Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
When you integrate Microsoft Intune with Microsoft Defender for Endpoint, you can use Intune endpoint security policies to manage the Defender security settings on devices that aren't enrolled with Intune. This capability is known as Defender for Endpoint security settings management.
When you manage devices through security settings management:
You can use the Microsoft Intune admin center or the Microsoft 365 Defender portal to manage Intune endpoint security policies for Defender for Endpoint and assign those policies to Microsoft Entra ID groups. The Defender portal includes the user interface for device views, policy management, and reports for security settings management.
To manage policies from within the Defender portal, see Manage endpoint security policies in Microsoft Defender for Endpoint in the Defender content.
Devices get their assigned policies based on their Microsoft Entra ID device object. A device that isn't already registered in Microsoft Entra is joined as part of this solution.
When a device receives a policy, the Defender for Endpoint components on the device enforce the policy and report on the device's status. The device's status is available in the Microsoft Intune admin center and the Microsoft Defender portal.
This scenario extends the Microsoft Intune Endpoint Security surface to devices that aren't capable of enrolling in Intune. When a device is managed by Intune (enrolled to Intune) the device doesn't process policies for Defender for Endpoint security settings management. Instead, use Intune to deploy policy for Defender for Endpoint to your devices.
Applies to:
- Windows 10 and Windows 11
- Windows Server 2012 R2 and later
- Linux
- macOS
Prerequisites
Review the following sections for requirements for the Defender for Endpoint security settings management Scenario.
Environment
When a supported device onboards to Microsoft Defender for Endpoint:
- The device is surveyed for an existing Microsoft Intune presence, which is a mobile device management (MDM) enrollment to Intune.
- Devices without an Intune presence enable the security settings management feature.
- For devices that aren't fully Microsoft Entra registered, a synthetic device identity is created in Microsoft Entra ID that allows the device to retrieve policies. Fully registered devices use their current registration.
- On the device, Microsoft Defender for Endpoint enforces policies that are retrieved from Microsoft Intune.
Government cloud support
The Defender for Endpoint security settings management scenario is supported in the following government tenants:
- US Government Community Cloud (GCC)
- US Government Community High (GCC High)
- Department of Defense (DoD)
For more information, see:
- Intune US Government service description
- Microsoft Defender for Endpoint for US Government customers
- Feature parity with commercial in Microsoft Defender for Endpoint for US Government customers.
Connectivity requirements
Devices must have access to the following endpoint:
*.dm.microsoft.com- The use of a wildcard supports the cloud-service endpoints that are used for enrollment, check-in, and reporting, and which can change as the service scales.
Note
Endpoints for government customers are located at Network endpoints for US government deployments
Supported platforms
Policies for Microsoft Defender for Endpoint security management are supported for the following device platforms:
Linux:
With Microsoft Defender for Endpoint for Linux agent version 101.23052.0009 or later, security settings management is supported across all Linux distributions listed at Supported Linux distributions.
You can find the version of your Defender agents using these methods from within the Microsoft Defender portal:
You can investigate a single device by browsing to Assets > Devices > Overview and reviewing the Defender engine version field.
You can view a summary report and export a full inventory list showing platform versions at Reports > Endpoints > Device health > Microsoft Defender Antivirus health.
You can use the following query in Hunting > Advanced hunting and review the SoftwareVersion data:
DeviceTvmSoftwareInventory | where SoftwareName == "defender_for_linux"
For guidance on updating the agent version, see Deploy updates for Microsoft Defender for Endpoint on Linux.
Known issues
With Defender agent version 101.23052.0009, Linux devices fail to enroll if the following file path is absent:
/sys/class/dmi/id/board_vendor.When a Linux device performs synthetic registration, the Device Entra ID (formerly known as Device AAD ID) isn't visible in the Defender portal. This information can be viewed from the Intune or Microsoft Entra portals. Administrators can still manage devices with policies in this manner.
macOS:
With Microsoft Defender for Endpoint for macOS agent version 101.23052.0004 or later, security settings management supports the following macOS versions:
- macOS 15 (Sequoia)
- macOS 14 (Sonoma)
- macOS 13 (Ventura)
You can find the versions of your Defender agents using these methods from within the Microsoft Defender portal:
You can investigate a single device by browsing to Assets > Devices > Overview and reviewing the Defender engine version field.
You can view a summary report and export a full inventory list showing platform versions at Reports > Endpoints > Device health > Microsoft Defender Antivirus health.
You can use the following query in Hunting > Advanced hunting and review the SoftwareVersion data:
DeviceTvmSoftwareInventory | where SoftwareName == "defender_for_mac"
For guidance on updating the agent version, see Deploy updates for Microsoft Defender for Endpoint on macOS.
Known issues
- When a macOS device performs synthetic registration, the Device Entra ID (formerly known as Device AAD ID) isn't visible in the Defender portal. This information can be viewed from the Intune or Microsoft Entra portals. Administrators can still manage devices with policies in this manner.
