Step 3. Integrate Mobile Threat Defense
The Microsoft Mobile Threat Defense (MTD) connector is a feature in Microsoft Intune that creates a channel of communication between Intune and your chosen MTD vendor, regardless of the device’s operating system. There are various supported MTD partners for both Windows and mobile devices. Intune integrates data from an MTD vendor as an information source for device compliance policies and device conditional access rules. The information provided by this communication channel can help protect corporate resources, such as Exchange and SharePoint data, by blocking access from compromised devices.
Mobile Application Management (MAM) threat detection can be integrated with various MTD partners, including Windows Security Center. This integration provides a client device health assessment to Intune application protection policies (APP) via a service-to-service connector. This assessment supports gating the flow and access to organizational data on personal unmanaged devices.
The health assessment and state includes the following details:
- User, app, and device identifiers
- A predefined health state
- The time of last health state update
Only users enrolled in Mobile Application Management send health state data. If end users want to stop sending data, they can sign out of their organization account in the protected applications. Similarly, administrators can stop data transmission by removing the MTD connector from Microsoft Intune.
Intune app protection policies
Intune app protection policies help secure organizational data and help ensure client devices are healthy. It also can perform additional client health verification via Windows Security Center. This involves designating the Windows Security Center risk level for allowing end users to access corporate resources. In addition, it also involves setting up tenant-based connectors to Microsoft Intune for Windows Security Center.
Apps: Select the apps that you want to target from app protection policies. For this feature set, these apps are blocked or selectively wiped based on device risk assessment from your chosen Mobile Threat Defense vendor.
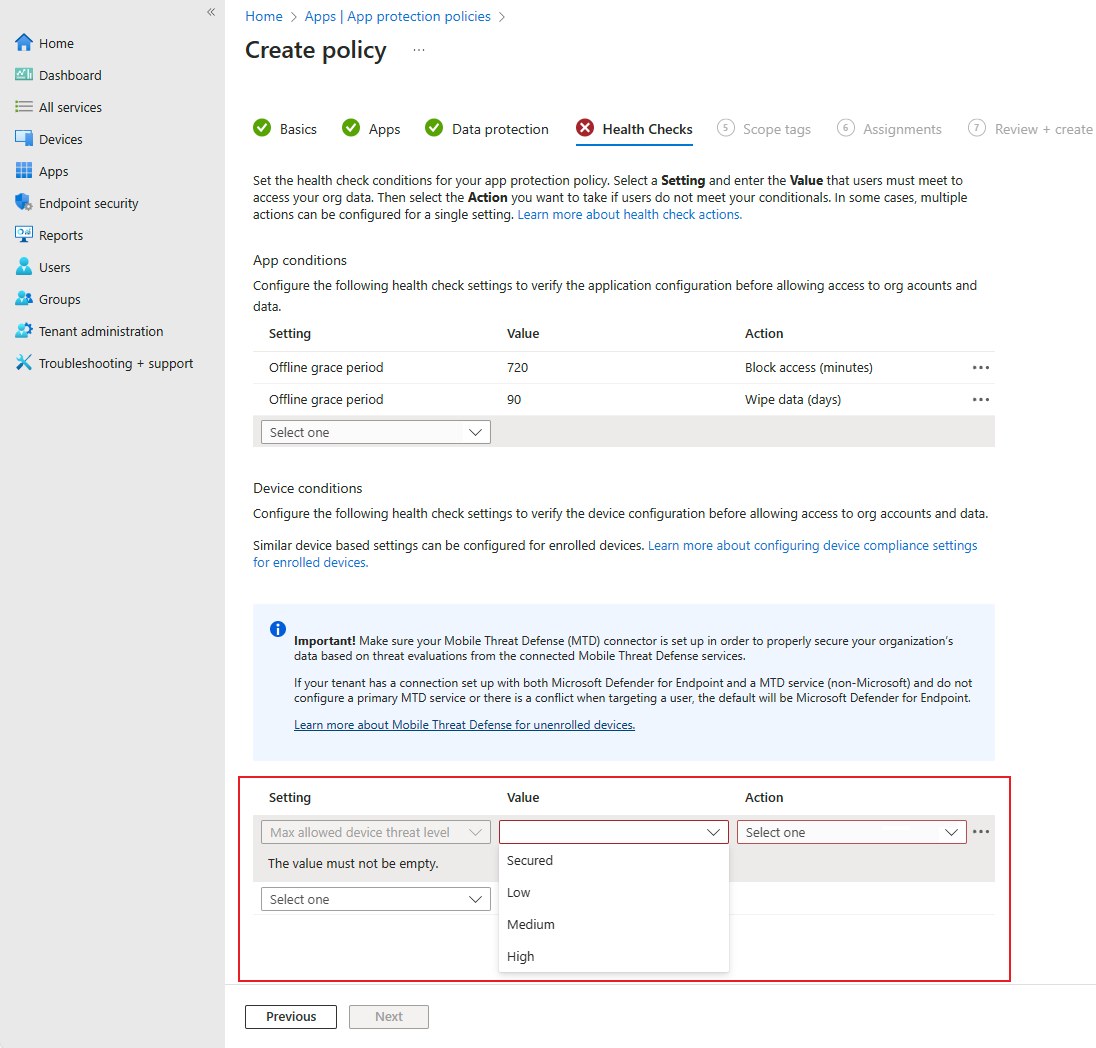
Health Checks: Under Device conditions you can select Max allowed device threat level.
