Examine how spoofing deceives users and compromises data security
A feature of the Simple Mail Transfer Protocol (SMTP) enables a domain to send messages that represent another domain. When a sender spoofs an email address, they appear to be a user in one of your organization's domains, or a user in an external domain that sends email to your organization. Interestingly, there are legitimate reasons for organizations to allow spoofing. It's the illegitimate scenarios in which attackers spoof senders to send spam or phishing email that organizations want blocked.
Legitimate scenarios for spoofing include:
- Spoofing internal domains:
- Third-party senders use your domain to send bulk mail to your own employees for company polls.
- An external company generates and sends advertising or product updates on your behalf.
- An assistant regularly needs to send email for another person within your organization.
- An internal application sends email notifications.
- Spoofing external domains:
- The sender is on a mailing list (also known as a discussion list), and the mailing list relays email from the original sender to all the participants on the mailing list.
- An external company sends email on behalf of another company (for example, an automated report or a software-as-a-service company).
Exchange Online Protection (EOP) automatically protects inbound email messages against spoofing. Microsoft 365 provides this protection for organizations with mailboxes in Exchange Online. Standalone EOP also provides this protection to organizations that don't have Exchange Online mailboxes. EOP uses spoof intelligence as part of an organization's overall defense against phishing. Spoof intelligence, and specifically the default (and only) spoof intelligence policy in EOP, helps ensure the spoofed email sent by legitimate senders doesn't get caught up in EOP spam filters or external email systems. At the same time, spoofed intelligence protects an organization's users from spam and phishing attacks.
Over time, however, hackers found ingenious ways to turn this perfectly legitimate process into a means of stealing personal information. They do so using a technique known as Spoofing. Spoofing forges an email header so that it appears the message came from a trusted source. By doing so, attackers trick the recipient into divulging information such as account credentials, credit card information, or other sensitive information. When a user sees the sender information in the message, it looks like someone they know or a domain they trust, even though the message came from an attacker.
An email message contains two sender addresses:
- 5321.MailFrom. A sending mail server uses this address to identify the sender, shown in the header as Return-Path.
- 5322.From. The mail client displays this address as the from address, shown in the header as From.
The following telnet SMTP transcript shows how the SMTP conversation defines the two addresses:
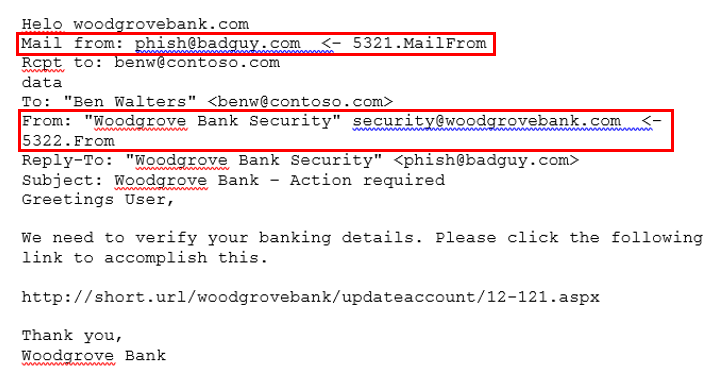
When the recipient receives this message in an email client such as Microsoft Outlook, the sender appears as "Woodgrove Bank Security"security@woodgrovebank.com. The recipient doesn't realize that it actually came from phish@badguy.com.