Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The Chief Information Security Office (CISO) workshop helps accelerate security program modernization with reference strategies built using Zero Trust principles.
The workshop covers all aspects of a comprehensive security program including strategic initiatives, roles and responsibilities, success metrics, maturity models, and more. Videos and a Visio file can be found here.
Customers with Microsoft Unified can contact their Customer Success Account Manager (CSAM) to request a delivery of the CISO workshop (Envisioning session for End to End security).
Why should you make time to watch this workshop?
You get actionable advice on how to quickly increase your security program maturity, security posture, and ability to rapidly respond to attacks. These best practices, references, and other guidance are based on real world lessons learned across our customers and from Microsoft’s internal security teams.
Who should watch this workshop?
The workshop is useful for security teams, IT teams, business leaders, and cloud teams, but is primarily focused on:
- CISO + Security Directors - modernize security strategy and program components, integrate security into larger organization.
- CIO + IT Directors - integrate security into technology program, cloud, and other initiatives.
- Enterprise + Security Architects – and other roles with broad strategy/technology responsibilities.
Note
The CISO workshop videos are modular so you can jump to any section of interest or start at the beginning and watch all the way through.
What’s in the workshop?
Guidance on how to align security to continuously changing business priorities, technology platforms, threat landscape, and security tools. The workshop includes reference strategies and plans, lessons learned, and antipatterns/gotchas based on real world projects.
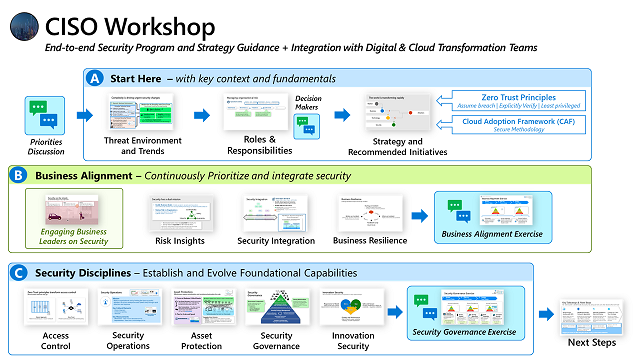
The workshop videos (about 4 hours total) and slides are organized into these discussions:
- Introduction and Overview of the CISO Workshop
- Part A - Key Context and Fundamentals
- Trends impacting security from the threat environment, technology, and business transformations
- Evolution of security roles and responsibilities, including key best practices and trends to monitor
- Recommended strategy and strategic initiatives to improve your program: the role of Zero Trust in strategy, the (low) cost for attackers to buy tools and passwords, learnings on getting reliable information, and a business analysis of ransomware attacks.
- Part B - Business Alignment
- Engaging business leaders on security – guidance to have a conversation in the language of leaders to explain security, key metrics to measure success of a program, and how to get support for security goals.
- Risk Insights – discusses the dual mission of security to reduce risk to the organization and enable business goals, shares tips on aligning security business goals and business risk, and shares insights on the types of attacker motivations organization’s face.
- Security Integration - guidance for successfully integrating security teams together and integrating security into IT and Business processes. Including an in-depth discussion of how to build a posture management program – an operational team focused on preventive controls (which complements the security operations (SecOps/SOC) team focused on detection, response, and recovery)
- Business Resilience – discusses how business resilience is the north star of the security program across all the security disciplines that requires balancing security investments (before, during, and after an incident) and creating a strong feedback loop. This section also includes discussion of the impact of unbalanced strategies (which is a common antipattern).
- Maturity models describing real world journeys for Risk Insights, Security Integration, and Business Resilience – including specific concrete actions to help you move up to the next level
- Part C – Security Disciplines
- Access Control - discusses how the Zero Trust approach is transforming access control, including identity and network access converging into a single coherent approach, and the emergence of the Known-Trusted-Allowed model (which updates the classic authenticated/authorized approach).
- Security Operations – discusses key leadership aspects of a security operations capability, often called SecOps or a Security Operations Center (SOC) including critical success metrics, key touchpoints with business leaders and functions, and the most important cultural elements.
- Asset Protection – discusses two key imperatives for teams that manage and secure assets (often IT Operations or Workload operations in DevOps). These teams must prioritize security work based on business criticality and must strive to efficiently scale security across the large, growing, and continuously evolving set of assets in the technical estate.
- Security Governance – discusses the role of Security Governance as a bridge between the world of business goals and technology and how this role is changing with the advent of cloud, digital and Zero Trust transformations. This section also covers key components of security governance including risk, compliance, security architecture, posture management, (strategic) threat intelligence, and more.
- Innovation Security - discussion of how application security evolves into a modern approach (including DevSecOps) and key focus areas to drive success of this capability.
- Security Governance Maturity models describing real world journeys for Security Architecture, Posture Management, and IT Security Maintenance – including specific concrete actions to help you move up to the next level
- Next Steps/Closing – wraps up the workshop with key quick wins and next steps
Note
The Architecture Design Session modules discussed in the video aren't yet published
Next steps
Continue your journey as part of the Security Adoption Framework.