Improve your secure score
The Secure Score tool determines the current state of an organization’s security posture and identifies the risks within the organization. The organization begins by running the tool and receiving this information. Its next step is to analyze the findings and plan how to improve its condition. During this planning process, it should consider:
- The potential for risk.
- The difficulty of implementing proposed solutions.
- The time frames for implementation.
- The effect on its rating based on each Microsoft 365 Secure Score action.
Based on a combination of these factors, the organization should rank its goals in order of priority. Doing so results in a roadmap to a safer, more secure environment.
Important
Planning and implementation should involve all the key stakeholders in an organization. These roles include the Chief Information Security Officer (CISO), the IT security manager, and the administrators who manage on-premises Active Directory, Exchange, Microsoft Entra ID, networking, and so on.
Design your security upgrade plan
Every organization is going to have different success criteria:
- Some organizations want to achieve the maximum target score. Others remain satisfied to settle somewhere in the middle.
- Some organizations prefer to address just their top five items. Others only focus on the items that require the least amount of effort.
As you can see, there’s no “one size fits all” approach. Every organization must determine where they want to be and what they're willing to do to get there.
Many companies start with common approaches when designing their security upgrade plan. For example, unless the tenant is in a high-risk industry such as finance or government, a common approach is to begin by implementing actions that have the lowest effect on user productivity while providing immediate gains. Examples of these actions include:
- Enabling multifactor authentication on all administrator accounts.
- Assigning the Global administrator role to more than one user.
- Enabling auditing across workloads.
- Enabling mailbox auditing.
- Having a weekly review of user sign-in attempts:
- after multiple failures
- from unknown sources
- from multiple geographies
Priorities differ from one organization to another. For example, organizations in the finance and healthcare sectors who are subject to industry regulations might decide on a more aggressive timeline. As such, they might implement solutions such as Data Loss Prevention and Information Rights Management. These solutions have a greater effect on users and take longer to implement.
Tip
Microsoft recommends that you assign a sponsor to help set up meetings, remove roadblocks, and ensure teams stay on schedule.
Finally, using the Secure Score tool to identify potential risks and create a roadmap to mitigate those risks shouldn't be a one-time project. Changes that affect your state of security usually occur over time. These scenarios can include the addition of new administrators and users, new regulations, and new services and features across Microsoft 365. Periodically running Secure Score every six months or so provides the insight needed to mitigate any risks associated with those changes.
Take action to improve your score
The Recommended actions tab lists the security recommendations that address possible attack surfaces. It also includes their status (to address, planned, risk accepted, resolved through third party, resolved through alternate mitigation, and completed). You can search, filter, and group all the recommended actions.
Once you complete an action, it can take between 24-48 hours for your secure score to reflect the changes.
Ranking
Ranking is based on the number of points an organization has yet to achieve, implementation difficulty, user impact, and complexity. The highest ranked recommended actions have a large number of points remaining with low difficulty, user impact, and complexity.
View recommended action details
When you select a specific recommended action, a full page flyout appears.
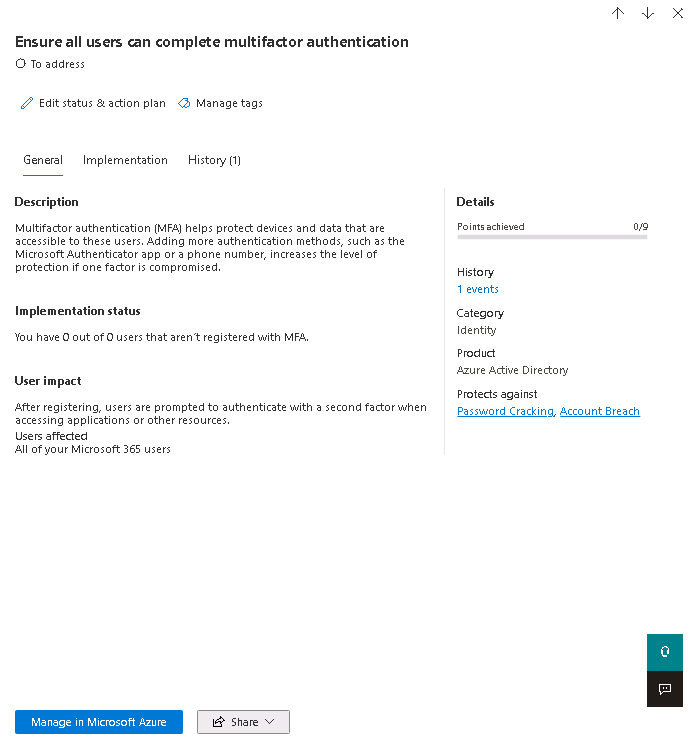
You have two options at the bottom of the flyout page to complete the action:
- Select the Manage button to navigate to the appropriate portal and make the change. By doing so, you gain the points the action is worth, which is visible in the flyout. Points generally take about 24 hours to update.
- Select the Share button to copy the direct link to the recommended action. You can also choose the platform to share the link, such as email, Microsoft Teams, or Microsoft Planner.
Tip
Add Notes to keep track of progress or anything else you want to comment on. If you add your own tags to the recommended action, you can filter by those tags.
Choose a recommended action status
You can choose any of the following statuses and record notes specific to the recommended action.
- To address. You recognize the recommended action is necessary and plan to address it at some point in the future. This state also applies to partially completed actions.
- Planned. There are concrete plans in place to complete the recommended action.
- Risk accepted. Organizations should always balance security with usability. Keep in mind, not every recommendation works for your environment. In those instances, you can choose to accept the risk, or the remaining risk, and not enact the recommended action. This status doesn't receive any points. You can view this action in history or undo it at any time.
- Resolved through third party and Resolved through alternate mitigation. An internal tool or a third-party application already addressed the recommended action. You gain the points the action is worth, so your score more closely reflects your overall security posture. If a third party or internal tool no longer covers the control, you can choose another status. Keep in mind, Microsoft has no visibility into the completeness of an implementation if the system assigned either of these statuses to the recommended action.
Recommended action status for devices
You can't choose a status for Secure Score recommended actions in the Device category. Instead, the system directs you to the associated Microsoft Defender Vulnerability Management security recommendation to take action.
If you choose to create a Global exception in the Defender Vulnerability management security recommendation, the system assigns the exception justification to the status in the Microsoft Secure Score recommended action. Updates can take up to 2 hours.
If you choose to create an Exception per device group in the Defender Vulnerability manage security recommendation, Secure Score doesn't get updated, and the recommended action remains as To address.
Completed recommended actions
Recommended actions have a Completed status once all possible points for the recommended action are achieved. The system confirms completed recommended actions through Microsoft data, and you can't change the status.
Assess information and review user impact
The section called At a glance tells you the category, attacks it can protect against, and the product. When you complete a recommended action, User impact reflects the users' experience. The Users affected are the people impacted by the action.
Implement the recommended action
The Implementation section shows:
- Any prerequisites
- Step-by-step next steps to complete the recommended action
- The current implementation status of the recommended action
- Any Learn more links
Prerequisites include any required licenses or actions you must complete before addressing the recommended action. Verify you have enough available licenses in your subscription to complete the recommended action, and that you applied those licenses to the necessary users.