Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The audit log sync flows connect to the Office 365 Management Activity API reference to gather telemetry data, such as unique users and launches for apps. The flows use an HTTP action to access the API. In this article, you set up the app registration for the HTTP action and the environment variables that are needed to run the flows.
Note
The Center of Excellence (CoE) Starter Kit works without these flows. However, if the flows aren't used, usage information such as app launches and unique users is blank in the Power BI dashboard.
Prerequisites
- Complete the Before setting up the CoE Starter Kit and Set up inventory components articles.
- Set up your environment.
- Sign in with the correct identity.
Tip
Set up the audit log flows only if you chose cloud flows as the mechanism for inventory and telemetry.
Before you set up the audit log flows
- Microsoft 365 audit log search must be turned on for the audit log connector to work. Learn more in Turn auditing on or off.
- Your tenant must have a subscription that supports unified audit logging. Learn more in Microsoft 365 guidance for security & compliance.
- Microsoft Entra permissions might be required to configure the Microsoft Entra app registration. Depending on your Microsoft Entra configuration, these permissions could be an Application Developer role or higher. You can find more guidance in Least privileged roles by task in Microsoft Entra ID.
Note
To grant rights for your application to access the Office 365 Management APIs, you can use authentication services that the APIs provide through Microsoft Entra ID.
Create a Microsoft Entra app registration for Office 365 Management API access
Follow these steps to set up a Microsoft Entra app registration for an HTTP call in a Power Automate flow to connect to the audit log. Learn more in Get started with Office 365 Management APIs.
Sign in to the Azure portal.
Go to Microsoft Entra ID > App registrations.
Select + New Registration.
Enter a name, such as Microsoft 365 Management, but don't change any other setting. Then select Register.
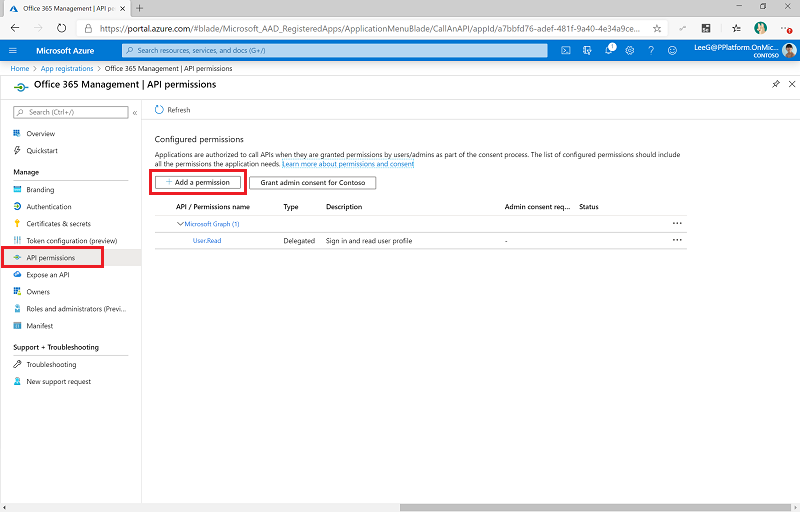
Select API Permissions > + Add a permission.
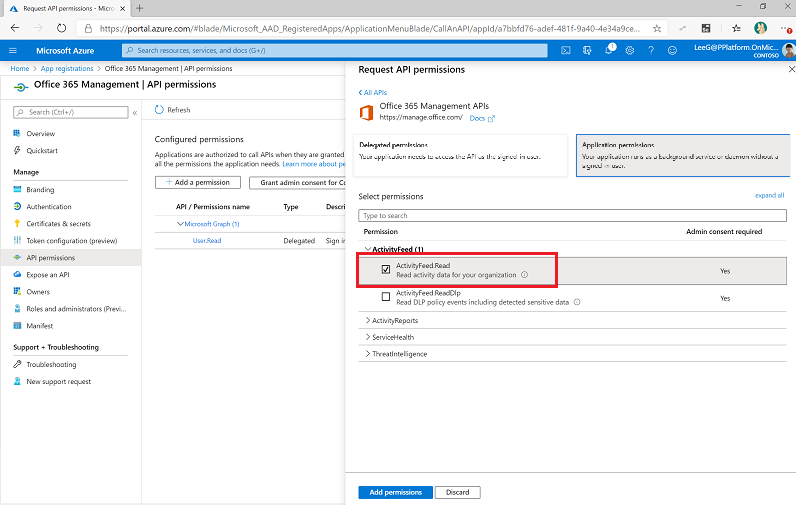
Select Office 365 Management API, and configure permissions as follows:
Select Grant Admin Consent for <your organization>. Learn more about how to set up admin content in Prerequisites.
