Provide insight into suspicious activity using Microsoft Defender for Cloud App Security
Microsoft Cloud App Security provides insight into suspicious activity in Microsoft 365. This information gives organizations enhanced visibility and control over your Microsoft 365 tenant.
Cloud App Security consists of three core areas:
- Threat detection. Identifies high-risk and abnormal usage, security incidents, and potential threats in their environment. For example, if an administrator does something that administrators normally don't do – such as forwarding mail to different people – Cloud App Security send you an email alert so you can investigate those actions.
- Enhanced control. Monitors activities using granular controls and policies. For example, if someone completes a mass download of information, Cloud App Security sends you an email alert so you can take appropriate action.
- Discovery and insights. Provides insight into the variety of cloud apps people in your organization are using. This insight enables you to see which apps your organization uses and whether it approved them.
Moving to the cloud increases flexibility for employees and IT alike. However, it also introduces new challenges and complexities for keeping your organization secure. To get the full benefit of cloud apps and services, an IT team must find the right balance of supporting access while maintaining control to protect critical data.
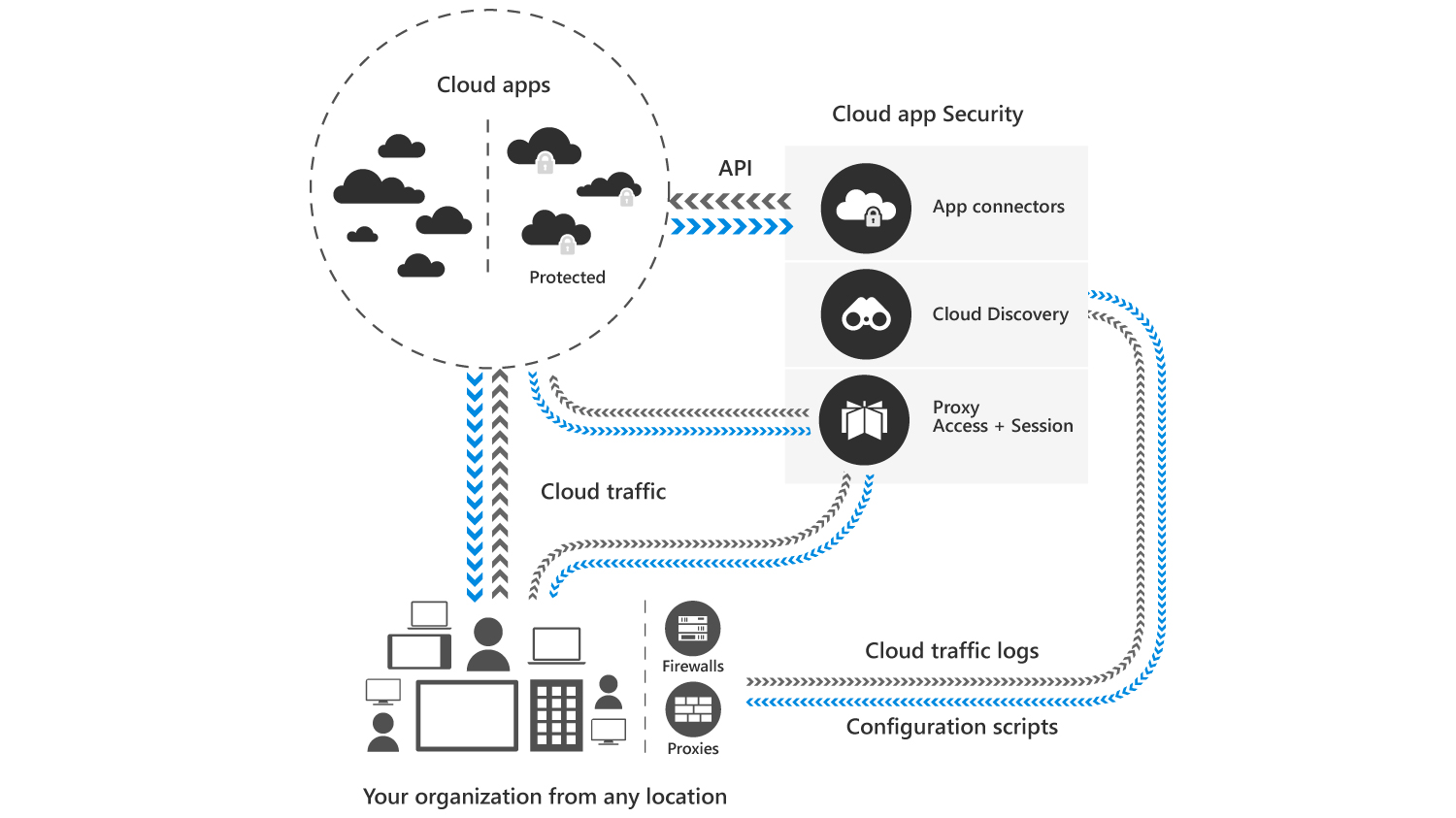
Microsoft Cloud App Security supports various deployment modes including log collection, API connectors, and reverse proxy. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your Microsoft and third-party cloud services. Microsoft designed Cloud App Security with security professionals in mind, and it natively integrates with leading Microsoft solutions.
Additional reading. For information about licensing, see the Microsoft Cloud App Security licensing datasheet.
The Cloud App Security framework
Cloud App Security provides the following functionality:
- Discover and control the use of Shadow IT. Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 16,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
- Protect your sensitive information anywhere in the cloud. Understand, classify, and protect the exposure of sensitive information at rest. Use out-of-the-box policies and automated processes to apply controls in real time across all your cloud apps.
- Protect against cyberthreats and anomalies. Detect unusual behavior across cloud apps to identify ransomware, compromised users or rogue applications, analyze high-risk usage and remediate automatically to limit the risk to your organization.
- Assess the compliance of your cloud apps. Assess if your cloud apps meet relevant compliance requirements including regulatory compliance and industry standards. Prevent data leaks to noncompliant apps, and limit access to regulated data.
Cloud App Security integrates visibility with your cloud by:
- Using Cloud Discovery to map and identify your cloud environment and the cloud apps your organization is using.
- Sanctioning and unsanctioning apps in your cloud.
- Using easy-to-deploy app connectors that take advantage of provider APIs, for visibility and governance of apps that you connect to.
- Using Conditional Access App Control protection to get real-time visibility and control over access and activities within your cloud apps.
- Helping you have continuous control by setting, and then continually fine-tuning, policies.
Additional reading. For more information, see: What is Cloud App Security?
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”