Windows:
Windows 10 Professional/Enterprise (with KB5023773)
Windows 11 Professional/Enterprise (with KB5023778)
Windows Server 2012 R2 with Microsoft Defender for Down-Level Devices
Windows Server 2016 with Microsoft Defender for Down-Level Devices
Windows Server 2019 (with KB5025229)
Windows Server 2019 Core (with the Server Core App Compatibility Feature on Demand installed)
Windows Server 2022, including Server Core (with KB5025230)
Windows Server 2025
Domain controllers. See important information in Use of security settings management on domain controllers (in this article).
Security settings management doesn't work on and isn't supported with the following devices:
- Windows Server Core 2016 and earlier
- Non-persistent desktops, like Virtual Desktop Infrastructure (VDI) clients
- Azure Virtual Desktop (AVD and formerly Windows Virtual Desktop, WVD)
- 32-bit versions of Windows
Licensing and subscriptions
To use security settings management, you need:
A subscription that grants licenses for Microsoft Defender for Endpoint, like Microsoft 365, or a standalone license for only Microsoft Defender for Endpoint. A subscription that grants Microsoft Defender for Endpoint licenses also grants your tenant access to the Endpoint security node of the Microsoft Intune admin center.
Note
Exception: If you have access to Microsoft Defender for Endpoint only through Microsoft Defender for servers (part of Microsoft Defender for Cloud, formerly Azure Security Center), the security settings management functionality isn't available. You must have at least one Microsoft Defender for Endpoint (user) subscription license active.
The Endpoint security node is where you configure and deploy policies to manage Microsoft Defender for Endpoint for your devices and monitor device status.
For current information about options, see Minimum requirements for Microsoft Defender for Endpoint.
Role-based access controls (RBAC)
For guidance on assigning the right level of permissions and rights to administrators who manage Intune endpoint security policies from within the Intune admin center, see Assign role-based access controls for endpoint security policy.
Architecture
The following diagram is a conceptual representation of the Microsoft Defender for Endpoint security configuration management solution.
- Devices onboard to Microsoft Defender for Endpoint.
- Devices communicate with Intune. This communication enables Microsoft Intune to distribute policies that are targeted to the devices when they check in.
- A registration is established for each device in Microsoft Entra ID:
- If a device previously was fully registered, like a Hybrid Join device, the existing registration is used.
- For devices that aren't registered, a synthetic device identity is created in Microsoft Entra ID to enable the device to retrieve policies. When a device with a synthetic registration has a full Microsoft Entra registration created for it, the synthetic registration is removed and the devices management continues on uninterrupted by using the full registration.
- Defender for Endpoint reports the status of the policy back to Microsoft Intune.
Important
Security settings management uses a synthetic registration for devices that don't fully register in Microsoft Entra ID, and drops the Microsoft Entra hybrid join prerequisite. With this change, Windows devices that previously had enrollment errors begin onboarding to Defender and then receive and process the security settings management policies.
To filter for devices that were unable to enroll due to failing to meet the Microsoft Entra hybrid join prerequisite, navigate to the Devices list in the Microsoft Defender portal, and filter by enrollment status. Because these devices aren't fully registered, their device attributes show MDM = Intune and Join Type = Blank. These devices now enroll with security settings management using the synthetic registration.
After enrolling these devices appear in the device lists for Microsoft Defender, Microsoft Intune, and Microsoft Entra portals. While the devices don't fully register with Microsoft Entra, their synthetic registration counts as one device object.
What to expect in the Microsoft Defender portal
You can use the Microsoft Defender for Endpoint Device inventory to confirm a device is using the security settings management capability in Defender for Endpoint, by reviewing the devices status in the Managed by column. The Managed by information is also available on the devices side-panel or device page. Managed by should consistently indicate that its managed by MDE.
You can also confirm a device is enrolled in security settings management successfully by confirming that the device-side panel or device page display MDE Enrollment status as Success.
If the MDE Enrollment status doesn't display Success, make sure you're looking at a device that was updated and is in scope for security settings management. (You configure the scope on the Enforcement scope page while configuring security settings management.)
What to expect in the Microsoft Intune admin center
In the Microsoft Intune admin center, go to the All Devices page. Devices enrolled with security settings management appear here as in the Defender portal. In the admin center, the devices Managed by field should display MDE.
Tip
In June 2023, security settings management began using synthetic registration for devices that don't fully register in Microsoft Entra. With this change, devices that previously had enrollment errors begin onboarding to Defender and then receive and process the security settings management policies.
What to expect in the Microsoft Azure portal
On the All devices page In the Microsoft Azure portal, you can view device details.
To ensure that all devices enrolled in Defender for Endpoint security settings management receive policies, we recommend creating a dynamic Microsoft Entra group based on the devices' OS Type. With a dynamic group, devices that are managed by Defender for Endpoint are automatically added to the group without requiring admins to perform other tasks, like creating a new policy.
Important
From July 2023 to September 25, 2023, security settings management ran an opt-in public preview that introduced new behavior for devices that were managed and enrolled to the scenario. Starting on September 25, 2023, the public preview behavior became generally available and now applies to all tenants that use security settings management.
