Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to integrate LoginRadius with Microsoft Entra ID. When you integrate LoginRadius with Microsoft Entra ID, you can:
- Control in Microsoft Entra ID who has access to LoginRadius.
- Enable your users to be automatically signed-in to LoginRadius with their Microsoft Entra accounts.
- Manage your accounts in one central location.
Prerequisites
The scenario outlined in this article assumes that you already have the following prerequisites:
- A Microsoft Entra user account with an active subscription. If you don't already have one, you can Create an account for free.
- One of the following roles:
- A LoginRadius single sign-on enabled subscription.
Scenario description
In this article, you configure and test Microsoft Entra single sign-on in a test environment.
- LoginRadius supports SP initiated SSO.
Note
Identifier of this application is a fixed string value so only one instance can be configured in one tenant.
Add LoginRadius from the gallery
To configure the integration of LoginRadius into Microsoft Entra ID, you need to add LoginRadius from the gallery to your list of managed SaaS apps.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Entra ID > Enterprise apps > New application.
- In the Add from the gallery section, type LoginRadius in the search box.
- Select LoginRadius from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, and walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO for LoginRadius
Configure and test Microsoft Entra SSO with LoginRadius using a test user called B.Simon. For SSO to work, you need to establish a link relationship between a Microsoft Entra user and the related user in LoginRadius.
To configure and test Microsoft Entra SSO with LoginRadius, perform the following steps:
- Configure Microsoft Entra SSO - to enable your users to use this feature.
- Create a Microsoft Entra test user - to test Microsoft Entra single sign-on with B.Simon.
