Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
To help familiarize you with Endpoint DLP features and how they surface in DLP policies, we've put together some scenarios for you to follow.
Important
These Endpoint DLP scenarios are not the official procedures for creating and tuning DLP policies. Refer to the below topics when you need to work with DLP policies in general situations:
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Before you begin
SKU/subscriptions licensing
For information on licensing, see
These scenarios require that you already have devices onboarded and reporting into Activity explorer. If you haven't onboarded devices yet, see Get started with Endpoint data loss prevention.
Important
Be sure you understand the difference between an unrestricted administrator and an administrative unit restricted administrator Administrative units before you start.
Scenario 1: Create a policy from a template, audit only
This scenario is for an unrestricted admin creating and full directory policy.
Sign in to the Microsoft Purview portal. > Data loss prevention > Policies.
Choose + Create policy.
Select Data stored in connected sources.
For this scenario, under Categories, choose Privacy.
Under Regulations choose U.S. Personally Identifiable Information (PII) Data Enhanced, and then choose Next.
Give your new policy a Name and Description, and then choose Next.
Accept the default Full directory under Admin units. Select Next.
Select the Devices location and deselect all other locations and then choose Next.
On the Define policy settings page, choose Next.
On the Info to protect page, choose Next.
On the Protection actions page, choose Next again.
On the Customize access and override settings page, choose Audit or restrict activities on Devices and then choose Next.
On the Policy mode page, accept the default Run the policy in simulation mode and select Show policy tips while in simulation mode.
Choose Next.
Choose Submit.
Once the new policy is created, choose Done.
Now it’s time to test your policy:
On the Data Loss Prevention home page, open Activity explorer.
Try to share a test item from your Endpoint DLP device that contains content that will trigger the U.S. Personally Identifiable Information (PII) Data condition. This should trigger the policy.
Back in Activity explorer, check the list of activities for this event.
Scenario 2: Modify the existing policy, set an alert
This scenario is for an unrestricted admin modifying a full directory scoped policy.
Sign in to the Microsoft Purview portal > Data loss prevention > Policies.
Choose the U.S. Personally Identifiable Information (PII) Data Enhanced policy that you created in Scenario 1.
Choose Edit policy.
Go to the Customize advanced DLP rules page and edit the Low volume of content detected scenarios U.S. PII Data Enhanced.
Scroll down to the Incident reports section and toggle Send an alert to admins when a rule match occurs to On. Email alerts are automatically sent to the administrator and anyone else you add to the list of recipients.
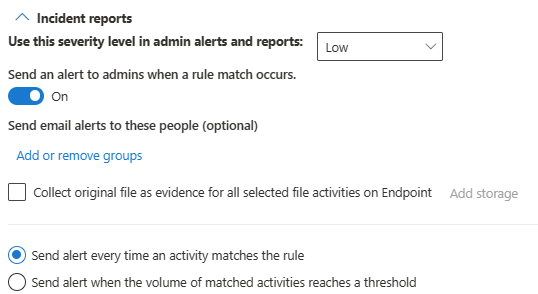
For the purposes of this scenario, choose Send alert every time an activity matches the rule.
Choose Save.
Retain all your previous settings by choosing Next throughout the rest of the wizard, then Submit the policy changes.
Try to share a test item containing content that will trigger the U.S. Personally Identifiable Information (PII) Data condition. This should trigger the policy.
Check the activity explorer for the event.
Scenario 3: Modify the existing policy, block the action with allow override
This scenario is for an unrestricted admin modifying a full directory policy.
Sign in to the Microsoft Purview portal > Data loss prevention > Policies.
Choose the U.S. Personally Identifiable Information (PII) Data policy that you created in Scenario 1.
Choose Edit policy.
Go to the Customize advanced DLP rules page and edit the Low volume of content detected scenarios U.S. PII Data Enhanced.
Scroll down to the Actions > Audit or restrict activities on Windows device section and set both options under the Service domain and browser activities to Block with override.