If you used security settings management prior to September 25, 2023, and didn't join the opt-in public preview that ran from July 2023 to September 25, 2023, review your Microsoft Entra groups that rely on system labels to make changes that will identify new devices you manage with security settings management. This is because prior to September 25, 2023, devices not managed through the opt-in public preview would use the following system labels (tags) of MDEManaged and MDEJoined to identify managed devices. These two system labels are no longer supported and are no longer added to devices that enroll.
Use the following guidance for your Dynamic groups:
(Recommended) When targeting policy, use dynamic groups based on the device platform by using the deviceOSType attribute (Windows, Windows Server, macOS, Linux) to ensure policy continues to be delivered for devices that change management types, for example during MDM enrollment.
If necessary, dynamic groups containing exclusively devices that are managed by Defender for Endpoint can be targeted by defining a dynamic group using the managementType attribute MicrosoftSense. Use of this attribute targets all devices that are managed by Defender for Endpoint via the security settings management functionality, and devices remain in this group only while managed by Defender for Endpoint.
Also, when configuring security settings management, if you intend to manage entire OS platform fleets using Microsoft Defender for Endpoint, by selecting all devices instead of tagged devices in the Microsoft Defender for Endpoint Enforcement Scope page, understand that any synthetic registrations are counted against Microsoft Entra ID quotas the same as full registrations.
Which solution should I use?
Microsoft Intune includes several methods and policy types to manage the configuration of Defender for Endpoint on devices. The following table identifies the Intune policies and profiles that support deployment to devices managed by Defender for Endpoint security settings management and can help you identify if this solution is right for your needs.
When you deploy an endpoint security policy that's supported for both Defender for Endpoint security settings management and Microsoft Intune, a single instance of that policy is processed by:
- Devices supported through security settings management (Microsoft Defender)
- Devices that are managed by either Intune or Configuration Manager.
Profiles for the Windows 10 and later platform aren't supported for devices managed by security settings management.
Following profiles are supported for each device type:
Linux
The following policy types support the Linux platform.
| Endpoint security policy | Profile | Defender for Endpoint security settings management | Microsoft Intune |
|---|---|---|---|
| Antivirus | Microsoft Defender Antivirus |  |
 |
| Antivirus | Microsoft Defender Antivirus exclusions |  |
 |
| Endpoint detection and response | Endpoint detection and response |  |
 |
| Endpoint detection and response | Microsoft Defender Global Exclusions (AV+EDR) |  |
 |
macOS
The following policy types support the macOS platform.
| Endpoint security policy | Profile | Defender for Endpoint security settings management | Microsoft Intune |
|---|---|---|---|
| Antivirus | Microsoft Defender Antivirus |  |
 |
| Antivirus | Microsoft Defender Antivirus exclusions |  |
 |
| Endpoint detection and response | Endpoint detection and response |  |
 |
Windows
To support use with Microsoft Defender security settings management, your policies for Windows devices must use the Windows platform. Each profile for the Windows platform can apply to devices that are managed by Intune and to devices that are managed by security settings management.
| Endpoint security policy | Profile | Defender for Endpoint security settings management | Microsoft Intune |
|---|---|---|---|
| Antivirus | Defender Update controls |  |
 |
| Antivirus | Microsoft Defender Antivirus |  |
 |
| Antivirus | Microsoft Defender Antivirus exclusions |  |
 |
| Antivirus | Windows Security Experience |  |
 |
| Attack Surface Reduction | Attack Surface Reduction Rules |  |
 |
| Attack Surface Reduction | Device Control | Note 1 |  |
| Endpoint detection and response | Endpoint detection and response |  |
 |
| Firewall | Firewall |  |
 |
| Firewall | Firewall Rules |  |
 |
1 - This profile is visible in the Defender portal but isn't supported for devices managed only by Microsoft Defender through the Microsoft Defender security settings management scenario. This profile is supported only for devices managed by Intune.
Each Intune endpoint security profile is a discrete group of settings intended for use by security admins who focus on protecting devices in your organization. The following are descriptions of the profiles that are supported by the security settings management scenario:
Antivirus policies manage the security configurations found in Microsoft Defender for Endpoint.
Note
While endpoints don't require a restart in order to apply modified settings or new policies, there's an issue where the AllowOnAccessProtection and DisableLocalAdminMerge settings might at times require end users to restart their devices for these settings to update. This issue is under investigation in order to provide a resolution.
Attack surface reduction (ASR) policies focus on minimizing the places where your organization is vulnerable to cyberthreats and attacks. With security settings management, ASR rules apply to devices that run Windows 10, Windows 11, and Windows Server.
For current guidance about which settings apply to the different platforms and versions, see ASR rules supported operating systems in the Windows Threat protection documentation.
Tip
To help keep supported endpoints up to date, consider using the modern unified solution for Windows Server 2012 R2 and 2016.
Also see:
- Overview of attack surface reduction in the Windows Threat protection documentation.
Endpoint detection and response (EDR) policies manage the Defender for Endpoint capabilities that provide advanced attack detections that are near real-time and actionable. Based on EDR configurations, security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
Firewall policies focus on the Defender firewall on your devices.
