Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
- Microsoft Defender for Endpoint on macOS
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for business
This article describes how to deploy Microsoft Defender for Endpoint on macOS through Microsoft Intune.
Prerequisites and system requirements
Before you get started, see the main Microsoft Defender for Endpoint on macOS page for an overview of Microsoft Defender for Endpoint on macOS, including its capabilities and features. It also includes links to additional resources for more information. For a description of prerequisites and system requirements for the current software version, see Microsoft Defender for Endpoint on MacOS prerequisites.
Important
If you want to run multiple security solutions side by side, see Considerations for performance, configuration, and support.
You might have already configured mutual security exclusions for devices onboarded to Microsoft Defender for Endpoint. If you still need to set mutual exclusions to avoid conflicts, see Add Microsoft Defender for Endpoint to the exclusion list for your existing solution.
Overview
The following table summarizes the steps to deploy and manage Microsoft Defender for Endpoint on macOS via Microsoft Intune. See the following table for more detailed steps:
| Step | Sample file name | Bundle identifier |
|---|---|---|
| Approve system extension | sysext.mobileconfig |
N/A |
| Network extension policy | netfilter.mobileconfig |
N/A |
| Full Disk Access | fulldisk.mobileconfig |
com.microsoft.wdav.epsext |
| Microsoft Defender for Endpoint configuration settings If you're planning to run non-Microsoft antivirus on macOS, set passiveMode to true. |
MDE_MDAV_and_exclusion_settings_Preferences.xml |
com.microsoft.wdav |
| Background services | background_services.mobileconfig |
N/A |
| Configure Microsoft Defender for Endpoint notifications | notif.mobileconfig |
com.microsoft.wdav.tray |
| Accessibility settings | accessibility.mobileconfig |
com.microsoft.dlp.daemon |
| Bluetooth | bluetooth.mobileconfig |
com.microsoft.dlp.agent |
| Configure Microsoft AutoUpdate (MAU) | com.microsoft.autoupdate2.mobileconfig |
com.microsoft.autoupdate2 |
| Device Control | DeviceControl.mobileconfig |
N/A |
| Data Loss Prevention | DataLossPrevention.mobileconfig |
N/A |
| Download the onboarding package | WindowsDefenderATPOnboarding__MDATP_wdav.atp.xml |
com.microsoft.wdav.atp |
| Deploy the Microsoft Defender for Endpoint on macOS application | Wdav.pkg |
N/A |
Create system configuration profiles
The next step is to create system configuration profiles that Microsoft Defender for Endpoint needs. Open the Microsoft Intune admin center
Step 1: Approve system extensions
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
Under Configuration tab, On the Policies tab, select + Create > + New Policy.
Under Platform, select macOS.
Under Profile type, select Settings catalog.
Select Create.
On the Basics tab, Name the profile and enter a Description. Then select Next.
On the Configuration settings tab**,** select + Add settings.
In the Settings picker, expand the System Configuration category, and then select System Extensions and check Allowed System Extensions.
Close the Settings picker, and then select + Edit instance.
Configure the following entries in the Allowed system extensions section, then select Save, then select Next.
Allowed System Extensions Team Identifier com.microsoft.wdav.epsextUBF8T346G9com.microsoft.wdav.netextUBF8T346G9On the Scopes tab, (optional) select scope tags, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices or users are located, then select Next.
Review the configuration profile, then select Create.
Step 2: Network filter
As part of the Endpoint Detection and Response capabilities, Microsoft Defender for Endpoint on macOS inspects socket traffic and reports this information to the Microsoft 365 Defender portal. The following policy allows the network extension to perform this functionality.
Download netfilter.mobileconfig from GitHub repository.
Important
Only one .mobileconfig (plist) for Network Filter is supported. Adding multiple Network Filters leads to network connectivity issues on macOS. This issue isn't specific to Defender for Endpoint on macOS.
To configure your network filter:
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS Network Filter), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the netfilter.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 3: Full Disk Access
Note
With macOS Catalina (10.15) or newer, in order to provide privacy for the end-users, it created the FDA (Full Disk Access). Enabling TCC (Transparency, Consent & Control) through a Mobile Device Management solution such as Intune, eliminates the risk of Defender for Endpoint losing Full Disk Access Authorization to function properly.
