Protect data while in use
Microsoft enables customers to protect their data throughout its entire lifecycle: at rest, in transit, and in use. Azure confidential computing enables customers to safeguard their data while it's processed in the cloud.
Azure confidential computing
Azure confidential computing is a set of data security capabilities that offers encryption of data while in use. This type of security means that data can be processed in the cloud with the assurance that it's always under customer control. Confidential computing ensures that when data is in the clear, which is needed for efficient data processing in memory, the data is protected inside a hardware-based trusted execution environment (TEE), also known as an enclave. TEE helps ensure that there's no way to view data or the operations from outside the enclave. Only the application designer has access to TEE data. Access is denied to everyone else, including Azure administrators. TEE also helps ensure that only authorized code is permitted to access data. If the code is altered or tampered with, the operations are denied, and the environment is disabled.
Azure DCsv2-series virtual machines have the latest generation of Intel Xeon processors with Intel Software Guard Extensions (SGX) technology, which provides a hardware-based TEE. Intel SGX isolates a portion of physical memory to create an enclave where select code and data are protected from viewing or modification. The protection offered by Intel SGX, when used appropriately by application developers, can prevent compromise due to attacks from privileged software and many hardware-based attacks. An application using Intel SGX needs to be refactored into trusted and untrusted components. The untrusted part of the application sets up the enclave, allowing the trusted part to run inside the enclave. No other code, irrespective of the privilege level, has access to the code executing within the enclave or the data associated with enclave code. Design best practices call for the trusted partition to contain just the minimum amount of content required to protect customer’s secrets.
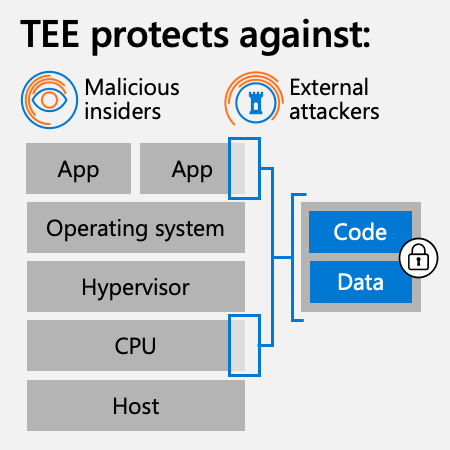
Infographic with title “TEE protects against:”. Underneath the title are two icons indicating the two groups that TEE protects against, one labeled “Malicious insiders” and the other labeled “External attackers”. Under the icons, on the left side of the infographic, are a stack of five tiers of boxes. The top row has two boxes side by side, each labeled “App”. The next four boxes under that row are labeled, in descending order, “Operating system”, “Hypervisor”, “CPU”, and “Host”. To the right of the stack of boxes, is another box with two stacked boxes inside of it, one labeled “Code” and one labeled “Data”. A lock icon is superimposed over the right-hand side of the “Code” and “Data” boxes. On the right-hand side of the top right “App” box, is a rectangular outline encompassing the right-hand end of that “App” box. A similar rectangular outline encompasses the right-hand end of the “CPU” box. These two rectangular outlines are a joined together by line connecting them. From the middle of that connecting line is a line segment that connects to the box containing the “Code” and “Data” boxes.
Aside from VMs using Intel SGX, Azure confidential computing also includes VMs based on AMD EPYC 3rd Gen CPUs, which support lift and shift scenarios without changing any code. With AMD EPYC 3rd Gen technology, the contents of the entire VM is encrypted at runtime, making it opaque to cloud administrators for secure and isolated computations.
Based on customer feedback, Microsoft has started to invest in higher-level scenarios for Azure confidential computing. Customers can review the scenario recommendations as a starting point for developing their own applications using confidential computing services and frameworks.
Now, let's review what you've learned with a brief knowledge check.