Explore today's work and threat landscape
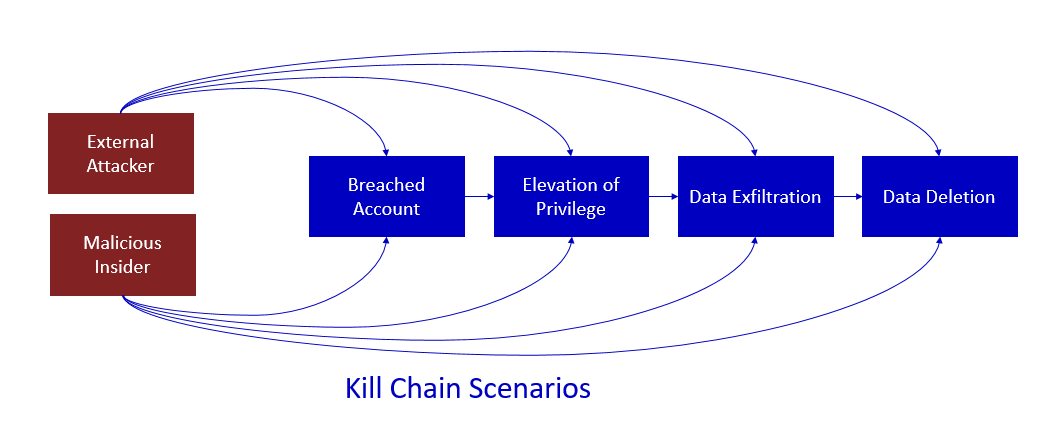
Most attacks follow a common process referred to within the security industry as the “Kill Chain.” Briefly, an attack follows a basic pattern and proceeds from one step to the next to achieve the wanted outcomes. Organizations can defend against this step-wise process by implementing security measures on choke points in the chain. Since attackers can bypass any step through various exploitation techniques, the best strategies apply defenses at every step along the chain.
The threat landscape across the globe changed dramatically over the past several years. Hackers continuously increase the sophistication of their attack methods to compromise users and networks alike. At the same time, more organizations are enjoying the benefits of cloud computing. But as companies move to the cloud, they understandably worry how Microsoft 365 protects their users and data from cybercriminals.
Compared to a few years ago, companies today have many more factors to consider when dealing with different entities such as users, devices, apps, and data. While organizations share data with employees, business partners, and customers, they must protect users’ identities and data stored on their devices and apps. Organizations must also mitigate the risks of providing flexibility and space while maintaining company security policies and detecting threats. They must do so while giving workers a better and more productive experience.
This process can be overwhelming to many organizations who don't want to lose control of sensitive data. Statistics show that most data breaches could be avoided by implementing appropriate internal controls. As hackers become more sophisticated in their attacks, data theft continues to rise. Many businesses declare a list of approved services and applications. However, an alarming number of employees use nonapproved third-party apps and personal storage services to store sensitive company documents.
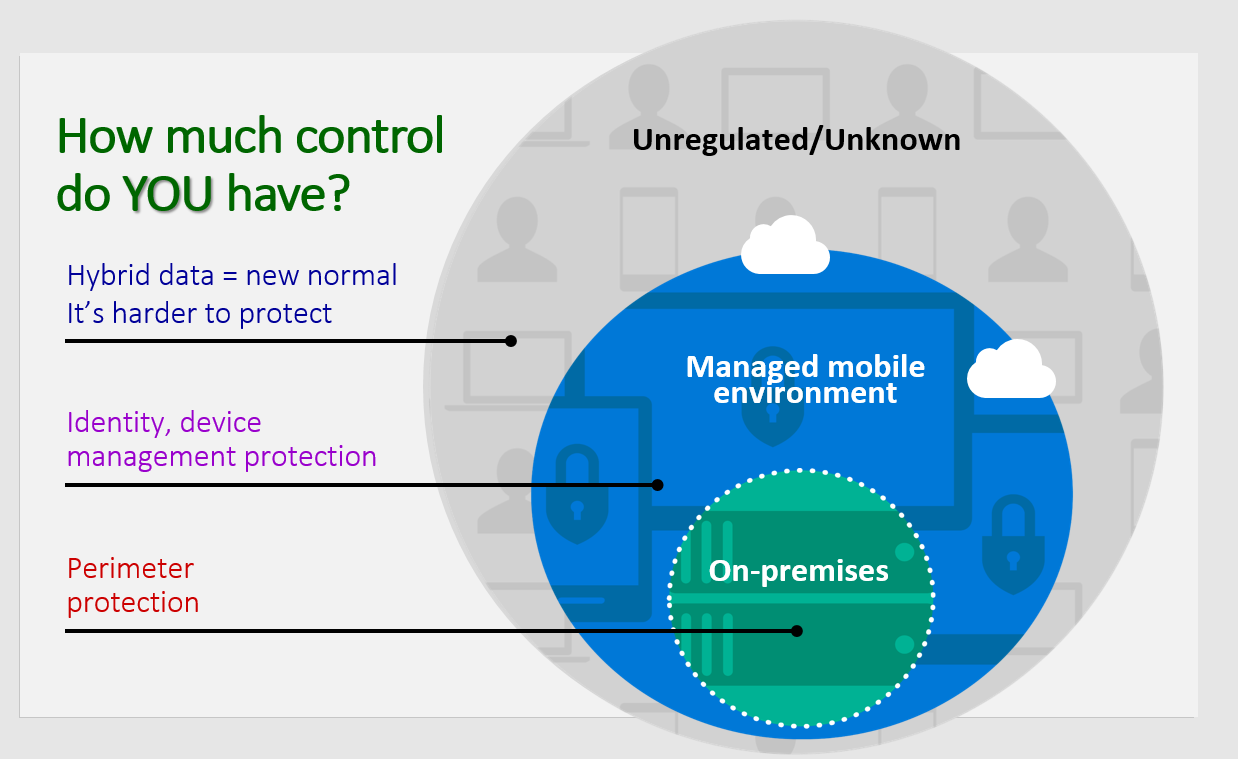
So how much control do companies have?
In an on-premises environment, you have firewalls, email gateways, and proxies that can conduct content inspection. In recent years, organizations expanded that protection boundary to include mobile devices, tablets, and cloud assets. The problem many companies face is that they either lightly manage or even fail to manage the devices that can access their data. Some companies use Mobile Device Management (MDM) solutions to help enforce some level of security. For example, they encrypt the device or configure it for remote wipe in the event the device gets stolen. However, they still don’t have any control when data on those devices moves outside their controlled environment.
In today’s cloud-centric world, organizations face the unregulated (such as files on cloud storage services) and the unknown (such as advanced threats targeting users’ email). This situation is more difficult to protect because organizations now store data everywhere - it’s on-premises, on PCs, on phones, and in the cloud.
The question now becomes: How do companies operate in this world but still adhere to security and business requirements to protect information, particularly when they're dealing with not only their own intellectual property, but also personal identifiable information such as personal identification numbers and credit cards?
Microsoft is invested in addressing these challenges and in helping organizations be more secure by helping them to protect against, detect, and respond to various threat vectors. The remaining units in this module examine the most common threat vectors that organizations must face today.