Exercise - Configure security settings
Contoso's security policy requires all user accounts to use multi-factor authentication (MFA). Instead of just offering email or over-the-phone verification, you should enable a second method as an alternative.
In order to always keep its users protected throughout, it's important to follow the order of changing the settings. First, the dynamic group was created. This group doesn't contain any users yet, but this will change with the next exercise. This dynamic group can then be used in the next step when creating a conditional access policy. By excluding the group, meeting room resource accounts are excluded from MFA requirements.
Afterward, the security defaults can be deactivated and changed to user defined and a second MFA method can be activated.
Setup Microsoft Entra Conditional Access
Due to Contoso Ltd.'s compliance policy, all users need to use MFA. Because Microsoft Teams Room accounts currently don't support MFA, you need to create an exclusion for these accounts with a Conditional Access Policy.
As the Global Administrator (globalAdmin@<tenant>.onmicrosoft.com), navigate to the Azure portal and go to Microsoft Entra Conditional Access.
Create a new Conditional Access Policy that includes all users. In the Exclude tab, select Users or groups and select the previous created group for MTR accounts TeamsRoomsAccounts_dynamic.
At Cloud apps or actions select All cloud apps
At Grant in the menu of Access control, select Require multi-factor authentication.
Save your settings and enable the policy.
Disable Security default settings
In the Azure portal logged in as Global Admin, below Properties, select Manage security defaults.
To be allowed to create and setup other security features, you need to set the Security defaults value to Disabled.
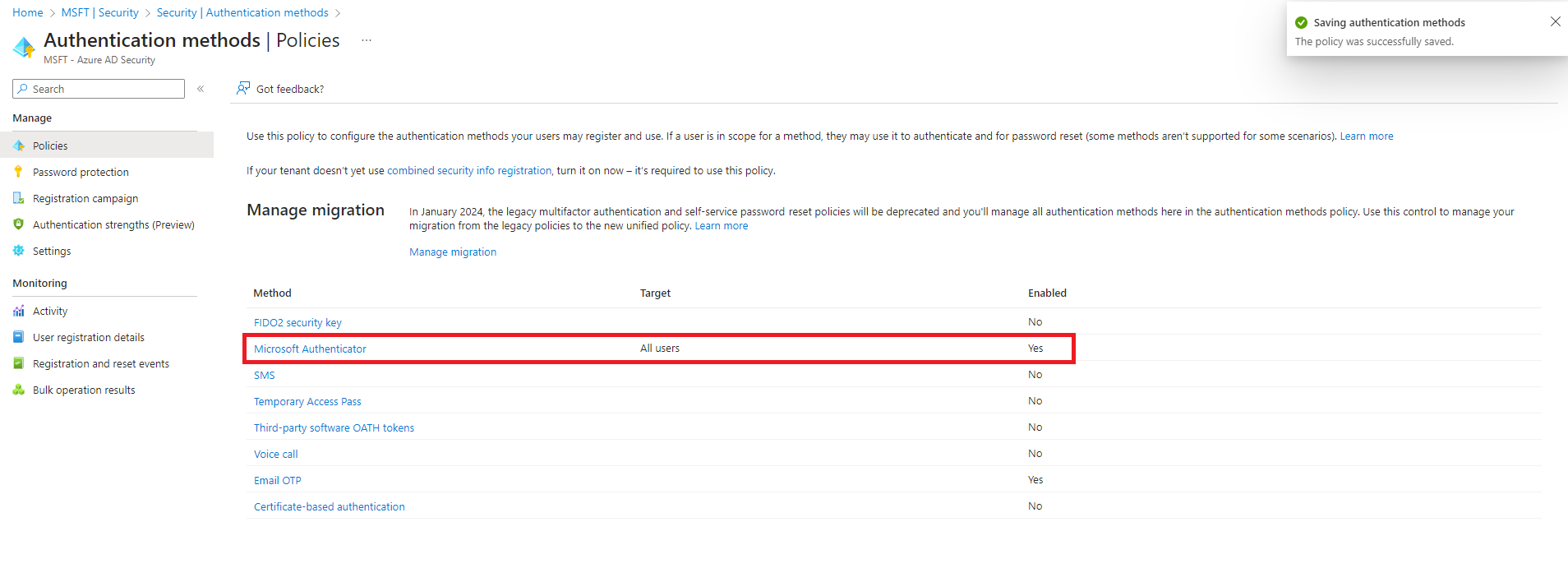
Allow the Microsoft Authenticator App as authentication method