Firewall Rules are a type of profile for Firewall policy that is comprised of granular rules for Firewalls, including specific ports, protocols, applications, and networks.
Configure your tenant to support Defender for Endpoint security settings management
To support security settings management through the Microsoft Intune admin center, you must enable communication between them from within each console.
The following sections guide you through that process.
Configure Microsoft Defender for Endpoint
In the Microsoft Defender portal, as a security administrator:
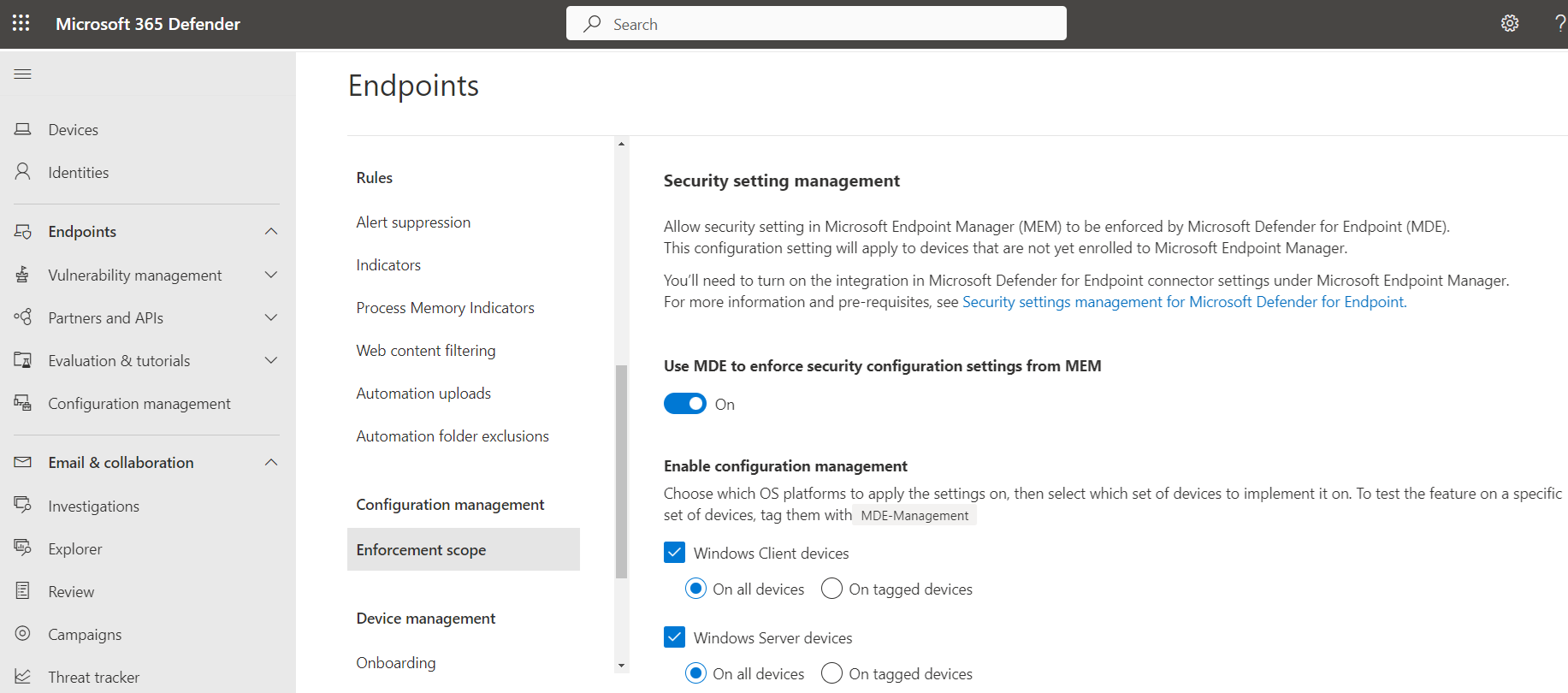
Sign in to the Microsoft Defender portal and go to Settings > Endpoints > Configuration Management > Enforcement Scope and enable the platforms for security settings management.
Note
If you have the Manage security settings in Security Center permission in the Microsoft Defender portal, and are simultaneously enabled to view devices from all Device Groups (no role-based access control limits on your user permissions), you can also perform this action.
Initially, we recommend testing the feature for each platform by selecting the platforms option for On tagged devices, and then tagging the devices with the
MDE-Managementtag.Tip
Use the proper device tags to test and validate your rollout on a small number of devices.
When you deploy to the All devices group, any device that falls into the scope configured will automatically be enrolled.
While most devices complete enrollment and apply assigned policy within a few minutes, a device can sometimes take up to 24 hours to complete enrollment.
Important
Dynamic asset rules are not currently supported for this task. For more information, see Create dynamic rules for devices in asset rule management.
