Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Symptoms
Conditional Access is a Microsoft Entra feature that helps make sure that devices that access corporate resources are correctly managed and secured. If Conditional Access policies are applied to the Microsoft Teams service, Android devices that access Teams must comply with the policies. Such devices include Teams phones, Teams displays, Teams panels, and Teams Rooms on Android. Otherwise, Conditional Access will prevent users from signing in to or using the Teams app on the devices.
If these policies are applied, you might experience one or more of the following issues on non-compliant devices:
- The devices can't sign in to Teams, or they get stuck in sign-in loops.
- The devices automatically sign out of Teams randomly.
- Microsoft Teams stops responding (freezes).
Cause
These issues can occur for the following reasons:
Unsupported Conditional Access policy or Intune device compliance policy settings
If a device is marked as non-compliant, the Microsoft Entra token-issuing service stops renewing the tokens for the device object or even revokes the token. In this case, the device can't get an updated authentication token, and it's forced to sign out.
To check the compliance status of your devices, use the Intune Device compliance dashboard.
The Sign-in frequency setting
This setting forces periodic reauthentication. This action might cause the devices to sign out randomly, depending on how many of your Conditional Access policies have different sign-in frequencies set. Whenever reauthentication occurs, the token is revoked and a new device object is created under the user account. If the number of device objects exceeds the Microsoft Entra device limit or Intune device limit, the user can't sign in to the device.
The Terms of Use (ToU) and MFA Conditional Access policies, if both are used
For more information, see Known issues with Teams phones.
Resolution
Identify the specific cause of the issue by checking multiple details about the affected user's access to the Teams app. To perform the checks that are required, you can either use an automated option or run the checks manually by using the steps provided.
Automated checks
The automated option is to run the Microsoft Teams Rooms Sign in connectivity test in the Microsoft Remote Connectivity Analyzer tool. This tool is used to troubleshoot connectivity issues that affect Teams. The connectivity test performs checks to verify a specific user's permissions to sign in to Teams by using a Teams Rooms device.
Note
- A Global Administrator account is required to run the Microsoft Teams Rooms sign-in connectivity test.
- The Microsoft Remote Connectivity Analyzer tool isn’t available for the GCC and GCC High Microsoft 365 Government environments.
To run the connectivity test, follow these steps:
- Open a web browser and navigate to the Microsoft Teams Rooms Sign in connectivity test.
- Sign in by using the credentials of a Global Administrator account.
- Specify the username for the account that can't access the Teams Rooms app.
- In the Device Selection field, select a type for the affected user's device.
- Enter the verification code that's displayed, and then select Verify.
- Select the checkbox to accept the terms of agreement, and then select Perform Test.
After the test finishes, the screen displays details about all the checks that were performed and whether the test succeeded, failed, or was successful but displayed a few warnings. Select the provided link for more information about the warnings and failures, and about how to resolve them.
Manual checks
To manually check user access to the Teams app, follow these steps:
Go to the sign-in logs in the Azure portal.
Select the User sign-ins (non-interactive) tab.
Select Add filters to add the following filters:
- Status: Select Failure, and then select Apply.
- Application: Enter Teams, and then select Apply.

For the affected usernames, look for items that have the following Application values:
- Microsoft Teams
- Microsoft Teams Service
- Microsoft Teams – Device Admin Agent
Select each item to view details about the failed sign-in. Usually, you can get more information from the following fields on the Basic info tab:
- Sign-in error code
- Failure reason
- Additional Details
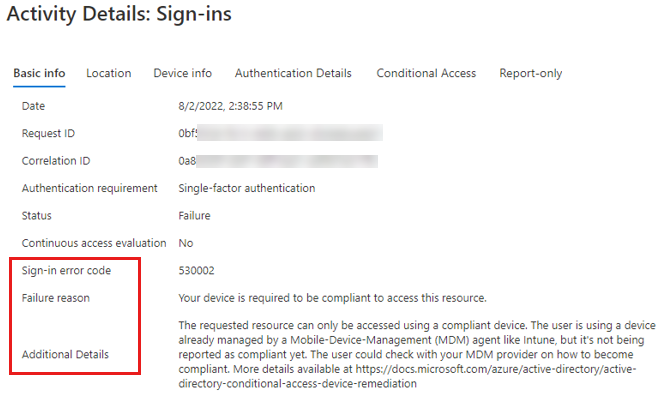
If the sign-in error code seems to be related to compliance, select the Conditional Access tab, and then look for policies that show a Failure result.
