Climb the security ladder from EOP to Microsoft Defender for Office 365
Every Microsoft 365 subscription comes with security capabilities. The goals and actions that you can take depend on the focus of these different subscriptions. In Office 365 security, there are three main cloud-based security services (or products) tied to your subscription type:
- Exchange Online Protection (EOP)
- Microsoft Defender for Office 365 Plan 1 (Defender for Office P1)
- Microsoft Defender for Office 365 Plan 2 (Defender for Office P2)
Office 365 security builds on the core protections offered by EOP. EOP is present in any subscription where Exchange Online mailboxes exist.
The following table provides a common summarization of these three cloud-based security products.
| EOP | Microsoft Defender for Office 365 P1 | Microsoft Defender for Office 365 P2 |
|---|---|---|
| Prevents broad, volume-based, known attacks. | Protects email and collaboration from zero-day malware, phish, and business email compromise. | Adds post-breach investigation, hunting, and response, as well as automation, and simulation (for training). |
But in terms of architecture, let's start by thinking of each piece as cumulative layers of security, each with a security emphasis. More like this:
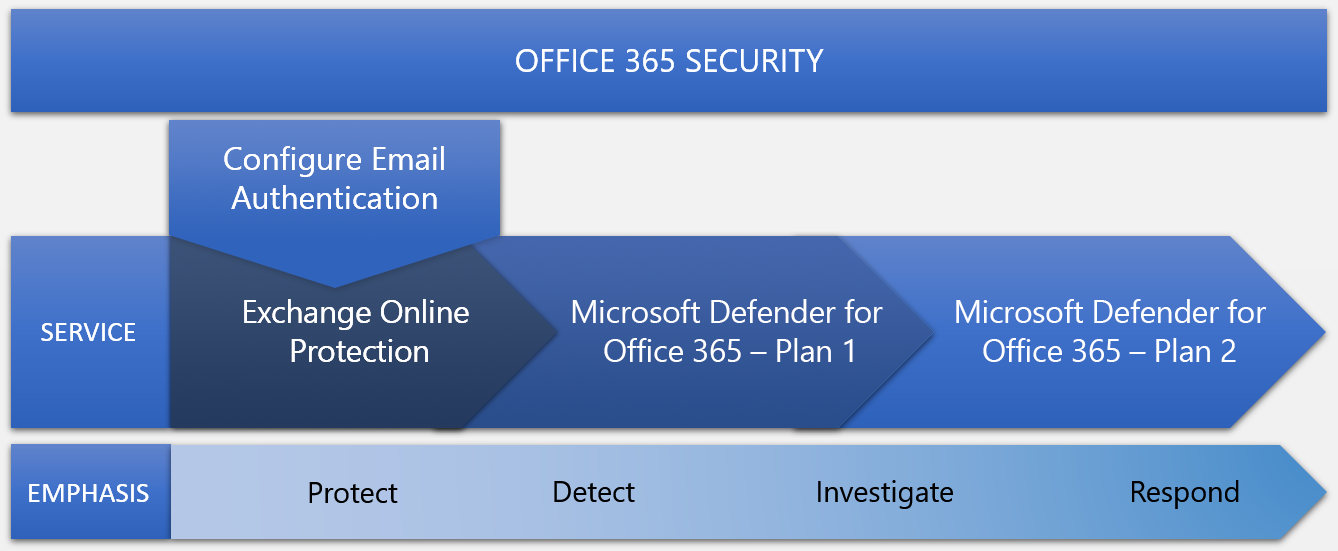
Each of these services emphasizes a goal from among Protect, Detect, Investigate, and Respond. However, all the services can carry out any of the goals of protecting, detecting, investigating, and responding.
The core of Office 365 security is EOP protection. Microsoft Defender for Office 365 P1 contains EOP in it. Defender for Office 365 P2 contains P1 and EOP. The structure is cumulative. For this reason, when an organization configures Microsoft Defender for Office 365, it should start with EOP and work to Microsoft Defender for Office 365.
Though email authentication configuration takes place in public DNS, it's important to configure this feature to help defend against spoofing.
Important
If you have EOP, you should configure email authentication.
You have EOP if you have any of the lower-tiered plans of Office 365 up through Office 365 E3. However, you can also buy standalone Microsoft Defender for Office 365 P1 through upgrade. If you have Office 365 E5, you already have Microsoft Defender for Office 365 P2.
