Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to: ![]() IoT Edge 1.1
IoT Edge 1.1
Important
IoT Edge 1.1 end of support date was December 13, 2022. Check the Microsoft Product Lifecycle for information about how this product, service, technology, or API is supported. For more information about updating to the latest version of IoT Edge, see Update IoT Edge.
As the IoT Edge service releases new versions, you'll want to update your IoT Edge devices for the latest features and security improvements. This article provides information about how to update your IoT Edge devices when a new version is available.
Two logical components of an IoT Edge device need to be updated if you want to move to a newer version. The first is the security subsystem. Although the architecture of the security subsystem changed between version 1.1 and 1.2, its overall responsibilities remained the same. It runs on the device, handles security-based tasks, and starts the modules when the device starts. Currently, the security subsystem can only be updated from the device itself. The second component is the runtime, made up of the IoT Edge hub and IoT Edge agent modules. Depending on how you structure your deployment, the runtime can be updated from the device or remotely.
You should update the IoT Edge runtime and application layers use the same release version. While mismatched versions are supported, they aren't tested together. Use the following sections in this article to update both the runtime and application layers on a device:
- Update the security subsystem
- Update the runtime containers
- Verify versions match
- On your device, use
iotedge versionto check the security subsystem version. The output includes the major, minor, and revision version numbers. For example, iotedge 1.4.2. - In your device deployment runtime settings, verify edgehub and edgeagent image URI versions match the major and minor version of the security subsystem. If the security subsystem version is 1.4.2, the image versions would be 1.4. For example, mcr.microsoft.com/azureiotedge-hub:1.4 and mcr.microsoft.com/azureiotedge-agent:1.4.
- On your device, use
To find the latest version of Azure IoT Edge, see Azure IoT Edge releases.
Update the security subsystem
The IoT Edge security subsystem includes a set of native components that need to be updated using the package manager on the IoT Edge device.
Check the version of the security subsystem running on your device by using the command iotedge version. If you're using IoT Edge for Linux on Windows, you need to SSH into the Linux virtual machine to check the version.
Important
If you are updating a device from version 1.0 or 1.1 to the latest release, there are differences in the installation and configuration processes that require extra steps. For more information, refer to the steps later in this article: Special case: Update from 1.0 or 1.1 to latest release.
On Linux x64 devices, use apt-get or your appropriate package manager to update the runtime module to the latest version.
Update apt.
sudo apt-get update
Note
For instructions to get the latest repository configuration from Microsoft see the preliminary steps to Install IoT Edge.
Check to see which versions of IoT Edge are available.
apt list -a iotedge
If you want to update to the most recent version of the runtime module, use the following command, which also updates libiothsm-std to the latest version:
sudo apt-get install iotedge
If you want to update to a specific version of the runtime module, specify the version from the apt list output. Whenever iotedge is updated, it automatically tries to update the libiothsm-std package to its latest version, which may cause a dependency conflict. If you aren't going to the most recent version, be sure to target both packages for the same version. For example, the following command installs a specific version of the 1.1 release:
sudo apt-get install iotedge=1.1.1 libiothsm-std=1.1.1
If the version that you want to install isn't available through apt-get, you can use curl to target any version from the IoT Edge releases repository. For whichever version you want to install, locate the appropriate libiothsm-std and iotedge files for your device. For each file, right-click the file link and copy the link address. Use the link address to install the specific versions of those components:
curl -L <libiothsm-std link> -o libiothsm-std.deb && sudo apt-get install ./libiothsm-std.deb
curl -L <iotedge link> -o iotedge.deb && sudo apt-get install ./iotedge.deb
Then, reapply configuration to ensure system is fully updated.
sudo iotedge config apply
Update the runtime containers
The way that you update the IoT Edge agent and IoT Edge hub containers depends on whether you use rolling tags (like 1.1) or specific tags (like 1.1.1) in your deployment.
Check the version of the IoT Edge agent and IoT Edge hub modules currently on your device using the commands iotedge logs edgeAgent or iotedge logs edgeHub. If you're using IoT Edge for Linux on Windows, you need to SSH into the Linux virtual machine to check the runtime module versions.
Understand IoT Edge tags
The IoT Edge agent and IoT Edge hub images are tagged with the IoT Edge version that they're associated with. There are two different ways to use tags with the runtime images:
Rolling tags - Use only the first two values of the version number to get the latest image that matches those digits. For example, 1.1 is updated whenever there's a new release to point to the latest 1.1.x version. If the container runtime on your IoT Edge device pulls the image again, the runtime modules are updated to the latest version. Deployments from the Azure portal default to rolling tags. This approach is suggested for development purposes.