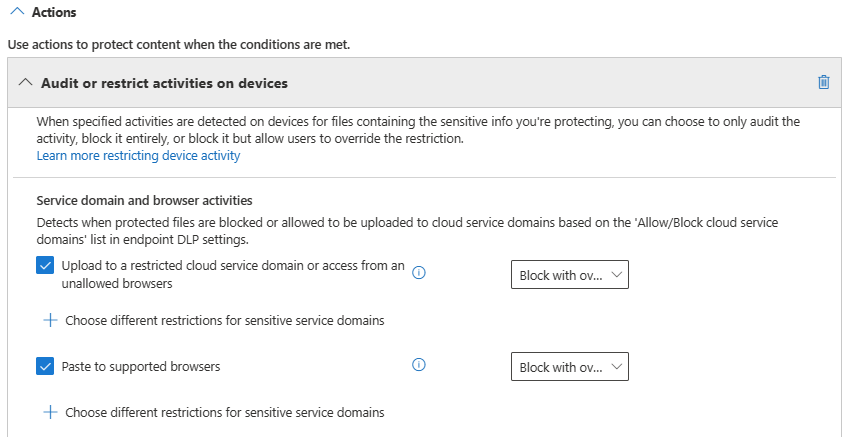
Choose Save.
Repeat steps 4-6 for the High volume of content detected scenarios U.S. PII Data Enhanced.
Retain all your previous settings by choosing Next through the rest of the wizard,and then Submit the policy changes.
Attempt to share a test item that contains content that will trigger the U.S. Personally Identifiable Information (PII) Data condition with someone outside your organization. This should trigger the policy.
You see a popup like this on the client device:
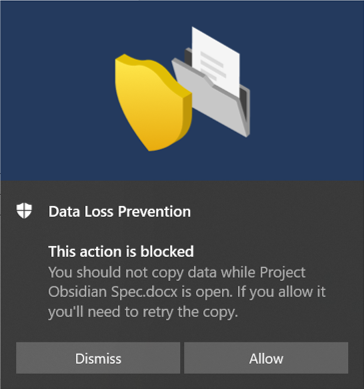
Check the activity explorer for the event.
Scenario 4: Avoid looping DLP notifications from cloud synchronization apps with autoquarantine
This scenario is for an unrestricted admin creating a full directory policy.
Before you begin Scenario 4
In this scenario, synchronizing files with the Highly Confidential sensitivity label to OneDrive is blocked. This is a complex scenario with multiple components and procedures. You need:
- A Microsoft Entra user account to target and an onboarded Windows 10/11 or macOS computer that is already synchronizing a local OneDrive folder with OneDrive cloud storage.
- Sensitivity labels configured and published—see Get started with sensitivity labels and Create and configure sensitivity labels and their policies.
There are three procedures.
- Configure the Endpoint DLP Autoquarantine settings.
- Create a policy that blocks sensitive items that have the Highly Confidential sensitivity label.
- Create a Word document on the Windows 10/11 or macOS device that the policy is targeted to, apply the label, and copy it to the user accounts local OneDrive folder that is being synchronized.
Configure Endpoint DLP unallowed app and Autoquarantine settings
Sign in to the Microsoft Purview portal > Data loss prevention > Settings (gear in the upper left hand corner) > Data loss prevention > Endpoint settings.
Expand Restricted apps and app groups.
Under Restricted app groups, choose Add restricted app group. Enter Cloud Sync apps as the group name.
Select the Auto-quarantine box.
For the App name, enter OneDrive. For the Windows Executable name, enter onedrive.exe, then choose the + button. For the macOS Executable name, enter /Applications/OneDrive.app/Contents/MacOS/OneDrive, then choose the + button. This disallows onedrive application on devices from accessing items with the Highly Confidential label.
Note
To restrict other common cloud sync app on macOS devices, add the below path
- Box:
/Applications/Box Sync.app/Contents/MacOS/Box Sync - Dropbox:
/Applications/Dropbox.app/Contents/MacOS/Dropbox - Google Drive:
/Applications/Google Drive.app/Contents/MacOS/Google Drive - iCloud:
System/Library/PrivateFrameworks/CloudDocsDaemon.framework/Versions/A/Support/bird
- Box:
Choose Save.
