Manage authentication
Microsoft Power Platform authentication involves a sequence of requests, responses, and redirects between the user's browser and Microsoft Power Platform or Azure services. The sequence follows the Microsoft Entra ID auth code grant flow.
You can choose from three main identity models in Microsoft 365 when you set up and manage user accounts:
Cloud identity: Manage your user accounts in Microsoft 365 only. No on-premises servers are required to manage users; it's all done in the cloud.
Synchronized identity: Synchronize on-premises directory objects with Microsoft 365 and manage your users on-premises. You can also synchronize passwords so that the users have the same password on-premises and in the cloud, but they'll have to sign in again to use Microsoft 365.
Federated identity: Synchronize on-premises directory objects with Microsoft 365 and manage your users on-premises. The users have the same password on-premises and in the cloud, and they don't have to sign in again to use Microsoft 365. This is often referred to as single sign-on.
It's important to carefully consider which identity model to use from the start. Consider time, existing complexity, and cost. These factors manifest differently for every organization. Your choice should be based on the size of your company and the depth and breadth of your IT resources.
Understanding Microsoft 365 identity and Microsoft Entra ID
Microsoft 365 uses Microsoft Entra ID, the cloud-based user identity, and authentication service, to manage users. Deciding how to configure the identity management between your on-premises and Microsoft 365 is an early and foundational decision for your cloud infrastructure. Changing this configuration later can be difficult, so carefully consider the options to determine what works best for your organization.
You can choose from two main authentication models in Microsoft 365 to set up and manage user accounts: cloud authentication and federated authentication.
Cloud authentication
If you don't have an existing Active Directory environment on-premises, that may influence your choice of authentication and identity services. Below are some authentication and identity management models to consider.
Cloud Only
With the cloud-only model, you manage your user accounts in Microsoft 365 only. No on-premises servers are required. You create and manage users in the Microsoft 365 admin center or by using Windows PowerShell PowerShell cmdlets. Identity and authentication are handled completely in the cloud by Microsoft Entra ID.
The cloud-only model is typically a good choice if:
You have no other on-premises user directory.
You have a complex on-premises directory and simply want to avoid the work to integrate with it.
You have an existing on-premises directory, but you want to run a trial or pilot of Microsoft 365. Later, you can match the cloud users to on-premises users when you're ready to connect to your on-premises directory.
Password hash sync with seamless single sign-on
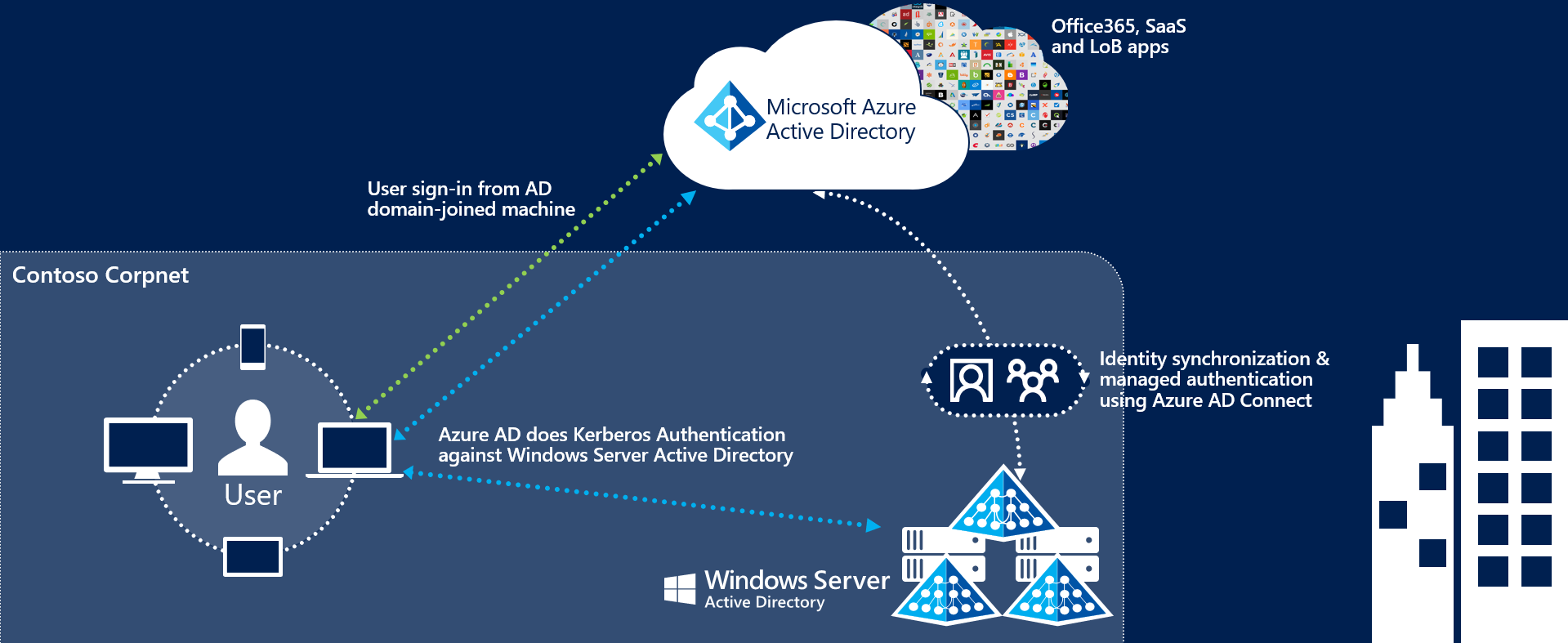
