Manage permissions using administrative units in Microsoft Entra ID
An administrative unit is a Microsoft Entra resource that can be a container for other Microsoft Entra resources. An administrative unit can contain only users, groups, or devices.
Administrative units restrict permissions in a role to any portion of your organization that you define. For example, you could use administrative units to delegate the Helpdesk Administrator role to regional support specialists. By doing so, they can manage users only in the region they support.
You can assign a user as a member of multiple administrative units. For example, an organization can add users to administrative units by geography and division. In this example, the organization can add the same user to both the "London" (geography) and "Marketing" (division) administrative units.
Deployment scenario
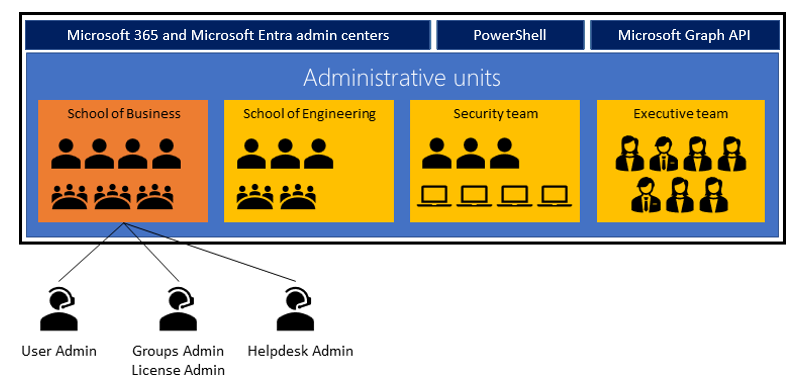
Organizations made up of independent divisions of any kind can find it useful to restrict administrative scope by using administrative units. For example, consider a large university consisting of many autonomous schools (School of Business, School of Engineering, and so on). Each school has a team of IT admins who control access, manage users, and set policies for their school.
In this scenario, a central administrator could:
- Create an administrative unit for the School of Business.
- Populate the administrative unit with only students and staff within the School of Business.
- Create a role with administrative permissions over only Microsoft Entra users in the School of Business administrative unit.
- Add the business school IT team to the role, along with its scope.
License requirements
Using administrative units requires:
- A Microsoft Entra Premium P1 license for each administrative unit administrator.
- A Microsoft Entra Free license for each administrative unit member.
If you'e using dynamic membership rules for administrative units, each administrative unit member requires a Microsoft Entra Premium P1 license.
Manage administrative units
You can manage administrative units by using the Microsoft Entra admin center, PowerShell cmdlets and scripts, or Microsoft Graph API.
Administrative units can logically group Microsoft Entra resources. Consider the following scenarios:
- An organization scattered its IT department globally. As such, it created administrative units that defined relevant geographical boundaries.
- A global organization has suborganizations that are semi-autonomous in their operations. As such, administrative units could represent the suborganizations.
An organization must use its unique requirements to guide which administrative units to create. Administrative units are a common way to define structure across Microsoft 365 services. When an organization plans its administrative units, it should consider how it uses them across Microsoft 365 services. You can get maximum value out of administrative units when you can associate common resources across Microsoft 365 under an administrative unit.
An organization can expect its administrative units to go through the following stages:
- Initial adoption. The organization creates administrative units based on initial criteria. The number of administrative units increase as the organization refines the criteria.
- Pruning. After the organization defines the criteria, it deletes administrative units no longer required.
- Stabilization. Once an organization defines its organizational structure, it doesn't significantly change the number of administrative units in the short term.
Currently supported scenarios
As a Global Administrator or a Privileged Role Administrator, you can use the Microsoft Entra admin center to:
- Create administrative units.
- Add users, groups, or devices as members of administrative units.
- Manage users or devices for an administrative unit with dynamic membership rules.
- Assign IT staff to administrative unit-scoped administrator roles.
Administrative unit-scoped admins can use the Microsoft 365 admin center for basic management of users in their administrative units. A group administrator with administrative unit scope can manage groups by using PowerShell, Microsoft Graph, and the Microsoft 365 admin centers.