- Assign the Microsoft Entra test user - to enable B.Simon to use Microsoft Entra single sign-on.
- Configure LoginRadius SSO - to configure the single sign-on settings on application side.
- Create LoginRadius test user - to have a counterpart of B.Simon in LoginRadius that's linked to the Microsoft Entra representation of user.
- Test SSO - to verify whether the configuration works.
Configure Microsoft Entra SSO
Follow these steps to enable Microsoft Entra SSO.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Entra ID > Enterprise apps > LoginRadius > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, select the pencil icon for Basic SAML Configuration to edit the settings.
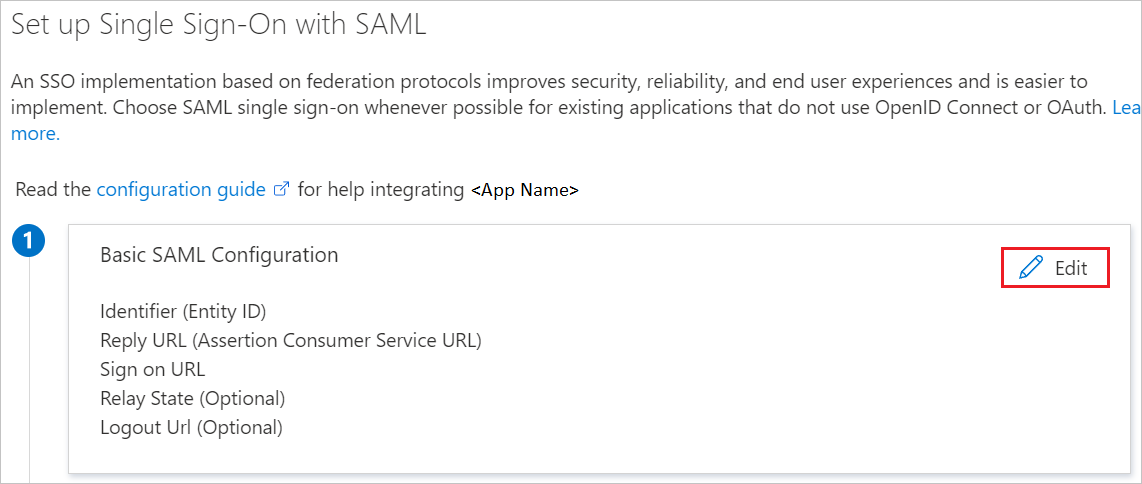
On the Basic SAML Configuration section, perform the following steps:
In the Identifier (Entity ID) text box, enter the URL
https://lr.hub.loginradius.com/In the Reply URL (Assertion Consumer Service URL) textbox, enter the LoginRadius ACS URL
https://lr.hub.loginradius.com/saml/serviceprovider/AdfsACS.aspxIn the Sign on URL text box, enter the URL
https://secure.loginradius.com/login
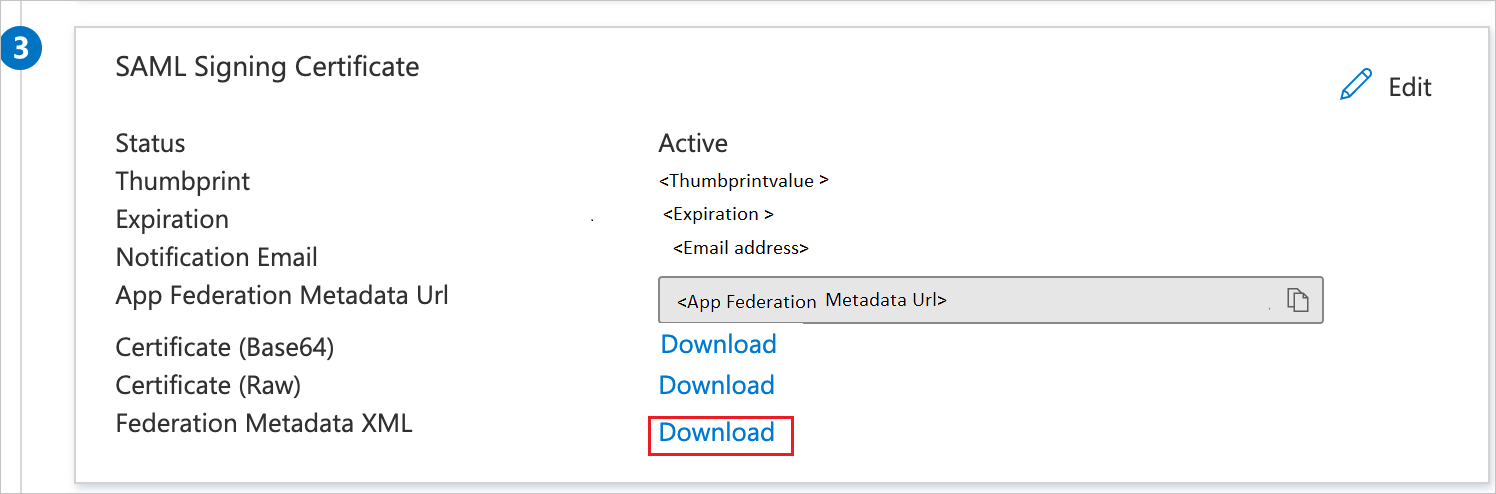
On the Set up Single Sign-On with SAML page, in the SAML Signing Certificate section, select Download to download the Federation Metadata XML from the given options as per your requirement and save it on your computer.
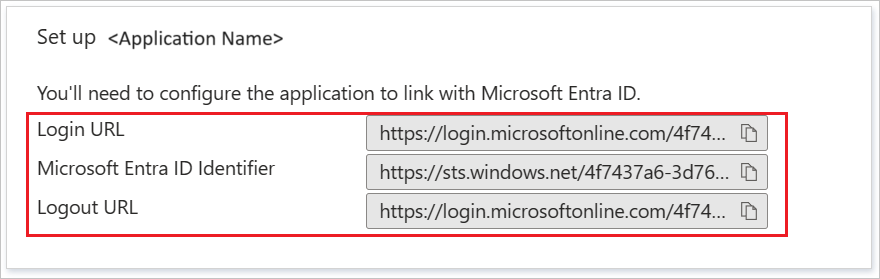
In the Set up LoginRadius section, copy the appropriate URL(s) as per your requirement.
Create and assign Microsoft Entra test user
Follow the guidelines in the create and assign a user account quickstart to create a test user account called B.Simon.
Configure LoginRadius SSO
In this section, you enable Microsoft Entra single sign-on in the LoginRadius Admin Console.
Log in to your LoginRadius Admin Console account.
Go to your Team Management section in the LoginRadius Admin Console.