Under Auto-quarantine settings choose Edit auto-quarantine settings.
Enable Auto-quarantine for unallowed apps.
Enter the path to the folder on local machines where you want the original sensitive files to be moved to. For example:
%homedrive%%homepath%\Microsoft DLP\Quarantinefor the username Isaiah Langer will place the moved items in a folder named:C:\Users\IsaiahLanger\Microsoft DLP\Quarantine\OneDrive
A separate path for the macOS device is required, such as
/System/Applications/Microsoft DLP/Quarantine
Append a date and time stamp to the original file name.
Note
DLP auto-quarantine will create sub-folders for the files for each unallowed app. So if you have both Notepad and OneDrive in your unallowed apps list, a sub-folder will be created for \OneDrive and another sub-folder for \Notepad.
Choose Replace the files with a .txt file that contains the following text and enter the text you want in the placeholder file. For example for a file named auto quar 1.docx, you could enter:
%%FileName%% contains sensitive info that your organization is protecting with the data loss prevention (DLP) policy %%PolicyName%%. It was moved to the quarantine folder: %%QuarantinePath%%
will leave a text file that contains this message:
auto quar 1.docx contains sensitive info that your organization is protecting with the data loss prevention (DLP) policy. It was moved to the quarantine folder: C:\Users\IsaiahLanger\Microsoft DLP\Quarantine\OneDrive\auto quar 1.docx.
Choose Save.
Configure a policy to block OneDrive synchronization of files with the sensitivity label "Highly Confidential"
Sign in to the Microsoft Purview portal > Data loss prevention > Policies.
Select Create policy.
Data stored in connected sources.
For this scenario, choose Custom, then Custom policy. Choose Next.
Fill in the Name and Description fields, choose Next.
Select Full directory under Admin units.
Toggle the Status field to off for all locations except Devices. If you have a specific end user account that you want to test this from, be sure to select it in the scope. Choose Next.
Accept the default Create or customize advanced DLP rules selection and choose Next.
Create a rule with these values:
- Name > Scenario 4 Autoquarantine.
- Under Conditions choose Add condition and then Content Contains.
- Enter a group name, for example Highly Confidential Sensitivity Labels and then choose Add.
- Select Sensitivity labels then Highly Confidential and choose Add.
- Under Actions choose Add an action.
- Select Audit or restrict activities on devices > File activities for apps in restricted app groups.
- Choose Add restricted app group then choose the Cloud Sync Apps group you created previously.
- Choose Apply a restriction to all activity > Block. For the purposes of this scenario, clear all the other activities.
- Under User notifications, toggle User notifications to On and under Endpoint devices choose Show users a policy tip notification when an activity if not already enabled.
Choose Save and Next.
Choose Turn it on right away. Choose Next.
Review your settings and choose Submit.
Note
Allow at least an hour for the new policy to be replicated and applied to the target Windows 10 computer.
The new DLP policy appears in the policy list.
Test Autoquarantine on the Windows 10/11 device
Sign in to the Windows 10/11 computer with the user account you specified in Configure a policy to block OneDrive synchronization of files with the sensitivity label Highly Confidential, step 5.
Create a folder whose contents won't be synchronized to OneDrive. For example:
C:\auto-quarantine source folder
Open Microsoft Word and create a file in the autoquarantine source folder. Apply the Highly confidential sensitivity label; see Apply sensitivity labels to your files and email in Office.
Copy the file you created to your OneDrive synchronization folder. A user notification toast should appear telling you that the action isn't allowed and that the file will be quarantined. For example, for user name Isaiah Langer, and a document titled autoquarantine doc 1.docx you would see this message:
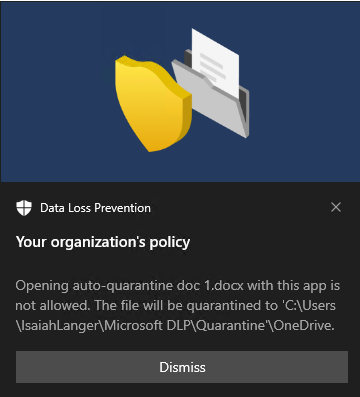
The message reads:
Opening auto-quarantine doc 1.docx with this app is not allowed. The file will be quarantined to C:\Users\IsaiahLanger\Microsoft DLP\OneDrive
Choose Dismiss.
