Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Organizations that use Conditional Access along with the Global Secure Access can prevent malicious access to Microsoft apps, third-party SaaS apps, and private line-of-business (LoB) apps using multiple conditions to provide defense-in-depth. These conditions might include strong factor authentication, device compliance, location, and others. Enabling these conditions protects your organization against user identity compromise or token theft. Global Secure Access introduces the concept of a compliant network within Microsoft Entra ID Conditional Access. This compliant network check ensures users connect via the Global Secure Access service for their specific tenant and are compliant with security policies enforced by administrators.
The Global Secure Access Client installed on devices or users behind configured remote networks allows administrators to secure resources behind a compliant network with advanced Conditional Access controls. This compliant network feature makes it easier for administrators to manage access policies, without having to maintain a list of egress IP addresses and removes the requirement to hairpin traffic through organization's VPN in order to maintain source IP anchoring and apply IP-based Conditional Access policies. To learn more about Conditional Access, see What is Conditional Access?
Compliant network check enforcement
Compliant network enforcement reduces the risk of token theft/replay attacks. Authentication plane enforcement is performed by Microsoft Entra ID at the time of user authentication. If an adversary has stolen a session token and attempts to replay it from a device that is not connected to your organization’s compliant network (for example, requesting an access token with a stolen refresh token), Entra ID will immediately deny the request and further access will be blocked. Data plane enforcement works with services integrated with Global Secure Access and that support Continuous Access Evaluation (CAE) - currently, Microsoft Graph. With apps that support CAE, stolen access tokens that are replayed outside your tenant’s compliant network will be rejected by the application in near-real time. Without CAE, a stolen access token will last up to its full lifetime (default is between 60 and 90 minutes).
This compliant network check is specific to the tenant in which it is configured. For example, if you define a Conditional Access policy requiring compliant network in contoso.com, only users with the Global Secure Access or with the Remote Network configuration are capable of passing this control. A user from fabrikam.com will not be able to pass contoso.com's compliant network policy.
The compliant network is different than IPv4, IPv6, or geographic locations you might configure in Microsoft Entra. Administrators are not required to review and maintain compliant network IP addresses/ranges, strengthening the security posture and minimizing the administrative overhead.
Prerequisites
- Administrators who interact with Global Secure Access features must have one or more of the following role assignments depending on the tasks they're performing.
- The Global Secure Access Administrator role role to manage the Global Secure Access features.
- Conditional Access Administrator to enable Global Secure Access signaling for Conditional Access, as well as to create and interact with Conditional Access policies and named locations.
- The product requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
Known limitations
For detailed information about known issues and limitations, see Known limitations for Global Secure Access.
Enable Global Secure Access signaling for Conditional Access
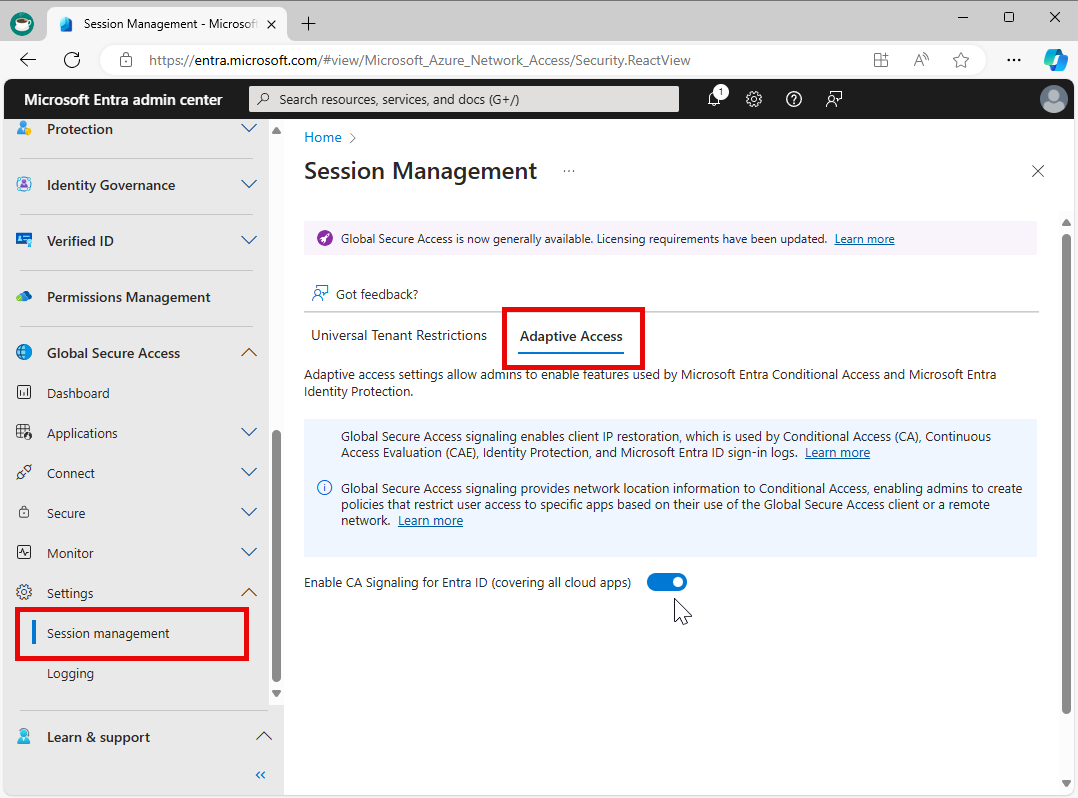
To enable the required setting to allow the compliant network check, an administrator must take the following steps.
