Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, we describe how to manually disable mDNS IP masking for browsers on Windows machines via the registry. To clarify, we aren't disabling mDNS itself, but its local Network Interface Card's (NIC) IP address obfuscation behavior in regard to WebRTC, just for the Microsoft eCDN and Teams domains.
Alternative methods achieved via the browser UI might exist but as they frequently change we don't cover them here.
As the concept can be a bit confusing, it might be more accurate to say that we're allowing WebRTC to expose the client's local IP to JavaScript in our domain on a per browser basis.
Important
If you have observed a decrease in peering efficiency during live events for browser users, refer to our updated Registry Keys guidance which now includes a second domain.
Purpose
This configuration change using the WebRtcLocalIpsAllowedUrls policy is a required component for enabling our browser-based client to participate in peering. Without this change, browser policy obfuscates the computer's local IP address from the JavaScript layer, which is essential for direct p2p in organizational networks.
Typically, mDNS's IP masking is first disabled manually on an individual basis for the testing and validating of Microsoft eCDN's P2P solution on a small-scale test set. Next, customers proceed to using Group Policy or an endpoint management system such as SCCM or Intune to make the change en mass across their environment.
Note
No such configuration change requirement applies to the Teams Desktop application as it already has access to the computer's IP address.
Multi-NIC caveat / limitation
There's a limitation with this method of exposing the local IP in that it only exposes the endpoint's most preferred NIC's IP address. This limitation is inconsequential for most users but can adversely affect browser viewers with multiple NICs by preventing them from being assigned to their intended subnet group.
A common example of such a potentially impacted endpoint is one with an always-on VPN.
Workaround
Granting the player's domain, typically https://teams.microsoft.com, microphone and/or camera permissions allows it to expose all NICs to the Microsoft eCDN service. Therefore allowing the multi-nic scenario logic to assign the endpoint to the appropriate subnet mapping group.
Caution
There is currently no workaround for the Viva Engage live events use case. A solution is in development and we’ll update this doc once available.
Registry Keys
Two registry entries are required to support peering with Microsoft eCDN. Each domain requires its own entry with a unique value name.
| Registry element | Value |
|---|---|
| Path for Edge | HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Edge\\ |
| Path for Chrome | HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Google\\Chrome\\ |
| Key name | WebRtcLocalIpsAllowedUrls |
| Value name | 1 or other numeric value |
| Value 1 | *.ecdn.teams.microsoft.com |
| Value 2 | https://teams.microsoft.com |
| Value 3 | *.ecdn.teams.cloud.microsoft |
| Value 4 | https://teams.cloud.microsoft |
Important
By the end of June 2025, in accordance with the Unified Domains initiative, we will have transitioned domains from *.teams.microsoft.com to *.teams.cloud.microsoft. We urge customers to add the new domain(s) to their firewall, proxy, VPN, and/or mDNS configurations as soon as possible. The transition is not a clean cut-over but gradual, so both versions are required during the transition period, beginning June 1st.
Tip
Customers who have a third party integration, such as MediaPlatform, may see improved performance by also adding the third party platform's domain(s). Reach out to your third party provider for the specific video platform's domain, which may differ from the organization's website's domain.
Firefox support
The configuration for Firefox is slightly different. Only one registry entry, value data, contains the domains, separated by a comma.
| Registry element | Value |
|---|---|
| Path for Firefox | HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Mozilla\\Firefox\\ |
| Key name | Preferences |
| Value name | media.peerconnection.ice.obfuscate_host_addresses.blocklist |
| Value | *.ecdn.teams.microsoft.com, https://teams.microsoft.com, *.ecdn.teams.cloud.microsoft, https://teams.cloud.microsoft |
Common issue
The key for the required REG_SZ (string) value might not exist.
Example scenario for Microsoft Edge
Here we see that a subkey isn't present in the hierarchy under the Edge key as expected.
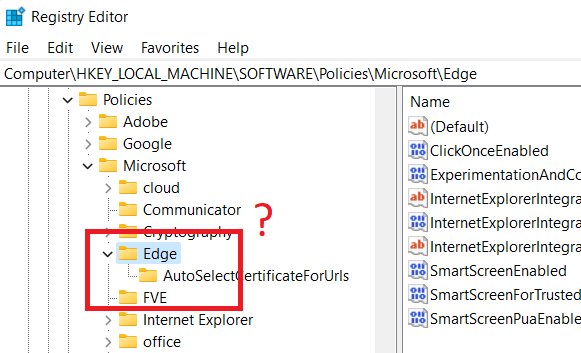
In this particular scenario, only the WebRtcLocalIpsAllowedUrls key is missing but it's also plausible for a key farther up in the hierarchy to be missing such as Edge, Chrome, or Google, even if the corresponding browser is installed.
Solution
The steps to resolve this scenario are straightforward.
Create the missing keys.
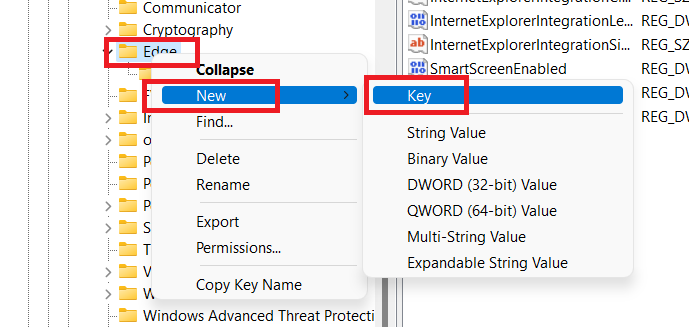
Input key name.
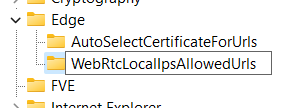
Continue creating missing keys down the hierarchy as necessary.
In the
WebRtcLocalIpsAllowedUrlskey, create the string value, setting value name to1or another available numerical value, and value data to*.ecdn.teams.microsoft.com.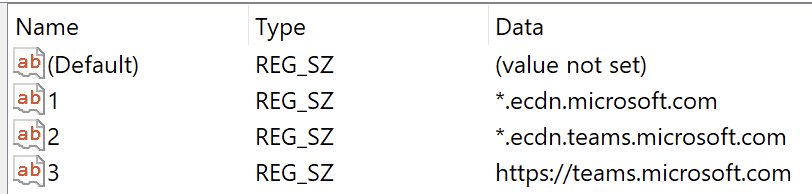
Repeat the necessary steps for the other URLs.
Important
Remember to restart the browser or the computer to apply the changes.
Tip
To quickly and easily restart the browser, you can use the following shortcut URLs:
edge://restart
chrome://restart
about:restartrequired
Complete! Now mDNS is disabled on Microsoft Edge for the Microsoft eCDN domain.