Open the place holder text file. It is named auto-quarantine doc 1.docx_date_time.txt.
Open the quarantine folder and confirm that the original file is there.
Check Activity explorer for data from the monitored endpoints. Set the location filter for devices and add the policy, then filter by policy name to see the effect of this policy. For information on using activity explorer, see Get started with activity explorer.
Check Activity explorer for the event.
Scenario 5: Restrict unintentional sharing to unallowed cloud apps and services
This scenario is for an unrestricted admin creating a full directory policy.
With Endpoint DLP and a supported web browser, you can restrict unintentional sharing of sensitive items to unallowed cloud apps and services. Microsoft Edge understands when an item is restricted by an Endpoint DLP policy and enforces access restrictions.
Note
The following web browsers are supported:
- Microsoft Edge (Win/macOS)
- Chrome (Win/macOS)- Microsoft Purview extension for Chrome Windows only
- Firefox (Win/macOS)- Microsoft Purview extension for Firefox Windows only
- Safari (macOS only)
When you select Devices as a location in a properly configured DLP policy and use a supported web browser, the unallowed browsers that you've defined in these settings will be prevented from accessing the sensitive items that match your DLP policy controls. Instead, users are redirected to use Microsoft Edge, which, with its understanding of DLP imposed restrictions, can block or restrict activities when the conditions in the DLP policy are met.
To use this restriction, you need to configure three important pieces:
Specify the places – services, domains, IP addresses – that you want to prevent sensitive items from being shared to.
Add the browsers that aren’t allowed to access certain sensitive items when a DLP policy match occurs.
Configure DLP policies to define the kinds of sensitive items for which upload should be restricted to these places by turning on Upload to cloud services and Access from unallowed browser.
You can continue to add new services, apps, and policies to extend and augment your restrictions to meet your business needs and protect sensitive data.
This configuration helps ensure your data remains safe while also avoiding unnecessary restrictions that prevent or restrict users from accessing and sharing nonsensitive items.
You can also audit, block with override, or block these user-upload sensitive items to cloud apps and services through Sensitive service domains.
Sign in to the Microsoft Purview portal > Data loss prevention > Settings (gear icon in the upper left hand corner) > Data Loss Prevention > Endpoint DLP settings > Browser and domain restrictions to sensitive data > Sensitive service domain groups.
Select Create sensitive service domain group.
Name the group.
Enter the Sensitive service domain for the group. You can add multiple websites to a group and use wildcards to cover subdomains. For example,
www.contoso.comfor just the top level website, or: *.contoso.com for corp.contoso.com, hr.contoso.com, fin.contoso.com.Select the Match type you want. You can select from URL, IP address, IP address range.
Select Save.
In the left navigation pane, select Data loss prevention > Policies.
Data stored in connected sources.
Create and scope a policy that is applied only to the Devices location. For more information on how to create a policy, see Create and Deploy data loss prevention policies. Be sure to scope the Admin units to Full directory.
On the Define policy settings page, select Create or customize advanced DLP rules and choose Next.
Create a rule, as follows:
- Under Conditions, select + Add condition and select Content contains from the drop-down menu.
- Give the group a name.
- Choose Add and then select Sensitive info types.
- Select a Sensitive info type from the flyout pane, then choose Add.
- Add the action Audit or restrict activities on devices.
- Under Service domain and browser activities, choose Upload to a restricted cloud service domain or access from an unallowed browser and set the action to Audit only.
- Select + Choose different restrictions for sensitive service domains and then choose Add group.
