second sign-in URL as mentioned in the error page.
If you're confident the app doesn't use a nonce, you can disable this by editing the apps settings as described in Slow sign-ins.
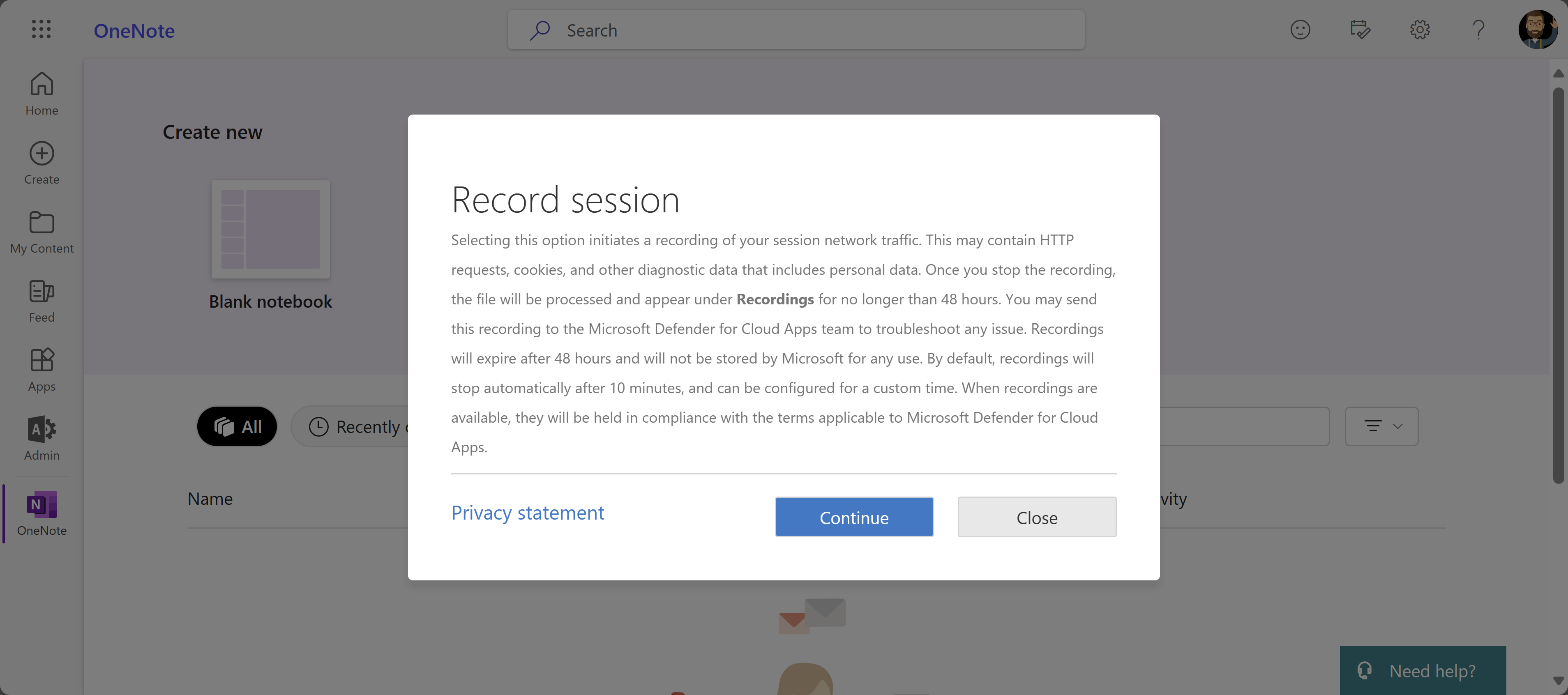
Record a session
You may want to help the root cause analysis of a problem by sending a session recording to Microsoft support engineers. Use the Admin View toolbar to record your session.
Note
All personal data is removed from the recordings.
To record a session:
In the Admin View toolbar, select Record session. When prompted, select Continue to accept the terms. For example:
Sign into your app if needed to begin simulating the session.
When you finish recording the scenario, make sure to select Stop recording in the Admin View toolbar.
