Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to integrate IBM Storage Virtualize with Microsoft Entra ID. When you integrate IBM Storage Virtualize with Microsoft Entra ID, you can:
Use Microsoft Entra ID to control who can access IBM Storage Virtualize. Enable your users to be automatically signed in to IBM Storage Virtualize with their Microsoft Entra accounts. Manage your accounts in one central location: the Azure portal.
Prerequisites
The scenario outlined in this article assumes that you already have the following prerequisites:
- A Microsoft Entra user account with an active subscription. If you don't already have one, you can Create an account for free.
- One of the following roles:
- IBM Storage Virtualize single sign-on (SSO) enabled subscription.
Add IBM Storage Virtualize from the gallery
To configure the integration of IBM Storage Virtualize into Microsoft Entra ID, you need to add IBM Storage Virtualize from the gallery to your list of managed SaaS apps.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Entra ID > Enterprise apps > New application.
In the Add from the gallery section, enter IBM Storage Virtualize in the search box.
Select IBM Storage Virtualize in the results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Configure Microsoft Entra SSO
Follow these steps to enable Microsoft Entra SSO in the Microsoft Entra admin center.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Entra ID > Enterprise apps > IBM Storage Virtualize > Single sign-on.
Perform the following steps in the below section:
Navigate to Authentication tab on the left menu and perform the following steps:
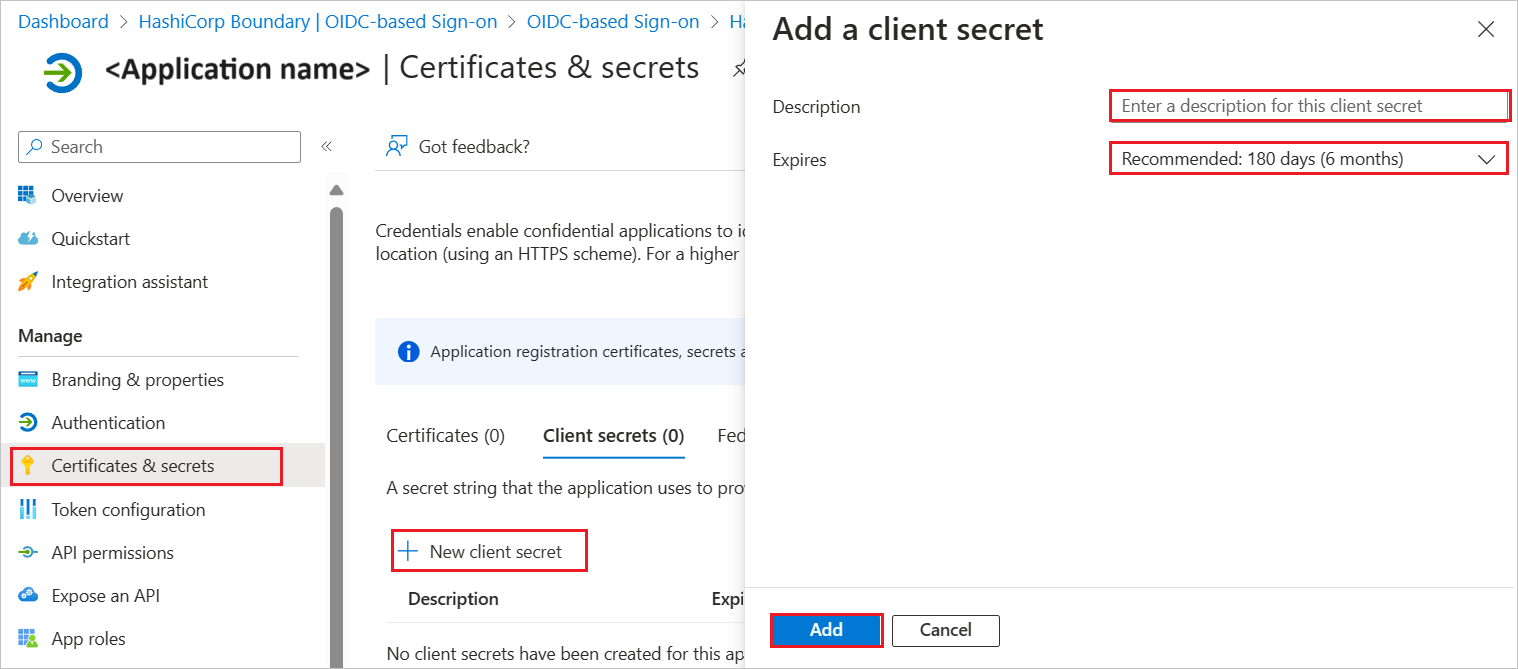
Navigate to Certificates & secrets on the left menu and perform the following steps:
Go to Client secrets tab and select +New client secret.
Enter a valid Description in the textbox and select Expires days from the drop-down as per your requirement and select Add.