This configuration profile grants Full Disk Access to Microsoft Defender for Endpoint. If you previously configured Microsoft Defender for Endpoint through Intune, we recommend you update the deployment with this configuration profile.
Download fulldisk.mobileconfig from GitHub repository.
To configure Full Disk Access:
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS Full disk access), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the fulldisk.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Note
Full Disk Access granted through Apple MDM Configuration Profile isn't reflected in System Settings > Privacy & Security > Full Disk Access.
Step 4: Background services
Caution
macOS 13 (Ventura) contains new privacy enhancements. Beginning with this version, by default, applications can't run in background without explicit consent. Microsoft Defender for Endpoint must run its daemon process in background. This configuration profile grants Background Service permission to Microsoft Defender for Endpoint. If you previously configured Microsoft Defender for Endpoint through Microsoft Intune, we recommend you update the deployment with this configuration profile.
Download background_services.mobileconfig from GitHub repository.
To configure background services:
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS background services), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the background_services.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 5: Notifications
This profile is used to allow Microsoft Defender for Endpoint on macOS and Microsoft AutoUpdate to display notifications in UI.
Download notif.mobileconfig from GitHub repository.
To turn off notifications for the end users, you can change Show NotificationCenter from true to false in notif.mobileconfig.
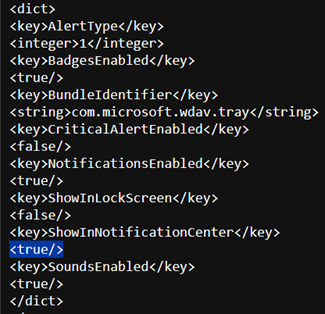
To configure notifications:
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS Notifications consent), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the notif.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 6: Accessibility settings
This profile is used to allow Microsoft Defender for Endpoint on macOS to access the accessibility settings on Apple macOS High Sierra (10.13.6) and newer.
Download accessibility.mobileconfig from GitHub repository.
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS Accessibility settings), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the accessibility.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 7: Bluetooth permissions
Caution
macOS 14 (Sonoma) contains new privacy enhancements. Beginning with this version, by default, applications can't access Bluetooth without explicit consent. Microsoft Defender for Endpoint uses it if you configure Bluetooth policies for Device Control.
Download bluetooth.mobileconfig from GitHub repository and use the same workflow as in Step 6: Accessibility settings to enable Bluetooth access.
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MacOS Bluetooth consent), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the bluetooth.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Note
Bluetooth granted through Apple MDM Configuration Profile isn't reflected in System Settings => Privacy & Security => Bluetooth.
Step 8: Microsoft AutoUpdate
This profile is used to update the Microsoft Defender for Endpoint on macOS via Microsoft AutoUpdate (MAU). If you're deploying Microsoft Defender for Endpoint on macOS, you have the options to get an updated version of the application (Platform Update) that are in the different channels mentioned here:
- Beta (Insiders-Fast)
- Current channel (Preview, Insiders-Slow)
- Current channel (Production)
For more information, see Deploy updates for Microsoft Defender for Endpoint on macOS.
Download com.microsoft.autoupdate2.mobileconfig from the GitHub repository.
Note
The sample com.microsoft.autoupdate2.mobileconfig from the GitHub repository is set to Current Channel (Production).
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example,
macOS Microsoft Auto-Update), and enter a Description, then select Next.On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the com.microsoft.autoupdate2.mobileconfig Configuration profile file downloaded earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 9: Microsoft Defender for Endpoint configuration settings
In this step, you will configure anti-malware and EDR policies, using either the Microsoft Defender portal (Step 9a.) OR the Microsoft Intune portal (Step 9b.), depending on your preference or your organization requirements.
Note
Complete only one of the following steps (9a. OR 9b.)
9a. Set policies using the Microsoft Defender portal
Set policies using the Microsoft Defender portal by following these steps:
Go through Configure Microsoft Defender for Endpoint in Intune before setting the security policies using Microsoft Defender for Endpoint Security Settings Management.