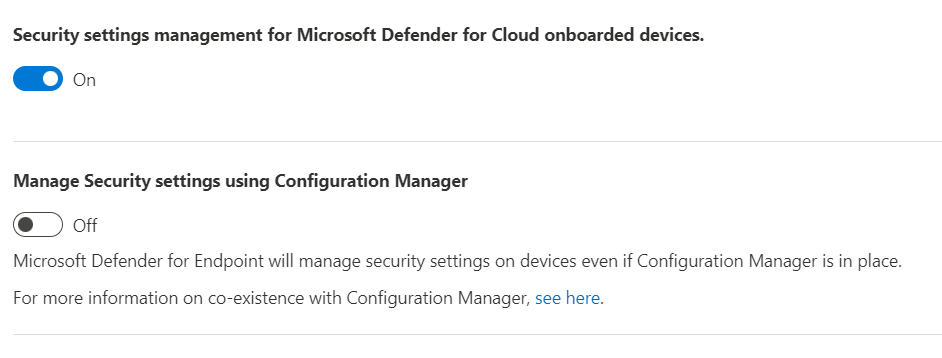
Configure the feature for Microsoft Defender for Cloud onboarded devices and Configuration Manager authority settings to fit your organization's needs:
Tip
To ensure your Microsoft Defender portal users have consistent permissions across portals, if not already provided, request that your IT administrator grants them the Microsoft Intune Endpoint Security Manager built-in RBAC role.
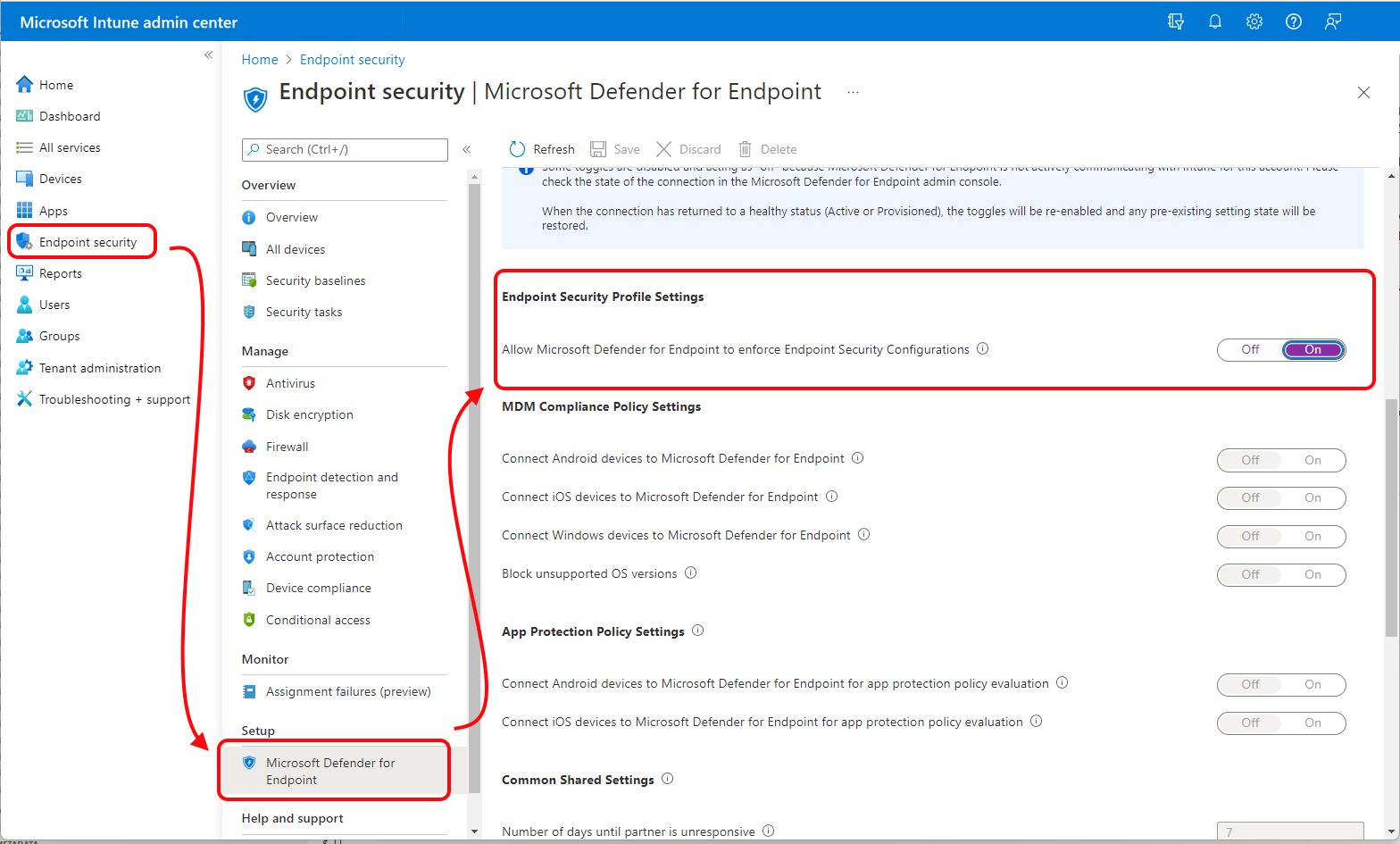
Configure Intune
In the Microsoft Intune admin center, your account needs permissions equal to Endpoint Security Manager built-in Role based access control (RBAC) role.
