Examine identity models for Microsoft 365
Microsoft 365 uses Microsoft Entra ID to manage identities and authentication for Microsoft 365. Microsoft Entra ID is a cloud-based user identity and authentication service included with your Microsoft 365 subscription. Getting your identity infrastructure configured correctly is vital to managing Microsoft 365 user access and permissions for your organization.
Important
Azure Active Directory (Azure AD) is now Microsoft Entra ID. Learn more.
Additional viewing. Before you begin, watch this short four-minute video for an overview of identity models and authentication for Microsoft 365.
In Microsoft 365, a well-planned and executed identity infrastructure paves the way for stronger security. For example, restricting access to your productivity workloads and their data to only authenticated users and devices. Security for identities is a key element of a Zero Trust deployment, in which Microsoft 365 authenticates and authorizes all attempts to access resources both on-premises and in the cloud.
To plan for user accounts, you must first understand the two identity models in Microsoft 365:
- Cloud-only identity. You can maintain your organization's identities only in the cloud.
- Hybrid identity. You can maintain your on-premises Active Directory Domain Services (AD DS) identities and use them for authentication when users access Microsoft 365 cloud services.
The following table outlines the two types of identity, including their best fit and benefits.
| Attribute | Cloud-only identity | Hybrid identity |
|---|---|---|
| Definition | User account only exists in the Microsoft Entra tenant for your Microsoft 365 subscription. | User account exists in AD DS and a copy is also in the Microsoft Entra tenant for your Microsoft 365 subscription. The user account in Microsoft Entra ID might also include a hashed version of the already hashed AD DS user account password. |
| How Microsoft 365 authenticates user credentials | The Microsoft Entra tenant for your Microsoft 365 subscription performs the authentication with the cloud identity account. | The Microsoft Entra tenant for your Microsoft 365 subscription either handles the authentication process or redirects the user to another identity provider. |
| Best for | Organizations that don't have or need an on-premises AD DS. | Organizations using AD DS or another identity provider. |
| Greatest benefit | Simple to use. No extra directory tools or servers required. | Users can use the same credentials when accessing on-premises or cloud-based resources. |
The following sections examine each identity type in greater detail.
Cloud-only identity
Organizations that choose the cloud-only identity model already have a Microsoft Entra tenant for their Microsoft 365 subscription to store all their users, groups, and contacts. Once an organization sets up protection for administrator accounts and user accounts, it's ready to create the new accounts and groups that it needs.
A cloud-only identity uses user accounts that exist only in Microsoft Entra ID. Small and medium-sized organizations that don't have on-premises servers or don't use AD DS to manage local identities typically use cloud-only identity. The following diagram illustrates the basic components of the cloud-only identity model.
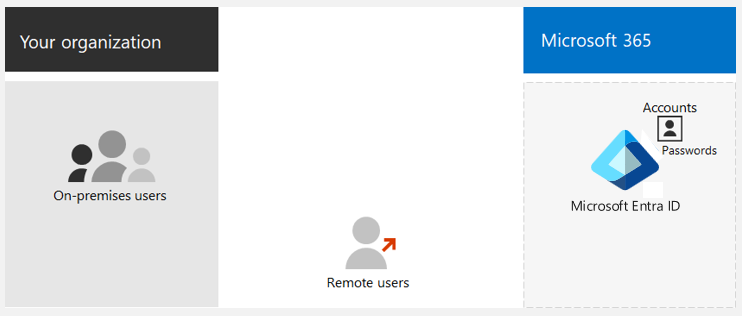
Both on-premises and remote (online) users use their Microsoft Entra user accounts and passwords to access Microsoft 365 cloud services. Microsoft Entra ID authenticates user credentials based on its stored user accounts and passwords.
Because Microsoft 365 only stores user accounts in Microsoft Entra ID, you manage cloud identities with tools such as the Microsoft 365 admin center and Windows PowerShell.
You can categorize users and their user accounts in several ways. For example, some are employees and have a permanent status. Some are vendors, contractors, or partners that have a temporary status. Some are external users that have no user accounts; however, you must still grant them access to specific services and resources to support interaction and collaboration. For example:
- Tenant accounts represent users within your organization that you license for cloud services.
- Business to Business (B2B) accounts represent users outside your organization that you invite to participate in collaboration.