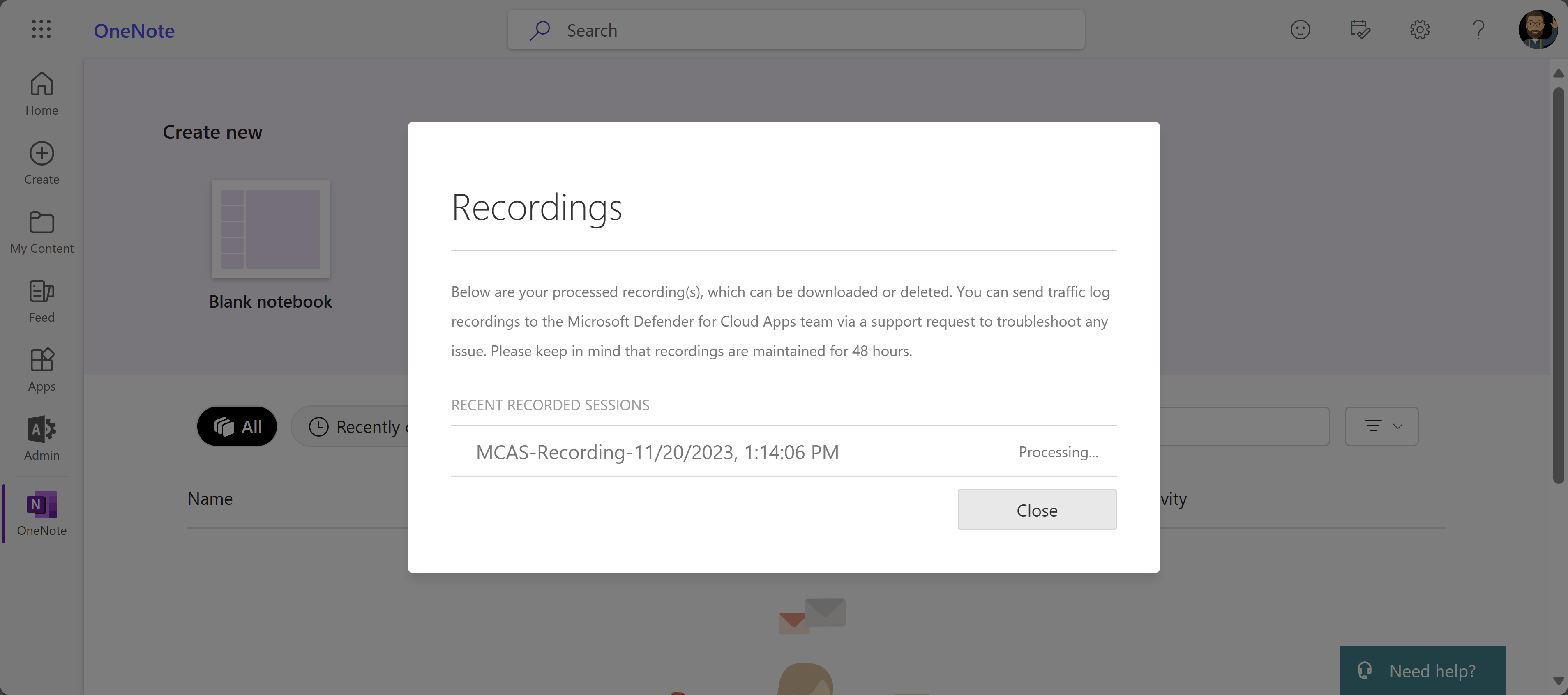
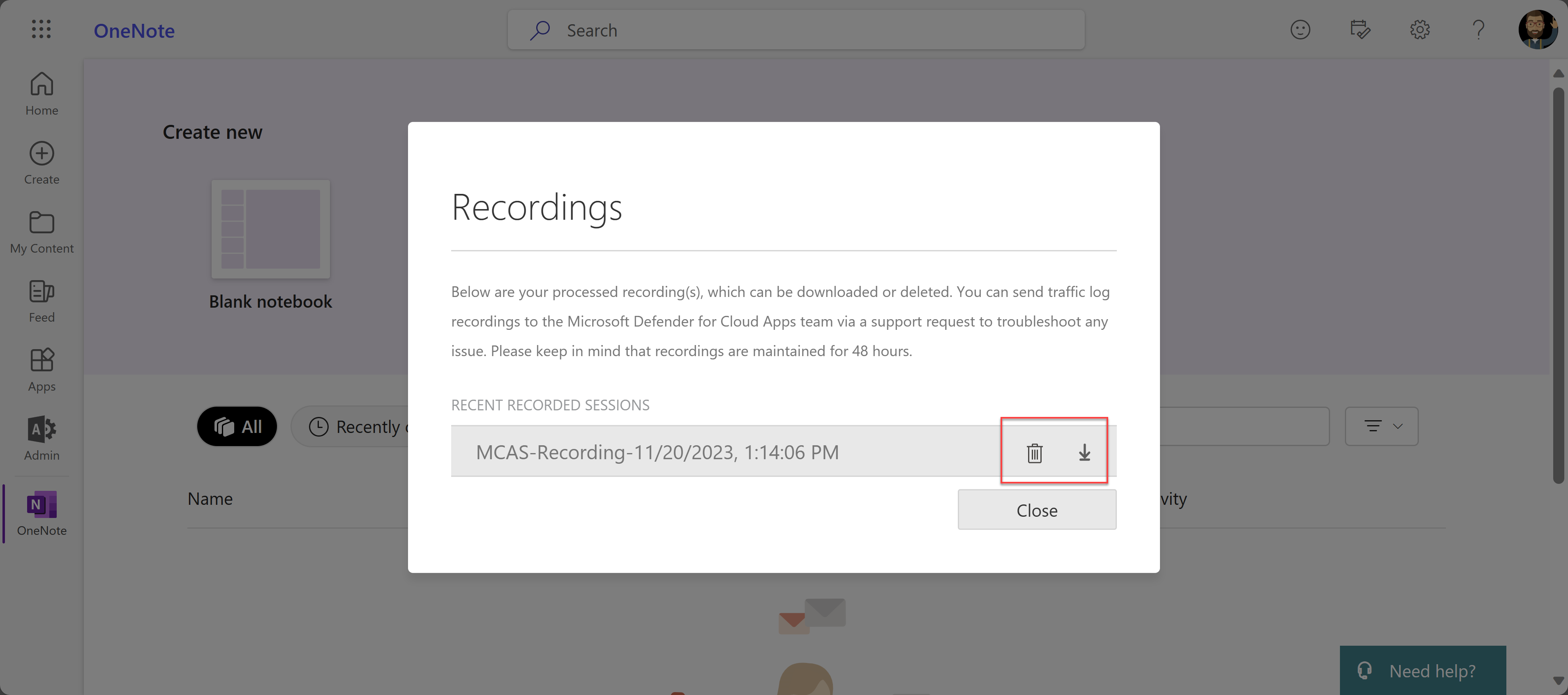
To view your recorded sessions:
After you've finished recording, view the recorded sessions by selecting Session recordings from the Admin View toolbar. A list of recorded sessions from the previous 48 hours appear. For example:
To manage your recordings, select a file and then select Delete or Download as needed. For example:
Add domains for your app
Associating the correct domains to an app allows Defender for Cloud Apps to enforce policies and audit activities.
For example, if you've configured a policy that blocks downloading files for an associated domain, file downloads by the app from that domain will be blocked. However, file downloads by the app from domains not associated with the app won't be blocked and the action won't be audited in the activity log.
If an admin browses in a proxied app to an unrecognized domain, that Defender for Cloud Apps doesn't consider to a part of the same app or any other app, the Unrecognized domain message appears, prompting the admin to add the domain so that it's protected next time. In such cases, if the admin doesn't want to add the domain, no action is needed.
Note
Defender for Cloud Apps still adds a suffix to domains not associated with the app to ensure a seamless user experience.
To add domains for your app:
Open your app in a browser, with the Defender for Cloud Apps Admin View toolbar visible on your screen.
In the Admin View toolbar, select Discovered domains.
In the Discovered domains pane, make a note of the domain names listed, or export the list as a .csv file.
The Discovered domains pane shows a list of all domains that are not associated with the app. The domain names are fully qualified.
In Microsoft Defender XDR, select Settings > Cloud Apps > Connected apps > Conditional Access App Control apps.
Locate your app in the table. Select the options menu on the right and then select Edit app.
In the User-defined domains field, enter the domains you want to associate with this app.
To view the list of domains already configured in the app, select the View app domains link.
When adding domains, consider whether you want to add specific domains, or use an asterisk (*****as a wildcard to use multiple domains at once.
For example,
sub1.contoso.com,sub2.contoso.comare examples of specific domains. To add both of these domains at once, as well as other sibling domains, use*.contoso.com.
For more information, see Protect apps with Microsoft Defender for Cloud Apps Conditional Access app control.