Configure Privileged Identity Management
Microsoft Entra ID automatically assigns the Microsoft 365 Security Administrator role and the Privileged Role Administrator role to the first person to use Privileged Identity Management (PIM) in an organization's instance of Microsoft Entra ID. This person must be an eligible Microsoft Entra user. Only Privileged Role Administrators can manage the Microsoft Entra directory role assignments of users.
PIM role assignments give organizations a secure way to grant access to their resources. The PIM role assignment process includes the following tasks, each of which this unit examines in greater detail:
- Configure PIM role settings.
- Assign roles to users.
- Activate role assignments.
- Approve or deny requests.
- Extend and renew assignments.
Privileged Identity Management lets you know when important role-related events occur in your Microsoft Entra organization. For example, when an administrator assigns or activates a role. PIM keeps you informed by sending you and other participants email notifications. These emails might also include links to relevant tasks, such activating or renewing a role.
Configure PIM role settings
In Privileged Identity Management, role settings define role assignment properties, such as:
- Multifactor authentication (MFA) and approval requirements for activation
- Assignment maximum duration
- Notification settings
You must have either the Global Administrator or Privileged Role Administrator role to manage PIM role settings for a Microsoft Entra role. You define role settings per role. In other words, all assignments for the same role follow the same role settings. Role settings of one role are independent from role settings of another role.
Organizations should complete the following tasks to configure PIM role settings.
Task 1 - Discover and mitigate privileged roles
You should identify who has privileged roles in your organization. As part of this process, you should:
- Review the users assigned.
- Identify administrators who no longer need the role.
- Remove them from their assignments.
You can use Microsoft Entra roles access reviews to automate the discovery, review, and approval or removal of assignments.
Task 2 - Determine the roles that you want PIM to manage
After you discover and mitigate privileged roles, you should then prioritize the protection of Microsoft Entra roles that have the most permissions. You should also consider what data and permissions are most sensitive for your organization.
First, you should ensure that PIM manages all Global and Security Administrator roles. Why? Because the users assigned to these roles can do the most harm when compromised. Then consider other roles used throughout your organization that are potentially vulnerable to attack. You should ensure that PIM also manages these roles.
Task 3 - Configure PIM settings for Microsoft Entra roles
Finally, you should draft and configure your PIM settings for every privileged Microsoft Entra role that your organization uses.
The following graphic provides an example of how an organization can plan their role settings.
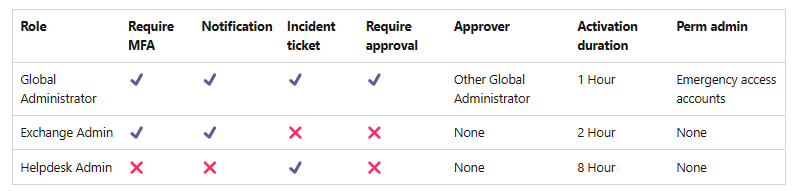
You can configure the following PIM role settings:
Activation maximum duration. Use the Activation maximum duration slider to set the maximum time, in hours, that an activation request for a role assignment remains active before it expires. This value can be from one to 24 hours. If you enter a value greater than 24 hours, the system reverts it back to 24.
On activation, require multifactor authentication. Before a user who is eligible for a role can activate the role, you can require they prove their identity using Microsoft Entra multifactor authentication (MFA). MFA ensures the user is who they say they are with reasonable certainty. Enforcing this option protects critical resources in situations involving a potentially compromised user. The system doesn't prompt users for multifactor authentication if they authenticated with a strong credential or provided multifactor authentication earlier in their session.
Tip
Microsoft recommends that organizations require MFA for all their administrators. Multifactor authentication reduces the risk of an attack using a compromised password. You can require that users complete a multifactor authentication challenge when they sign in. You can also require that users complete a multifactor authentication challenge when they activate a role in PIM. This way, even if the user didn't complete multifactor authentication when they signed in, PIM asks them to do it.
