Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The Encrypting File System Remote Protocol (hereafter referred to as EFSRPC) is a Remote Procedure Call (RPC) interface that is used to manage data objects stored in an encrypted form. The objective of encrypting data in this fashion is to enforce access control policies and to provide confidentiality from unauthorized users.
EFSRPC is implemented in Windows to provide remote management for files encrypted by the Encrypting File System (EFS). EFS is the ability of the New Technology File System (NTFS) file system to encrypt files on disk in a manner that is transparent to the user. For more information on EFS, see [MSFT-EFS]. For more information about NTFS, see [MSFT-NTFS].
EFSRPC does not address how data is encrypted, how the encrypted data is stored, or how it is accessed for routine operations such as reading, writing, creating, and deleting. All these actions are specific to the server implementation. On Windows, NTFS provides the storage mechanism (the file is the unit of storage) and the Server Message Block (SMB) Protocol provides remote access to such files. For more information about SMB, see [MS-SMB] and [MS-SMB2].
EFSRPC models the underlying data encryption architecture using two basic constructs:
A set of data objects, each of which is encrypted independently and can be managed independently.
A set of access control subjects, each of which is represented by a key pair generated by a public key cryptographic algorithm. The public key of this key pair is embedded in a certificate and can be widely distributed in that form. The corresponding private key is held solely by the user or users who represent that subject. Thus, a given access control subject can correspond to one or more users, and a given user can possess the private keys for zero or more access control subjects. Access control subjects are further divided into two types:
Unprivileged user subjects, which are used for routine data access by ordinary users of the system. For convenience, this specification refers to such subjects as user certificate.
Data Recovery Agents (DRAs), which are controlled by system administrators. The storage system ensures that all active DRAs for the system are automatically authorized to access all encrypted objects on the system. If an unprivileged user loses the private key, an administrator can use a DRA's private key to recover the contents of encrypted objects.
EFSRPC also assumes that each encrypted object is associated with some security-related metadata, which contains information required for authorized users and DRAs to access the plaintext of the object. This specification refers to this security-related metadata as the EFSRPC Metadata.
EFSRPC does not specify how data is encrypted, stored, or accessed. It is possible to build a compliant EFSRPC implementation that uses a mechanism, such as access control lists (ACLs), instead of encryption to control access to data objects. For the purposes of this specification, the term encrypted is used to indicate that a data object and its metadata can be successfully manipulated through the EFSRPC methods, with the exception of the EfsRpcEncryptFileSrv method, which converts data objects from an unencrypted state to an encrypted state.
Within the preceding model, EFSRPC provides various categories of management routines. The syntax of the individual methods and rules for how these methods are processed on the server are specified in section 3.1.4.2. The categories of management routines that EFSRPC provides are as follows:
Requesting the server to convert objects from encrypted state to unencrypted state and vice versa.
EfsRpcEncryptFileSrv (section 3.1.4.2.5)
Creating, querying, and manipulating the EFSRPC Metadata. Clients use the following methods to query and change which user certificates can be used to decrypt an encrypted object. The set of user certificates with access to an object needs to be changed when the set of users with access to the object changes or when a user with access to the object changes the user certificate. The following methods can also be used to copy the access rights from one object to another; the EfsRpcDuplicateEncryptionInfoFile method is particularly well-suited for this purpose. Methods:
EfsRpcDuplicateEncryptionInfoFile (section 3.1.4.2.13)
Performing backup of encrypted objects in ciphertext form along with their EFSRPC Metadata, and restoring encrypted objects from such backups. Depending on the implementation of these methods, the backups that are created can expose the implementation-specific EFSRPC Metadata format to the client. The Windows implementation of these methods exposes the Windows EFSRPC Metadata format; however, Windows applications do not manipulate this information. The following methods are suitable for secure content archival or transferring encrypted data securely between servers of the same implementation because they do not require decrypting the data. Methods:
Controlling the server's encryption subsystem. Methods:
Most of the EFSRPC routines are stateless and can be called in any order. When one of these routines is called, the message exchange is as follows.
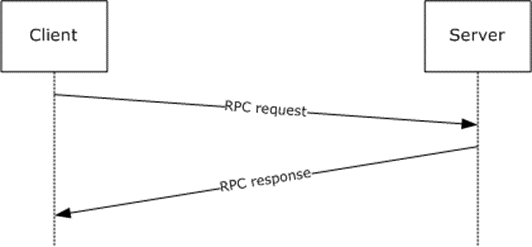
Figure 1: Message exchange for stateless routines
There are two routines in EFSRPC that are an exception to the stateless nature of the protocol. Several methods, collectively known as the EFSRPC raw methods, are an exception and need to be called in a specific order. This includes the EfsRpcOpenFileRaw, EfsRpcReadFileRaw, EfsRpcWriteFileRaw, and EfsRpcCloseRaw methods. The following two sequences are permissible.
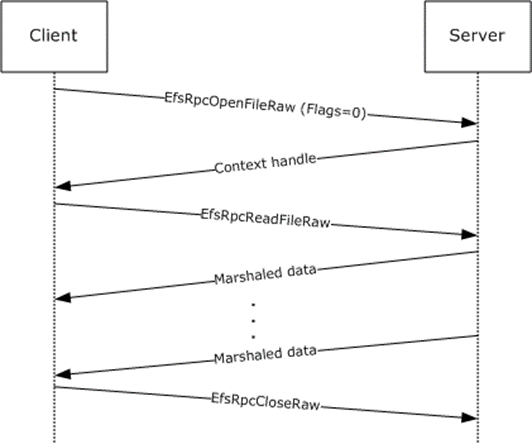
Figure 2: Message sequence for opening a file
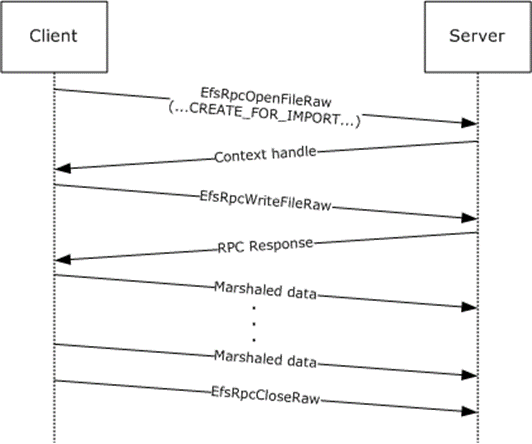
Figure 3: Message sequence for importing a file