The API permissions now reflect delegated ActivityFeed.Read permissions with a status of Granted for <your organization>.
Select Certificates and secrets.
Select + New client secret.
Add a description and expiration in line with your organization's policies. Then select Add.
Copy and paste the application (client) ID to a text document such as a Notepad file.
Select Overview, and copy and paste the application (client) ID and directory (tenant) ID values to the same text document. Be sure to make a note of which globally unique identifier (GUID) is for which value. You need these values when you configure the custom connector.
Update environment variables
Environment variables are used to control whether the legacy Office 365 Management API or the Graph API is used. They are also used to store the client ID and secret for the app registration. In addition, depending on the type of cloud that you use for the HTTP action, they are used to define audience and authority service endpoints. Your cloud type might be commercial, US Government Community Cloud (GCC), US GCC High, or US Department of Defense (DoD). Update the environment variables before you turn on the flows.
You can store the client secret in plain text in the Audit Logs - Client Secret environment variable. However, we don't recommend this approach. Instead, we recommend that you create and store the client secret in Azure Key Vault and reference it in the Audit Logs - Client Azure Secret environment variable.
Note
The flow that uses this environment variable is configured with a condition to expect either the Audit Logs - Client Secret or Audit Logs - Client Azure Secret environment variable. However, you don't need to edit the flow to work with Azure Key Vault.
| Name | Description | Value |
|---|---|---|
| Audit Logs - Use Graph API | A parameter that controls whether Graph API should be used to query events. | No (default) Sync flow uses the legacy Office 365 Management API. |
| Audit Logs - Audience | The audience parameter for the HTTP calls. |
|
| Audit Logs - Authority | The authority field in the HTTP calls. |
|
| Audit Logs - ClientID | The app registration client ID. | The application client ID from the Create a Microsoft Entra app registration for Office 365 Management API access step. |
| Audit Logs - Client Secret | The app registration client secret (not the secret ID, but the actual value) in plain text. | The application client secret from the Create a Microsoft Entra app registration for the Office 365 Management API access step. If you're using Azure Key Vault to store your client ID and secret, leave this variable empty. |
| Audit Logs - Client Azure Secret | The Azure Key Vault reference of the app registration client secret. | The Azure Key Vault reference for the application client secret from the Create a Microsoft Entra app registration for the Office 365 Management API access step. If you're storing your client ID in plain text in the Audit Logs - Client Secret environment variable, leave this variable empty. This variable expects the Azure Key Vault reference, not the secret. Learn more in Use environment variables for Azure Key Vault secrets. |
Start a subscription to audit log content
Go to make.powerapps.com.
Select Solutions.
Open the Center of Excellence – Core Components solution.