- Sign in to the Microsoft Entra admin center with an account which has the Global Secure Access Administrator and Conditional Access Administrator role activated.
- Browse to Global Secure Access > Settings > Session management > Adaptive access.
- Select the toggle to Enable CA Signaling for Entra ID (covering all cloud apps).
- Browse to Entra ID > Conditional Access > Named locations.
- Confirm you have a location called All Compliant Network locations with location type Network Access. Organizations can optionally mark this location as trusted.
Caution
If your organization has active Conditional Access policies based on compliant network check, and you later disable Global Secure Access signaling in Conditional Access, you may unintentionally block targeted end-users from being able to access the resources. If you must disable this feature, first delete any corresponding Conditional Access policies.
Protect your resources behind the compliant network
The compliant network Conditional Access policy can be used to protect your Microsoft and third-party applications that are integrated with Entra ID single sign-on. A typical policy will have a 'Block' grant for all network locations except Compliant Network. The following example demonstrates the steps to configure this type of policy:
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Entra ID > Conditional Access.
- Select Create new policy.
- Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
- Under Assignments, select Users or workload identities.
- Under Include, select All users.
- Under Exclude, select Users and groups and choose your organization's emergency access or break-glass accounts.
- Under Target resources > Include, and select All resources (formerly 'All cloud apps').
- If your organization is enrolling devices into Microsoft Intune, it is recommended to exclude the applications Microsoft Intune Enrollment and Microsoft Intune from your Conditional Access policy to avoid a circular dependency.
- Under Network.
- Set Configure to Yes.
- Under Include, select Any location.
- Under Exclude, select the All Compliant Network locations location.
- Under Access controls:
- Grant, select Block Access, and select Select.
- Confirm your settings and set Enable policy to On.
- Select the Create button to create to enable your policy.
Note
Use Global Secure Access along with Conditional Access policies that require a Compliant Network for All Resources.
Global Secure Access resources are automatically excluded from the Conditional Access policy when Compliant Network is enabled in the policy. There's no explicit resource exclusion required. These automatic exclusions are required to ensure the Global Secure Access client is not blocked from accessing the resources it needs. The resources Global Secure Access needs are:
- Global Secure Access Traffic Profiles
- Global Secure Access Policy Service (internal service)
Sign-in events for authentication of excluded Global Secure Access resources appear in the Microsoft Entra ID sign-in logs as:
- Internet resources with Global Secure Access
- Microsoft apps with Global Secure Access
- All private resources with Global Secure Access
- ZTNA Policy Service
User exclusions
Conditional Access policies are powerful tools. We recommend excluding the following accounts from your policies:
- Emergency access or break-glass accounts to prevent lockout due to policy misconfiguration. In the unlikely scenario where all administrators are locked out, your emergency access administrative account can be used to sign in and recover access.
- More information can be found in the article, Manage emergency access accounts in Microsoft Entra ID.
- Service accounts and Service principals, such as the Microsoft Entra Connect Sync Account. Service accounts are noninteractive accounts that aren't tied to any specific user. They're typically used by backend services to allow programmatic access to applications, but they're also used to sign in to systems for administrative purposes. Calls made by service principals aren't blocked by Conditional Access policies scoped to users. Use Conditional Access for workload identities to define policies that target service principals.
- If your organization uses these accounts in scripts or code, replace them with managed identities.