An organization should take stock of the types of users in the company. What are the groupings? For example, you can group users by high-level function or by their purpose to your organization.
Additionally, you can share some cloud services with users outside your organization without any user accounts. Organizations must identify these groups of users as well.
Organizations can use groups in Microsoft Entra ID for several purposes that simplify management of their cloud environment. For example, with Microsoft Entra groups, you can:
- Use group-based licensing to automatically assign licenses for Microsoft 365 to your user accounts as soon as you add them as members.
- Add user accounts to specific groups dynamically based on user account attributes, such as department name.
- Automatically provision users for Software as a Service (SaaS) applications and to protect access to those applications with multifactor authentication and other Conditional Access policies.
- Provision permissions and levels of access for teams and SharePoint Online team sites.
Hybrid identity
Hybrid identity uses accounts that originate in an on-premises AD DS and have a copy in the Microsoft Entra tenant of a Microsoft 365 subscription. Most changes, except for specific account attributes, only flow one way. The system synchronizes changes that you make to on-premises AD DS user accounts to their copy in Microsoft Entra ID.
Organizations can choose between Microsoft Entra Connect Sync and Microsoft Entra Cloud Sync to provide the ongoing account synchronization.
- Microsoft Entra Connect Sync. An on-premises solution that runs on an on-premises server, checks for changes in the AD DS, and forwards those changes to Microsoft Entra ID. It offers a range of features for synchronizing on-premises Active Directory with Microsoft Entra ID. These features include password synchronization (known as password hash synchronization), device registration, and Active Directory Federation Services (AD FS) integration. Microsoft Entra Connect Sync is a scalable solution that can support large enterprise deployments with complex Active Directory environments. With Microsoft Entra Connect Sync, organizations are responsible for maintaining and supporting the solution on their own.
- Microsoft Entra Cloud Sync. A cloud-based solution that Microsoft hosts and manages in the Azure cloud. It only synchronizes user accounts, groups, and contact objects from on-premises Active Directory to Microsoft Entra ID. Microsoft designed Microsoft Entra Connect Cloud Sync for smaller organizations with simpler Active Directory environments. It's a fully managed service provided by Microsoft, which means that Microsoft takes care of all maintenance and support tasks.
When you implement hybrid identity, your on-premises AD DS is the authoritative source for account information. This model means that organizations perform administration tasks mostly on-premises, which they must then synchronize to Microsoft Entra ID.
The following diagram illustrates the basic components of the hybrid identity model.
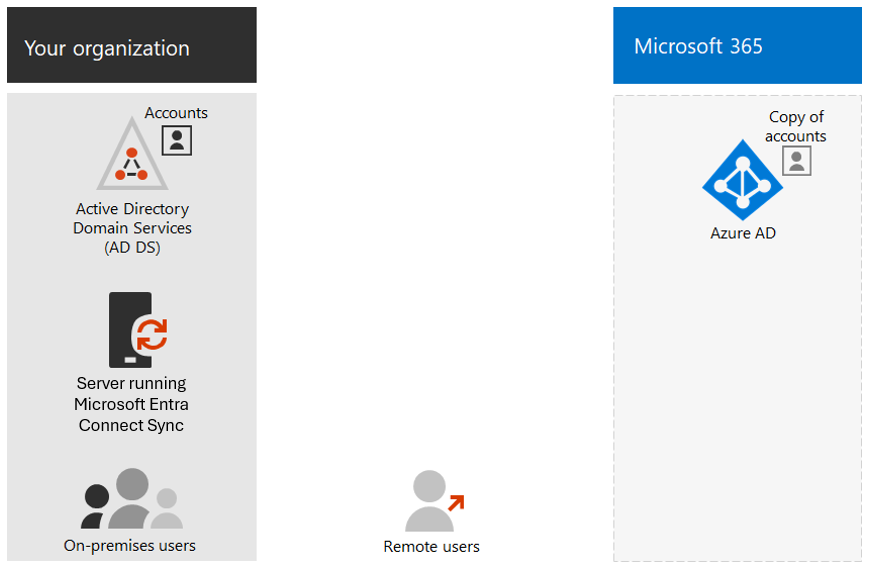
The Microsoft Entra tenant has a copy of the AD DS accounts. In this configuration, both on-premises and remote users accessing Microsoft 365 cloud services authenticate against Microsoft Entra ID.