Sign in to the Microsoft Intune admin center.
Select Endpoint security > Microsoft Defender for Endpoint, and set Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations to On.
When you set this option to On, all devices in the platform scope for Microsoft Defender for Endpoint that aren't managed by Microsoft Intune qualify to onboard to Microsoft Defender for Endpoint.
Onboard devices to Microsoft Defender for Endpoint
Microsoft Defender for Endpoint supports several options to onboard devices. For current guidance, see Onboard to Microsoft Defender for Endpoint in the Defender for Endpoint documentation.
Coexistence with Microsoft Configuration Manager
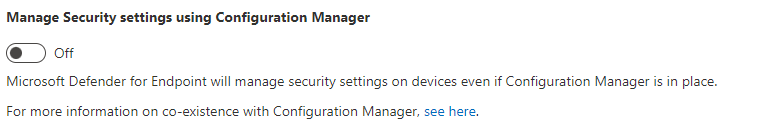
In some environments, it might be desired to use security settings management with devices managed by Configuration Manager. If you use both, you need to control policy through a single channel. Use of more than one channel creates the opportunity for conflicts and undesired results.
To support this, configure the Manage Security settings using Configuration Manager toggle to Off. Sign in to the Microsoft Defender portal and go to Settings > Endpoints > Configuration Management > Enforcement Scope:
Create Microsoft Entra Groups
After devices onboard to Defender for Endpoint, you'll need to create device groups to support deployment of policy for Microsoft Defender for Endpoint. To identify devices that have enrolled with Microsoft Defender for Endpoint but aren't managed by Intune or Configuration Manager:
Sign in to Microsoft Intune admin center.
Go to Devices > All devices, and then select the column Managed by to sort the view of devices.
Devices that onboard to Microsoft Defender for Endpoint and are registered but aren't managed by Intune display Microsoft Defender for Endpoint in the Managed by column. These are the devices that can receive policy for security management for Microsoft Defender for Endpoint.
Starting on September 25, 2023, devices that use security management for Microsoft Defender for Endpoint can no longer be identified by using the following system labels:
- MDEJoined - A now deprecated tag that was previously added to devices that were joined to the directory as part of this scenario.
- MDEManaged - A now deprecated tag that was previously added to devices that actively used the security management scenario. This tag is removed from the device if Defender for Endpoint stops managing the security configuration.
Instead of using system labels, you can use the management type attribute, and configure it to MicrosoftSense.
You can create groups for these devices in Microsoft Entra or from within the Microsoft Intune admin center. When creating groups, you can use the OS value for a device if you're deploying policies to devices running Windows Server vs devices that run a client version of Windows:
- Windows 10 and Windows 11 - The deviceOSType or OS displays as Windows
- Windows Server - The deviceOSType or OS displays as Windows Server
- Linux Device - The deviceOSType or OS displays as Linux
Sample Intune Dynamic Groups with Rule Syntax
Windows Workstations:
Windows Servers:
Linux Devices:
Important
In May 2023, deviceOSType updated to distinguish between Windows clients and Windows Servers.
Custom scripts and Microsoft Entra dynamic device groups created before this change that specify rules that reference only Windows might exclude Windows Servers when used with the Security Management for Microsoft Defender for Endpoint solution. For example:
- If you have a rule that uses the
equalsornot equalsoperator to identify Windows, this change affects your rule. That is because previously both Windows and Windows Server were reported as Windows. To continue to include both, you must update the rule to also reference Windows Server. - If you have a rule that uses the
containsorlikeoperator to specify Windows, then your rule isn't affected by this change. These operators can find both Windows and Windows Server.
Tip
Users that are delegated the ability to manage endpoint security settings might not have the ability to implement tenant-wide configurations in Microsoft Intune. Check with your Intune administrator for more information on roles and permissions in your organization.
Deploy policy
After creating one or more Microsoft Entra groups that contain devices managed by Microsoft Defender for Endpoint, you can create and deploy the following policies for security settings management to those groups. The policies and profiles available vary by platform.
For the list of policy and profile combinations supported for security settings management, see the chart in Which solution should I use, found in this article.
Tip
Avoid deploying multiple policies that manage the same setting to a device.
Microsoft Intune supports deploying multiple instances of each endpoint security policy type to the same device, with each policy instance being received by the device separately. Therefore, a device might receive separate configurations for the same setting from different policies, which results in a conflict. Some settings (like Antivirus Exclusions) merge on the client and apply successfully.
Sign in to the Microsoft Intune admin center.
Go to Endpoint security, select the type of policy you want to configure, and then select Create Policy.
For the policy, select the Platform and the Profile that you want to deploy. For a list of the Platforms and Profiles that support security settings management, see the chart in Which solution should I use? earlier in this article.