Try your compliant network policy
- On an end-user device with the Global Secure Access client installed and running, browse to https://myapps.microsoft.com or any other application that uses Entra ID single sign-on in your tenant.
- Pause the Global Secure Access client by right-clicking the application in the Windows tray and selecting Disable.
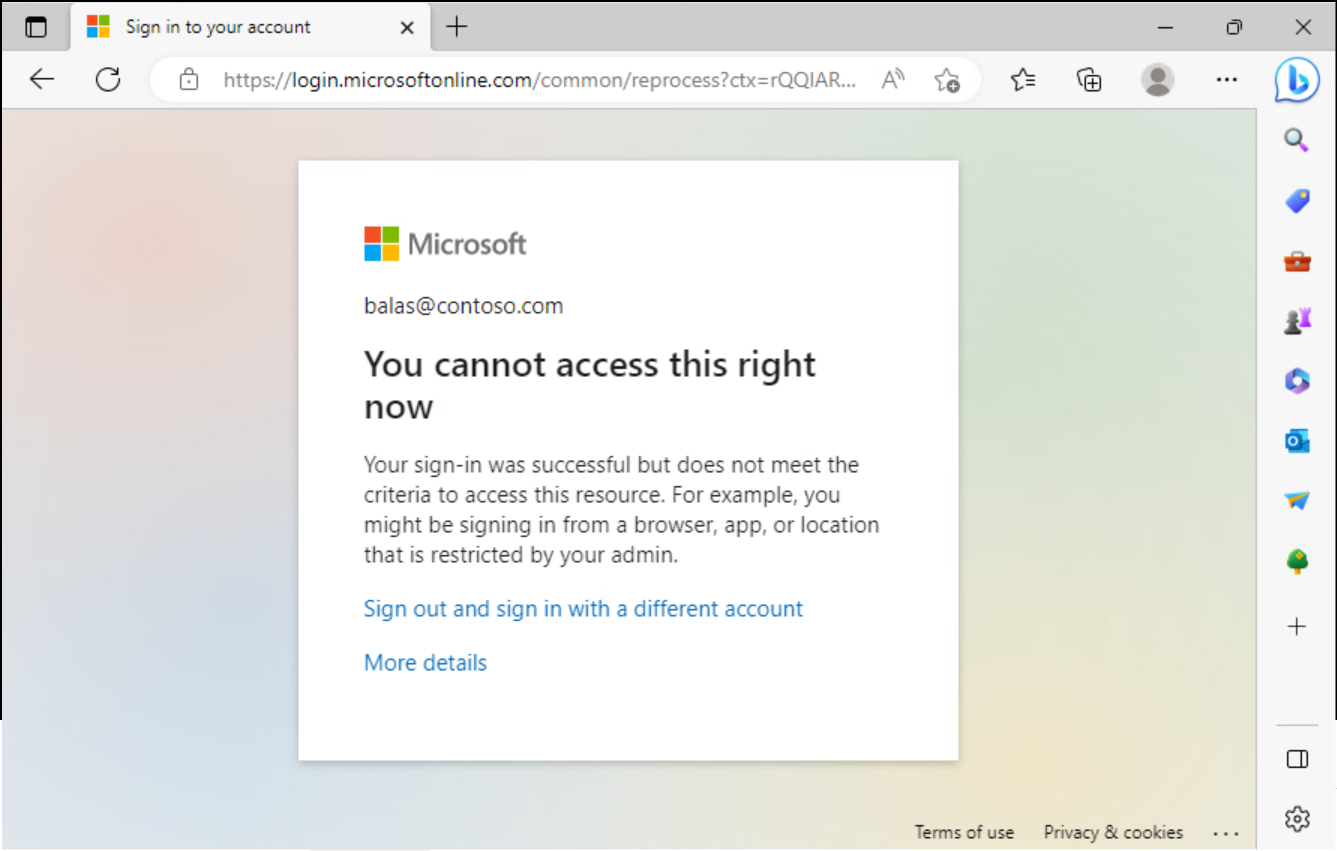
- After disabling the Global Secure Access client, access another application integrated with Entra ID single sign-on. For example, you can try signing in to the Azure portal. Your access should be blocked by Entra ID Conditional Access.
Note
If you are already signed in to an application, access will not be interrupted. Compliant Network condition is evaluated by Entra ID, and if you are already signed in, you may have an existing session with the application. In this scenario, Compliant Network check will be re-evaluated next time the Entra ID sign-in is required, when your application session has expired.