- On the Choose sensitive service domain groups flyout, select the sensitive service domain group(s) you want, choose Add and then choose Save.
- Under File activities for all apps, select the user activities you want to monitor or restrict and the actions for DLP to take in response to those activities.
- Finish creating the rule and choose Save and then Next.
- On the confirmation page, choose Done.
- On the Policy mode page, choose Turn it on right away. Choose Next and then Submit.
Scenario 6: Monitor or restrict user activities on sensitive service domains
This scenario is for an unrestricted admin creating a full directory policy.
Use this scenario when you want to audit or block the following user activities on a website.
- print from a website
- copy data from a website
- save a website as local files
Note
The following web browsers are supported:
- Microsoft Edge (Win/macOS)
- Chrome (Win/macOS)- Microsoft Purview extension for Chrome Windows only
- Firefox (Win/macOS)- Microsoft Purview extension for Firefox Windows only
- Safari (macOS only)
Configure Sensitive service domains
Sign in to the Microsoft Purview portal > Data loss prevention > Settings (gear icon in the upper left hand corner) > Data Loss Prevention > Endpoint settings > Browser and domain restrictions to sensitive data > Service domains.
Set Service domains to Block.
To control whether sensitive files can be uploaded to specific domains, select Add cloud service domain.
Enter the domain that you want to audit or block and choose the + button. Repeat for any additional domains. Choose Save.
Under Sensitive service domain groups, choose Create sensitive service domain group.
Give the group a name, select the Match type you want (you can select from URL, IP address, IP address range), and enter the URL, IP address, or IP address range to be audited or blocked. When matching a URL, you can add multiple websites to a group and use wildcards to cover subdomains. For example,
www.contoso.comfor just the top level website or *.contoso.com for corp.contoso.com, hr.contoso.com, fin.contoso.com.Select Save.
In the left navigation pane, select Data loss prevention > Policies.
Data stored in connected sources.
Create and scope a policy that is applied only to the Devices location. See, Create and Deploy data loss prevention policies for more information on how to create a policy. Be sure to scope the Admin units to Full directory.
Create a rule that uses the condition the user accessed a sensitive site from Edge, and the action Audit or restrict activities when users access sensitive sites in Microsoft Edge browser on Windows devices.
In the action, under Sensitive Site Restrictions, select Add or remove Sensitive site groups.
Create and/or select the Sensitive site groups you want. Any website under the group(s) you select here will be redirected to Microsoft Edge when opened in Chrome or Firefox (so long as the Microsoft Purview extension is installed).
Select Add.
Select the user activities you want to monitor or restrict and the actions you want Microsoft Purview to take in response to those activities.
Finish configuring the rule and policy and choose Submit and then Done.
Scenario 7: Restrict pasting sensitive content into a browser
Use this scenario to restrict users from pasting sensitive content into a browser web form or field in a browser. Evaluation is performed on the content that is being pasted when it is pasted. The evaluation that happens at pasting is independent of how the source item that the content came from is classified. The Paste to browser setting works with Sensitive Service Domain Groups if the rule is configured to use Sensitive Service Domain Groups. The Paste to browser activity doesn't work with the Service domains endpoint DLP setting. For more information, see Endpoint activities you can monitor and take action on
Note
The following web browsers are supported:
- Microsoft Edge (Win/macOS)
- Chrome (Win/macOS)- Microsoft Purview extension for Chrome Windows only
- Firefox (Win/macOS)- Microsoft Purview extension for Firefox Windows only
- Safari (macOS only)
Important
- If you have configured evidence collection for file activities on devices and your Antimalware Client Version on the device is older than 4.18.23110, when you implement this scenario, Restrict pasting sensitive content into a browser, you will see random characters when you attempt to view the source file in Alert details. To see the actual source file text, you should download the file.
- If Document could not be scanned is selected as the action for the matched rule, the evidence file will not be captured.
Create your DLP policy
You can set up different levels of enforcement when it comes to blocking data from being pasted into a browser. To do this, create different URL groups. For instance, you can create a policy that warns users against posting U.S. Social Security Numbers (SSN) to any website, and that triggers an audit action for websites in Group A. You can create another policy that completely blocks the paste action--without giving a warning--for all of the websites in Group B.