Note
The supported profiles apply to devices that communicate through Mobile Device Management (MDM) with Microsoft Intune and devices that communicate using the Microsoft Defender for Endpoint client.
Ensure you review your targeting and groups as necessary.
Select Create.
On the Basics page, enter a name and description for the profile, then choose Next.
On the Configuration settings page, select the settings you want to manage with this profile.
To learn more about a setting, expand its information dialog and select the Learn more link to view the on-line Configuration Service Provider (CSP) documentation or related details, for that setting.
When you're done configuring settings, select Next.
On the Assignments page, select the Microsoft Entra groups that receive this profile. For more information on assigning profiles, see Assign user and device profiles.
Select Next to continue.
Tip
- Assignment filters aren't supported for devices managed by security settings management.
- Only Device Objects are applicable for Microsoft Defender for Endpoint management. Targeting users is not supported.
- Policies apply to both Microsoft Intune and Microsoft Defender for Endpoint clients.
Complete the policy creation process and then on the Review + create page, select Create. The new profile is displayed in the list when you select the policy type for the profile you created.
Wait for the policy to be assigned and view a success indication that policy was applied.
You can validate that settings were applied locally on the client by using the Get-MpPreference command utility.
Monitor status
Intune:
Status and reports for policies that target devices in this channel are available from the policy node under Endpoint security in the Microsoft Intune admin center.
Drill in to the policy type and then select the policy to view its status. You can view the list of platforms, policy types, and profiles that support security settings management in the table in Which solution should I use, earlier in this article.
When you select a policy, you can view information about the device check-in status, and can select:
- View report - View a list of devices that received the policy. You can select a device to drill in and see its per-setting status. You can then select a setting to view more information about it, including other policies that manage that same setting, which could be a source of conflict.
- Per setting status - View the settings that are managed by the policy, and a count of success, errors, or conflicts for each setting.
Defender Portal:
You can also monitor the Intune policies that are applied from within the Microsoft Defender portal. Within the portal, go to Endpoints, expand configuration management and select Endpoint security policies. Select a policy to view its status, and then select:
- Overview - View an overview of the groups the policy is applied to, the policy settings that are applied, and device check-in status.
- Policy Settings Values - View the settings that are configured by the policy.
- Policy settings status - View the settings that are managed by the policy, and a count of success, errors, or conflicts for each setting.
- Applied devices - View the devices to which the policy is applied.
- Assigned Groups - View the groups to which the policy is assigned.
For more information, see Manage endpoint security policies in Microsoft Defender for Endpoint in the Defender content.
Frequently asked questions and considerations
Device check-in frequency
Devices managed by this capability check-in with Microsoft Intune every 90 minutes to update policy.
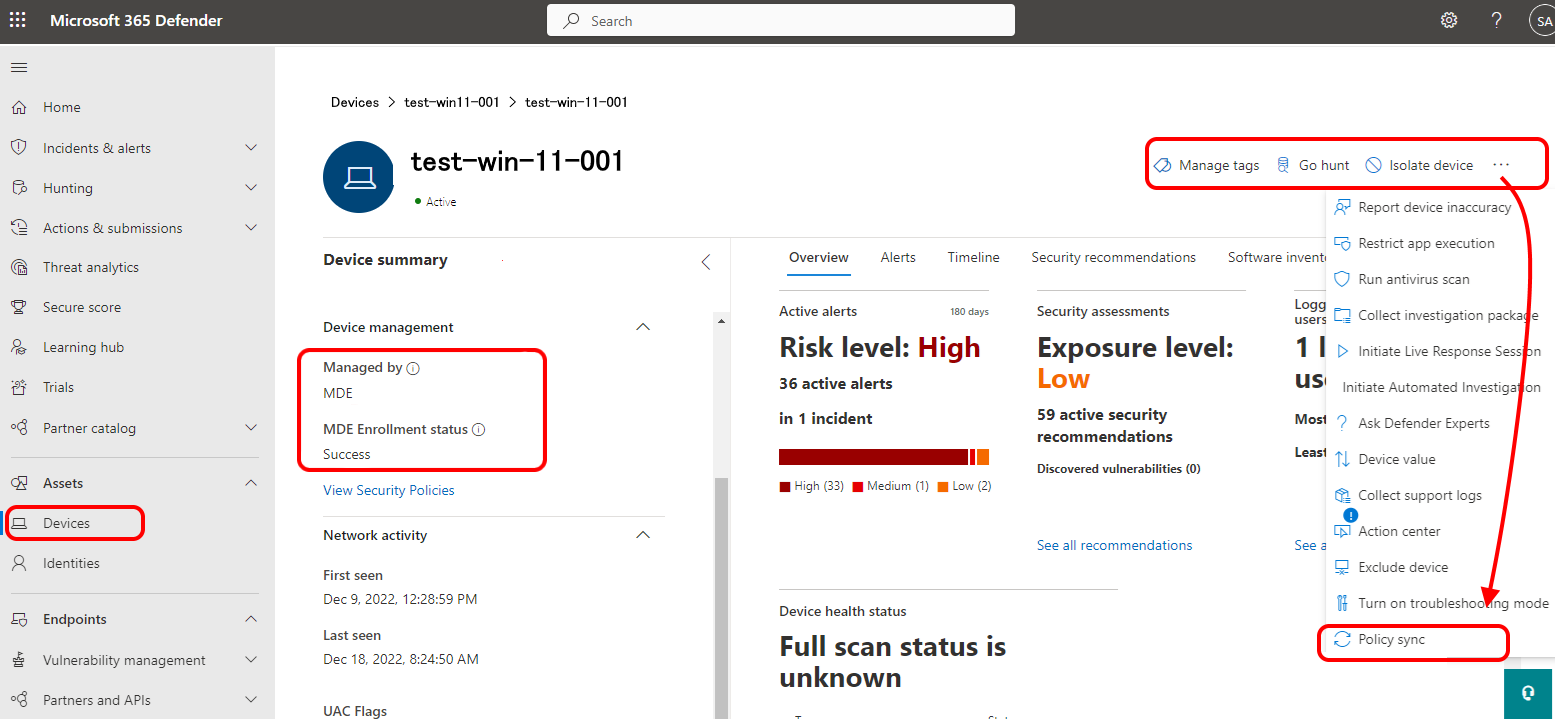
You can manually sync a device on-demand from the Microsoft Defender portal. Sign-in to the portal and go to Devices. Select a device that is managed by Microsoft Defender for Endpoint, and then select the Policy sync button:
The Policy sync button only appears for devices that are successfully managed by Microsoft Defender for Endpoint.
Devices protected by tamper protection
If a device has tamper protection turned on, it isn't possible to edit the values of Tamper-protected settings without disabling Tamper Protection first.
Assignment Filters and security settings management
