Create Function App and private endpoint-secured Storage
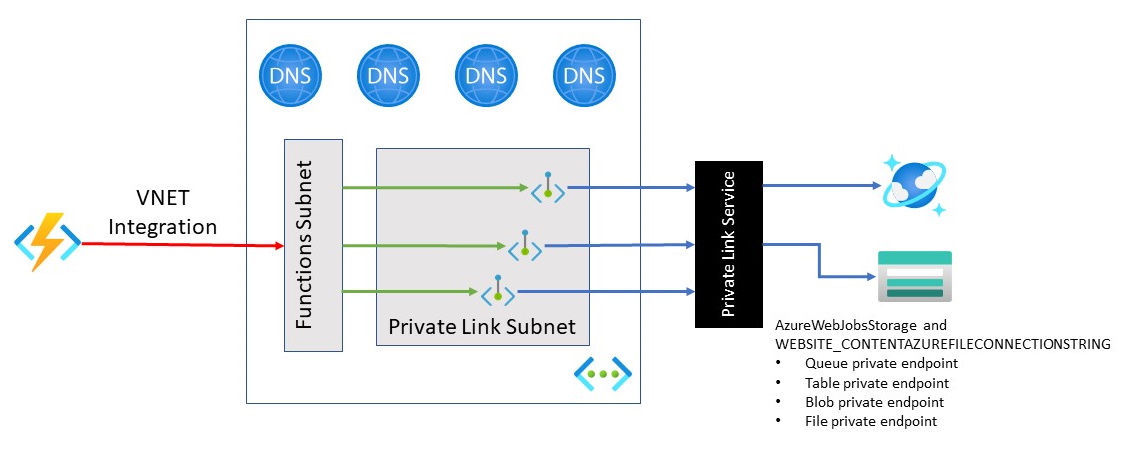
This sample Azure Resource Manager template deploys an Azure Function App that communicates with the Azure Storage account referenced by the AzureWebJobsStorage and WEBSITE_CONTENTAZUREFILECONNECTIONSTRING app settings, via private endpoints.
OS
This template has a parameter functionPlanOS to choose Windows or Linux OS. Windows is selected by default. If you choose Linux, then parameter linuxFxVersion will be parameter, so you can skip it for Windows.
Elastic Premium Plan
The Azure Function app provisioned in this sample uses an Azure Functions Elastic Premium plan.
- Microsoft.Web/serverfarms: The Azure Functions Premium plan (a.k.a. Elastic Premium plan)
Azure Function App
The Function App uses the AzureWebJobsStorage and WEBSITE_CONTENTAZUREFILECONNECTIONSTRING app settings to connect to a private endpoint-secured Storage Account.
- Microsoft.Web/sites: The function app instance.
Azure Storage account
The Storage account that the Function uses for operation and for file contents.
- Microsoft.Storage/storageAccounts: Azure Functions requires a storage account for the function app instance.
Virtual Network
Azure resources in this sample either integrate with or are placed within a virtual network. The use of private endpoints keeps network traffic contained with the virtual network.
The sample uses two subnets:
- Subnet for Azure Function virtual network integration. This subnet is delegated to the Function App.
- Subnet for private endpoints. Private IP addresses are allocated from this subnet.
Private Endpoints
Azure Private Endpoints are used to connect to specific Azure resources using a private IP address This ensures that network traffic remains within the designated virtual network, and access is available only for specific resources. This sample configures private endpoints for the following Azure resources:
- Azure Storage
- Azure File storage
- Azure Blob storage
- Azure Queue storage
- Azure Table storage
Private DNS Zones
Using a private endpoint to connect to Azure resources means connecting to a private IP address instead of the public endpoint. Existing Azure services are configured to use existing DNS to connect to the public endpoint. The DNS configuration will need to be overridden to connect to the private endpoint.
A private DNS zone will be created for each Azure resource configured with a private endpoint. A DNS A record is created for each private IP address associated with the private endpoint.
The following DNS zones are created in this sample:
- privatelink.queue.core.windows.net
- privatelink.blob.core.windows.net
- privatelink.table.core.windows.net
- privatelink.file.core.windows.net
Application Insights
Application Insights is used to provide monitor the Azure Function.
- Microsoft.Insights/components: The Application Insights instance used by the Azure Function for monitoring.
NOTE:
- This ARM template will allow access to the storage account through the private endpoints only. So, you will not be able to access the data storage in the storage account through the portal or otherwise.
- You can give access to your secured IP address or virtual network for the data storage in the storage account, by Managing the default network access rule
For more information on configuring Azure Storage firewalls and virtual networks, please refer: Configure Azure Storage firewalls and virtual networks
For more information on Azure Functions networking options and VNET integration, please refer: Azure Functions Networking Options
Tags: Microsoft.Network/privateDnsZones/virtualNetworkLinks, Microsoft.Network/privateEndpoints/privateDnsZoneGroups, Microsoft.Network/virtualNetworks, Microsoft.Network/privateDnsZones, Microsoft.Network/privateEndpoints, Microsoft.Storage/storageAccounts, Microsoft.Storage/storageAccounts/fileServices/shares, Microsoft.Insights/components, Microsoft.Web/serverfarms, Microsoft.Web/sites

