Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
As an admin in Microsoft 365, you might have company requirements to restrict or control automatically forwarded messages to external recipients (recipients outside of your organization). Email forwarding can be useful, but can also pose a security risk due to the potential disclosure of information. Attackers might use this information to attack your organization or partners.
The following types of automatic forwarding are available in Microsoft 365:
- Users can configure Inbox rules to automatically forward messages to external senders (deliberately or as a result of a compromised account).
- Admins can configure mailbox forwarding (also known as SMTP forwarding) to automatically forward messages to external recipients. The admin can choose whether to forward messages, or keep copies of forwarded messages in the mailbox.
Tip
Users with automatic forwarding from on-premises email systems through Microsoft 365 are subject to the same policy controls as cloud mailboxes.
You can use outbound spam filter policies to control automatic forwarding to external recipients. Three settings are available:
- Automatic - System-controlled: This is the default value. This value is now the same as Off - Forwarding is disabled. When this value was originally introduced, it was equivalent to On - Forwarding is enabled. Over time, thanks to the principles of secure by default, the effect of this value was eventually changed to Off - Forwarding is disabled for all customers. For more information, see this blog post.
- On - Forwarding is enabled: Automatic external forwarding is allowed and not restricted.
- Off - Forwarding is disabled: Automatic external forwarding is disabled and results in a non-delivery report (also known as an NDR or bounce message) to the sender.
For instructions on how to configure these settings, see Configure outbound spam filtering in EOP.
Note
- Disabling automatic forwarding disables any Inbox rules (users) or mailbox forwarding (admins) that redirect messages to external addresses.
- Automatic forwarding of messages between internal users isn't affected by the settings in outbound spam filter policies.
How the outbound spam filter policy settings work with other automatic email forwarding controls
As an admin, you might use other controls to allow or block automatic email forwarding. For example:
- Remote domains to allow or block automatic email forwarding to some or all external domains.
- Conditions and actions in Exchange mail flow rules (also known as transport rules) to detect and block automatically forwarded messages to external recipients.
When one setting allows external forwarding, but another setting blocks external forwarding, the block typically wins. Examples are described in the following table:
| Scenario | Result |
|---|---|
|
Automatically forwarded messages to recipients in the affected domains are blocked. |
|
Automatically forwarded messages to recipients in the affected domains are blocked. As described earlier, Automatic - System-controlled used to mean On, but the setting changed over time to mean Off in all organizations. For absolute clarity, you can configure your outbound spam filter policy to On or Off. |
|
Automatically forwarded messages to affected recipients are blocked by mail flow rules or remote domains. |
You can use this behavior (for example) to allow automatic forwarding in outbound spam filter policies, but use remote domains to control the external domains that users can forward messages to.
How to find users that are automatically forwarding
You can see information about users that are automatically forwarding messages to external recipients in the Auto forwarded messages report for cloud-based accounts.
For on-premises users that automatically forward from their on-premises email system through Microsoft 365, you need to create a mail flow rule to track these users. For general instructions on how to create a mail flow rule, see Use the EAC to create a mail flow rule.
Use the following information to create the mail flow rule in the Exchange admin center (EAC):
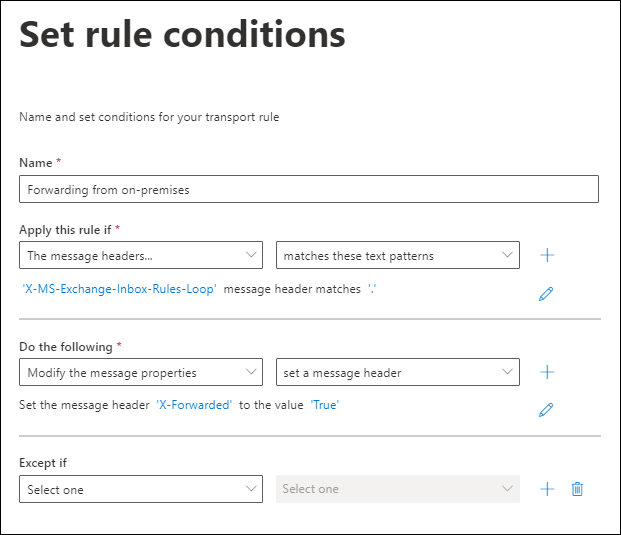
Set rule conditions page:
Apply this rule if (condition): The message headers > matches these text patterns.
- Select Enter text to specify the following header:
X-MS-Exchange-Inbox-Rules-Loop - Select Enter words to specify the following header value:
.(match any value for the header)
The condition looks like this: 'X-MS-Exchange-Inbox-Rules-Loop' message header matches '.'
- Select Enter text to specify the following header:
Do the following (action): Configure an appropriate action. For example, you can use the action Modify the message properties > set a message header, with the header name X-Forwarded and the value True.
Set rule settings page:
- Set the Severity value to Low, Medium, or High. This setting allows you to use the Exchange transport rule report to get details of users that are forwarding.
Blocked email forwarding messages
When a message is detected as automatically forwarded, and the outbound spam filter policy blocks that activity, the message is returned to the sender in an NDR that contains the following information:
5.7.520 Access denied, Your organization does not allow external forwarding. Please contact your administrator for further assistance. AS(7555)