Assignment filters aren't supported for devices communicating through the Microsoft Defender for Endpoint channel. While assignment filters can be added to a policy that could target these devices, the devices ignore assignment filters. For assignment filter support, the device must be enrolled in to Microsoft Intune.
Deleting and removing devices
You can delete devices that use this flow using one of two methods:
- From within the Microsoft Intune admin center go to Devices > All devices, select a device that displays either MDEJoined or MDEManaged in the Managed by column, and then select Delete.
- You can also remove devices from the scope of Configuration Management in the Security Center.
Once a device is removed from either location, that change propagates to the other service.
Unable to enable the Security Management for Microsoft Defender for Endpoint workload in Endpoint Security
While an Administrator with permissions in both services can complete initial provisioning flows, the following roles are sufficient to complete configurations in each separate service:
- For Microsoft Defender, use the Security Administrator role.
- For Microsoft Intune, use the Endpoint Security Manager role.
Microsoft Entra joined devices
Devices that are joined to Active Directory use their existing infrastructure to complete the Microsoft Entra hybrid join process.
Unsupported security settings
The following security settings are pending deprecation. The Defender for Endpoint security settings management flow doesn't support these settings:
- Expedite telemetry reporting frequency (under Endpoint Detection and Response)
- AllowIntrusionPreventionSystem (under Antivirus)
Use of security settings management on domain controllers
Security settings management is supported on domain controllers. To manage security settings on domain controllers, you must enable it in the enforcement scope page (go to Settings > Endpoints Enforcement scope). Windows Server devices must be enabled before you can enable configuration of domain controllers. Additionally, if the on tagged devices option is selected for Windows Servers, configuration of domain controllers is limited to tagged devices, too.
Caution
- Misconfiguration of domain controllers could have a negative impact on both your security posture and operational continuity.
- If configuration of domain controllers is enabled in your tenant, make sure to review all Windows policies to make sure you're not unintentionally targeting Microsoft Entra device groups that contain domain controllers. To minimize risk to productivity, firewall policies aren't supported on domain controllers.
- We recommend reviewing all policies targeted to domain controllers before unenrolling those devices. Make any required configurations first, and then unenroll your domain controllers. Defender for Endpoint configuration is maintained on each device after the device is unenrolled.
Microsoft Defender for Endpoint and PowerShell
Some Microsoft Defender for Endpoint client functions use PowerShell. For example, Live Response can execute custom scripts from an approved library. These functions run in an instance of PowerShell executed by the Defender for Endpoint client.
Troubleshooting device issues is more difficult if administrators are blocked from executing PowerShell. Performance and communications problems can be diagnosed more easily with PowerShell scripts.
Microsoft Defender for Endpoint security settings management will not work for a device that has PowerShell configured to run in Constrained Language Mode. For more information, see about_Language_Modes in the PowerShell documentation.
Managing security through Defender for Endpoint if you were previously using a third-party security tool
If you previously had a third-party security tool on the machine and are now managing it with Defender for Endpoint, you might see some impact on Defender for Endpoint's capability to manage Security settings in rare cases. In such cases, as a troubleshooting measure, uninstall and reinstall the latest version of Defender for Endpoint on your machine.
Related content
Manage endpoint security policies in Microsoft Defender for Endpoint in the Defender documentation.