Password hash sync with seamless single sign-on is the simplest way to enable authentication for on-premises directory objects in Microsoft Entra ID. With password hash sync (PHS), you synchronize your on-premises Active Directory user account objects with Microsoft 365 and manage your users on-premises. Hashes of user passwords are synchronized from your on-premises Active Directory to Microsoft Entra ID, so that the users have the same password on-premises and in the cloud.
When passwords are changed or reset on-premises, the new password hashes are synchronized to Microsoft Entra ID. This way, your users can use the same password for cloud and on-premises resources. The passwords are never sent to or stored in Microsoft Entra ID in clear text. Some premium features of Microsoft Entra ID, such as Identity Protection, require PHS regardless of which authentication method is selected. With seamless single sign-on, users are automatically signed in to Microsoft Entra ID when they are on their corporate devices and connected to your corporate network.
Pass-through authentication with seamless single sign-on
Pass-through authentication with seamless single sign-on provides simple password validation for Microsoft Entra ID authentication services. It uses a software agent running on one or more on-premises servers to validate users directly with your on-premises Active Directory. With pass-through authentication (PTA), you synchronize on-premises Active Directory user account objects with Microsoft 365 and manage your users on-premises.
This model allows your users to sign in to both on-premises and Microsoft 365 resources and applications using their on-premises account and password. This configuration validates user passwords directly against your on-premises Active Directory without sending password hashes to Microsoft 365. Organizations with a security requirement to immediately enforce on-premises user account states, password policies, and sign-in hours should use this authentication method. With seamless single sign-on, users are automatically signed in to Microsoft Entra ID when they are on their corporate devices and connected to your corporate network.
Single sign-on
By default, Dynamics 365 Online uses Microsoft Entra ID for authentication. However, many organizations around the world use their local Active Directory to do authentication in-house.
Microsoft Entra ID Seamless single sign-on (Seamless SSO) automatically signs in users when they are on their corporate devices and connected to your corporate network. When SSO is enabled, users don't need to enter their passwords (or often even their usernames) to sign in to Microsoft Entra. This feature provides your users easy access to cloud-based applications without needing any more on-premises components.
Seamless SSO can be combined with either the Password Hash Synchronization or Pass-through Authentication sign-in methods. Seamless SSO isn't applicable to Active Directory Federation Services (ADFS).*
Note
Seamless SSO needs the user's device to be domain-joined, but doesn't need for the device to be Microsoft Entra Joined.
