Examine how phishing retrieves sensitive information
Attacks through email are one of the most common methods used by hackers to gain entry into a network. Users’ computers and account credentials can become compromised through methods such as phishing, spoofing, and malware. Once a hacker can compromise a user’s computer or credentials, it becomes easy for the hacker to threaten the security of an organization.
Phishing attempts involve emails that look legitimate. Phishing is a technique a hacker uses to retrieve sensitive information such as a user’s account credentials or credit card number. For example, a user receives an email from what appears to be a trustworthy source, such as a bank or a company's IT administrator. The purpose of the email is to often entice users to select a link to a malicious website that looks legitimate, except for the URL of the website in question. When users enter the site, it often prompts them to enter personal information that hackers can use to their advantage. Another possibility is the attackers infected the site with malware. Malware can infect the user’s computer with a payload such as:
- Virus. A computer virus is a type of malicious software program, or "malware." When executed, the virus replicates itself by modifying other computer programs and inserting its own code. This process infects files or even the boot sector of the hard drive.
- Trojan horse. A trojan horse typically acts as a backdoor that enables a hacker to control or use the infected computer to the hacker's advantage. Depending on its design, a trojan horse can accomplish many tasks, including:
- Blocking anti-virus software.
- Installing applications.
- Stealing passwords and credit card numbers.
- Infecting other computers and devices connected to the same network.
- Rootkit. A rootkit is a type of malware that provides a hacker with administrative access to a computer. When used, a rootkit typically provides a hacker with full, undetected access to the computer. This access can lead to:
- Stealing or falsifying documents.
- Hiding other malware such as password-stealing key loggers and viruses.
- Using the computer for attacks on other computers.
- Spyware. Spyware often gathers information about internet activity, keystrokes, passwords, and other sensitive data. Attackers also use spyware as adware, where the software delivers pop-up ads and tracks user behavior.
Spear phishing is a type of phishing attack directed at specific individuals. Spear phishing, or whaling, typically targets senior executives and other high-profile individuals, usually for financial gain. Spear phishing often masquerades as a legitimate email. It often prompts the user to respond with sensitive information. It might also prompt the user to select a link that installs malware that infects the user’s computer with some type of payload.
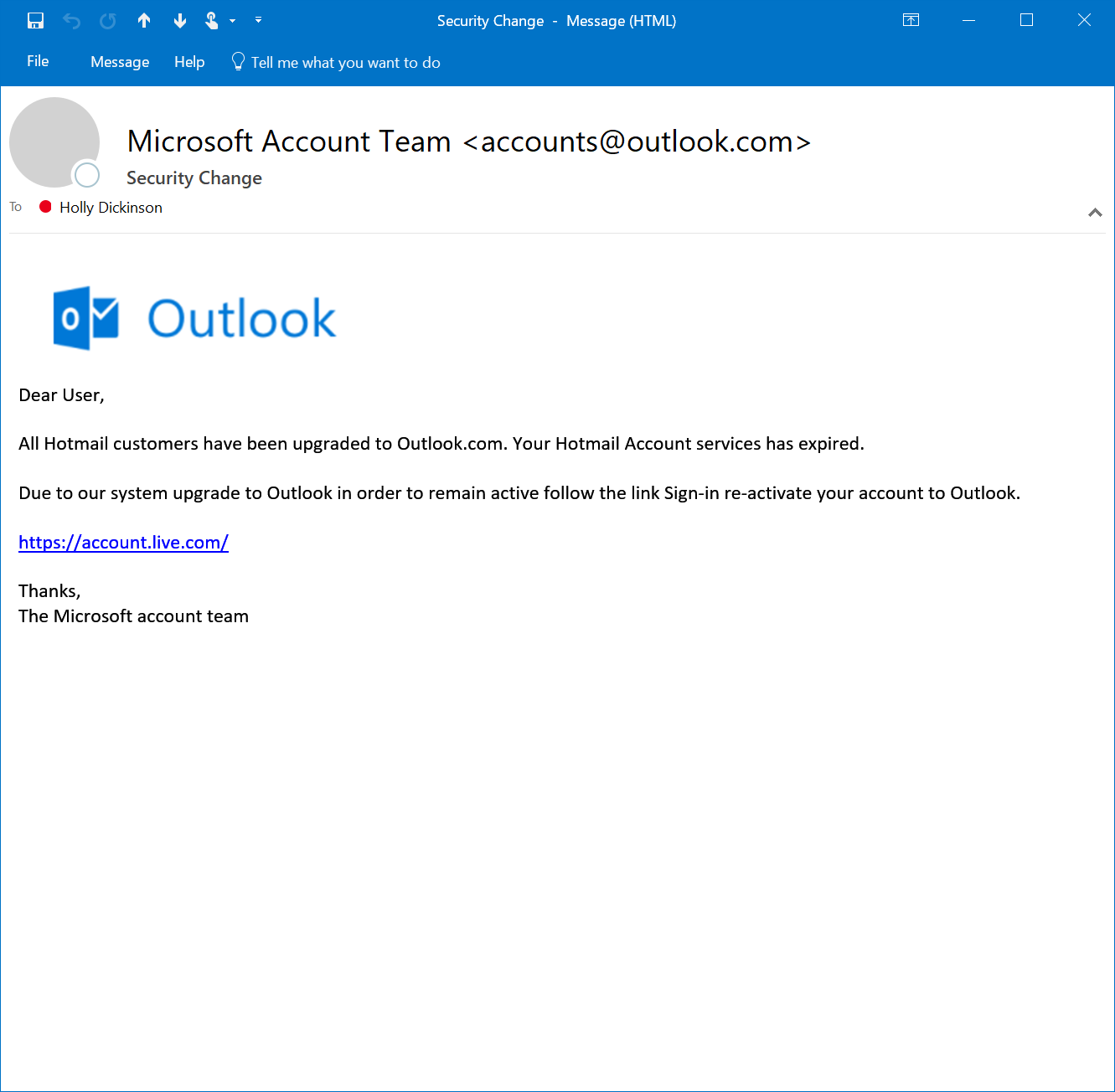
Phishing emails usually contain branding and URLs that, on the surface, appear legitimate. They also typically convey a sense of urgency to persuade the user to act quickly.
In the following example, a user (Holly Dickinson) receives an email that appears to be legitimate. The message is designed to trick the user into selecting the link embedded in the message under the false pretense the user's account expired. The user doesn’t realize the link points to a malicious web site that attackers use to collect user account credentials or download a malicious file.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”