Create a URL group
Sign in to the Microsoft Purview portal > Data loss prevention > Settings (gear icon in the upper left hand corner) > Data Loss Prevention > Endpoint settings, and scroll down to Browser and domain restrictions to sensitive data. Expand the section.
Scroll down to Sensitive service domain groups.
Choose Create sensitive service domain group.
- Enter a Group name.
- In the Sensitive service domain field, enter the URL for the first website you want to monitor and then choose Add site.
- Continue adding URLs for the rest of the websites you want to monitor in this group.
- When you are finished adding all URLs to your group, choose Save.
Create as many separate groups of URLs as you need.
Restrict pasting content into a browser
Sign in to the Microsoft Purview portal > Data loss prevention > Policies.
Data stored in connected sources.
Create a DLP policy scoped to Devices. For information on how to create a DLP policy, see Create and Deploy data loss prevention policies.
On the Define policy settings page in the DLP policy creation flow, select Create or customize advanced DLP rules and then choose Next.
On the Customize advanced DLP rules page, choose Create rule.
Enter a name and description for the rule.
Expand Conditions, choose Add condition, and then select the Sensitive info types.
Under Content Contains, scroll down and select the new sensitive information type that you previously chose or created.
Scroll down to the Actions section, and choose Add an action.
Choose Audit or restrict activities on devices
In the Actions section, under Service domain and browser activities, select Paste to supported browsers.
Set the restriction to Audit, Block with override, or Block, and then choose Add.
Choose Save.
Choose Next
Choose whether you want to test your policy, turn it on right away, or keep it off, and then choose Next.
Choose Submit.
Important
There may be a brief time lag between when the user attempts to paste text into a web page and when the system finishes classifying it and responds. If this classification latency happens, you may see both policy-evaluation and check-complete notifications in Edge or policy-evaluation toast on Chrome and Firefox. Here are some tips for minimizing the number of notifications:
- Notifications are triggered when policy for the target website is configured to Block or Block with override paste to browser for that user. You can configure setting the overall action to Audit and then list the target websites using the exceptions as Block. Alternately, you can set the overall action to Block and then list secure websites using the exceptions as Audit.
- Use latest Antimalware client version.
- Use latest Edge browser version, especially Edge 120.
- Install these Windows KBs
Scenario 8: Authorization groups
This scenario is for an unrestricted admin creating a full directory policy.
These scenarios require that you already have devices onboarded and reporting into Activity explorer. If you haven't onboarded devices yet, see Get started with Endpoint data loss prevention.
Authorization groups are mostly used as allowlists. You assigned policy actions to the group that are different than the global policy actions. In this scenario, we go through defining a printer group and then configuring a policy with block actions for all print activities except for the printers in the group. These procedures are essentially the same for Removeable storage device groups, and Network share groups.
In this scenario, we define a group of printers that the legal department uses for printing contracts. Printing contracts to any other printers is blocked.
Create and use printer groups
Sign in to the Microsoft Purview portal > Data loss prevention > Settings (gear in the upper left hand corner) > Data Loss Prevention > Endpoint settings > Printer groups.
Select Create printer group and enter a Group a name. In this scenario, we use
Legal printers.Select Add printer and provide a name. You can define printers by:
- Friendly printer name
- USB product ID
- USB vendor ID
- IP range
- Print to file
- Universal print deployed on a printer
- Corporate printer
- Print to local
Select Close.
Configure policy printing actions
Sign in to the Microsoft Purview portal.
Navigate to Data loss prevention > Policies.
Select Create policy.
Data stored in connected sources.
Select the Custom from the Categories then Custom policy template from Regulations.
Give your new policy a Name and Description.
Accept the default Full directory under Admin units.
Scope the location to only the Devices location.
