Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to integrate Catchpoint with Microsoft Entra ID. When you integrate Catchpoint with Microsoft Entra ID, you can:
- Control user access to Catchpoint from Microsoft Entra ID.
- Enable automatic Catchpoint sign-in for users with Microsoft Entra accounts.
- Manage your accounts in one central location: the Azure portal.
Prerequisites
The scenario outlined in this article assumes that you already have the following prerequisites:
- A Microsoft Entra user account with an active subscription. If you don't already have one, you can Create an account for free.
- One of the following roles:
- A Catchpoint subscription with single sign-on (SSO) enabled.
Scenario description
In this article, you configure and test Microsoft Entra SSO in a test environment.
- Catchpoint supports SP-initiated and IDP-initiated SSO.
- Catchpoint supports just-in-time (JIT) user provisioning.
Add Catchpoint from the gallery
To configure the integration of Catchpoint into Microsoft Entra ID, add Catchpoint to your list of managed SaaS apps.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Entra ID > Enterprise apps > New application.
- In the Add from the gallery section, type Catchpoint in the search box.
- Select Catchpoint from the results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, and walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO for Catchpoint
For SSO to work, you need to link a Microsoft Entra user with a user in Catchpoint. For this article, we configure a test user called B.Simon.
Complete the following sections:
- Configure Microsoft Entra SSO, to enable this feature for your users.
- Create a Microsoft Entra test user, to test Microsoft Entra single sign-on with B.Simon.
- Assign the Microsoft Entra test user, to enable B.Simon to use Microsoft Entra single sign-on.
- Configure Catchpoint SSO, to configure the single sign-on settings on the application side.
- Create Catchpoint test user, to allow linking of the B.Simon Microsoft Entra test account to a similar user account in Catchpoint.
- Test SSO, to verify that the configuration works.