Require justification on activation. You can require users to enter a business justification when they activate the eligible assignment.
Require ticket information on activation. You can require users to enter a support ticket number when they activate the eligible assignment. This setting is an information-only field. PIM doesn't enforce correlation with information from any ticketing system.
Require approval to activate. You can require approval for activation of eligible assignment. The approver doesn’t require any roles, nor does the approver need to be an administrator. When using this option, you have to select at least one approver (Microsoft recommends that you select at least two approvers). There are no default approvers.
Assignment duration. You can choose from two assignment duration options for each assignment type (eligible and active) when you configure settings for a role. These options become the default maximum duration when an administrator assigns the user to the role in PIM.
- You can choose one of these eligible assignment duration options:
- Allow permanent eligible assignment. Resource administrators can assign permanent eligible assignment.
- Expire eligible assignment after. Resource administrators can require that all eligible assignments have a specified start and end date.
- You can choose one of these active assignment duration options:
Allow permanent active assignment. Resource administrators can assign permanent active assignment.
Expire active assignment after. Resource administrators can require that all active assignments have a specified start and end date.
Note
Global Administrators and Privileged Role Administrators can renew all assignments that have a specified end date. Also, users can initiate self-service requests to extend or renew role assignments.
- You can choose one of these eligible assignment duration options:
Require multifactor authentication on active assignment. You can require that administrators provide multifactor authentication when they create an active (as opposed to eligible) assignment. PIM can't enforce MFA when the user uses their role assignment because they're already active in the role from the time the administrator assigned the role. PIM doesn't prompt an administrator for multifactor authentication if they authenticated with a strong credential or provided multifactor authentication earlier in their session.
Require justification on active assignment. You can require that users enter a business justification when they create an active (as opposed to eligible) assignment. In the Notifications tab on the role settings page, PIM enables granular control over who receives notifications and which notifications they receive.
- Turning off an email. You can turn off specific emails by clearing the default recipient check box and deleting any other recipients.
- Limit emails to specified email addresses. You can turn off emails sent to default recipients by clearing the default recipient check box. You can then add other email addresses as recipients. If you want to add more than one email address, separate them using a semicolon (;).
- Send emails to both default recipients and more recipients. You can send emails to both default recipient and another recipient by selecting the default recipient checkbox and adding email addresses for other recipients.
- Critical emails only. For each type of email, you can select the check box to receive critical emails only. What this means is that PIM sends emails to the specified recipients only when the email requires an immediate action. For example, PIM doesn't send emails asking users to extend their role assignment, but it sends emails requiring administrators to approve an extension request.
Assign roles to users
With Microsoft Entra ID, a Global Administrator can make permanent Microsoft Entra administrator role assignments. A Global Administrator can create these assignments using either the Microsoft Entra admin center or PowerShell commands. The PIM service also allows Privileged Role Administrators to make permanent administrator role assignments. Privileged Role Administrators can also make users eligible for Microsoft Entra administrator roles. An eligible administrator can activate the role when they need it. An activated role remains active through the duration of its assignment.
Privileged Identity Management supports both built-in and custom Microsoft Entra roles.
The assignment process starts by assigning roles to members. To grant access to a resource, the administrator assigns roles to users, groups, service principals, or managed identities. The assignment includes the following data:
- The members or owners to assign the role.
- The scope of the assignment. The scope limits the assigned role to a particular set of resources.
- The type of the assignment. There are two types of assignments:
- Eligible. These assignments require the member of the role to perform an action to use the role. Actions can include:
- Performing a multifactor authentication (MFA) check
- Providing a business justification
- Requesting approval from designated approvers
- Active. These assignments don't require the member to perform any action to use the role. Members assigned as active have the privileges assigned to the role.
- Eligible. These assignments require the member of the role to perform an action to use the role. Actions can include:
- The duration of the assignment. You can set the duration of an assignment to either:
- Permanent. These assignments have no expiration date. Use this option for permanent workers who frequently need the role permissions.