Options for the threat level
You can select one of the following threat level values:
- Secured: This level is the most secure. The device can't have any threats present and still access company resources. If any threats are found, the device is evaluated as noncompliant.
- Low: The device is compliant if only low-level threats are present. Anything higher puts the device in a noncompliant status.
- Medium: The device is deemed compliant if the threats found on the device are of low or medium level. If high-level threats are detected, the device is marked as noncompliant.
- High: This level is the least secure and allows all threat levels, using Mobile Threat Defense for reporting purposes only. Devices are required to have the MTD app activated with this setting.
Options for Action
You can select one of the following Action options:
- Block access: Will prevent the users from performing any activity until they're back in compliance.
- Wipe data: This removes any information stored in the application related to the corporate data. It doesn't affect personal data on the personal profile.
Assignments
Assign the policy to groups of users. The devices used by the group's members are evaluated for access to corporate data on targeted apps via Intune app protection.
Important
If you create an app protection policy for any protected app, the device's threat level is assessed. Depending on the configuration, devices that do not meet an acceptable level are either blocked or selectively wiped through conditional launch. If blocked, they are prevented from accessing corporate resources until the threat on the device is resolved and reported to Intune by the chosen MTD vendor.
Configure the MTD Connector
Use the following steps to configure the MTD Connector.
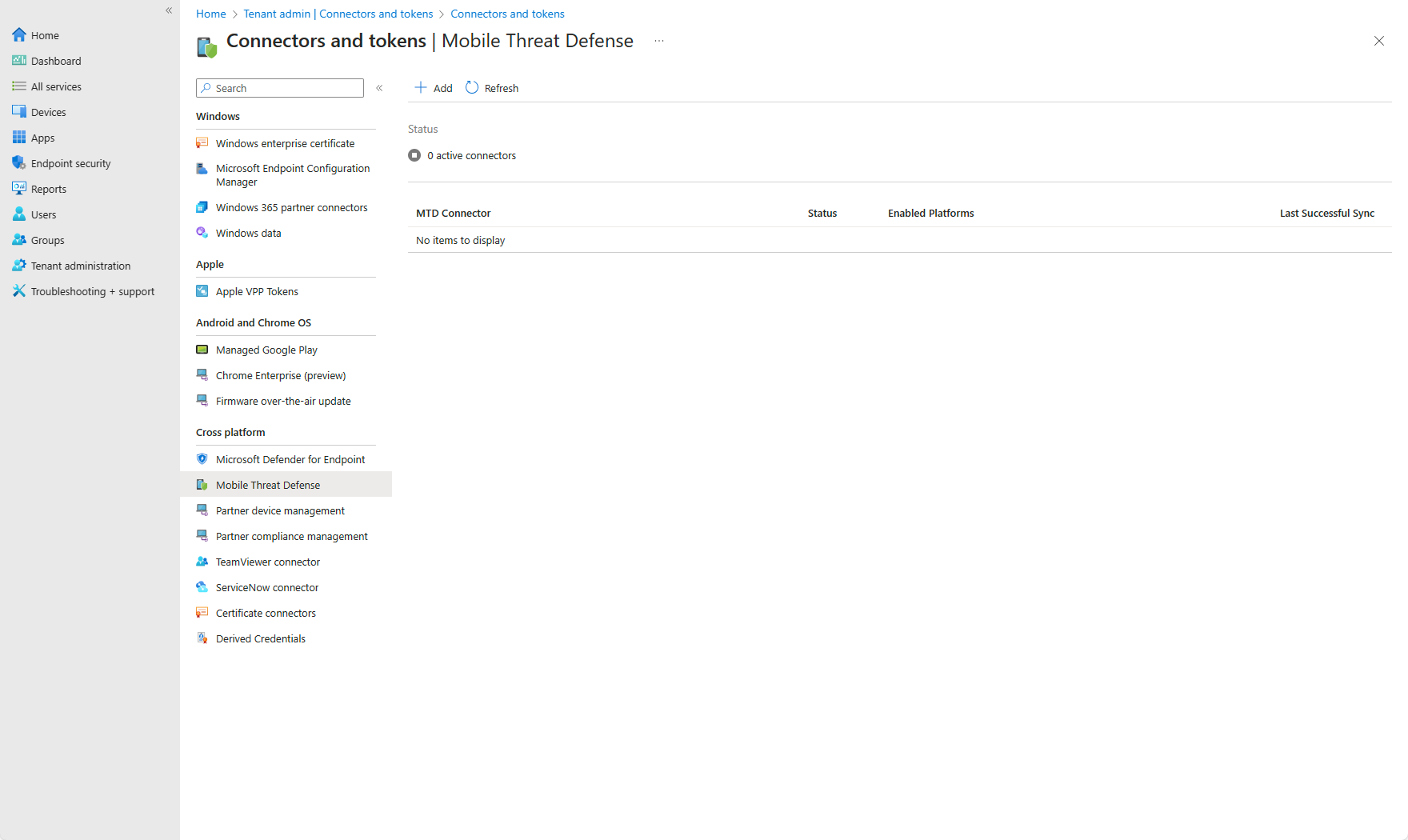
Navigate to the Microsoft Intune admin center.
Select Tenant Administrator > Connectors and tokens > Mobile Threat Defense.
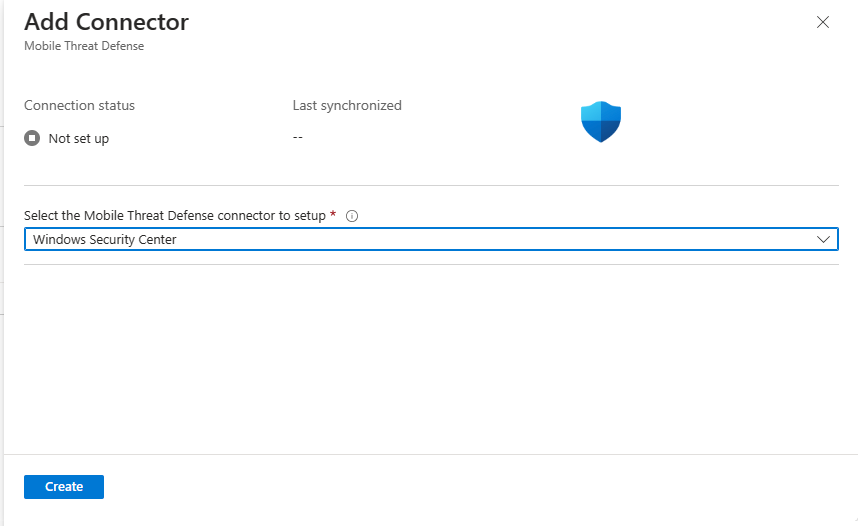
Select Add to display the Add Connector pane.
From the Select the Mobile Threat Defense connector to setup dropdown box, select Windows Security Center.
Note
In this example, you have selected Windows Security Center. For the full list of MTD Partners, see Mobile Threat Defense partners.
-
select Create to create the connector.
Important
The connector is now created. It's important to note that the Connection status remains Unavailable until the first App Protection Policy arrives to the user or the first MAM user is enrolled to your Intune tenant. For more information, see Connector status.
Next step
Continue with Step 4 to create app configuration policies for Microsoft Edge for Business.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for