Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
NTLM over a Server Message Block (SMB) transport is a common use of NTLM authentication and encryption. Although KILE is the preferred authentication method of an SMB session as described in section 1, when a client attempts to authenticate to an SMB server using the KILE protocol and fails, it can attempt to authenticate with NTLM.
The following is an example protocol flow of NTLM and Simple and Protected Generic Security Service Application Program Interface Negotiation Mechanism (SPNEGO) ([MS-SPNG]) authentication of an SMB session.
Note The NTLM messages are embedded in the SMB messages. For details about how SMB embeds NTLM messages, see [MS-SMB] section 4.1.
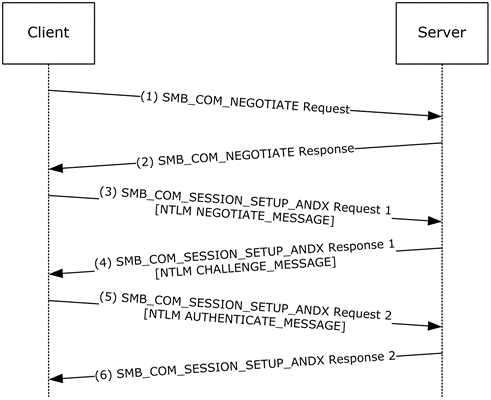
Figure 4: Message sequence to authenticate an SMB session
Steps 1 and 2: The SMB protocol negotiates protocol-specific options using the SMB_COM_NEGOTIATE ([MS-SMB] section 2.2.4.5) request and response messages.
Step 3: The client sends an SMB_COM_SESSION_SETUP_ANDX ([MS-SMB] section 2.2.4.6) request message. Assuming that NTLM authentication is negotiated, within this message an NTLM NEGOTIATE_MESSAGE (section 2.2.1.1) is embedded.
Step 4: The server responds with an SMB_COM_SESSION_SETUP_ANDX response message within which an NTLM CHALLENGE_MESSAGE (section 2.2.1.2) is embedded. The message includes an 8-byte random number, called a "challenge", that the server generates and sends in the ServerChallenge field of the message.
Step 5: The client extracts the ServerChallenge field from the NTLM CHALLENGE_MESSAGE and sends an NTLM AUTHENTICATE_MESSAGE (section 2.2.1.3) to the server (embedded in an SMB_COM_SESSION_SETUP_ANDX request message).
If the challenge and the response prove that the client knows the user's password, the authentication succeeds, and the client's security context is now established on the server.
Step 6: The server sends a success message embedded in an SMB_COM_SESSION_SETUP_ANDX response message.