In the Microsoft Defender portal, go to Configuration management > Endpoint security policies > Mac policies > Create new policy.
Under Select Platform, select macOS.
Under Select Template, select the Microsoft Defender Antivirus template (or the Endpoint detection and response if you are repeating the actions as per 9. below) then select Create Policy.
Specify a name (for example: Microsoft Defender Anti-Virus Policy (or EDR Policy)) and description for the policy, then select Next.
On the Configuration settings tab, select the appropriate settings for your organization, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
On the Review tab, select Save.
Repeat actions from 2. to 8. above to create an Endpoint detection and response (EDR) policy.
9b. Set policies using Microsoft Intune
Set policies using Microsoft Defender Portal by implementing the following instructions:
To create this profile, copy the code for the Intune recommended profile (recommended) or the Intune full profile (for advanced scenarios), and save the file as com.microsoft.wdav.xml.
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example,
macOS wdav preferences), and enter a Description, then select Next.On the Configuration settings tab, enter the Custom configuration profile name
com.microsoft.wdavChoose a Deployment channel and select Next.
Select the
com.microsoft.wdav.xmlConfiguration profile file created earlier, then select Next.On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Caution
You must enter the correct custom configuration profile name; otherwise, these preferences won't be recognized by Microsoft Defender for Endpoint.
For more information, see Set preferences for Microsoft Defender for Endpoint on Mac.
For more information about managing security settings, see:
- Manage Microsoft Defender for Endpoint on devices with Microsoft Intune
- Manage security settings for Windows, macOS, and Linux natively in Defender for Endpoint
Step 10: Network protection for Microsoft Defender for Endpoint on macOS (optional)
The Network protection setting is included in the Microsoft Defender Antivirus template created in step 9.
For more information about Network Protection for Microsoft Defender for Endpoint on MacOS see Network protection for MacOS
Step 11: Device Control for Microsoft Defender for Endpoint on macOS (optional)
The Device Control setting is included in the MacOS Full disk access template created in step 3.