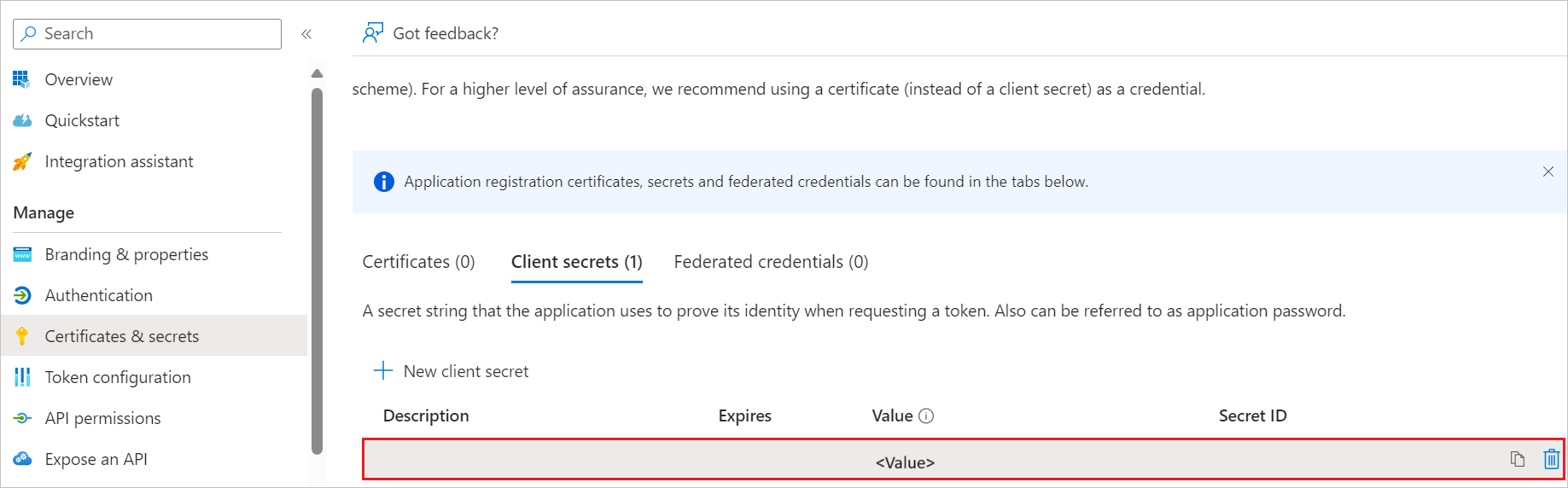
Once you add a client secret, Value is generated. Copy the value and use it later in the IBM Storage Virtualize side configuration.
Create and assign Microsoft Entra test user
Follow the guidelines in the create and assign a user account quickstart to create a test user account called B.Simon.
Configure IBM Storage Virtualize SSO
Below are the configuration steps to complete the OAuth/OIDC federation setup:
Sign in to the IBM Storage Virtualize administrator dashboard by using the following URL:
https://tenant.verify.ibm.com/ui/admin.In the IBM Security Verify interface, select **Applications Add application.
Note
Each system must be added as a separate application.
Navigate to General tab and perform the following steps:
In the Name field, enter a unique name to identity the system.
In the Description field, enter a brief description of the system.
In the Company name field, enter name of organization or company.
Navigate to Sign-on tab and perform the following steps:
Enter your Application URL which is used to access the management GUI for your system.
Select Authorization code and JWT bearer Grant type.
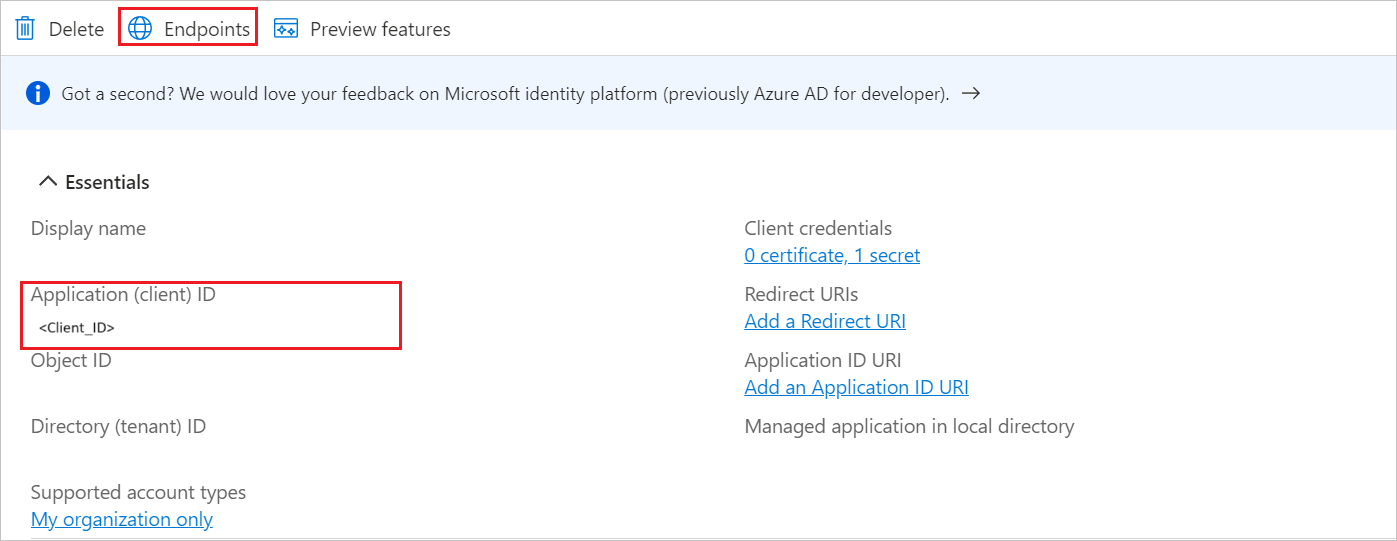
In the Client ID field, paste the Application ID value, which you have copied from Entra page.
In the Client Secret field, paste the value, which you have copied from Certificates & secrets section at Entra side.
For User consent, select don't ask for consent button.
Copy the Redirect URIs and use it later in the Entra configuration.
Select Username from the JWT bearer user identification.
Ensure Cloud Directory is selected in JWT bearer default identity source.
Ensure Generate refresh token option is unchecked.
Ensure Send all known user attributes in the ID token option is checked.
Under Access policies, Deselect Use default policy > select the Edit icon > Select Always require 2FA in all devices > select OK.
Ensure Restrict custom scopes option is unchecked.
Select Save.
On the confirmation page, select Confirm to enable single sign-on for the system.