Understand the Continuous Diagnostics and Mitigation program (CDM)
With a strategy put forth centrally, and numerous agencies poised to benefit from the agility, efficiency, and innovation that cloud computing provides, the government then turned its attention toward diagnosing and mitigating risks to government networks and systems.
While the risk management framework (RMF) provides a pro-active strategy and approach to managing risk, there are numerous unforeseen events that could potentially occur that could slow digital transformation and potentially compromise America's security.
As a result, in 2012 the Continuous Diagnostics and Mitigation (CDM) program was created to support government-wide and agency-specific efforts to provide risk-based, consistent, and cost-effective cybersecurity solutions to protect federal civilian networks across all organizational tiers.
Note
It's important to note that CDM seeks to limit its scope to only federal civilian networks, and not those of the Department of Defense or intelligence community.
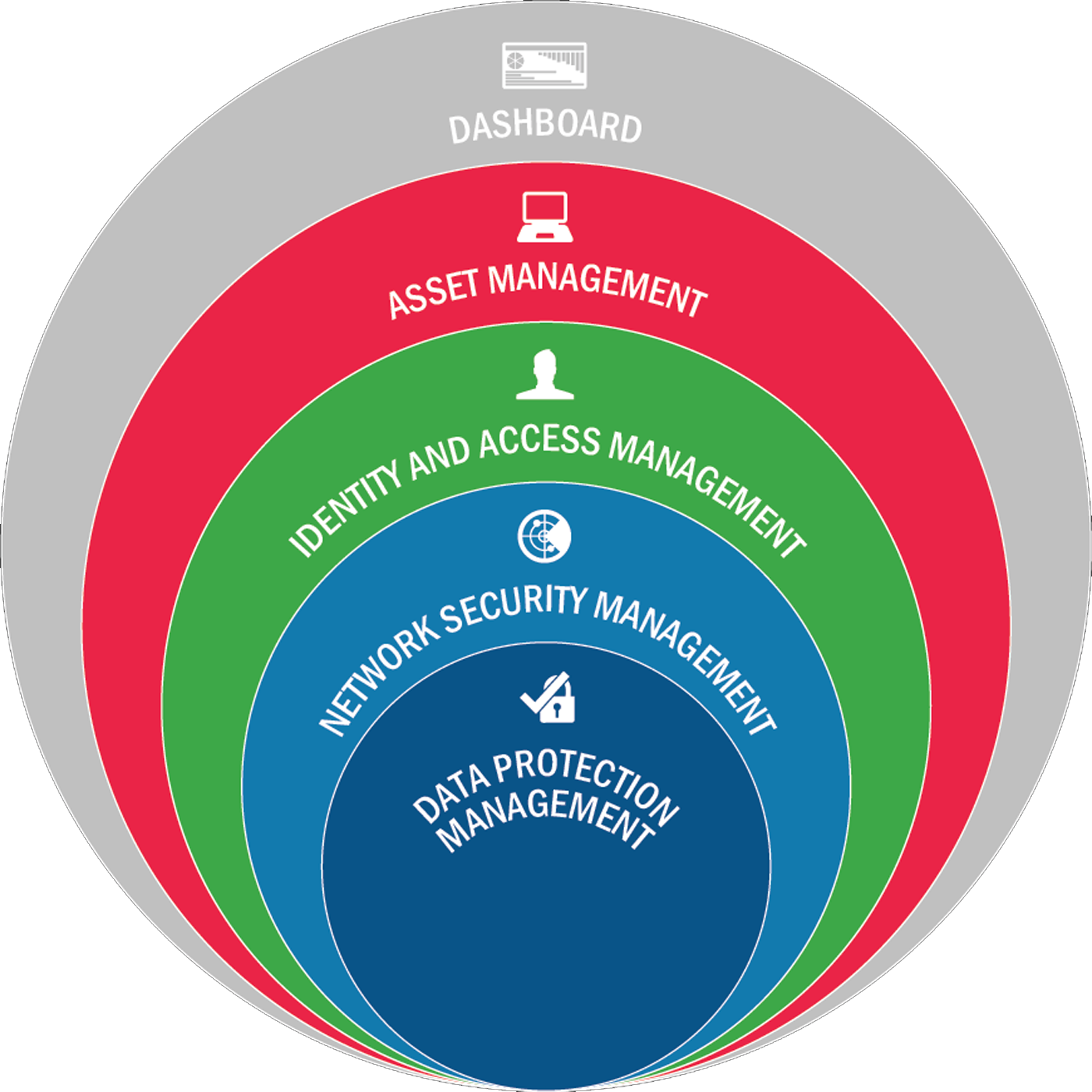
The CDM program includes cybersecurity tools, integration services, dashboards, asset management, identity and access management, network security management, and data protection management capabilities.
Recently, it has focused on cybersecurity and the improvement of security posture by:
- Reducing agency threat surface
- Increasing visibility into the federal cybersecurity posture
- Improving federal cybersecurity response capabilities
- Streamlining Federal Information Security Modernization Act (FISMA) reporting
The program also provides dashboards to 23 key agencies on the cybersecurity posture of their networks, servers, assets, and cloud services.
Funding model
Because it seeks to serve multiple federal civilian agencies, CDM is offered as a shared service and funded centrally. This model enables federal civilian agencies to take advantage of CDM capabilities without having to worry about cost implications.
Importance
CDM is important because it demonstrates that agencies realized, as part of the 2011 Cloud Strategy, that they share common challenges, and that by sharing resources and funding efforts centrally, they may all benefit.
CDM also recognizes the importance of always monitoring government resources from a central location rather than individual implementations, and ensuring all agencies reduce their threat surface, provide the best response capabilities, and streamline their FISMA reporting responsibilities.
Governing security
CDM largely seeks to govern the monitoring of federal civilian networks from a central point, while also providing those same capabilities to all federal civilian agencies.
Securing federal civilian networks
CDM's security capabilities fall into four broad categories:
- Asset management (hardware, software, configuration settings, software vulnerability, and enterprise mobility)
- Identity and access management (account/access/manage privileges, trust determination, credentials and authentication, security-related behavioral training)
- Network security management (network behavior, firewall traffic, encrypted and decrypted data, virtual private connections, ports and protocols)
- Data protection management (data discovery and classification, data protection, data loss prevention, data breach/spillage mitigation, information rights management)
Technology
CDM leverages numerous differing technologies to provide monitoring and mitigation. Of note are its CDM Agency Dashboard and CDM Federal Dashboard tooling that provide visibility at both an agency-level and government-wide level.
Compliance assurance
CDM is currently run out CISA, the CyberSecurity and Infrastructure Agency. Accordingly, CISA is empowered to leverage its authority to ensure compliance.