Configure Microsoft Entra SSO
Follow these steps in the Azure portal to enable Microsoft Entra SSO:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Entra ID > Enterprise apps > Catchpoint > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set Up Single Sign-On with SAML page, select the pencil icon to edit the Basic SAML Configuration settings.
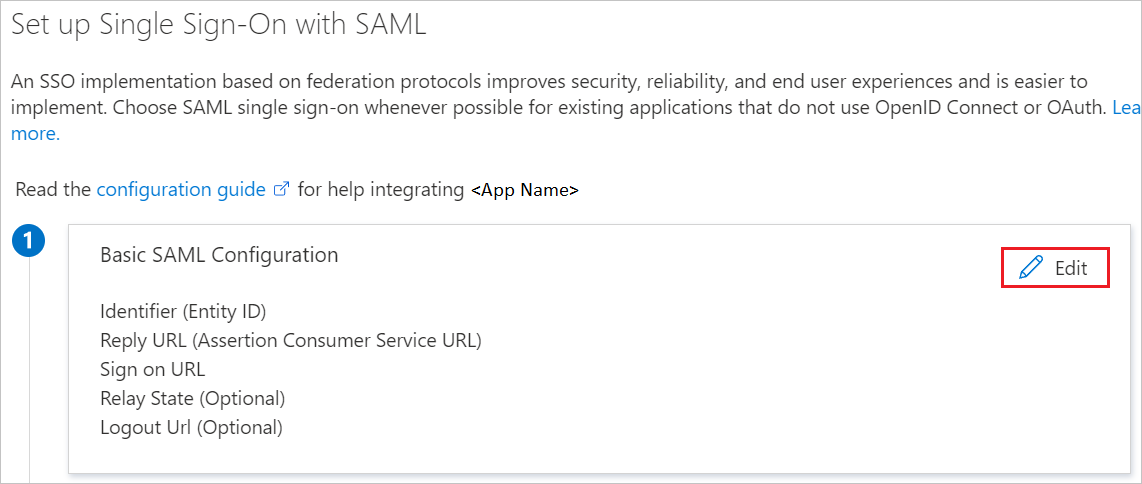
Configure the initiated mode for Catchpoint:
- For IDP-initiated mode, enter the values for the following fields:
- For Identifier:
https://portal.catchpoint.com/SAML2 - For Reply URL:
https://portal.catchpoint.com/ui/Entry/SingleSignOn.aspx
- For Identifier:
- For SP-initiated mode, select Set additional URLs and enter the following value:
- For Sign-on URL:
https://portal.catchpoint.com/ui/Entry/SingleSignOn.aspx
- For Sign-on URL:
- For IDP-initiated mode, enter the values for the following fields:
The Catchpoint application expects the SAML assertions in a specific format. Add custom attribute mappings to your configuration of SAML token attributes. The following table contains the list of default attributes:
Name Source attribute Givenname user.givenneame Surname user.surname Emailaddress user.mail Name user.userprincipalname Unique User Identifier user.userprincipalname 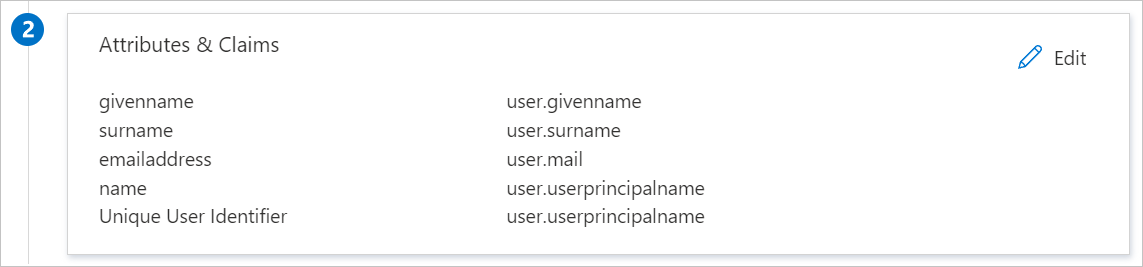
Also, the Catchpoint application expects another attribute to be passed in a SAML response. See the following table. This attribute is also pre-populated, but you can review and update it to fit your requirements.
Name Source attribute namespace user.assignedrole Note
The
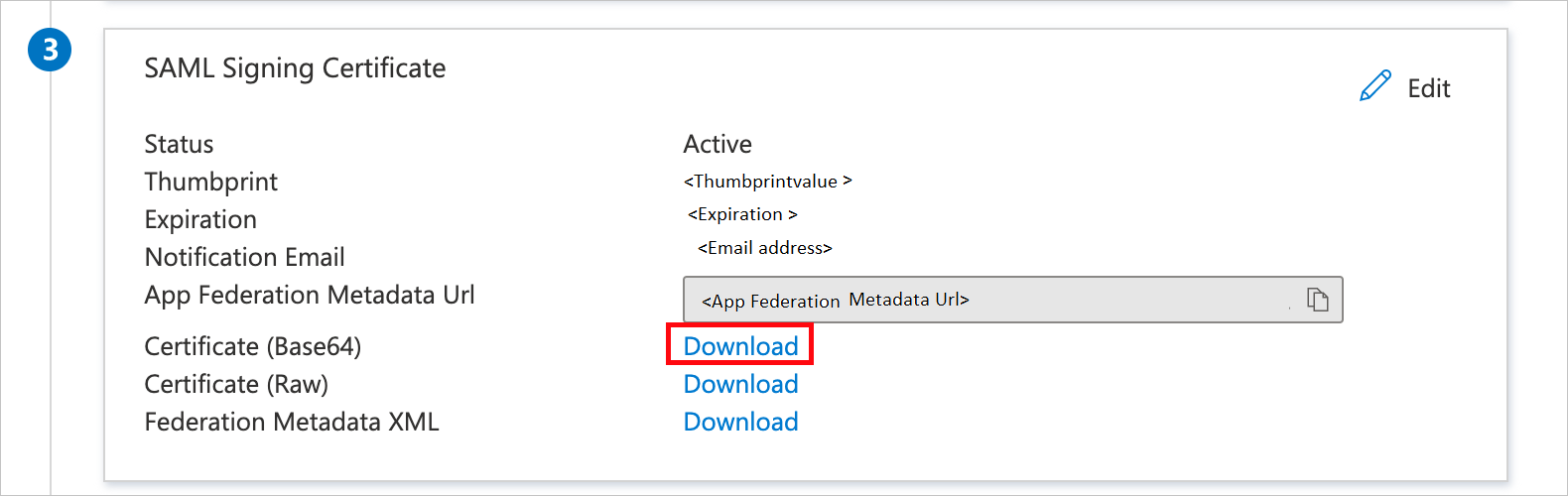
namespaceclaim needs to be mapped with the account name. This account name should be set up with a role in Microsoft Entra ID to be passed back in SAML response. For more information about roles in Microsoft Entra ID, see Configure the role claim issued in the SAML token for enterprise applications.Go to the Set Up Single Sign-On with SAML page. In the SAML Signing Certificate section, find Certificate (Base64). Select Download to save the certificate to your computer.