Administrative units apply scope only to management permissions. They don't prevent members or administrators from using their default user permissions to browse other users, groups, or resources outside the administrative unit. To address this issue, organizations use the Microsoft 365 admin center to filter out users outside the administrative units of a scoped admin. However, the scoped admin can browse other users in the Microsoft Entra admin center, PowerShell, and other Microsoft services.
Note
Only the features described in this unit are available in the Microsoft 365 admin center. No organization-level features are available for a Microsoft Entra role with administrative unit scope.
The following sections describe current support for administrative unit scenarios.
Administrative unit management
| Permissions | Microsoft Graph/PowerShell | Microsoft Entra admin center | Microsoft 365 admin center |
|---|---|---|---|
| Create or delete administrative units | X | X | |
| Add or remove members individually | X | X | |
| Add or remove members in bulk by using CSV files | X | No plan to support | |
| Assign administrative unit-scoped administrators | X | X | |
| Add or remove users or devices dynamically based on rules (Preview) | X | X | |
| Add or remove groups dynamically based on rules |
User management
| Permissions | Microsoft Graph/PowerShell | Microsoft Entra admin center | Microsoft 365 admin center |
|---|---|---|---|
| Administrative unit-scoped management of user properties, passwords | X | X | X |
| Administrative unit-scoped management of user licenses | X | X | |
| Administrative unit-scoped blocking and unblocking of user sign-ins | X | X | X |
| Administrative unit-scoped management of user multifactor authentication credentials | X | X |
Group management
| Permissions | Microsoft Graph/PowerShell | Microsoft Entra admin center | Microsoft 365 admin center |
|---|---|---|---|
| Administrative unit-scoped management of group properties and membership | X | X | |
| Administrative unit-scoped management of group licensing | X | X |
Note
Adding a group to an administrative unit doesn't grant scoped group administrators the ability to manage properties for individual members of that group. For example, a scoped group administrator can manage group membership. However, they can't manage authentication methods of users who are members of a group added to an administrative unit. Let's assume you want to manage the authentication methods of users who are members of a group that you previously added to an administrative unit. In this case, you must directly add the individual group members as users of the administrative unit. You must also assign a role that can manage user authentication methods to the group administrator.
Device management
| Permissions | Microsoft Graph/PowerShell | Microsoft Entra admin center | Microsoft 365 admin center |
|---|---|---|---|
| Enable, disable, or delete devices | X | X | |
| Read BitLocker recovery keys | X | X |
Managing permissions in administrative units
When managing permissions using administrative units in Microsoft Entra ID, you can create custom roles and scope them to a specific administrative unit. You can use these roles to grant specific permissions to users or groups within that administrative unit.
However, you can't create a role and globally scope it for all administrative units in the organization. Each administrative unit has its own set of roles and permissions, and you can't apply them across the entire organization.
While you can't globally scope a role for all administrative units, you can work around this restriction. How? You create a custom role that includes permissions for multiple administrative units within an organization. To do so, you must create a role with permissions that apply to all of the administrative units in question. You must then assign that role to users or groups within each of those administrative units.
Adding a group to an administrative unit brings the group itself into the management scope of the administrative unit, but not the members of the group. In other words, an administrator scoped to the administrative unit can manage properties of the group, such as group name or membership. However, they can't manage properties of the users or devices within that group (unless those users and devices are separately added as members of the administrative unit). Why? Because Microsoft Entra ID uses the Azure Role-Based Access Control (RBAC) model, where administrators grant access to resources based on the user's role and the permissions associated with that role.
Constraints
Organizations should keep in mind the following constraints when using administrative units to help manage permission levels:
- They can't nest administrative units.
- Administrative unit-scoped user account administrators can't create or delete users.
- A scoped role assignment doesn't apply to group members added to an administrative unit, unless the organization directly adds the group members to the administrative unit. For more information, see Add members to an administrative unit.
- The system doesn't currently include administrative units in Microsoft Entra Identity Governance.