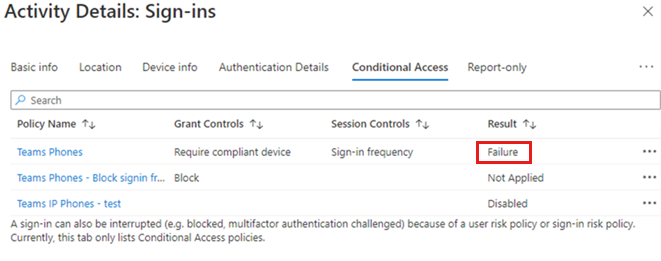
Review the policy details.
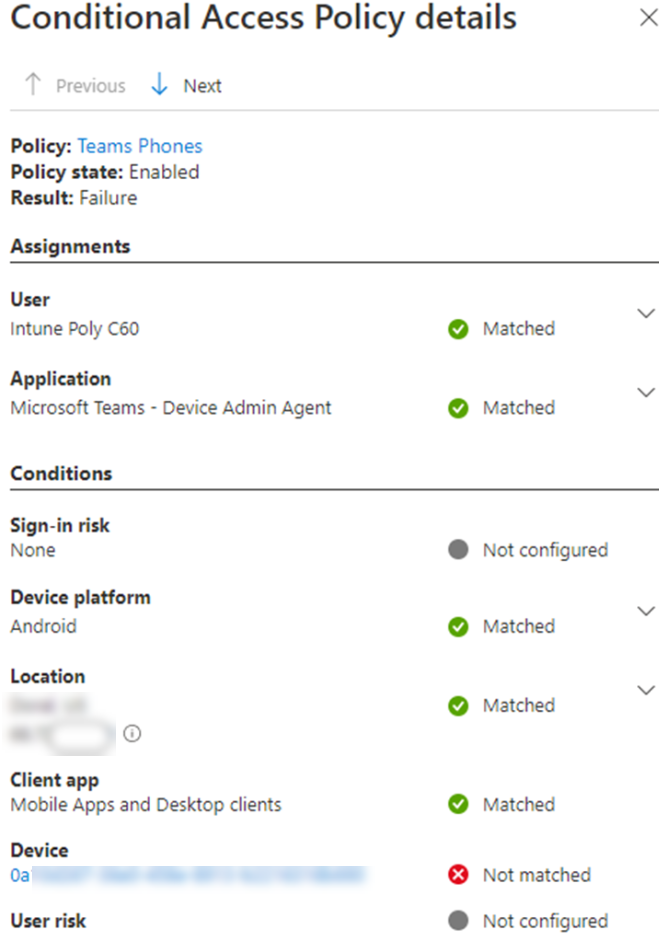
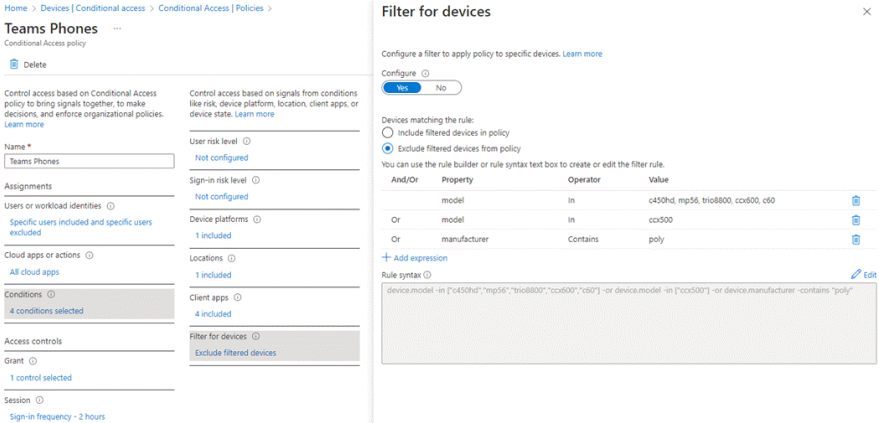
After you identify the specific Conditional Access policy that's causing the issue, you can use device filters to exclude the affected device from the policy. Commonly used device properties in device filters are manufacturer and model. These are used together with the Contains, StartsWith, and In operators.
Note
- Device filters apply to only device objects, not user accounts.
- Some attributes, such as model and manufacturer, can be set only if devices are enrolled in Intune. If your devices aren't enrolled in Intune, use extension attributes.
- Check each policy setting for unsupported settings for Teams devices.
The following screenshot shows a sample device filter.
References
- Supported Conditional Access and Intune device compliance policies for Microsoft Teams Rooms and Teams Android Devices
- App protection policies overview
- Conditional Access and compliance best practices for Microsoft Teams Rooms
- Authentication best practices for Microsoft Teams shared device management of Android devices
- Known issues in Teams Rooms and devices
- Video: Intune Compliance & Conditional Access with Teams Android devices