Business Central security for AL developers
This article helps you understand and improve the security of your Business Central app regardless of where it's hosted. In the following sections, you find guidance and recommended security best practices related to your app development lifecycle, and to what you as an AL developer need to know about authentication, authorization, auditing, and data encryption and secrets management.
Security development lifecycle (SDL)
The Microsoft Security Development Lifecycle (SDL) is a software development process that helps developers build more secure software and address security compliance requirements while reducing development cost.
For more information, see Security Development Lifecycle.
Layered security model in Business Central
Business Central uses a layered approach to application security, as outlined in the following diagram.
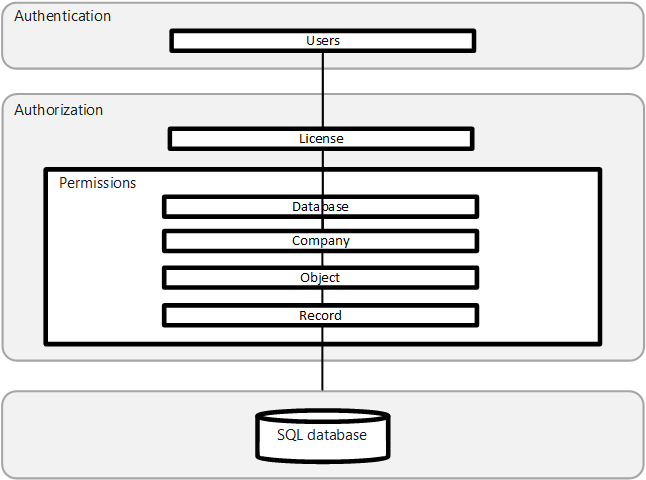
From AL, you can only affect the license and permission checks in the authorization layer. If you develop integrations with Business Central REST API, OData, or SOAP based web service endpoints, you also need to know how to deal with authentication for web service sessions.
Authentication for AL developers
Before a session can be created for a user in the Business Central server, the session must be authenticated as a valid user in the system. Business Central (on-premises) supports several authentication methods, such as Windows and Microsoft Entra ID. Business Central online deployments use Microsoft Entra ID only.
The following table includes links to help you understand authentication in Business Central.
| To | See |
|---|---|
| Learn about user session authentication in Business Central. | Authentication in Business Central |
| Learn about web service session authentication in Business Central REST API, OData, or SOAP based web service endpoints. | Authentication with OAuth Web Services Authentication (on-premises) Service-to-service authentication |
Authorization for AL developers
After a session is authenticated, the authorization step determines which areas the user of the session can access, such as code they can run, pages, and reports they can open, and the permissions they have on associated data.
The following table includes links to help you understand authorization in Business Central from the developer point of view.
| To | See |
|---|---|
| Learn how the entitlements are used to support the license part of authorization in Business Central online. | Entitlement object |
| Learn how entitlements can be used to support transactability for AppSource apps | Supporting transactability for AppSource apps |
| Learn how user permissions work in the application in Business Central. | User permissions in the application |
| Learn how to implement and extend permission sets in Business Central. | Permission sets and entitlements overview |
| Learn how to control access to data on the database, company, table, or record level using permissions. | Data Security Permissions on database objects |
| Learn how to use permissions to control visibility of UI elements. | Using permissions to hide elements in the User Interface |
Auditing for AL developers
Business Central includes several auditing features that help administrators track information about who is signing in, what their permissions are, what data they've changed, and more. As a developer, you can use some of these features to help you understand the security setup for your app and the stability of its permissions across customer installations.
The following table includes links to help you understand auditing in Business Central as seen from the developer point of view.
| To | See |
|---|---|
| See an overview of a users permissions. | Authorization Assessment |
| Monitor permission changes and stability with telemetry. | Permission changes telemetry Permission dependency cycle telemetry Permission error telemetry |
Encryption of data and secrets management for AL developers
Sensitive data in your application needs to be encrypted at rest, in transit, and in memory, and your app secrets should always be stored and processed in a safe manner.
The following table includes links to help you understand encryption in Business Central as seen from the developer point of view.
| To | See |
|---|---|
| Understand encryption at rest for data in Business Central. | Data isolation and encryption (online) Data isolation and encryption (on-premises) |
| Learn how to encrypt data in transit when calling external services from AL. | Supported cipher suites in HTTPS |
| Learn how to encrypt data in transit when calling Business Central REST API, OData, or SOAP based web service endpoints. | Business Central only supports HTTPS for web service endpoints. For on-premises installations, see Configuring SSL (on-premises) |
| To learn how to use the Isolated Storage feature to provide data isolation between extensions. | Isolated storage |
| To learn how to encrypt data in memory (to protect sensitive data from being exposed through the AL debugger when doing regular or snapshot debugging, or when an administrator takes a memory dump of the Business Central server process). | Protecting sensitive values with the SecretText data type |
| To safely store secrets for your app and retrieve them from AL. | Using Azure Key Vault for app secrets |
See also
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for