Key benefits
Great user experience
Users are automatically signed into both on-premises and cloud-based applications.
Users don't have to enter their passwords repeatedly.
Easy to deploy & administer
No other components needed on-premises to make this work.
Works with any method of cloud authentication - Password Hash Synchronization or Pass-through Authentication.
Can be rolled out to some or all your users using Group Policy.
Things to consider
The sign-in username can be either the on-premises default username (userPrincipalName) or another attribute configured in Microsoft Entra Connect (Alternate ID). Either of these options works because Seamless SSO uses the securityIdentifier claim in the Kerberos ticket to look up the corresponding user object in Microsoft Entra ID.
Seamless SSO is an opportunistic feature. If it fails for any reason, the sign-in experience reverts to its normal behavior, i.e., the user must enter their password on the sign-in page.
If an application includes a domain_hint (OpenID Connect) or whr (SAML) parameter in its Microsoft Entra sign-in request to identify your tenant, or a login_hint parameter to identify the user, the user is automatically signed in without needing to enter a username or password.
Users also get a silent sign-on experience if an application (for example,
https://contoso.crm.dynamics.com) sends sign-in requests to Microsoft Entra's tenant endpoints (such as,https://login.microsoftonline.com/contoso.comorhttps://login.microsoftonline.com <tenant_ID>) instead of Microsoft Entra's common endpoint (https://login.microsoftonline.com/common).Sign out is supported. This allows users to choose another Microsoft Entra ID account to sign in with, instead of being automatically signed in using Seamless SSO automatically.
Microsoft 365 Win32 clients (Outlook, Word, Excel, and others) with versions 16.0.8730.xxxx and above support a non-interactive flow. For OneDrive, you need to activate the OneDrive silent config feature to enable a silent Sign-On experience.
It can be enabled via Microsoft Entra Connect.
It's a free feature; you don't need paid licenses for Microsoft Entra ID to use it.
Federate a single AD forest environment to the cloud
The following tutorial walks you through creating a hybrid identity environment using federation. This environment can then be used for testing or for becoming more familiar with how a hybrid identity works.
Tutorial: Federate a single AD forest environment to the cloud
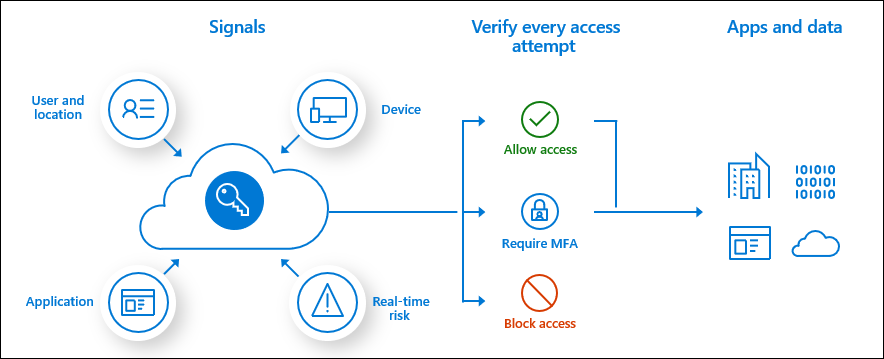
Microsoft Entra conditional Access
Conditional Access policies in Microsoft Entra ID at their simplest are if-then statements: if a user wants to access a resource, then they must complete an action.
Example: A payroll manager who wants to access the payroll app built with Power Apps is required to perform multifactor authentication to access it.
Administrators are faced with two primary goals:
Empower users to be productive wherever and whenever.
Protect the organization's assets.
Using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure, while staying out of your user’s way when they're not needed. Conditional Access policies are enforced after the first-factor authentication has been completed.
Only Global Admins can configure Conditional Access policies. These can't be configured by either Microsoft Power Platform or Dynamics 365 admins.
To learn how to set up Conditional Access policies, see Plan a Conditional Access deployment.