- Time-bound. These assignments expire at the end of a specified period. Use this option with temporary or contract workers. For example, workers whose project have a known end date and time.
For certain roles, administrators can use PIM to restrict the scope of the granted permissions to a single administrative unit, service principal, or application. This procedure is an example of assigning a role that has the scope of an administrative unit. For a list of roles that support scope through an administrative unit, see Assign scoped roles to an administrative unit.
Additional reading. For more information, see Assign Microsoft Entra roles, Assign Azure resource roles, and Assign eligibility for a PIM for Groups.
Activate role assignments
If a user is eligible for an administrative role, they must activate the role assignment when they need to perform privileged actions. For example, if you occasionally manage Microsoft 365 features, your organization's Privileged Role Administrators might not make you a permanent Global Administrator. Privileged Role Administrators are hesitant to assign a permanent Global Administrator role because it impacts too many other services. Instead, they would make you eligible for a specific service role, such as Exchange Online Administrator. You can request to activate that role when you need its privileges. Doing so provides you with administrator control for a predetermined time period.
If an administrator configured the role in PIM to require approval to activate, PIM sends an email notification to the approver. If the role doesn't require approval to activate, the assigned user can immediately start using the role.
Additional reading. For more information, see Activate Microsoft Entra roles, Activate my Azure resource roles and Activate my PIM for Groups roles.
Approve or deny requests
Delegated approvers receive email notifications when a role request is pending their approval. Approvers can view, approve, or deny these pending requests in PIM. After the approver approves the request, the member can start using the role. For example, if PIM assigns a user or group with the Contribution role to a resource group, they can then begin managing that particular resource group.
Additional reading. For more information, see Approve or deny requests for Microsoft Entra roles, Approve or deny requests for Azure resource roles, and Approve activation requests for PIM for Groups.
Extend and renew assignments
Administrators can assign roles with fixed durations using start and end date properties. When the assignment end approaches, Privileged Identity Management sends email notifications to the affected users or groups. It also sends email notifications to administrators of the resource to ensure they maintain appropriate access.
Note
The system can renew assignments and keep them visible for up to 30 days in an expired state, regardless of whether an administrator extended access.
Organizations can address the expiration of time-bound assignments in one of two ways:
- Extend. When a role assignment nears expiration, the user can use PIM to request an extension for the role assignment.
- Renew. When a role assignment expires, the user can use PIM to request a renewal for the role assignment.
Both user-initiated actions require an approval from a Global Administrator or Privileged Role Administrator. With PIM, organizations don't have to worry about their administrators constantly being on the lookout for assignments due to expire. Instead, administrators can just wait for the extension or renewal requests to arrive for simple approval or denial.
Only administrators of the resource can extend or renew role assignments. The affected user or group can request to extend roles that are about to expire and request to renew roles that are already expired.
Privileged Identity Management sends email notifications to administrators and affected user or groups of roles that are expiring within 14 days and one day prior to expiration. It sends another email when an assignment officially expires.
Administrators receive notifications when a user or group assigned an expiring or expired role requests to extend or renew. When a specific administrator resolves the request, the system notifies all other administrators of the resolution decision (approved or denied). It then notifies the requesting user or group of the decision.
When approving a request to extend role assignment, resource administrators can choose a new start date, end date, and assignment type. Changing assignment type can be necessary if the administrator wants to provide limited access to complete a specific task (one day, for example). In this example, the administrator can change the assignment from Eligible to Active. This change means they can provide access to the requestor without requiring them to activate.
If a user assigned to a role doesn't request an extension for the role assignment, an administrator can extend an assignment on behalf of the user. Administrative extensions of role assignment don't require approval. However, the system sends notifications to all other administrators after a user or administrator extends the role.
Additional reading. For more information, see:
- Extend or renew Microsoft Entra role assignments.
- Extend or renew Azure resource role assignments.
- Extend or renew PIM for Groups assignments.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”