Network provider details in the Microsoft 365 Admin Center
We try to detect network provider device interference between your tenant users and Microsoft 365 services. Here are the types of device interference we can detect.
Percentage refers to the percentage of media streams for Teams, and percentage of connections for Exchange and SharePoint.
SSL break and inspect test
This test detects a private or unknown certificate presented by a network device to your tenant users for data path connections to Microsoft 365 services, a private certificate is typically used when the network device intends to perform break and inspect operation at the SSL or TLS layer for those connections. We may not be able to show you the detected certificate issuer names due to privacy reasons.
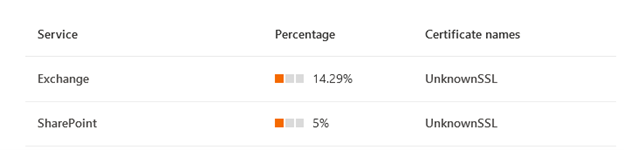
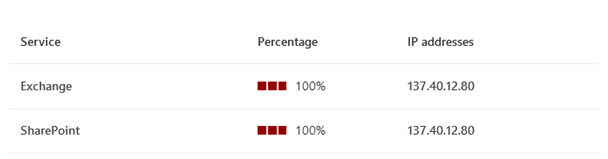
Incorrect destination IP address detected
This indicates that the destination endpoint representing Microsoft 365 endpoints have incorrect or unfamiliar IP addresses assigned to them. Typically, this means there's an intermediate network device acting as a proxy and we'll show you the incorrect or unfamiliar IP address detected.
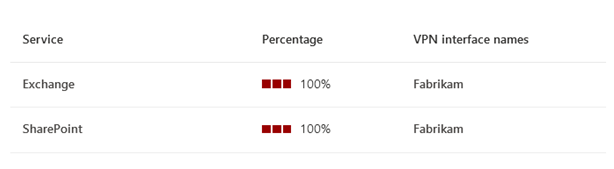
VPN or tunneling detected
This indicates that the network taken to connect to Microsoft 365 endpoints involves a VPN or traffic tunneling. A VPN or traffic tunneling might cause backhaul of network traffic and lead to network performance issues that impacts user experience.
No device interference detected
This is aligned with our connectivity principles and indicates that there was no device interference detected between your tenant users and Microsoft 365 services.
Related articles
Network connectivity in the Microsoft 365 admin center
Network provider program data calculations
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for