Specific tags - Use all three values of the version number to explicitly set the image version. For example, 1.1.0 won't change after its initial release. You can declare a new version number in the deployment manifest when you're ready to update. This approach is suggested for production purposes.
Update a rolling tag image
If you use rolling tags in your deployment (for example, mcr.microsoft.com/azureiotedge-hub:1.1) then you need to force the container runtime on your device to pull the latest version of the image.
Delete the local version of the image from your IoT Edge device. On Windows machines, uninstalling the security subsystem also removes the runtime images, so you don't need to take this step again.
docker rmi mcr.microsoft.com/azureiotedge-hub:1.1
docker rmi mcr.microsoft.com/azureiotedge-agent:1.1
You may need to use the force -f flag to remove the images.
The IoT Edge service will pull the latest versions of the runtime images and automatically start them on your device again.
Update a specific tag image
If you use specific tags in your deployment (for example, mcr.microsoft.com/azureiotedge-hub:1.1.1) then all you need to do is update the tag in your deployment manifest and apply the changes to your device.
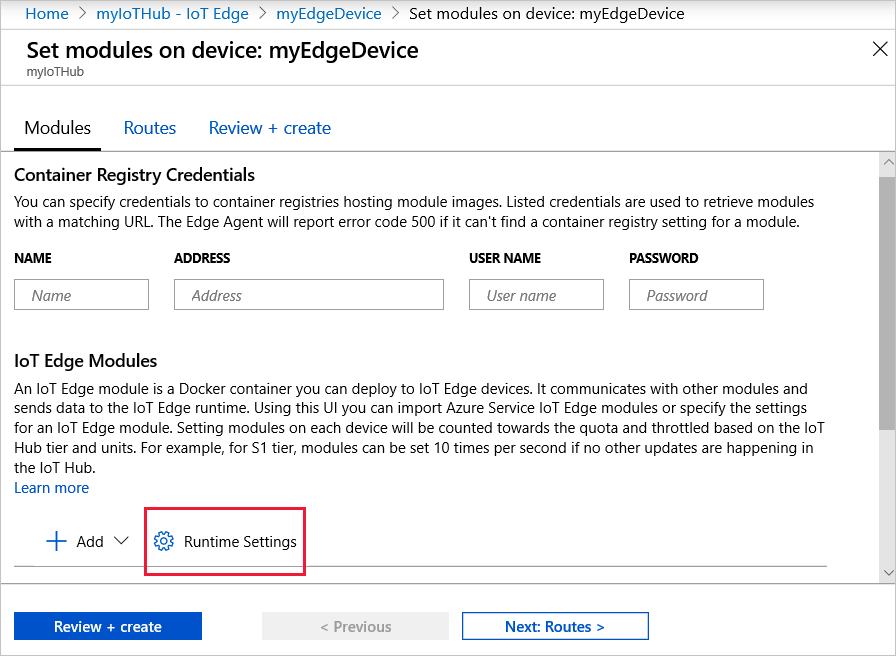
In the IoT Hub in the Azure portal, select your IoT Edge device, and select Set Modules.
In the IoT Edge Modules section, select Runtime Settings.
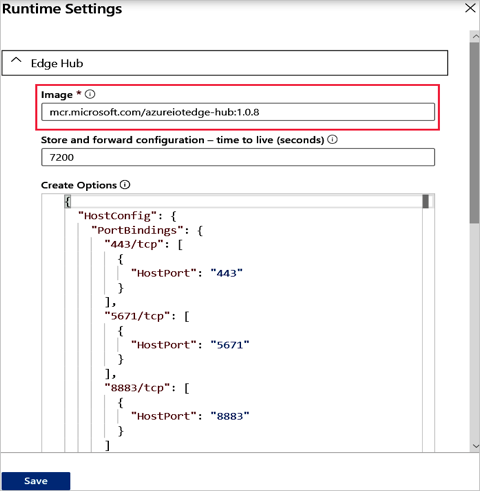
In Runtime Settings, update the Image value for Edge Hub with the desired version. Don't select Save yet.
Collapse the Edge Hub settings, or scroll down, and update the Image value for Edge Agent with the same desired version.
