4.1 Extended Security Authentication
The following diagram depicts the protocol message sequence for a multi-phase extended security exchange and previous versions enumeration and access on the share root folder.
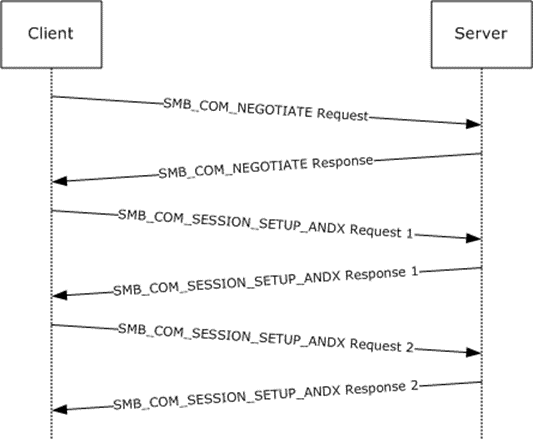
Figure 4: User authentication and session establishment sequence
Descriptions of the fields in this example are specified in [MS-CIFS] and section 2.2.4.1. Fields that are shown and highlighted in bold text are relevant to this extension. It is assumed that the client has successfully established a network connection with the server.
The client initiates the first message with an SMB_COM_NEGOTIATE request, as specified in [MS-CIFS]. The client specifies extended security negotiation in the header Flags2 field. It also includes NT LM 0.12 in the dialect strings list. The server constructs an extended SMB_COM_NEGOTIATE response packet that is denoted by the WordCount field. The server returns dialect index, its capabilities, GUID value, and the initial security binary large object (BLOB) obtained, as specified in [RFC2743] and defined in the preceding figure.
FRAME 1. Client negotiate request
-
Client -> Server: Command = SMB_COM_NEGOTIATE Flags2 Summary = 51207 (0xC807) 1100 1000 0000 0111 .... 1... .... .... = Extended security negotiation is supported Dialect Strings PC NETWORK PROGRAM 1.0 LANMAN1.0 Windows for Workgroups 3.1a LM1.2X002 LANMAN2.1 NT LM 0.12
FRAME 2. Server negotiate response
-
Server -> Client: Command = SMB_COM_NEGOTIATE NT status code = 0x0, STATUS_SUCCESS Word count = 17 Protocol Index = 5 (NT LM 0.12) Capabilities = 2147607549 (0x8001F3FD) 1000 0000 0000 0001 1111 0011 1111 1101 .... .... .... .... ..1. .... .... .... = Supports Pass-Thru levels 1... .... .... .... .... .... .... .... = Supports extended security Server GUID = 01 B3 1E 23 07 2A A4 4D A1 9F B6 69 F0 45 71 90 Security Blob in payload
The client uses the initial security BLOB that is returned by the server along with any user credential information in order to obtain its security BLOB, as specified in [RFC2743] and defined in section 3.2.4.2.4. The resulting security BLOB is sent to the server as part of the SMB_COM_SESSION_SETUP_ANDX extended request. The client also sends its capabilities and zero UID to mark the start of a new session setup exchange. The server verifies that the client requests extended security by checking the Flags2 and Capabilities fields in the request, accepts as input the client security BLOB, and processes it, as specified in [RFC2743]. In this case, the security package requires more processing and returns a second security BLOB to be returned to the client. Also, the server allocates a new UID and associates it with this session setup exchange.
Note Extended security can require multiple request and response exchanges between client and server to complete. The UID is defined by the server on first response to an extended session setup and is used for the lifetime of the session.
FRAME 3. Client request for extended session setup
-
Client -> Server: Command = SMB_COM_SESSION_SETUP_ANDX Header: Tid = 0x0000 Mid = 0x0070 Uid = 0x0000 Flags2 Summary = 51207 (0xC807) 1100 1000 0000 0111 .... 1... .... .... = Supports extended security Word count = 12 Capabilities = 0xA0000000 1010 0000 0000 0000 0000 0000 0000 0000 ..1. .... .... .... .... .... .... .... = Supports dynamic reauth 1... .... .... .... .... .... .... .... = Requests extended security Security Blob Length = 74 (0x4A) Security Blob in payload
FRAME 4. Server response with session setup continuation
-
Server -> Client: Command = SMB_COM_SESSION_SETUP_ANDX NT status code = 0xC0000016, STATUS_MORE_PROCESSING_REQUIRED Header: Tid = 0x0000 Mid = 0x0070 Uid = 0x0802 Flags2 Summary = 51207 (0xC807) 1100 1000 0000 0111 .... 1... .... .... = Extended security negotiation is supported Security Blob Length = 349 (0x15D) Security Blob in payload
The client accepts as input the server security BLOB and processes it, as specified in [RFC2743], and its output is returned to the server along with the UID. The server uses the UID value to associate this request with the pending session establishment. The server processes this request, as specified in [RFC4178], and receives a success result. At this point, the SMB_SESSION_SETUP_ANDX exchange is complete because the status code is not equal to STATUS_MORE_PROCESSING_REQUIRED. The final security BLOB is returned with the success indication.
FRAME 5. Client session setup request continuation
-
Client -> Server: Command = SMB_COM_SESSION_SETUP_ANDX Header: Tid = 0x0000 Mid = 0x0080 Uid = 0x0802 Flags2 Summary = 51207 (0xC807) 1100 1000 0000 0111 .... 1... .... .... = Extended security negotiation is supported Word count = 12 Security Blob Length = 226 (0xE2) Security Blob in payload
FRAME 6. Server response with session setup completion
-
Server -> Client: Command = SMB_COM_SESSION_SETUP_ANDX NT status code = 0x0, STATUS_SUCCESS Header: Tid = 0x0000 Mid = 0x0080 Uid = 0x0802 Security Blob Length = 9 (0x9) Security Blob in payload
At this point, the client has been successfully authenticated.