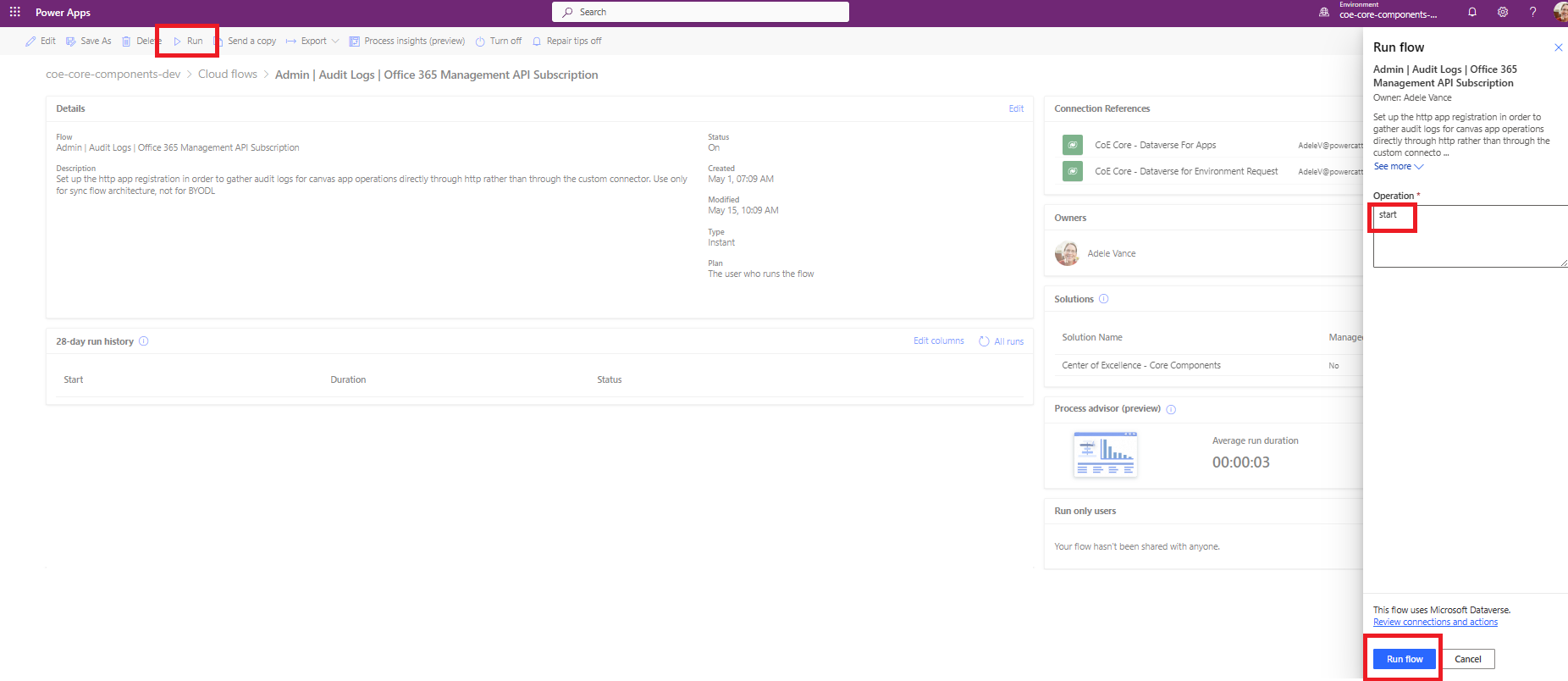
Turn on the Admin | Audit Logs | Office 365 Management API Subscription flow and run it, enter start as the operation to run.
Open the flow, and verify that the action to start the subscription is passed.
Important
If you previously enabled the subscription, you see a (400) The subscription is already enabled message. This means the subscription successfully enabled in the past. You can ignore this message and continue with the setup.
If you don't see the above message or a (200) response, the request likely failed. There might be an error with your setup that's keeping the flow from working. Common issues to check are:
- Are audit logs enabled, and do you have permission to view the audit logs? Test if the logs are enabled by searching in Microsoft Compliance Manager.
- Did you enable the audit log recently? If so, try again in a few minutes, to give the audit log time to activate.
- Validate that you correctly followed the steps in Microsoft Entra app registration.
- Validate that you correctly updated the environment variables for these flows.
Turn on flows
- Go to make.powerapps.com.
- Select Solutions.
- Open the Center of Excellence – Core Components solution.
- Turn on the Admin | Audit Logs | Update Data (V2) flow. This flow updates the Power Apps table with information about the last launch. It also adds metadata to the audit log records.
- Turn on the Admin | Audit Logs | Sync Audit Logs (V2) flow. This flow runs on an hourly schedule and collects audit log events into the audit log table.
Provide feedback
If you find a bug with the CoE Starter Kit, file a bug against the solution at aka.ms/coe-starter-kit-issues.