Select the Single Sign-On tab, and then select Microsoft Entra ID:
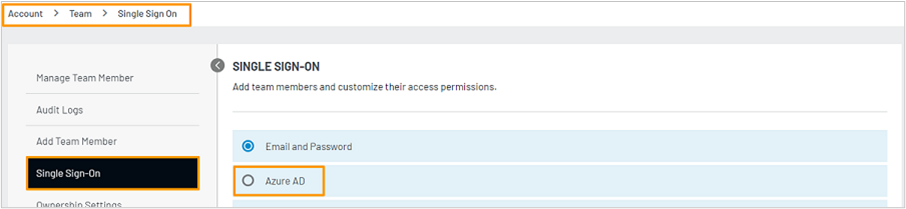
In the Microsoft Entra setup page, complete the following steps:
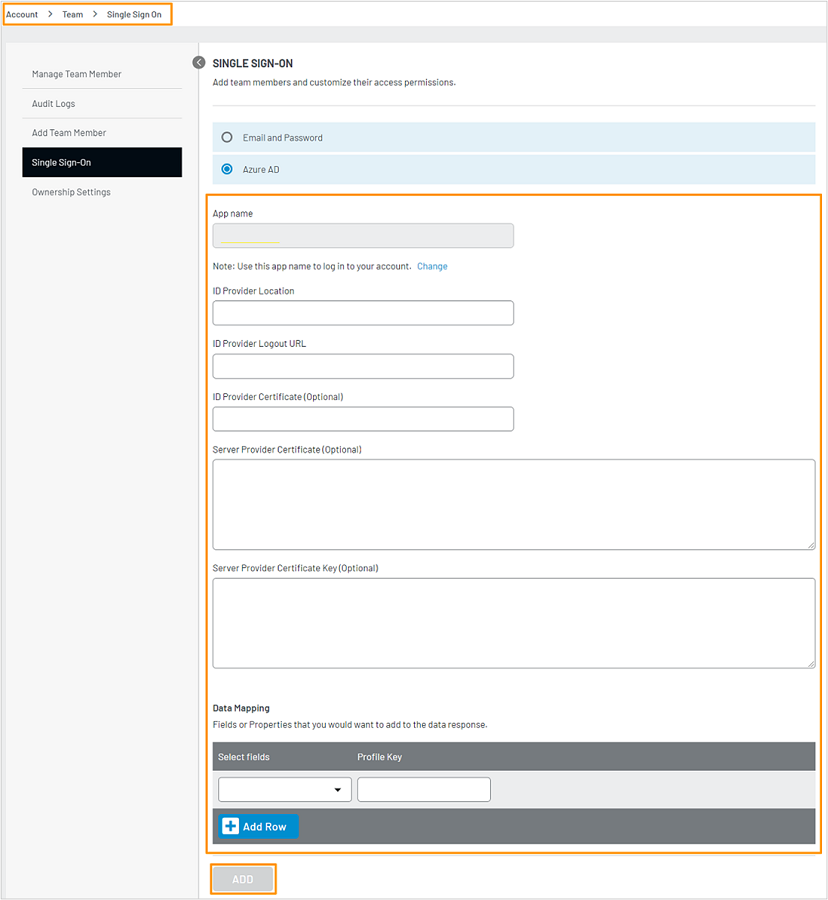
In ID Provider Location, enter the SIGN-ON ENDPOINT, which you get from your Microsoft Entra account.
In ID Provider Logout URL, enter the SIGN-OUT ENDPOINT, which you get from your Microsoft Entra account.
In ID Provider Certificate, enter the Microsoft Entra certificate, which you get from your Microsoft Entra account. Enter the certificate value with the header and footer. Example:
-----BEGIN CERTIFICATE-----<certificate value>-----END CERTIFICATE-----In Service Provider Certificate and Server Provider Certificate Key, enter your certificate and key.
You can create a self-signed certificate by running the following commands on the command line (Linux/Mac):
Command to get the certificate key for SP:
openssl genrsa -out lr.hub.loginradius.com.key 2048Command to get the certificate for SP:
openssl req -new -x509 -key lr.hub.loginradius.com.key -out lr.hub.loginradius.com.cert -days 3650 -subj /CN=lr.hub.loginradius.com
Note
Be sure to enter the certificate and certificate key values with the header and footer:
- Certificate value example format:
-----BEGIN CERTIFICATE-----<certificate value>-----END CERTIFICATE----- - Certificate key value example format:
-----BEGIN RSA PRIVATE KEY-----<certificate key value>-----END RSA PRIVATE KEY-----
In the Data Mapping section, select the fields (SP fields) and enter the corresponding Microsoft Entra ID fields(IdP fields).
Following are some listed field names for Microsoft Entra ID.
Fields Profile Key Email http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddressFirstName http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givennameLastName http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surnameNote
The Email field mapping is required. FirstName and LastName field mappings are optional.
Create LoginRadius test user
Log in to your LoginRadius Admin Console account.
Go to your team management section in the LoginRadius Admin Console.
Select Add Team Member in the side menu to open the form.
In the Add Team Member form, you create a user called Britta Simon in your LoginRadius site by providing the user's details and assigning the permissions you want the user to have. To know more about the permissions based on roles, see the Role Access Permissions section of the LoginRadius Manage Team Members document. Users must be created and activated before you use single sign-on.
Test SSO
In this section, you test your Microsoft Entra single sign-on configuration using MyApps.
- In a browser, go to https://accounts.loginradius.com/auth.aspx and select Fed SSO log in.
- Enter your LoginRadius app name, and then select Login.
- It should open a pop-up for asking you to sign in to your Microsoft Entra account.
- After the authentication, your pop-up will close and you be logged in to the LoginRadius Admin Console.
Related content
Once you configure LoginRadius you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.