For more information about Device Control for Microsoft Defender for Endpoint on macOS see Device Control for MacOS
Step 12: Publish the Microsoft Defender application
Important
The Microsoft Defender app for macOS splits features for both Microsoft Defender for Endpoint and Microsoft Purview Endpoint Data Loss Prevention, if you are also planning to onboard MacOS devices to Purview (Step 18), ensure Device Monitoring is turned on at this stage. To enable Purview Device Monitoring on the Microsoft Purview Portal go to Settings > Devices.
This step enables deploying Microsoft Defender for Endpoint to enrolled machines.
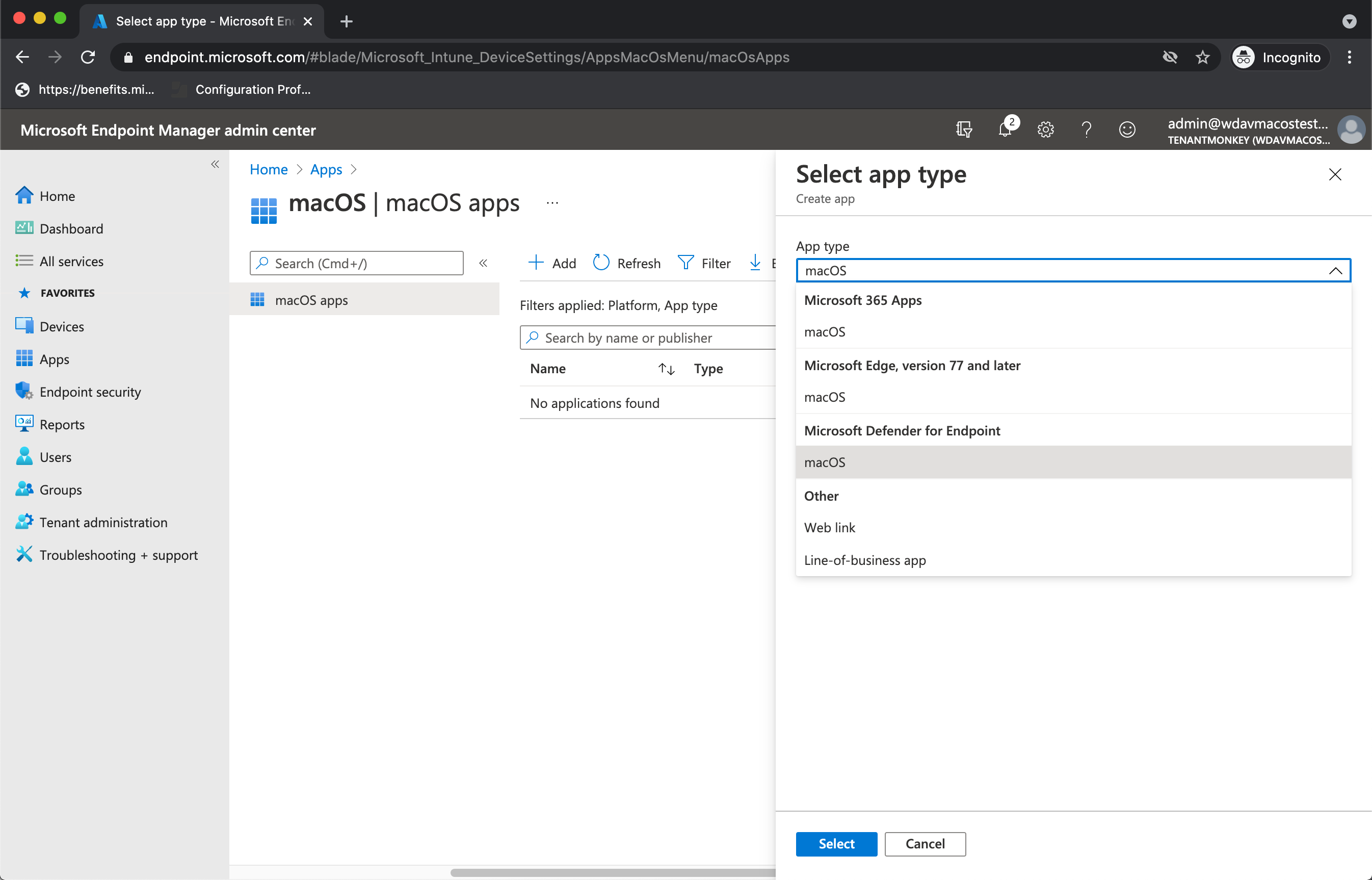
In the Microsoft Intune admin center, open Apps.
Expand Platforms, select macOS, then select +Create
Under App type, select Microsoft Defender for Endpoint > macOS, then select Select.
On the App information, keep the default values and select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
On the Review+Create tab, select Create.
For more information, see Add Microsoft Defender for Endpoint to macOS devices using Microsoft Intune.
Important
You should create and deploy the configuration profiles in the order specified (steps 1-12) for a successful system configuration.
Step 13: Download the Microsoft Defender for Endpoint onboarding package
To download the onboarding package from the Microsoft Defender portal:
In the Microsoft Defender portal, select Settings > Endpoints > Device management > Onboarding.
On the Select operating system to start the onboarding process drop-down, select macOS.
On the Deployment method drop-down, select Mobile Device Management / Microsoft Intune.
Select Download onboarding package. Save it as WindowsDefenderATPOnboardingPackage.zip to the same directory.
Extract the contents of the .zip file:
unzip WindowsDefenderATPOnboardingPackage.zipArchive: WindowsDefenderATPOnboardingPackage.zip warning: WindowsDefenderATPOnboardingPackage.zip appears to use backslashes as path separators inflating: intune/kext.xml inflating: intune/WindowsDefenderATPOnboarding.xml inflating: jamf/WindowsDefenderATPOnboarding.plist
Step 14: Deploy the Microsoft Defender for Endpoint onboarding package for MacOS
This profile contains license information for Microsoft Defender for Endpoint.
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab, select Create > New Policy.
Under Platform, select macOS.
Under Profile type, select Templates.
Under Template name, select Custom.
