Microsoft Defender for Endpoint in the Microsoft Defender portal
Applies to:
This article describes the Defender for Endpoint experience in the Microsoft Defender portal (https://security.microsoft.com). Formerly, Defender for Endpoint customers used the Microsoft Defender Security Center (https://securitycenter.windows.com or https://securitycenter.microsoft.com).
Quick reference
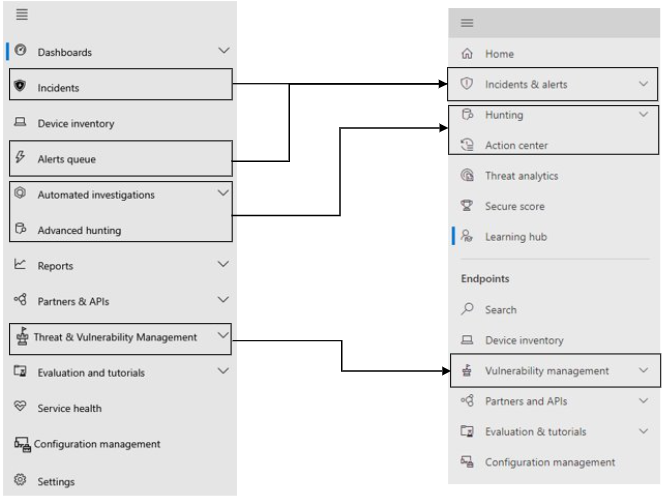
The image and the table below lists the changes in navigation between the Microsoft Defender Security Center and the Microsoft Defender portal.
| Microsoft Defender Security Center | the Microsoft Defender portal |
|---|---|
Dashboards
|
Home
|
| Incidents | Incidents & alerts |
| Device inventory | Device inventory |
| Alerts queue | Incidents & alerts |
| Automated investigations | Action center |
| Advanced hunting | Hunting |
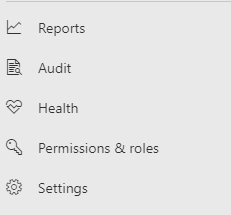
| Reports | Reports |
| Partners & APIs | Partners & APIs |
| Microsoft Defender Vulnerability Management | Vulnerability management |
| Evaluation and tutorials | Evaluation & tutorials |
| Configuration management | Configuration management |
| Settings | Settings |
The improved Microsoft Defender portal at https://security.microsoft.com combines security capabilities that protect, detect, investigate, and respond to email, collaboration, identity, and device threats. This brings together functionality from existing Microsoft security portals, including Microsoft Defender Security Center and the Office 365 Security & Compliance center.
If you're familiar with the Microsoft Defender Security Center, this article helps describe some of the changes and improvements in the Microsoft Defender portal. However there are some new and updated elements to be aware of.
Historically, the Microsoft Defender Security Center has been the home for Microsoft Defender for Endpoint. Enterprise security teams have used it to monitor and help responding to alerts of potential advanced persistent threat activity or data breaches. To help reduce the number of portals, the Microsoft Defender portal will be the home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure.
Microsoft Defender for Endpoint in the Microsoft Defender portal supports granting access to managed security service providers (MSSPs) in the same way access is granted in the Microsoft Defender Security Center.
Important
What you see in the Microsoft Defender portal depends on your current subscriptions. For example, if you don't have a license for Microsoft Defender for Office 365, then the Email & Collaboration section will not be shown.
Note
Microsoft Defender XDR is not fully available for:
- US Government Community Cloud (GCC)
- US Government Community Cloud High (GCC High)
- US Department of Defense
- All US government institutions with commercial licenses
- See availability for the above environments here: Microsoft Defender for Endpoint for US Government customers
Take a look in the Microsoft Defender portal at https://security.microsoft.com.
Learn more about the benefits: Overview of Microsoft Defender XDR
What's changed
This table is a quick reference of the changes between the Microsoft Defender Security Center and the Microsoft Defender portal.