The Office 365 security ladder from EOP to Microsoft Defender for Office 365
It can be difficult at first glance to tell how Microsoft Defender for Office 365 provides an advantage over pure EOP threat management. To help determine whether an upgrade path is right for an organization, let's look at the capabilities of each product when it comes to:
- Preventing and detecting threats
- Investigating
- Responding
Let's start with Exchange Online Protection:
| Prevent/Detect | Investigate | Respond |
|---|---|---|
| Technologies include: - spam - phish - malware - bulk mail - spoof intelligence - impersonation detection - Admin Quarantine - Admin and user submissions of False Positives and False Negatives - Allow/Block for URLs and Files - Reports |
- Audit log search - Message Trace |
- Zero-hour auto purge (ZAP) - Refinement and testing of allowlists and blocklists |
Because these products are cumulative, Microsoft Defender for Office 365 P1 includes these EOP features.
Gains with Microsoft Defender for Office 365, Plan 1 (to date):
| Prevent/Detect | Investigate | Respond |
|---|---|---|
| Technologies include everything in EOP plus: - Safe attachments - Safe links - Microsoft Defender for Office 365 protection for workloads (ex. SharePoint Online, Teams, OneDrive for Business) - Time-of-click protection in email, Office clients, and Teams - Anti-phishing in Defender for Office 365 - User and domain impersonation protection - Alerts, and SIEM integration API for alerts |
- SIEM integration API for detections - Real-time detections tool - URL trace |
- Same |
So, Microsoft Defender for Office 365 P1 expands on the prevention side of threat management and adds extra forms of detection.
Microsoft Defender for Office 365 P1 also adds the Real-time detections tool, which organizations can use for investigations. Having this tool is proof that you have Microsoft Defender for Office 365 P1. Why? Because it doesn't appear in Microsoft Defender for Office 365 P2.
Gains with Microsoft Defender for Office 365, Plan 2 (to date):
| Prevent/Detect | Investigate | Respond |
|---|---|---|
| Technologies include everything in EOP, and Microsoft Defender for Office 365 P1 plus: - Same |
- Threat Explorer - Threat Trackers - Campaign views |
- Automated Investigation and Response (AIR) - AIR from Threat Explorer - AIR for compromised users - SIEM Integration API for Automated Investigations |
So, Microsoft Defender for Office 365 P2 expands on the investigationandresponse side of the house. It also adds a new hunting strength - Automation.
In Microsoft Defender for Office 365 P2, the primary hunting tool is called Threat Explorer rather than Real-time detections. If you see Threat Explorer when you navigate to the Microsoft Defender portal, you're in Microsoft Defender for Office 365 P2.
Tip
EOP and Microsoft Defender for Office 365 are also different when it comes to end-users. In EOP and Microsoft Defender for Office 365 P1, the focus is on awareness. As such, those two services include the Report message Outlook add-in. With this feature, users can report suspicious looking emails for further analysis.
In Microsoft Defender for Office 365 P2 (which contains everything in EOP and P1), the focus shifts to further training for end-users. As such, the Security Operations Center has access to the powerful Threat Simulator tool, and the end-user metrics it provides.
Microsoft Defender for Office 365 Plan 1 vs. Plan 2 cheat sheet
The following quick reference cheat sheet identifies the capabilities that come with each Microsoft Defender for Office 365 subscription. When combined with your knowledge of EOP features, it should help you determine which Microsoft Defender for Office 365 plan provides the best fit for your organization.
| Microsoft Defender for Office 365 Plan 1 | Microsoft Defender for Office 365 Plan 2 |
|---|---|
| Configuration, protection, and detection capabilities: - Safe Attachments - Safe Links - Safe Attachments for SharePoint, OneDrive, and Microsoft Teams - Anti-phishing protection in Defender for Office 365 - Real-time detections |
Defender for Office 365 Plan 1 capabilities--- plus --- Automation, investigation, remediation, and education capabilities: - Threat Trackers - Threat Explorer - Automated investigation and response - Attack simulation training - Proactively hunt for threats with advanced hunting in Microsoft Defender XDR - Investigate incidents in Microsoft Defender XDR - Investigate alerts in Microsoft Defender XDRNote: Microsoft 365 Defender is now Microsoft Defender XDR (Extended Detection and Response). |