Create a rule with the following values:
- Add a Condition: Content contains = Trainable classifiers, Legal Affairs
- Actions = Audit or restrict activities on devices
- Then pick File activities on all apps
- The select Apply restrictions to specific activity
- Select Print = Block
Select Choose different print restrictions
Under Printer group restrictions, select Add group and select Legal printers.
Set Action = Allow.
Tip
The Allow action wil record and audit event to the audit log, but not generate an alert or notification.
Select Save and then Next.
Accept the default Run the policy in simulation mode value and choose Show policy tips while in simulaiton mode. Choose Next.
Review your settings and choose Submit.
The new DLP policy appears in the policy list.
Scenario 9: Network exceptions
This scenario is for an unrestricted admin creating a full directory policy.
This scenarios require that you already have devices onboarded and reporting into Activity explorer. If you haven't onboarded devices yet, see Get started with Endpoint data loss prevention.
In this scenario, we define a list of VPNs that hybrid workers use for accessing organization resources.
Create and use a Network exception
Network exceptions enable you to configure Allow, Audit only, Block with override, and Block actions to the file activities based on the network that users are accessing the file from. You can select from the VPN settings list you've defined and use the Corporate network option. The actions can be applied individually or collectively to these user activities:
- Copy to clipboard
- Copy to a USB removable device
- Copy to a network share
- Copy or move using unallowed Bluetooth app
- Copy or move using RDP
Get the Server address or Network address
On a DLP monitored Windows device, open a Windows PowerShell window as an administrator.
Run this cmdlet:
Get-VpnConnectionRunning this cmdlet returns multiple fields and values.
Find the ServerAddress field and record that value. You use this when you create a VPN entry in the VPN list.
Find the Name field and record that value. The Name field maps to the Network address field when you create a VPN entry in the VPN list.
Determin if the device is connected through a Corporate network
On a DLP monitored Windows device, open a Windows PowerShell window as an administrator.
Run this cmdlet:
Get-NetConnectionProfileIf the NetworkCategory field is DomainAuthenticated, then the device is connected to a corporate network. If its anything else, the device's connection is not through a corporate network.
Add a VPN
Sign in to the Microsoft Purview portal.
Open Settings > Data Loss Prevention > Endpoint settings > VPN settings.
Select Add or edit VPN addresses.
Provide either the Server address or Network address from running Get-VpnConnection.
Select Save.
Close the item.
Configure policy actions
Sign in to the Microsoft Purview portal.
Open Data Loss Prevention > Policies.
Select Create policy
Data stored in connected sources.
Select the Custom from the Categories then Custom policy template from Regulations.
Name your new policy and provide a description.
Select Full directory under Admin units.
Scope the location to Devices only.
Create a rule where:
- Content contains = Trainable classifiers, Legal Affairs
- Actions = Audit or restrict activities on devices
- Then pick File activities on all apps
- The select Apply restrictions to specific activity
- Select the actions that you want to configure Network exceptions for.
Select Copy to clipboard and the Audit only action
Select Choose different copy to clipboard restrictions.
Select VPN and set the action to Block with override.
Important
When you want to control the activities of a user when they're connected through a VPN you must select the VPN and make the VPN the top priority in the Network exceptions configuration. Otherwise, if the Corporate network option is selected, then that action defined for the Corporate network entry will be enforced.
Caution
The Apply to all activities option will copy the network exceptions that are defined here and apply them to all the other configured specific activities, like Print, and Copy to a network share. This will overwrite the network exceptions on the other activities The last saved configuration wins.
Save.
Accept the default Run the policy in simulation mode value and choose Show policy tips while in simulation mode. Choose Next.
Review your settings and choose Submit and then Done.
The new DLP policy appears in the policy list.
See also
- Learn about Endpoint data loss prevention
- Get started with Endpoint data loss prevention
- Learn about data loss prevention
- Get started with Activity explorer
- Microsoft Defender for Endpoint
- Onboard Windows 10 and Windows 11 devices into Microsoft Purview overview
- Microsoft 365 subscription
- Microsoft Entra joined
- Download the new Microsoft Edge based on Chromium
- Create and Deploy data loss prevention policies