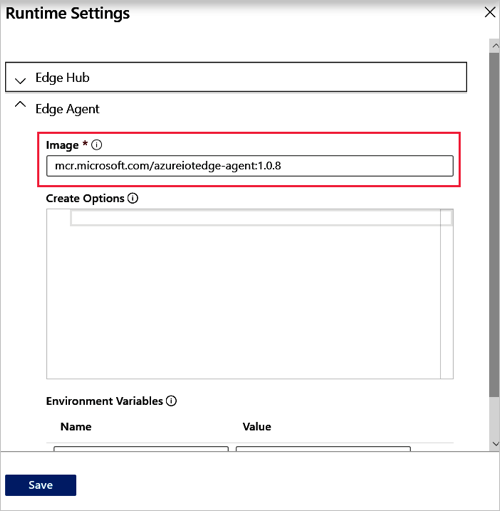
Select Save.
Select Review + create, review the deployment, and select Create.
Special case: Update from 1.0 or 1.1 to latest release
Starting with version 1.2, the IoT Edge service uses a new package name and has some differences in the installation and configuration processes. If you have an IoT Edge device running version 1.0 or 1.1, use these instructions to learn how to update to the latest release.
Some of the key differences between the latest release and version 1.1 and earlier include:
- The package name changed from iotedge to aziot-edge.
- The libiothsm-std package is no longer used. If you used the standard package provided as part of the IoT Edge release, then your configurations can be transferred to the new version. If you used a different implementation of libiothsm-std, then any user-provided certificates like the device identity certificate, device CA, and trust bundle will need to be reconfigured.
- A new identity service, aziot-identity-service was introduced as part of the 1.2 release. This service handles the identity provisioning and management for IoT Edge and for other device components that need to communicate with IoT Hub, like Device Update for IoT Hub.
- The default config file has a new name and location. Formerly
/etc/iotedge/config.yaml, your device configuration information is now expected to be in/etc/aziot/config.tomlby default. Theiotedge config importcommand can be used to help migrate configuration information from the old location and syntax to the new one.- The import command can't detect or modify access rules to a device's trusted platform module (TPM). If your device uses TPM attestation, you need to manually update the /etc/udev/rules.d/tpmaccess.rules file to give access to the aziottpm service. For more information, see Give IoT Edge access to the TPM.
- The workload API in the latest version saves encrypted secrets in a new format. If you upgrade from an older version to latest version, the existing master encryption key is imported. The workload API can read secrets saved in the prior format using the imported encryption key. However, the workload API can't write encrypted secrets in the old format. Once a secret is re-encrypted by a module, it's saved in the new format. Secrets encrypted in the latest version are unreadable by the same module in version 1.1. If you persist encrypted data to a host-mounted folder or volume, always create a backup copy of the data before upgrading to retain the ability to downgrade if necessary.
- For backward compatibility when connecting devices that don't support TLS 1.2, you can configure Edge Hub to still accept TLS 1.0 or 1.1 via the SslProtocols environment variable. Please note that support for TLS 1.0 and 1.1 in IoT Hub is considered legacy and may also be removed from Edge Hub in future releases. To avoid future issues, use TLS 1.2 as the only TLS version when connecting to Edge Hub or IoT Hub.
- The preview for the experimental MQTT broker in Edge Hub 1.2 has ended and isn't included in Edge Hub 1.3 or later. We're continuing to refine our plans for an MQTT broker based on feedback received. In the meantime, if you need a standards-compliant MQTT broker on IoT Edge, consider deploying an open-source broker like Mosquitto as an IoT Edge module.
- Starting with version 1.2, when a backing image is removed from a container, the container keeps running and it persists across restarts. In 1.1, when a backing image is removed, the container is immediately recreated and the backing image is updated.
Before automating any update processes, validate that it works on test machines.
When you're ready, follow these steps to update IoT Edge on your devices:
Update apt.
sudo apt-get updateUninstall the previous version of IoT Edge, leaving your configuration files in place.
sudo apt-get remove iotedgeInstall the most recent version of IoT Edge, along with the IoT identity service and the Microsoft Defender for IoT micro agent for Edge.
sudo apt-get install aziot-edge defender-iot-micro-agent-edge
It's recommended to install the micro agent with the Edge agent to enable security monitoring and hardening of your Edge devices. To learn more about Microsoft Defender for IoT, see What is Microsoft Defender for IoT for device builders.
Import your old config.yaml file into its new format, and apply the configuration info.
sudo iotedge config import
Now that the IoT Edge service running on your devices has been updated, follow the steps in this article to also Update the runtime containers.
Next steps
View the latest Azure IoT Edge releases.
Stay up-to-date with recent updates and announcements in the Internet of Things blog