Select Create.
On the Basics tab, Name the profile, (for example: MDE onboarding for macOS), and enter a Description, then select Next.
On the Configuration settings tab, enter a Custom configuration profile name.
Choose a Deployment channel and select Next.
Select the WindowsDefenderATPOnboarding.xml Configuration profile file created earlier, then select Next.
On the Assignments tab, assign the profile to a group where the macOS devices and/or users are located, then select Next.
Review the configuration profile, then select Create.
Step 15: Check Device and Configuration status
Step 15a. View Status
There are multiple ways to look at this information in the Microsoft Intune admin center, including monitoring and reports per device, user, configuration policies and more. Here's an example:
In the Intune admin center, go to Devices, and under Manage Devices, select Configuration.
On the Policies tab select a policy, then on the Device and user check-in status select View Report.
Step 15b. Client device setup
Follow the steps outlined in Enroll your macOS device using the Company Portal app
Confirm device management.

Select Open System Preferences, locate Management Profile on the list, and select Approve.... Your Management Profile would be displayed as Verified:
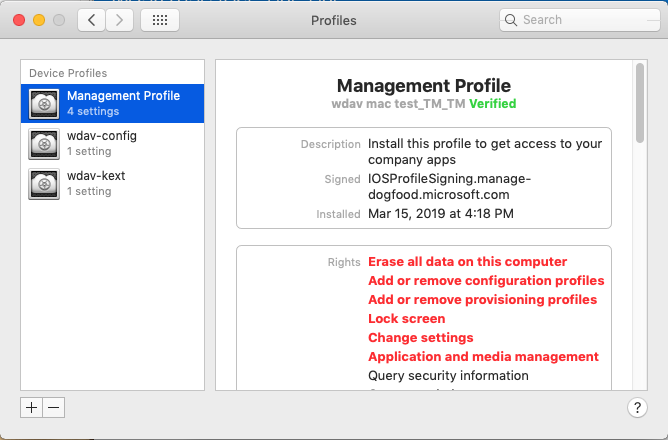
Select Continue and complete the enrollment.
You might now enroll more devices. You can also enroll them later, after finishing the provisioning system configuration and application packages.
In Intune, select Devices > All devices. Here you can see your device among the listed:
Step 15c. Verify client device state
After the configuration profiles are deployed to your devices, open System Settings > General > Device Management on your MacOS device.
Verify that all the configuration profiles are present and installed:
accessibility.mobileconfigbackground_services.mobileconfigbluetooth.mobileconfigcom.microsoft.autoupdate2.mobileconfigfulldisk.mobileconfig- Management Profile (this is the Intune system profile)
WindowsDefenderATPOnboarding.xml(this is the Defender for Endpoint onboarding package for macOS)netfilter.mobileconfignotif.mobileconfig
You should also see the Microsoft Defender icon in the top-right corner.

Step 16: Verify anti-malware detection
See the following article to test for an anti-malware detection review: Antivirus detection test for verifying device's onboarding and reporting services
Step 17: Verifying EDR detection
See the following article to test for an EDR detection review: EDR detection test for verifying device onboarding and reporting services
Step 18: Microsoft Purview Data Loss Prevention (DLP) for Endpoint on MacOS (strongly recommended)
See Get started with endpoint data loss prevention.
Troubleshooting
Issue: No license found.
Cause: Onboarding has not completed.
Resolution: Ensure you have completed steps 13 and 14 above.
Logging installation issues
See Logging installation issues for information on how to find the automatically generated log created by the installer, when an error occurs.
For information on troubleshooting procedures, see:
- Troubleshoot system extension issues in Microsoft Defender for Endpoint on macOS
- Troubleshoot installation issues for Microsoft Defender for Endpoint on macOS
- Troubleshoot license issues for Microsoft Defender for Endpoint on macOS
- Troubleshoot cloud connectivity issues for Microsoft Defender for Endpoint on macOS
- Troubleshoot performance issues for Microsoft Defender for Endpoint on macOS
Uninstallation
See Uninstalling for details on how to remove Microsoft Defender for Endpoint on macOS from client devices.