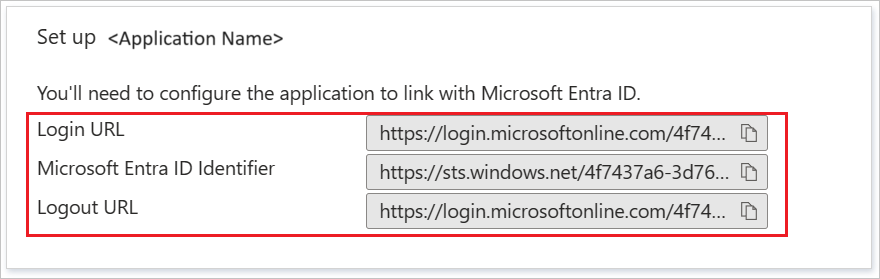
In the Set up Catchpoint section, copy the URLs that you need in a later step.
Create and assign Microsoft Entra test user
Follow the guidelines in the create and assign a user account quickstart to create a test user account called B.Simon.
Configure Catchpoint SSO
In a different web browser window, sign in to the Catchpoint application as an administrator.
Select the Settings icon and then SSO Identity Provider.

On the Single Sign On page, enter the following fields:

Field Value Namespace A valid namespace value. Identity Provider Issuer The Azure AD Identifiervalue.Single Sign On Url The Login URLvalue.Certificate The contents of the downloaded Certificate (Base64)file. Use Notepad to view and copy.You might also upload the Federation Metadata XML by selecting the Upload Metadata option.
Select Save.
Create a Catchpoint test user
Catchpoint supports just-in-time user provisioning, which is enabled by default. You have no action items in this section. If B.Simon doesn't already exist as a user in Catchpoint, it's created after authentication.
Test SSO
In this section, you test your Microsoft Entra single sign-on configuration with following options.
SP initiated:
Select Test this application, this option redirects to Catchpoint Sign on URL where you can initiate the login flow.
Go to Catchpoint Sign-on URL directly and initiate the login flow from there.
IDP initiated:
- Select Test this application, and you should be automatically signed in to the Catchpoint for which you set up the SSO
You can also use Microsoft My Apps to test the application in any mode. When you select the Catchpoint tile in the My Apps, if configured in SP mode you would be redirected to the application sign on page for initiating the login flow and if configured in IDP mode, you should be automatically signed in to the Catchpoint for which you set up the SSO. For more information about the My Apps, see Introduction to the My Apps.
Note
When you're signed in to the Catchpoint application through the login page, after providing Catchpoint Credentials, enter the valid Namespace value in the Company Credentials(SSO) field and select Login.

Related content
After you configure Catchpoint, you can enforce session control. This precaution protects against exfiltration and infiltration of your organization's sensitive data in real time. Session control is an extension of Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.