Alerts and actions
| Area | Description of change |
|---|---|
| Incidents & alerts | In the Microsoft Defender portal, you can manage incidents and alerts across all of your endpoints, email, and identities. We've converged the experience to help you find related events more easily. For more information, see Incidents Overview. |
| Hunting | Modifying custom detection rules created in Microsoft Defender for Endpoint to include identity and email tables automatically moves them to the Microsoft Defender portal. Their corresponding alerts will also appear in the Microsoft Defender portal. For more details about these changes, read Migrate custom detection rules. The DeviceAlertEvents table for advanced hunting isn't available in the Microsoft Defender portal. To query device-specific alert information in the Microsoft Defender portal, you can use the AlertInfo and AlertEvidence tables to accommodate even more information from a diverse set of sources. Craft your next device-related query by following Write queries without DeviceAlertEvents. |
| Action center | Lists pending and completed actions that were taken following automated investigations and remediation actions. Formerly, the Action center in the Microsoft Defender Security Center listed pending and completed actions for remediation actions taken on devices only, while Automated investigations listed alerts and status. In the improved the Microsoft Defender portal, the Action center brings together remediation actions and investigations across email, devices, and users—all in one location. |
| Threat analytics | Moved to the top of the navigation bar for easier discovery and use. Now includes threat information for both endpoints and email and collaboration. |
Endpoints
| Area | Description of change |
|---|---|
| Search | The search bar is located at the top of the page. Suggestions are provided as you type. You can search across the following entities in Defender for Endpoint and Defender for Identity: - Devices - supported for both Defender for Endpoint and Defender for Identity. You can even use search operators, for example, you can use "contains" to search for part of a host name. - Users - supported for both Defender for Endpoint and Defender for Identity. - Files, IPs, and URLs - same capabilities as in Defender for Endpoint. NOTE: *IP and URL searches are exact match and don't appear in the search results page – they lead directly to the entity page. - MDVM - same capabilities as in Defender for Endpoint (vulnerabilities, software, and recommendations). The enhanced search results page centralizes the results from all entities. |
| Dashboard | This is your security operations dashboard. See an overview of how many active alerts were triggered, which devices are at risk, which users are at risk, and severity level for alerts, devices, and users. You can also see if any devices have sensor issues, your overall service health, and how any unresolved alerts were detected. |
| Device inventory | No changes. |
| Vulnerability management | Name was shortened to fit in the navigation pane. It's the same as the Microsoft Defender Vulnerability Management section, with all the pages underneath. |
| Partners and APIs | No changes. |
| Evaluations & tutorials | New testing and learning capabilities. |
| Configuration management | No changes. |
Note
Automatic investigation and remediation is now a part of incidents. You can see Automated investigation and remediation events in the Incident > Investigation tab.
Tip
Device search is done from Endpoints > Search.
Access and reporting
| Area | Description of change |
|---|---|
| Reports | See reports for endpoints and email & collaboration, including Threat protection, Device health and compliance, and Vulnerable devices. |
| Health | Currently links out to the "Service health" page in the Microsoft 365 admin center. |
| Settings | Manage your settings for the Microsoft Defender portal, Endpoints, Email & collaboration, Identities, and Device discovery. |
Microsoft 365 security navigation and capabilities
The left navigation, or quick launch bar, will look familiar. However, there are some new and updated elements in Microsoft Defender portal.
Incidents and alerts
Brings together incident and alert management across your email, devices, and identities. The alert page provides full context to the alert by combining attack signals to construct a detailed story. A new, unified experience now brings together a consistent view of alerts across workloads. You can quickly triage, investigate, and take effective action.
Hunting
Proactively search for threats, malware, and malicious activity across your endpoints, Office 365 mailboxes, and more by using advanced hunting queries. These powerful queries can be used to locate and review threat indicators and entities for both known and potential threats.
Custom detection rules can be built from advanced hunting queries to help you proactively watch for events that might be indicative of breach activity and misconfigured devices.
Action center
Action center shows you the investigations created by automated investigation and response capabilities. This automated, self-healing in the Microsoft Defender portal can help security teams by automatically responding to specific events.
Learn more about the Action center.
Threat Analytics
Get threat intelligence from expert Microsoft security researchers. Threat Analytics helps security teams be more efficient when facing emerging threats. Threat Analytics includes:
- Email-related detections and mitigations from Microsoft Defender for Office 365. This is in addition to the endpoint data already available from Microsoft Defender for Endpoint.
- Incidents view related to the threats.
- Enhanced experience for quickly identifying and using actionable information in the reports.
You can access threat analytics either from the upper left navigation bar in the Microsoft Defender portal, or from a dedicated dashboard card that shows the top threats for your organization.
Learn more about how to track and respond to emerging threats with threat analytics.
Endpoints section
View and manage the security of endpoints in your organization. If you've used the Microsoft Defender Security Center, it will look familiar.
Access and reports
View reports, change your settings, and modify user roles.
SIEM API connections
If you use the Defender for Endpoint SIEM API, you can continue to do so. We've added new links on the API payload that point to the alert page or the incident page in the Microsoft 365 security portal. New API fields include LinkToMTP and IncidentLinkToMTP. For more information, see Redirecting accounts from Microsoft Defender for Endpoint to The Microsoft Defender portal.
Email alerts
You can continue to use email alerts for Defender for Endpoint. We've added new links in the emails that point to the alert page or the incident page in The Microsoft Defender portal. For more information, see Redirecting accounts from Microsoft Defender for Endpoint to The Microsoft Defender portal.
Managed Security Service Providers (MSSP)
Logging in to multiple tenants simultaneously in the same browsing session is currently not supported in the unified portal. You can opt out of the automatic redirection by reverting to the former Microsoft Defender for Endpoint portal, to maintain this functionality until the issue is resolved.
Related information
- Microsoft Defender XDR
- Microsoft Defender for Endpoint in The Microsoft Defender portal
- Redirecting accounts from Microsoft Defender for Endpoint to The Microsoft Defender portal
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for